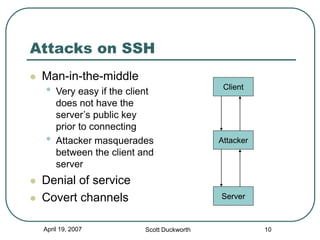
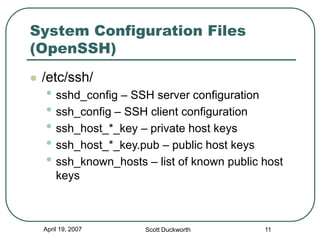
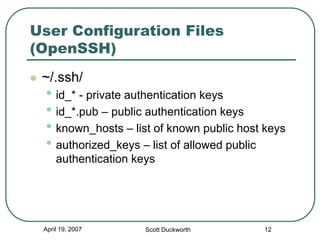
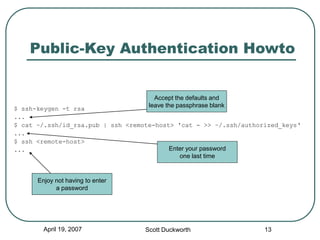
Secure Shell (SSH) is a protocol for secure remote login and other secure network services over an insecure network. It provides data confidentiality and integrity by using strong encryption and message authentication codes. SSH was created in 1995 in response to password sniffing attacks as a replacement for insecure remote shell protocols. Major implementations include OpenSSH, commonly used on UNIX systems, and PuTTY, a Windows client. SSH uses public-key cryptography for authentication and key exchange to secure connections between clients and servers.