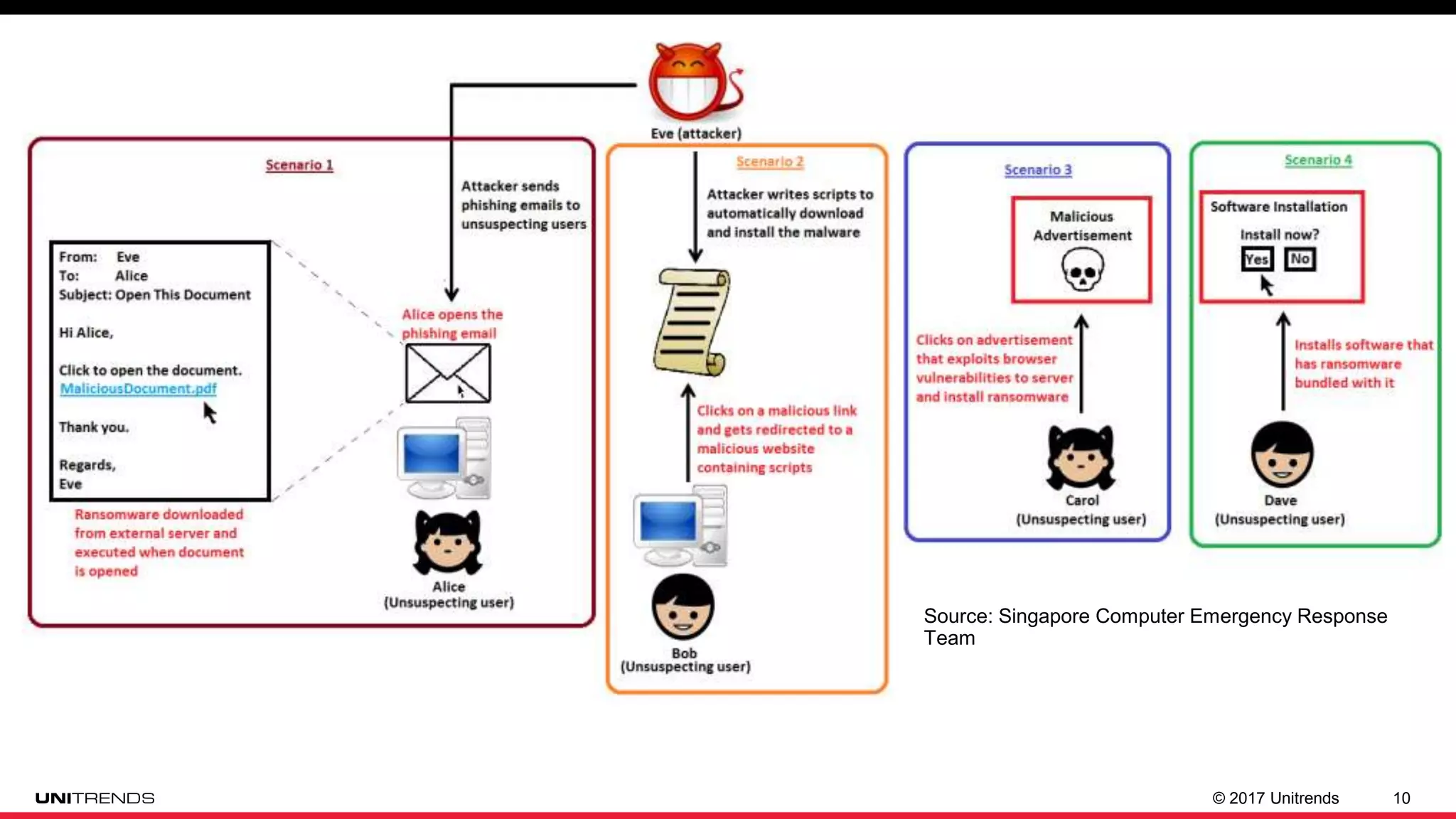
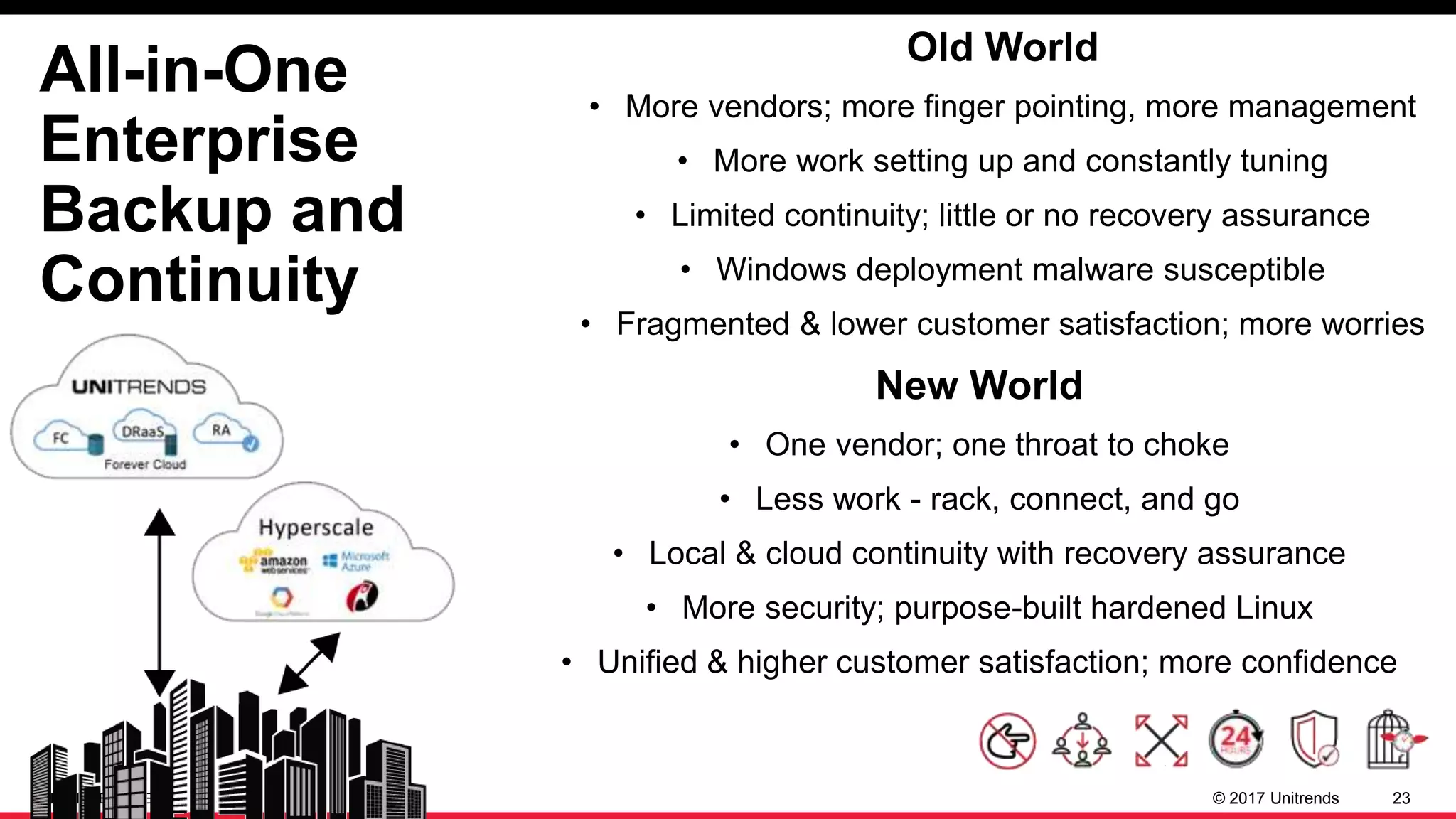
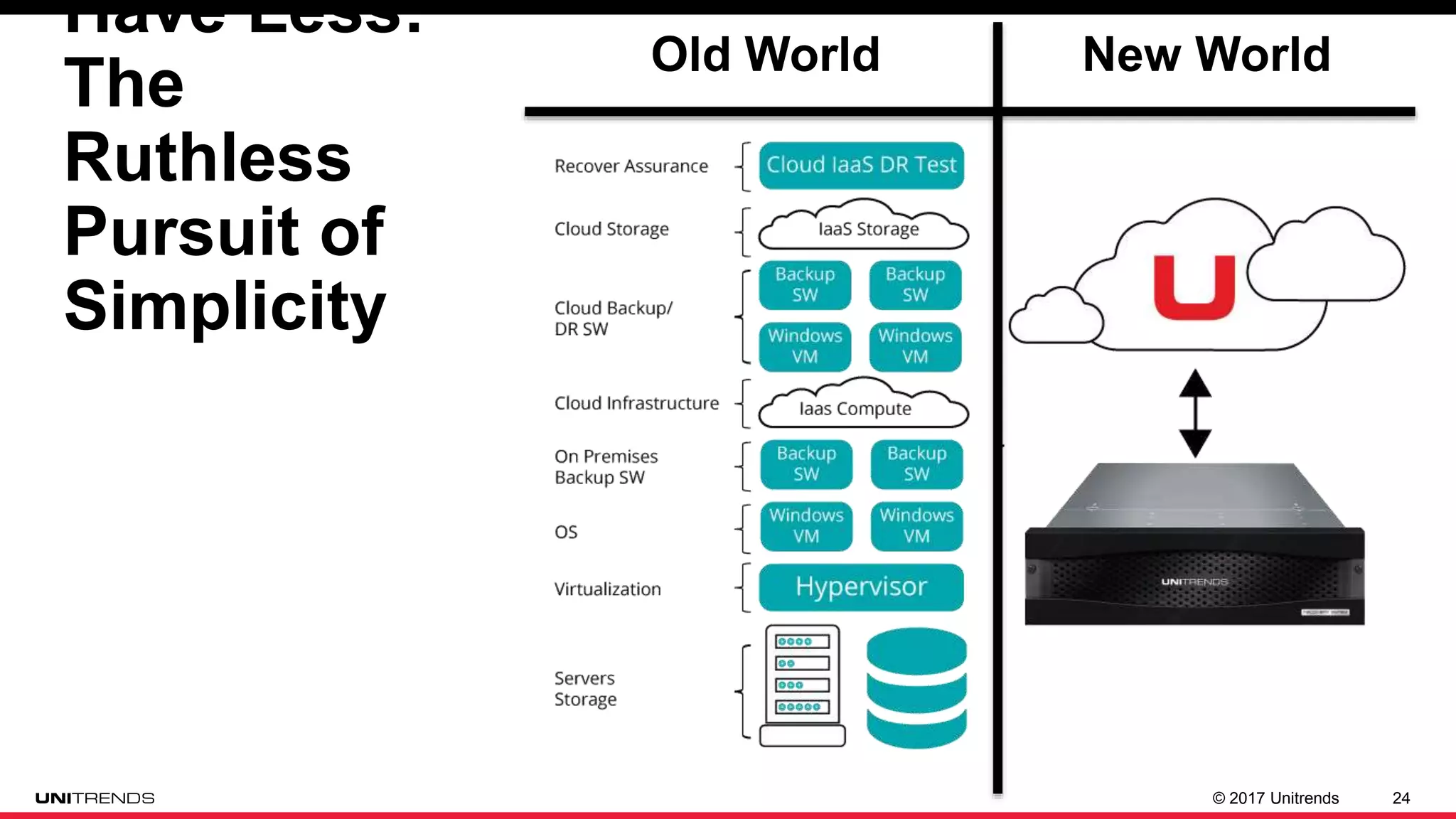
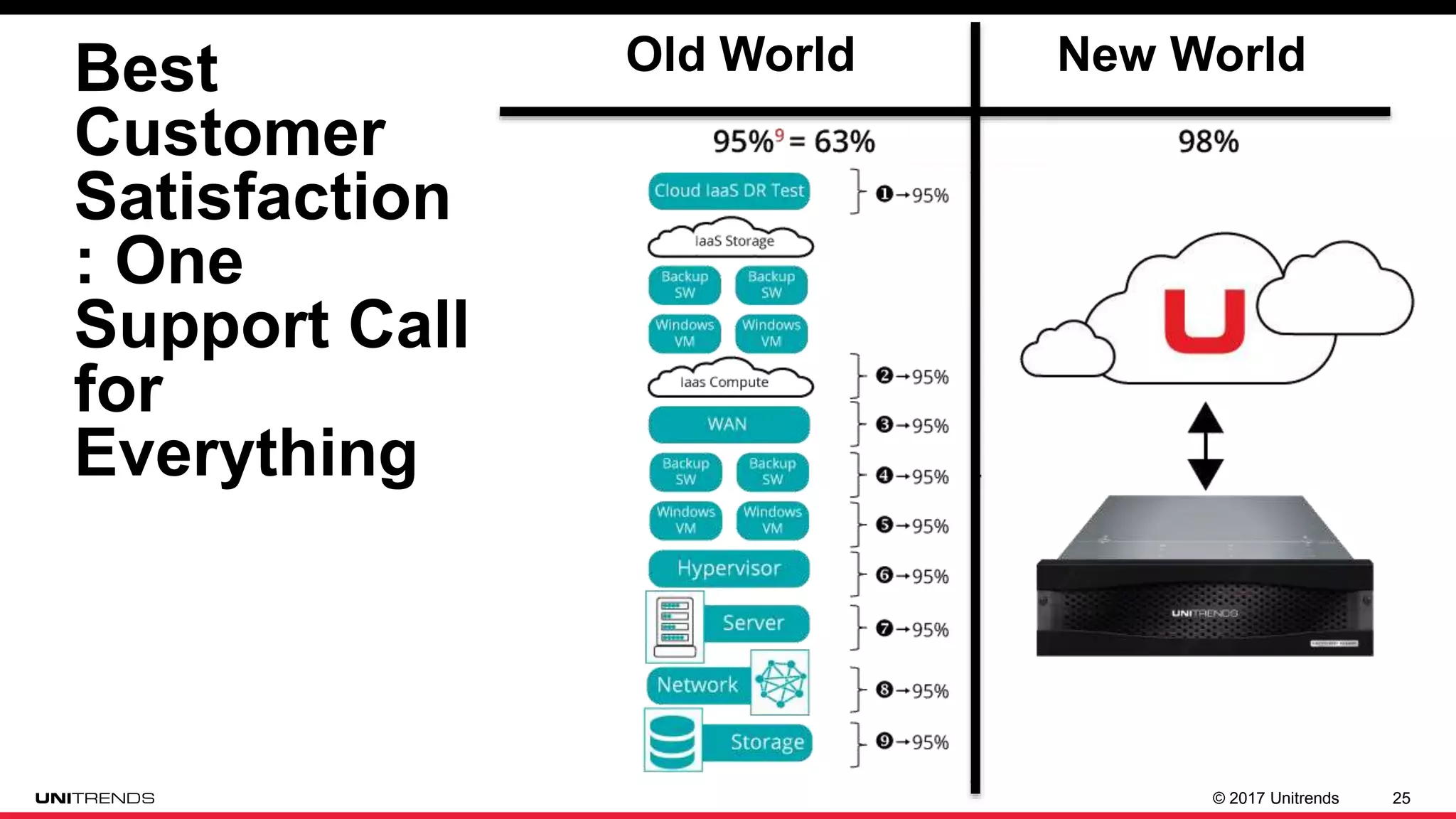
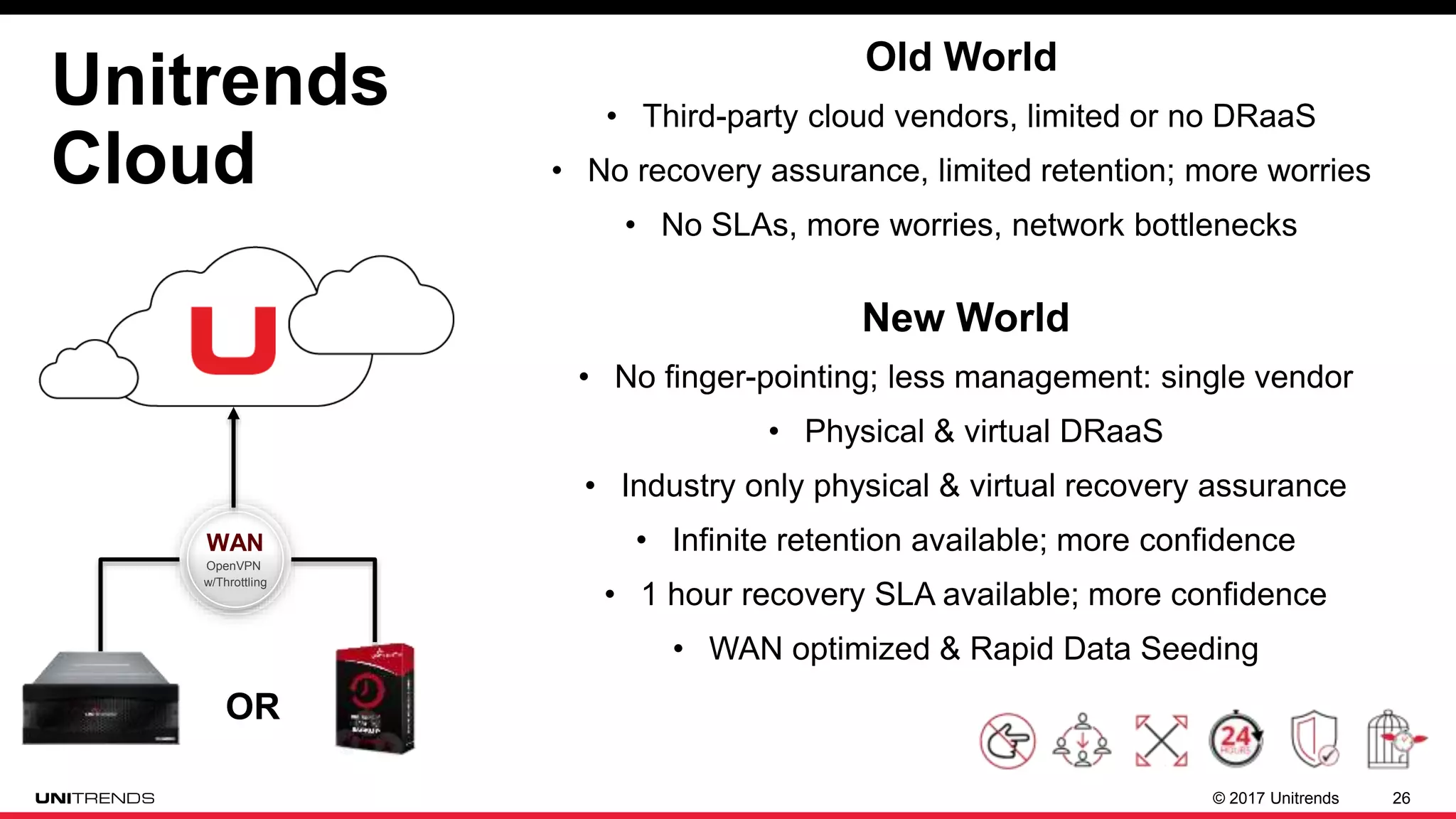
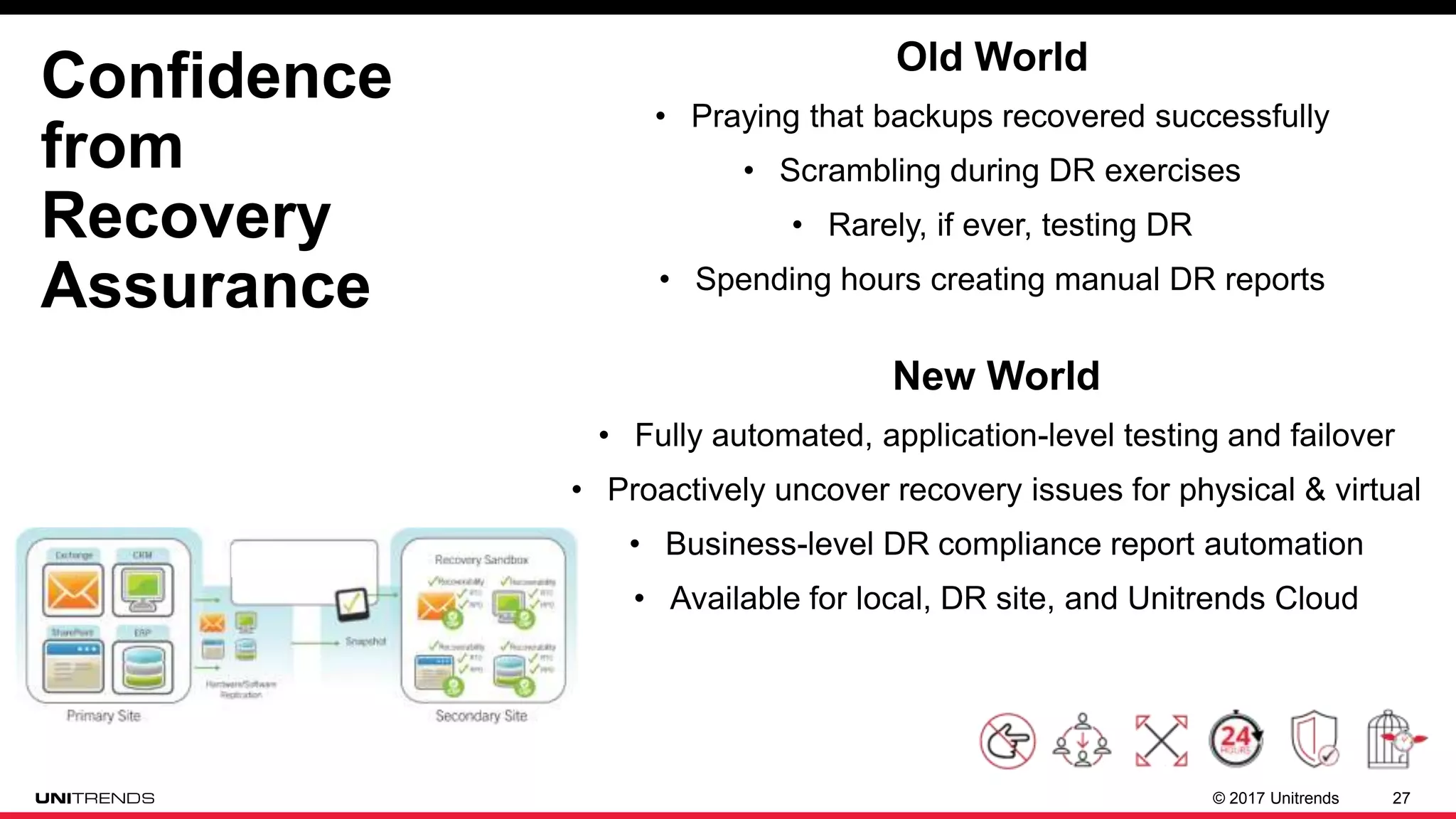
The document discusses the impact of ransomware, highlighting cases from St. Louis Public Libraries and Bethlehem, NY. It emphasizes the importance of backup solutions and proactive security measures to mitigate risks, while comparing traditional and modern backup solutions. It concludes by promoting Unitrends as a reliable provider of comprehensive backup and recovery services.