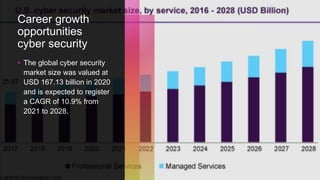
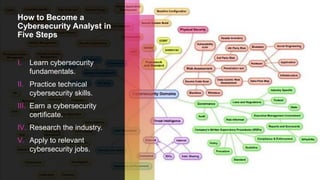
The document serves as a comprehensive guide on how to become a cybersecurity analyst, detailing necessary skills, training options, and career opportunities in the cybersecurity field. It outlines the critical responsibilities of a cybersecurity analyst, the importance of cybersecurity in protecting data, and the steps to enter the profession, including earning certifications and applying for jobs. Furthermore, the document discusses the benefits of cybersecurity for businesses and the expected salary range for cybersecurity analysts.