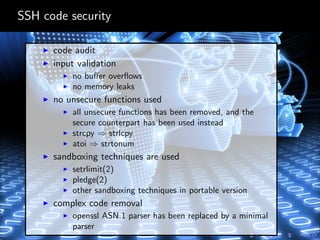
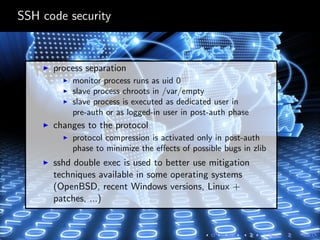
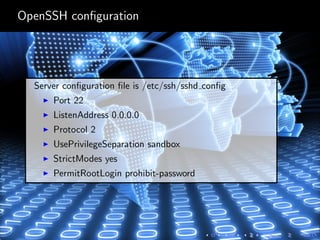
OpenSSH is a free SSH implementation used for secure communications and file transfers. It provides strong cryptography, authentication methods, and allows for features like port forwarding, X11 forwarding, and file transfers. OpenSSH uses a modular structure which separates the transport, authentication, and connection protocols. This makes it more secure than the original SSH version 1, especially against man-in-the-middle attacks. The OpenSSH codebase focuses on security through techniques like input validation, sandboxing, and process separation between the monitoring and slave processes.








![Using certificates
$ ssh-keygen
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in id_rsa.
Your public key has been saved in id_rsa.pub.
The key fingerprint is:
SHA256:uuNH/ECxy0i1T19EHXovdbfs3e134b4Yv++PpB1dPtc giovanni@ssh-test.org
The key’s randomart image is:
+---[RSA 2048]----+
| ..o.|
| o o .|
| . + o .+|
| . + . +.=|
| . =S+ . ..oo|
| ..* . . .=*|
| .. o .+oE|
| ... . ++==|
| .oo ..+*%|
+----[SHA256]-----+
$ ssh-add
Enter passphrase for /home/giovanni/.ssh/id_rsa:
Identity added: /home/giovanni/.ssh/id_rsa (/home/giovanni/.ssh/id_rsa)
$](https://image.slidesharecdn.com/slides-online-151128223907-lva1-app6891/85/OpenSSH-keep-your-secrets-safe-17-320.jpg)



![visual fingerprints
Using the visualfingerprint parameter in /etc/ssh/ssh config
you a visual fingerprint of the server you connect to will be
printed.
$ ssh shell.example.net
+---[RSA 2048]----+
| ..o.|
| o o .|
| . + o .+|
| . + . +.=|
| . =S+ . ..oo|
| ..* . . .=*|
| .. o .+oE|
| ... . ++==|
| .oo ..+*%|
+----[SHA256]-----+](https://image.slidesharecdn.com/slides-online-151128223907-lva1-app6891/85/OpenSSH-keep-your-secrets-safe-23-320.jpg)