Osi
•Download as PPTX, PDF•
1 like•298 views
The document discusses the seven layers of the OSI model: Physical, Data Link, Network, Transport, Session, Presentation, and Application. It provides details on the functions of the Physical, Data Link, and Network layers, including framing bits, error control, addressing, encapsulation, and routing. The Transport layer establishes connections between applications on different hosts. The top three layers (Session, Presentation, Application) deal with coding/decoding data and establishing communication between applications.
Report
Share
Report
Share
Recommended
protocols and types of protocols.

contents
Protocol
Types of protocol
Transmission control protocol (TCP)
internet protocol (IP)
Hyper text transfer protocol (HTTP)
Simple mail transfer protocol (SMTP)
File transfer protocol (FTP)
Layers
protocol:-A protocol is a set of rules for the exchange of data between a terminal and computer or between two computers. Think of protocol as a sort of recommunication agreement about the form in which a message or data is to be sent and receipt is to be acknowledge.
transmission control protocol(TCP):-This protocol ensures the delivery of information packets across network.
internet protocol (IP):-This important protocol is responsible for providing logical addressing called IP address to route information between networks.
hyper text transfer protocol (HTTP):- This protocol is used to access, send and receive Hypertext Markup Language (HTML) files on the Internet.
simple mail transfer protocol(SMTP):-This protocol is used for transferring email between computers.
file transfer protocol(FTP):-FTP is responsible for allowing file to be copied between devices.
layers:-In computer programming, layering is the organization of programming into separate functional components that interact in some sequential and hierarchical way, with each layer usually having an interface only to the layer above it and the layer below it.
thankyou.
OSI Model

Explained Host & Media bring into play with respect to data, protocol over 7 layers of OSI Models.
Recommended
protocols and types of protocols.

contents
Protocol
Types of protocol
Transmission control protocol (TCP)
internet protocol (IP)
Hyper text transfer protocol (HTTP)
Simple mail transfer protocol (SMTP)
File transfer protocol (FTP)
Layers
protocol:-A protocol is a set of rules for the exchange of data between a terminal and computer or between two computers. Think of protocol as a sort of recommunication agreement about the form in which a message or data is to be sent and receipt is to be acknowledge.
transmission control protocol(TCP):-This protocol ensures the delivery of information packets across network.
internet protocol (IP):-This important protocol is responsible for providing logical addressing called IP address to route information between networks.
hyper text transfer protocol (HTTP):- This protocol is used to access, send and receive Hypertext Markup Language (HTML) files on the Internet.
simple mail transfer protocol(SMTP):-This protocol is used for transferring email between computers.
file transfer protocol(FTP):-FTP is responsible for allowing file to be copied between devices.
layers:-In computer programming, layering is the organization of programming into separate functional components that interact in some sequential and hierarchical way, with each layer usually having an interface only to the layer above it and the layer below it.
thankyou.
OSI Model

Explained Host & Media bring into play with respect to data, protocol over 7 layers of OSI Models.
Basic Concepts of Computer Networking

Here, I Discuss about the definition, Communication devices, Nic, Mac address, ip adress,transmission mode. types of computer network.
Cn

explanation of :-difference between udp and tcp,different network models,modes of communication,different layers with help of examples.network layers and how it works
Lecture 3- tcp-ip

Internet Technology Lectures
network protocols, TCP/IP Model
Lecturer: Saman M. Almufti / Kurdistan Region, Nawroz University
facebook: https://www.facebook.com/saman.malmufti
YouTube Link:https://youtu.be/JgbAWAc0fDs
Network Protocol

DCS and Scada Presentation on Topic of the Network Protocol.
This Presentation will save ur Lots of Time and Effort if you are Lucky One to Have this as ur ALA Topic.. Kudos Guys
Networking Essentials Lesson 02 - Standards and OSI - Eric Vanderburg

Networking Essentials Lesson 02 - Standards and OSI - Eric Vanderburg
Communication protocol presentation

About Communication Protocols,In this presentation user can get some basic idea about Protocols and how its communicating with OSI Layer.
Slides for protocol layering and network applications

why and how Protocol layering is done in TCP/IP protocol suite, how multiplexing and demultiplexing can be done in different protocol layers in TCP\IP.
Network Protocol and TCP/IP

Network Protocol and TCP/IP
Presented by Bwsrang Basumatary & Dashrath Singh Nag TISS, Mumbai, MLISc. Sem -III, 2015
TCP-IP Reference Model

What is the TCP-IP reference model? Comparison with OSI Model. Functions of the various layers of TCP model. Connection-oriented and connectionless services.
Video on OSI Model is here: https://youtu.be/b-JU9aWdoP8
withe exam questions
TCP/IP Protocols With All Layer Description

TCP/IP have 5 layers, whereas OSI model have 7 layers in its Model. TCP/IP is known for the secured connection and comunication. I have explained all functions and definitions of layers in TCP/IP Model
Osi model

This slide is all about OSI model of Computer Network. It was the very first standard model for Computer Network System. In this slide I have discussed about the 7 layers of OSI model.
More Related Content
What's hot
Basic Concepts of Computer Networking

Here, I Discuss about the definition, Communication devices, Nic, Mac address, ip adress,transmission mode. types of computer network.
Cn

explanation of :-difference between udp and tcp,different network models,modes of communication,different layers with help of examples.network layers and how it works
Lecture 3- tcp-ip

Internet Technology Lectures
network protocols, TCP/IP Model
Lecturer: Saman M. Almufti / Kurdistan Region, Nawroz University
facebook: https://www.facebook.com/saman.malmufti
YouTube Link:https://youtu.be/JgbAWAc0fDs
Network Protocol

DCS and Scada Presentation on Topic of the Network Protocol.
This Presentation will save ur Lots of Time and Effort if you are Lucky One to Have this as ur ALA Topic.. Kudos Guys
Networking Essentials Lesson 02 - Standards and OSI - Eric Vanderburg

Networking Essentials Lesson 02 - Standards and OSI - Eric Vanderburg
Communication protocol presentation

About Communication Protocols,In this presentation user can get some basic idea about Protocols and how its communicating with OSI Layer.
Slides for protocol layering and network applications

why and how Protocol layering is done in TCP/IP protocol suite, how multiplexing and demultiplexing can be done in different protocol layers in TCP\IP.
Network Protocol and TCP/IP

Network Protocol and TCP/IP
Presented by Bwsrang Basumatary & Dashrath Singh Nag TISS, Mumbai, MLISc. Sem -III, 2015
TCP-IP Reference Model

What is the TCP-IP reference model? Comparison with OSI Model. Functions of the various layers of TCP model. Connection-oriented and connectionless services.
Video on OSI Model is here: https://youtu.be/b-JU9aWdoP8
withe exam questions
TCP/IP Protocols With All Layer Description

TCP/IP have 5 layers, whereas OSI model have 7 layers in its Model. TCP/IP is known for the secured connection and comunication. I have explained all functions and definitions of layers in TCP/IP Model
Osi model

This slide is all about OSI model of Computer Network. It was the very first standard model for Computer Network System. In this slide I have discussed about the 7 layers of OSI model.
What's hot (20)
Networking Essentials Lesson 02 - Standards and OSI - Eric Vanderburg

Networking Essentials Lesson 02 - Standards and OSI - Eric Vanderburg
INTRODUCTION TO INTERNET PROTOCOL BY SAIKIRAN PANJALA

INTRODUCTION TO INTERNET PROTOCOL BY SAIKIRAN PANJALA
Slides for protocol layering and network applications

Slides for protocol layering and network applications
Viewers also liked
Illustrating Freedom: 'Martin Luther King and the Montgomery Story' as a Rhet...

Published as a comic book in 1958, 'Martin Luther King and the Montgomery Story' went on to inspire hundreds of thousands to use active nonviolence in the fight against injustice, and inequality.
Viewers also liked (9)
Illustrating Freedom: 'Martin Luther King and the Montgomery Story' as a Rhet...

Illustrating Freedom: 'Martin Luther King and the Montgomery Story' as a Rhet...
Similar to Osi
TCP IP PowerPoint presentation download.

TCP project here PowerPoint presentation for study for BCA student
OSI MODEL 

OSI stands for Open Systems Interconnection. It has been developed by ISO – ‘International Organization of Standardization‘, in the year 1984. It is a 7 layer architecture with each layer having specific functionality to perform.
Manish Jha- Research Scholar- Internet Basics Requriement

Manish Jha is a Research Scholar- Uttrakhand Technical University Dehradun
seven layer OSI model

The International Standards Organization (ISO) developed the Open Systems Interconnection (OSI) model. It divides network communication into seven layers. ... Layers 5-7, called the the upper layers, contain application-level data
#imannjeet #mannjeet mn
OSI &TCP/IP Model

This is a notes about basic introduction of OSI Model & TCP/IP Model. It contain details about the seven layers of the OSI Model which are Application layer, Presentation Layer, Session Layer, Transport Layer, Network Layer, Data Link Layer, Physical Layer
OSI reference Model

This topic explains the Open system interconnect model, and simply explains each of the seven layers in a way that is understandable by all
presentation on TCP/IP protocols data comunications

If the content is useful. Please use it as reference.
Similar to Osi (20)
Manish Jha- Research Scholar- Internet Basics Requriement

Manish Jha- Research Scholar- Internet Basics Requriement
presentation on TCP/IP protocols data comunications

presentation on TCP/IP protocols data comunications
Recently uploaded
Communications Mining Series - Zero to Hero - Session 1

This session provides introduction to UiPath Communication Mining, importance and platform overview. You will acquire a good understand of the phases in Communication Mining as we go over the platform with you. Topics covered:
• Communication Mining Overview
• Why is it important?
• How can it help today’s business and the benefits
• Phases in Communication Mining
• Demo on Platform overview
• Q/A
GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...

Leonard Jayamohan, Partner & Generative AI Lead, Deloitte
This keynote will reveal how Deloitte leverages Neo4j’s graph power for groundbreaking digital twin solutions, achieving a staggering 100x performance boost. Discover the essential role knowledge graphs play in successful generative AI implementations. Plus, get an exclusive look at an innovative Neo4j + Generative AI solution Deloitte is developing in-house.
UiPath Test Automation using UiPath Test Suite series, part 4

Welcome to UiPath Test Automation using UiPath Test Suite series part 4. In this session, we will cover Test Manager overview along with SAP heatmap.
The UiPath Test Manager overview with SAP heatmap webinar offers a concise yet comprehensive exploration of the role of a Test Manager within SAP environments, coupled with the utilization of heatmaps for effective testing strategies.
Participants will gain insights into the responsibilities, challenges, and best practices associated with test management in SAP projects. Additionally, the webinar delves into the significance of heatmaps as a visual aid for identifying testing priorities, areas of risk, and resource allocation within SAP landscapes. Through this session, attendees can expect to enhance their understanding of test management principles while learning practical approaches to optimize testing processes in SAP environments using heatmap visualization techniques
What will you get from this session?
1. Insights into SAP testing best practices
2. Heatmap utilization for testing
3. Optimization of testing processes
4. Demo
Topics covered:
Execution from the test manager
Orchestrator execution result
Defect reporting
SAP heatmap example with demo
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

Sudheer Mechineni, Head of Application Frameworks, Standard Chartered Bank
Discover how Standard Chartered Bank harnessed the power of Neo4j to transform complex data access challenges into a dynamic, scalable graph database solution. This keynote will cover their journey from initial adoption to deploying a fully automated, enterprise-grade causal cluster, highlighting key strategies for modelling organisational changes and ensuring robust disaster recovery. Learn how these innovations have not only enhanced Standard Chartered Bank’s data infrastructure but also positioned them as pioneers in the banking sector’s adoption of graph technology.
The Art of the Pitch: WordPress Relationships and Sales

Clients don’t know what they don’t know. What web solutions are right for them? How does WordPress come into the picture? How do you make sure you understand scope and timeline? What do you do if sometime changes?
All these questions and more will be explored as we talk about matching clients’ needs with what your agency offers without pulling teeth or pulling your hair out. Practical tips, and strategies for successful relationship building that leads to closing the deal.
Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf

91mobiles recently conducted a Smart TV Buyer Insights Survey in which we asked over 3,000 respondents about the TV they own, aspects they look at on a new TV, and their TV buying preferences.
20240607 QFM018 Elixir Reading List May 2024

Everything I found interesting about the Elixir programming ecosystem in May 2024
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Monitoring and observability aren’t traditionally found in software curriculums and many of us cobble this knowledge together from whatever vendor or ecosystem we were first introduced to and whatever is a part of your current company’s observability stack.
While the dev and ops silo continues to crumble….many organizations still relegate monitoring & observability as the purview of ops, infra and SRE teams. This is a mistake - achieving a highly observable system requires collaboration up and down the stack.
I, a former op, would like to extend an invitation to all application developers to join the observability party will share these foundational concepts to build on:
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
Elevating Tactical DDD Patterns Through Object Calisthenics

After immersing yourself in the blue book and its red counterpart, attending DDD-focused conferences, and applying tactical patterns, you're left with a crucial question: How do I ensure my design is effective? Tactical patterns within Domain-Driven Design (DDD) serve as guiding principles for creating clear and manageable domain models. However, achieving success with these patterns requires additional guidance. Interestingly, we've observed that a set of constraints initially designed for training purposes remarkably aligns with effective pattern implementation, offering a more ‘mechanical’ approach. Let's explore together how Object Calisthenics can elevate the design of your tactical DDD patterns, offering concrete help for those venturing into DDD for the first time!
Epistemic Interaction - tuning interfaces to provide information for AI support

Paper presented at SYNERGY workshop at AVI 2024, Genoa, Italy. 3rd June 2024
https://alandix.com/academic/papers/synergy2024-epistemic/
As machine learning integrates deeper into human-computer interactions, the concept of epistemic interaction emerges, aiming to refine these interactions to enhance system adaptability. This approach encourages minor, intentional adjustments in user behaviour to enrich the data available for system learning. This paper introduces epistemic interaction within the context of human-system communication, illustrating how deliberate interaction design can improve system understanding and adaptation. Through concrete examples, we demonstrate the potential of epistemic interaction to significantly advance human-computer interaction by leveraging intuitive human communication strategies to inform system design and functionality, offering a novel pathway for enriching user-system engagements.
Alt. GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using ...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
Removing Uninteresting Bytes in Software Fuzzing

Imagine a world where software fuzzing, the process of mutating bytes in test seeds to uncover hidden and erroneous program behaviors, becomes faster and more effective. A lot depends on the initial seeds, which can significantly dictate the trajectory of a fuzzing campaign, particularly in terms of how long it takes to uncover interesting behaviour in your code. We introduce DIAR, a technique designed to speedup fuzzing campaigns by pinpointing and eliminating those uninteresting bytes in the seeds. Picture this: instead of wasting valuable resources on meaningless mutations in large, bloated seeds, DIAR removes the unnecessary bytes, streamlining the entire process.
In this work, we equipped AFL, a popular fuzzer, with DIAR and examined two critical Linux libraries -- Libxml's xmllint, a tool for parsing xml documents, and Binutil's readelf, an essential debugging and security analysis command-line tool used to display detailed information about ELF (Executable and Linkable Format). Our preliminary results show that AFL+DIAR does not only discover new paths more quickly but also achieves higher coverage overall. This work thus showcases how starting with lean and optimized seeds can lead to faster, more comprehensive fuzzing campaigns -- and DIAR helps you find such seeds.
- These are slides of the talk given at IEEE International Conference on Software Testing Verification and Validation Workshop, ICSTW 2022.
20240605 QFM017 Machine Intelligence Reading List May 2024

Everything I found interesting about machines behaving intelligently during May 2024
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

The publishing industry has been selling digital audiobooks and ebooks for over a decade and has found its groove. What’s changed? What has stayed the same? Where do we go from here? Join a group of leading sales peers from across the industry for a conversation about the lessons learned since the popularization of digital books, best practices, digital book supply chain management, and more.
Link to video recording: https://bnctechforum.ca/sessions/selling-digital-books-in-2024-insights-from-industry-leaders/
Presented by BookNet Canada on May 28, 2024, with support from the Department of Canadian Heritage.
GraphSummit Singapore | Enhancing Changi Airport Group's Passenger Experience...

Dr. Sean Tan, Head of Data Science, Changi Airport Group
Discover how Changi Airport Group (CAG) leverages graph technologies and generative AI to revolutionize their search capabilities. This session delves into the unique search needs of CAG’s diverse passengers and customers, showcasing how graph data structures enhance the accuracy and relevance of AI-generated search results, mitigating the risk of “hallucinations” and improving the overall customer journey.
Recently uploaded (20)
Communications Mining Series - Zero to Hero - Session 1

Communications Mining Series - Zero to Hero - Session 1
GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...

GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...
UiPath Test Automation using UiPath Test Suite series, part 4

UiPath Test Automation using UiPath Test Suite series, part 4
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...
Free Complete Python - A step towards Data Science

Free Complete Python - A step towards Data Science
The Art of the Pitch: WordPress Relationships and Sales

The Art of the Pitch: WordPress Relationships and Sales
Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf

Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...
FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf

FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf
Elevating Tactical DDD Patterns Through Object Calisthenics

Elevating Tactical DDD Patterns Through Object Calisthenics
Epistemic Interaction - tuning interfaces to provide information for AI support

Epistemic Interaction - tuning interfaces to provide information for AI support
Alt. GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using ...

Alt. GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using ...
20240605 QFM017 Machine Intelligence Reading List May 2024

20240605 QFM017 Machine Intelligence Reading List May 2024
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

Transcript: Selling digital books in 2024: Insights from industry leaders - T...
GraphSummit Singapore | Enhancing Changi Airport Group's Passenger Experience...

GraphSummit Singapore | Enhancing Changi Airport Group's Passenger Experience...
Osi
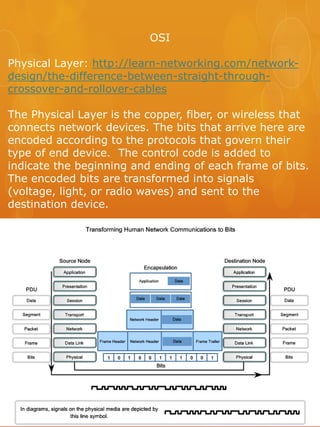
- 1. OSI Physical Layer: http://learn-networking.com/network- design/the-difference-between-straight-through- crossover-and-rollover-cables The Physical Layer is the copper, fiber, or wireless that connects network devices. The bits that arrive here are encoded according to the protocols that govern their type of end device. The control code is added to indicate the beginning and ending of each frame of bits. The encoded bits are transformed into signals (voltage, light, or radio waves) and sent to the destination device.
- 2. The Data-Link layer arranges the bits it receives into frames and provides synchronization, error control and flow control. It has two sub layers that are the logical link control and media access control. It begins the process of encapsulation and adds a trailer and header. The source and destination addresses are included along with frame check sequence values, quality of service, and type of protocol for whatever media is present. It links the hardware and software layers together.
- 3. Network Layer Translates addresses from logical to physical and visa- versa the other way. This is where addressing the networks and subnetting comes into play. Encapsulation of frames: IP header, source IP address, destination IP address. All available common network layer protocols. can’t wait! Dynamically done for me
- 4. Type of service determines the priority of the packet and looks for the Quality of Service to decide who goes first. EX: Voice transmits faster than e-mail. Time to Live ensures a packet can’t get stuck looping in to infinity. Protocol determines which type of data packet it is: ICMP, TCP, UDP The header checksum provides a security measure to make sure the data is exactly how it was from origination to destination. Packet Length is between
- 5. Routing: Carrying Data end to end:
- 9. Transport Layer: Visual Version
- 15. Source Port Address or name of remote host destination Port Connection State
- 30. The top three layers Application Layer: Is the first step to getting data onto the network. Three primary functions: 1. Coding and conversion of application layer data to ensure that data from the source device can be interpreted by the appropriate application on the destination device. 2. Compression of the data so that it can be decompressed by the destination device. 3. Encryption of the data for transmission and decryption of data by the destination device. Applications are computer programs with which the user interacts and that initiate the data transfer process at the user’s request. Services are background programs that provide the connection between the application layer and the lower layers of the networking model. The most widely-known TCP/IP Application layer protocols are those that provide for the exchange of user information. These protocols specify the format and control information necessary for many of the common Internet communication functions. Among these TCP/IP protocols are:
- 31. DNS: TCP/UDP port 53 Telnet: TCP port 23 SMTP:TCP port 25, POP:UDP port 110 DHDHCP: UDP port 67 port 80a TCP ports 20 and 21