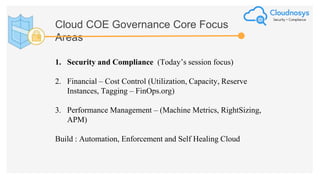
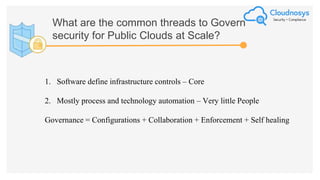
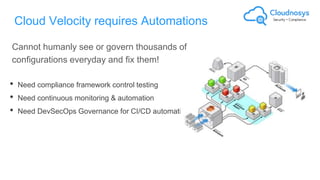
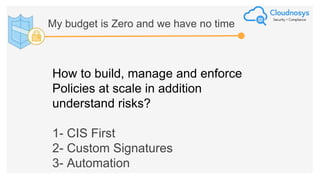
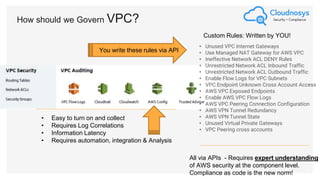
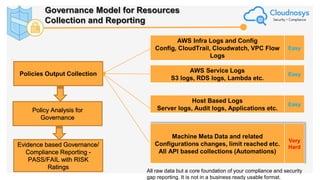
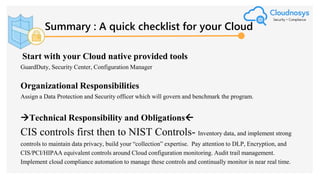
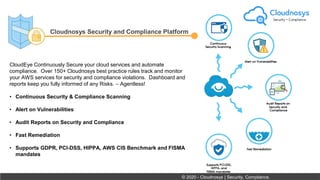
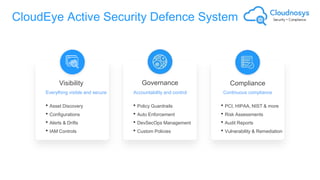
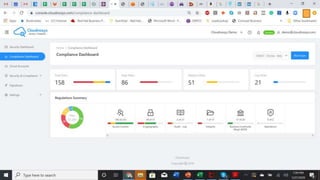
The document outlines best practices and governance strategies for multi-cloud security and compliance, emphasizing the importance of automation and continuous monitoring. It highlights the need for organizations to adopt a comprehensive governance framework that includes policy enforcement, risk management, and visibility across cloud assets. Additionally, it introduces the Cloudnosys Security and Compliance Platform as a solution for continuous security and compliance monitoring.