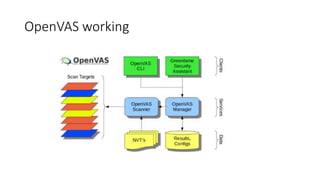
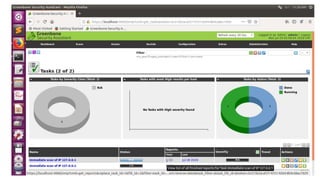
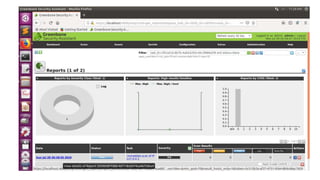
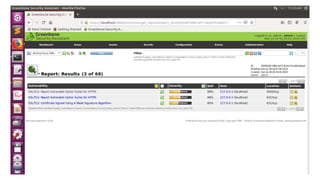
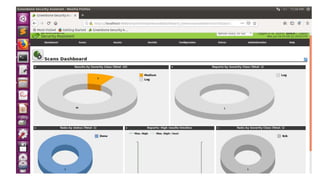
OpenVAS is an open source vulnerability scanning framework consisting of services and tools that allow for vulnerability scanning and management. It includes OpenVAS scanner which executes network vulnerability tests daily using over 530,000 plugins, and OpenVAS manager which controls scanners and the central SQL database where scan results are stored. The OpenVAS CLI allows users to create batch processes to control the OpenVAS manager.