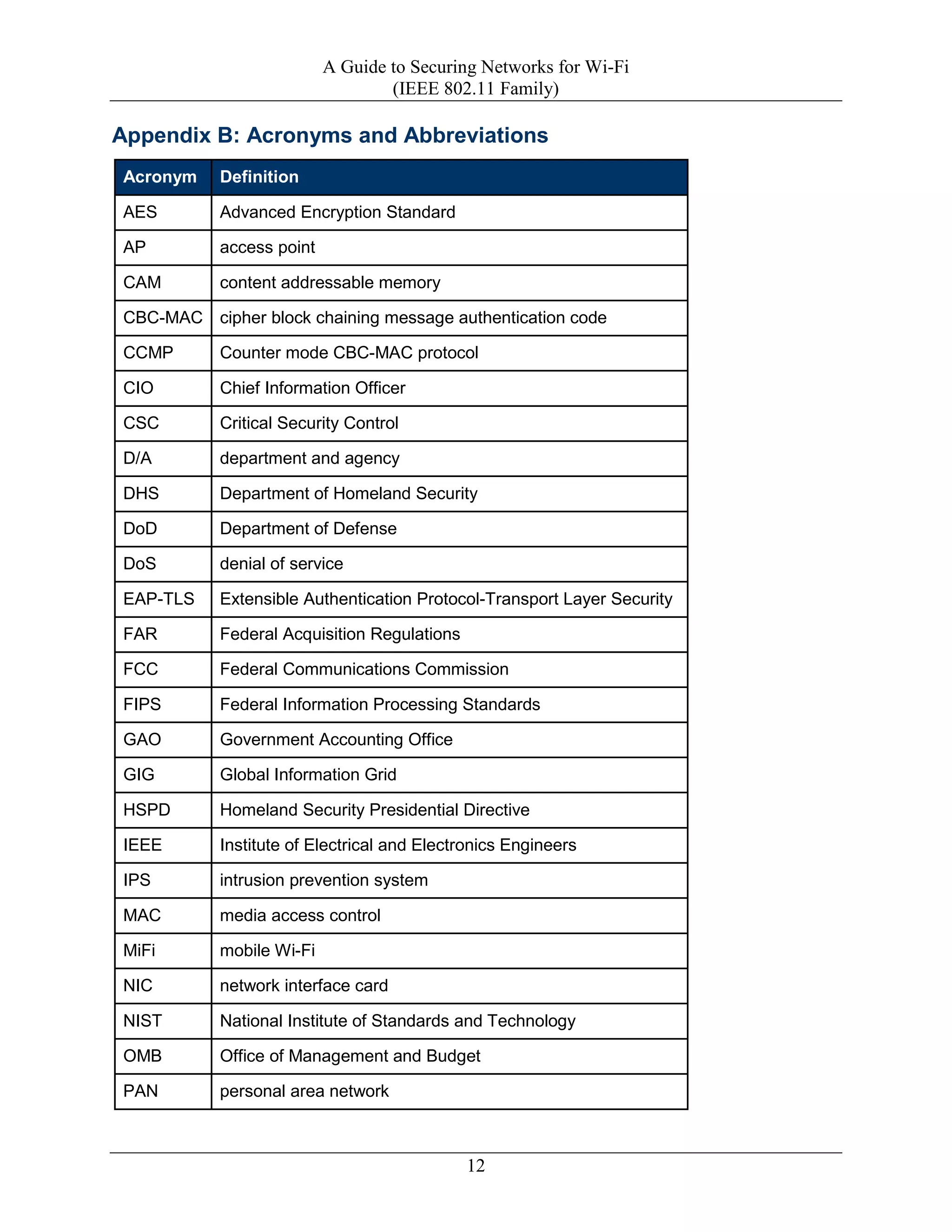
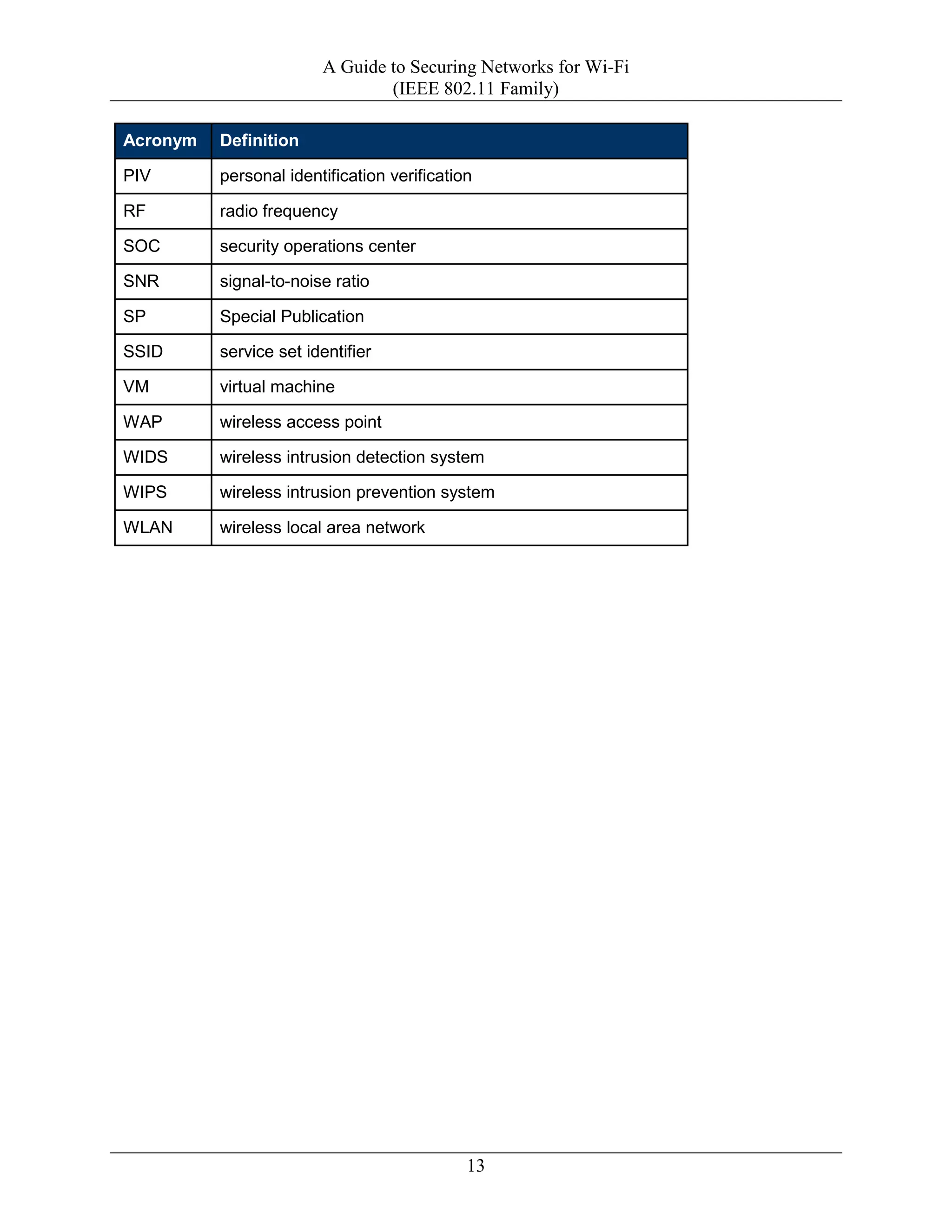
This document provides guidance on securing Wi-Fi networks and recommendations for:
1. Threat types including rogue access points, misconfigured APs, and denial of service attacks.
2. Using a wireless intrusion detection/prevention system to identify threats and enforce policies.
3. Requirements for enterprise wireless networking including encryption standards and authentication.