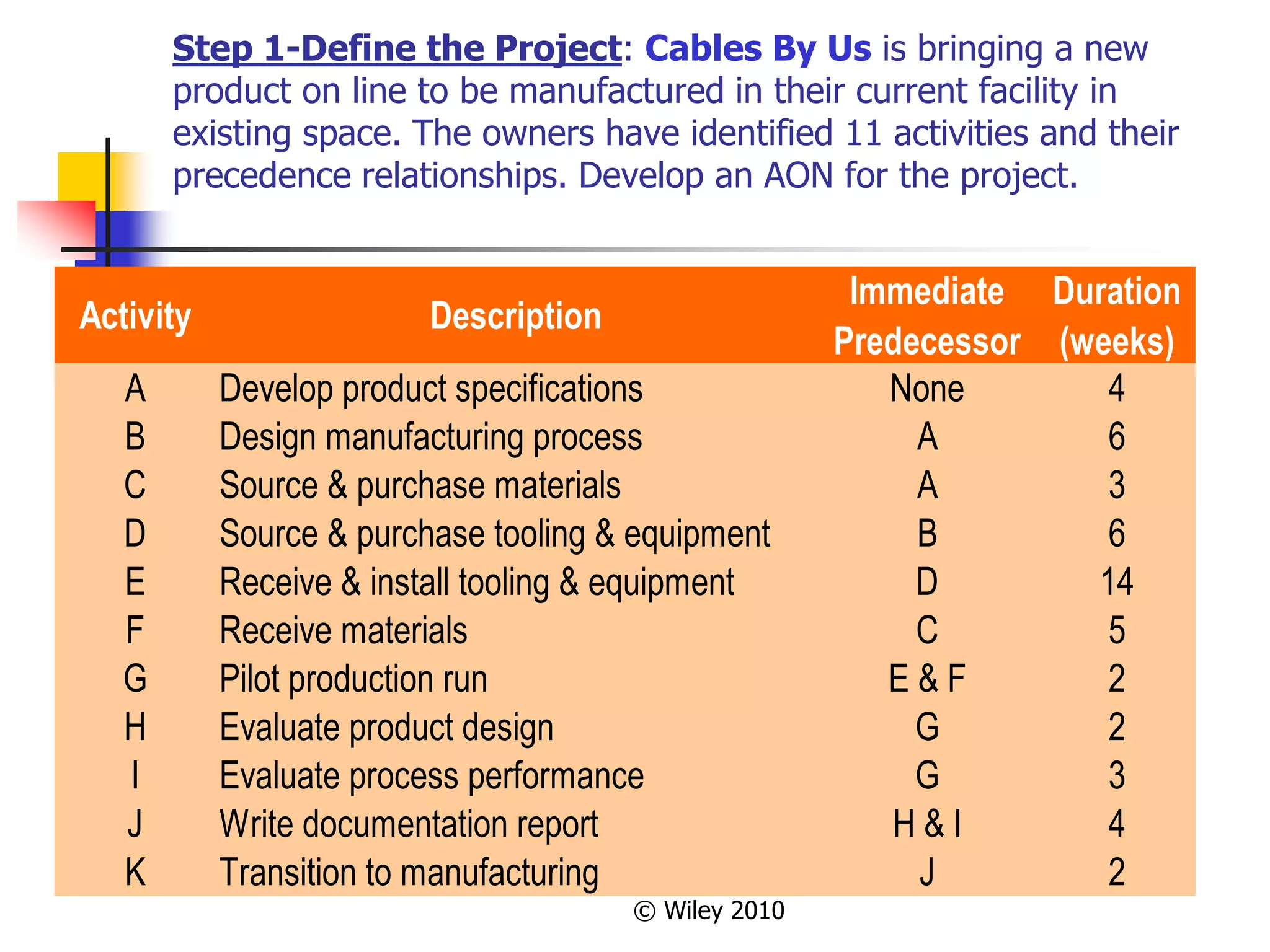
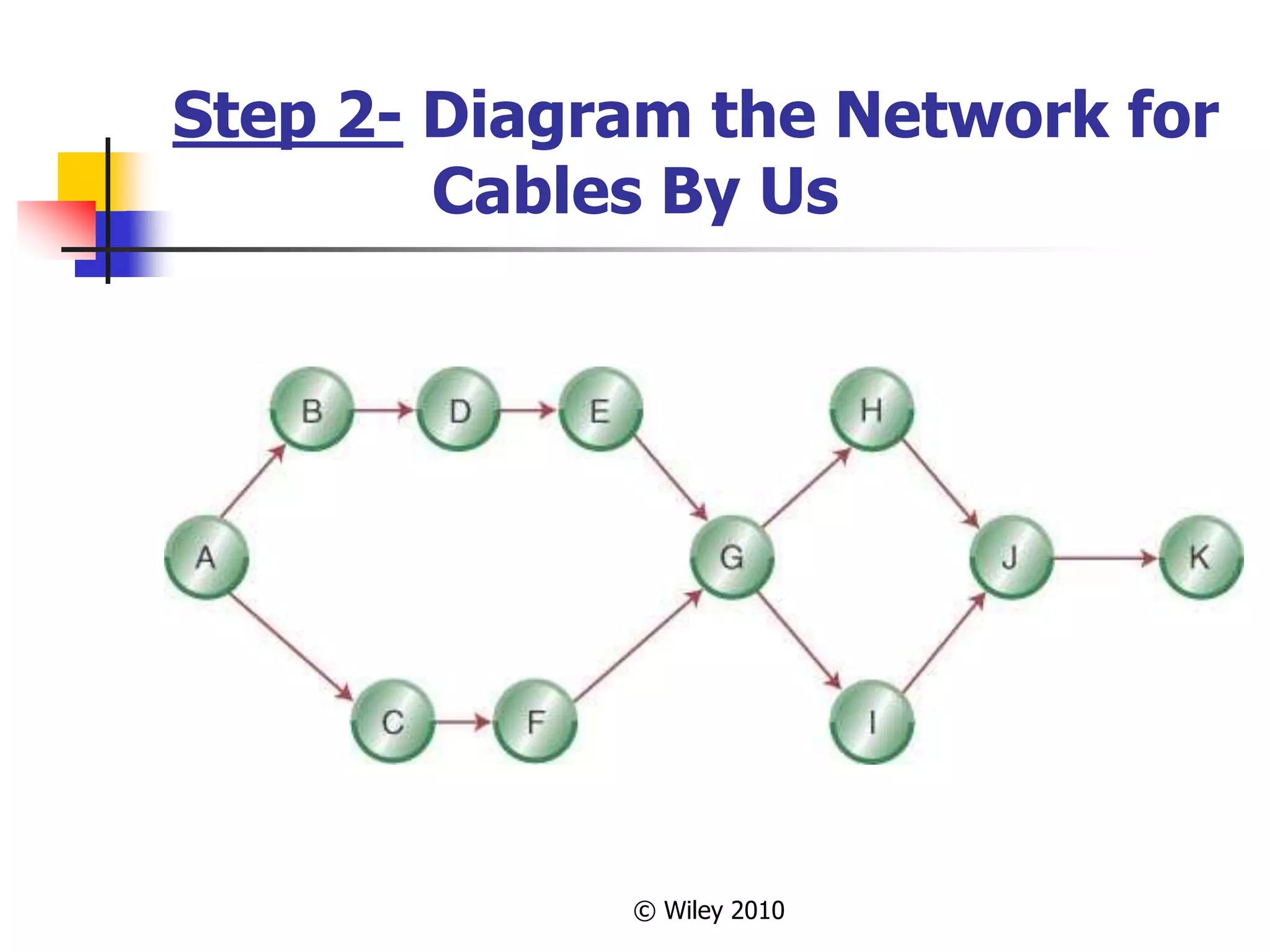
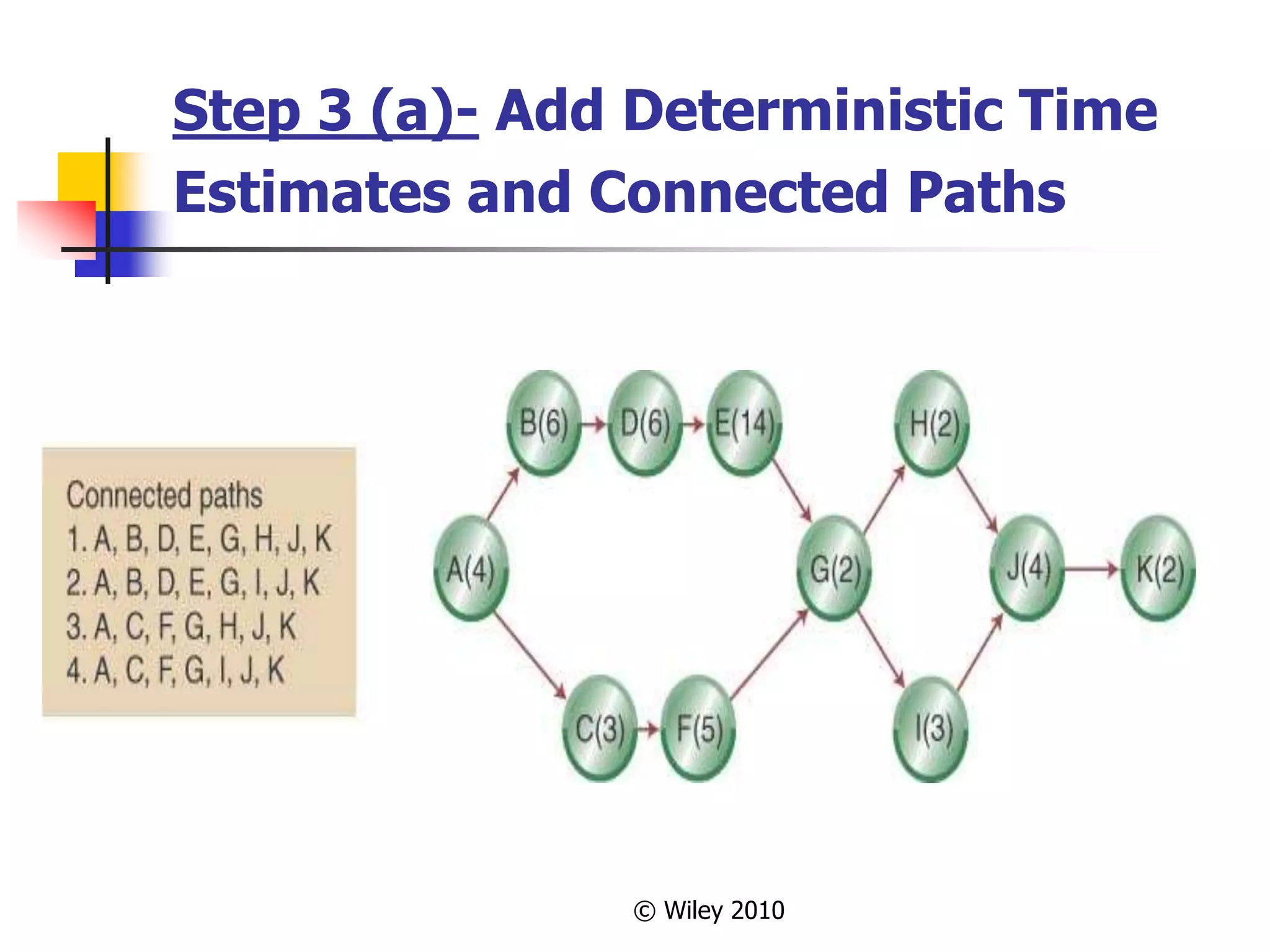
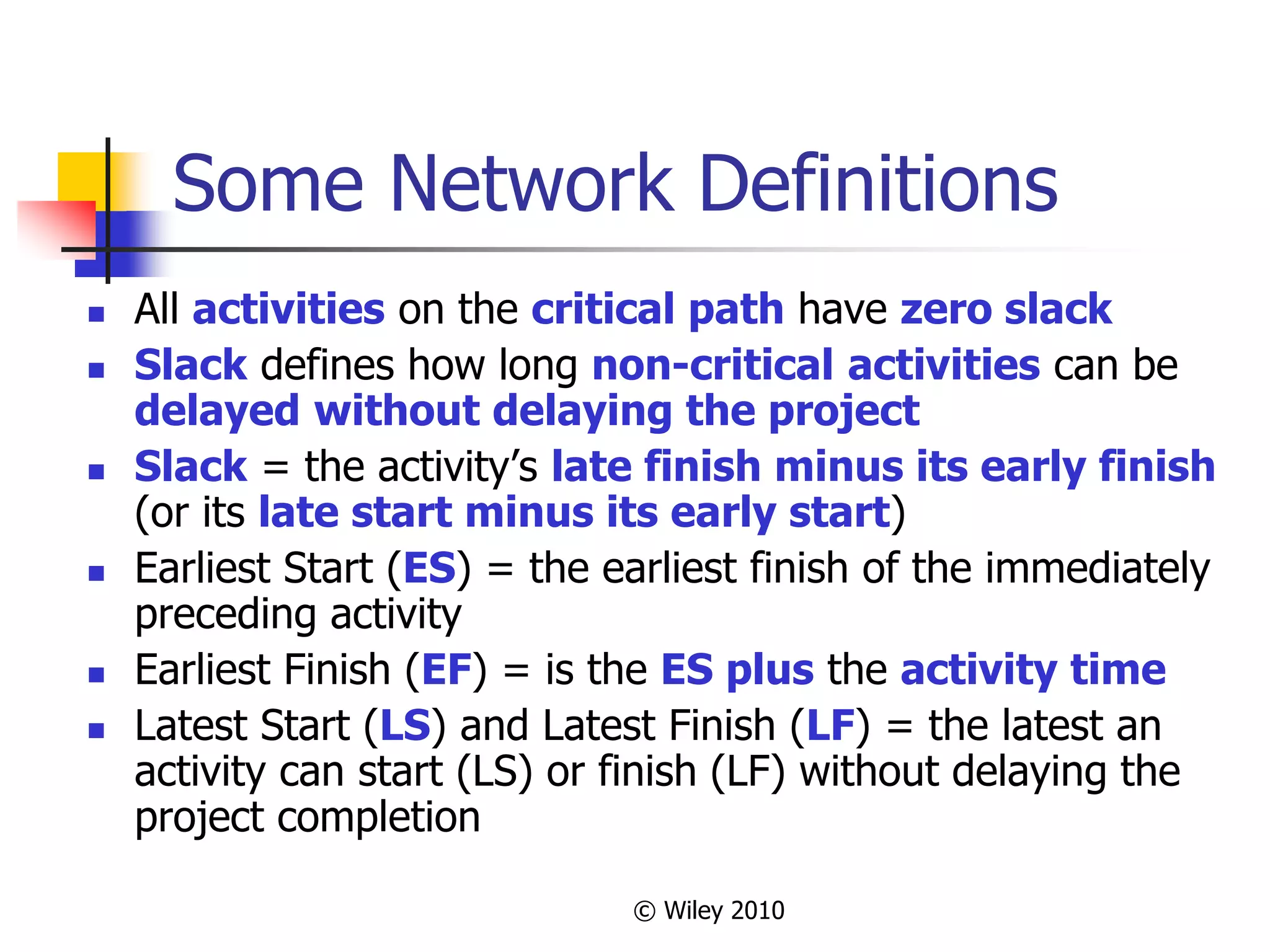
This document provides an overview of key concepts in project management. It describes the project life cycle, network planning techniques like PERT and CPM, identifying the critical path, calculating completion times, reducing project duration through crashing, and integrating project management across the organization. Specific techniques like adding buffers to critical chains in the critical chain approach are also summarized.
































![Homework Hints
Problems 16.1-2: Use CPM deterministic
model (A). [10 points]
Problems 16.4-8: Use CPM probabilistic
model (A). Use the AON diagram for 16.4.
[20 points]
Problems 16.9-10: Use CPM deterministic
model (A). Crash the project one week at
a time—find the lowest cost task to reduce.
Watch for the creation of additional critical
paths. [10 points]](https://image.slidesharecdn.com/opm101chapter160012-220818193019-919257a4/75/OPM101Chapter16_001-2-ppt-42-2048.jpg)