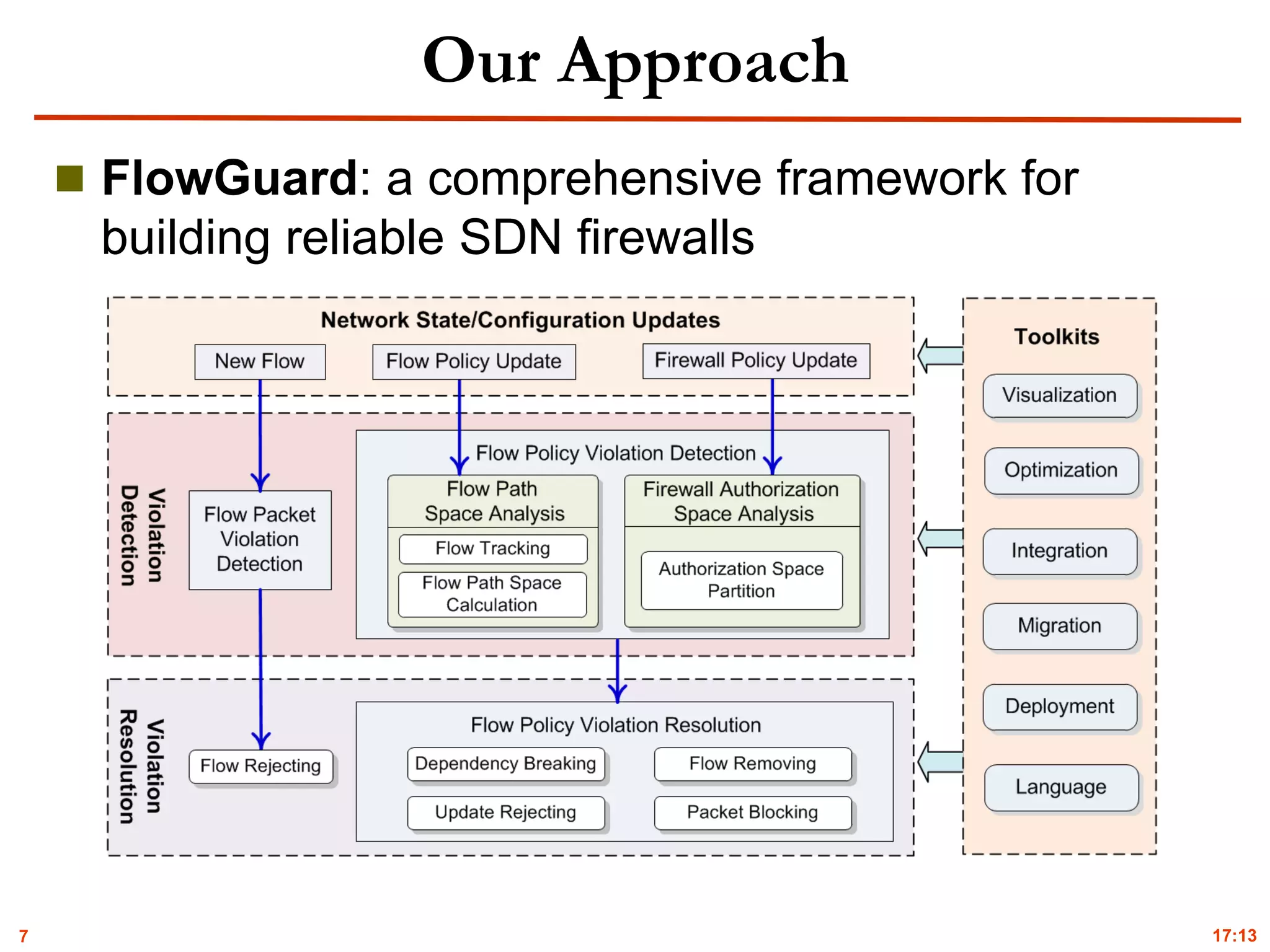
The document discusses the challenges and solutions in creating reliable Software-Defined Networking (SDN) firewalls, specifically addressing dynamic policy updates, indirect security violations, and architecture options. It presents FlowGuard, a comprehensive framework aimed at improving violation detection and resolution in SDN firewalls. The document also outlines the evaluation of FlowGuard in real-world network environments and ongoing work for further enhancement of SDN firewalls.



![6
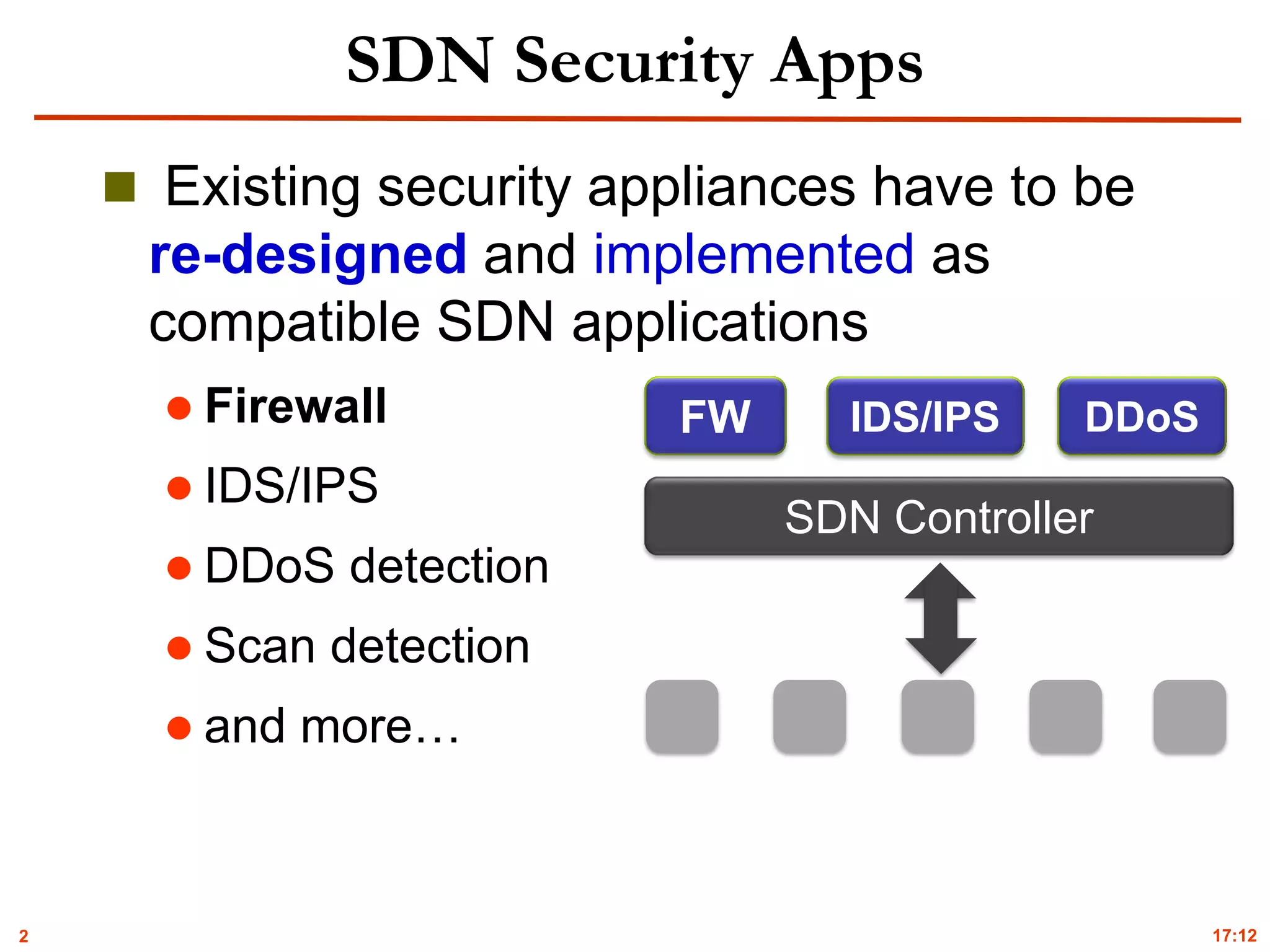
State Of The Art
SDN Firewall App
Built-in firewall application in Floodlight
Limited to check flow packet violations and unable to examine flow
policy violations
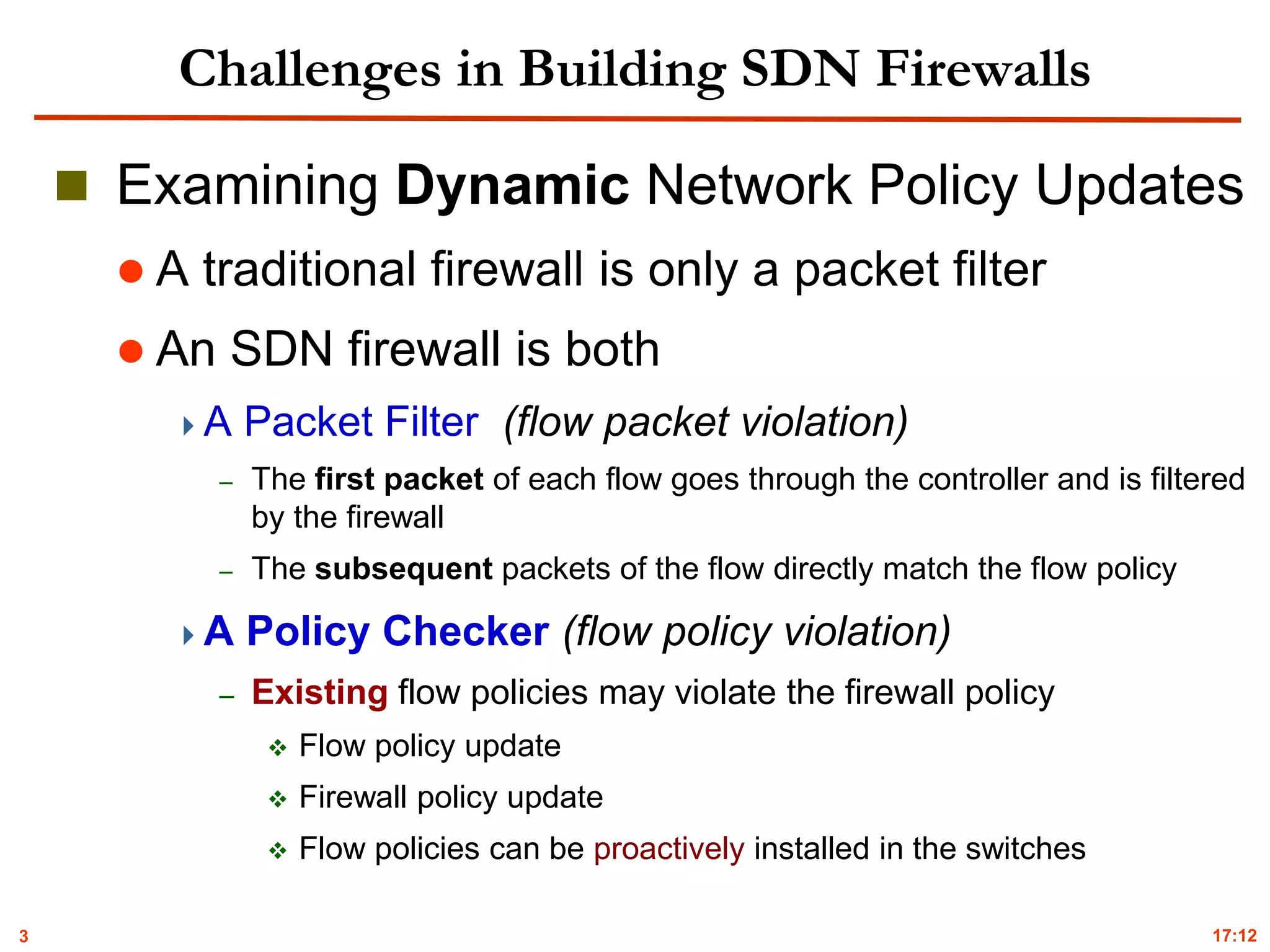
Policy Conflict Detection and Resolution
VeriFlow [Khurshid’13] and NetPlumber [Kazemian’13]
Lack of automatic, effective and real-time violation resolution
Pyretic [Monsanto’13]
Cannot discover and resolve indirect security violations
FortNOX [Porras’12]
Only conducts pairwise conflict analysis without considering rule
dependencies in flow tables and firewall policies
17:13](https://image.slidesharecdn.com/ons2014-hongxinhu-researchtrackpart1-150323102648-conversion-gate01/75/SFA-Stateful-Forwarding-Abstraction-in-SDN-Data-Plane-8-2048.jpg)
![8
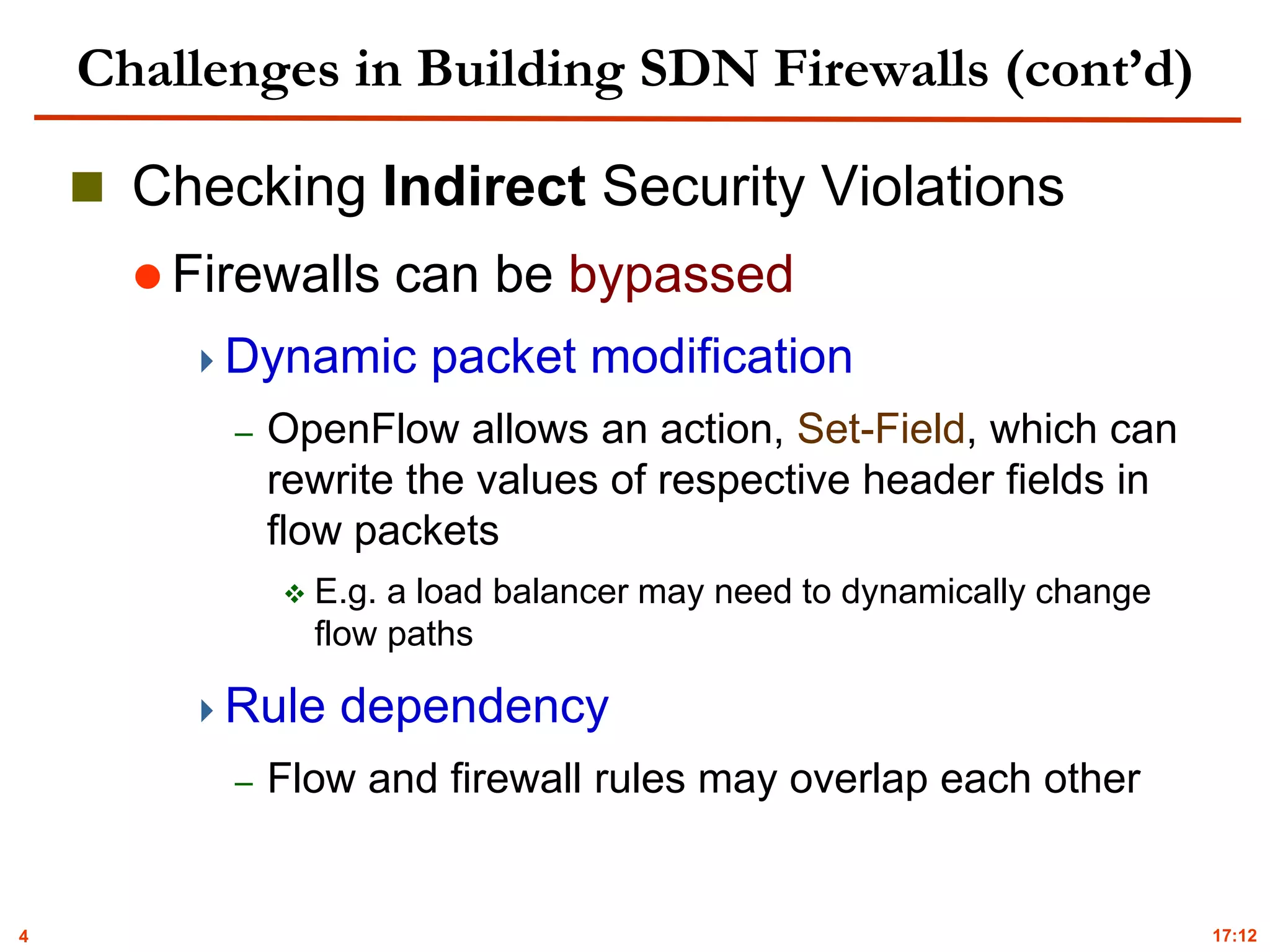
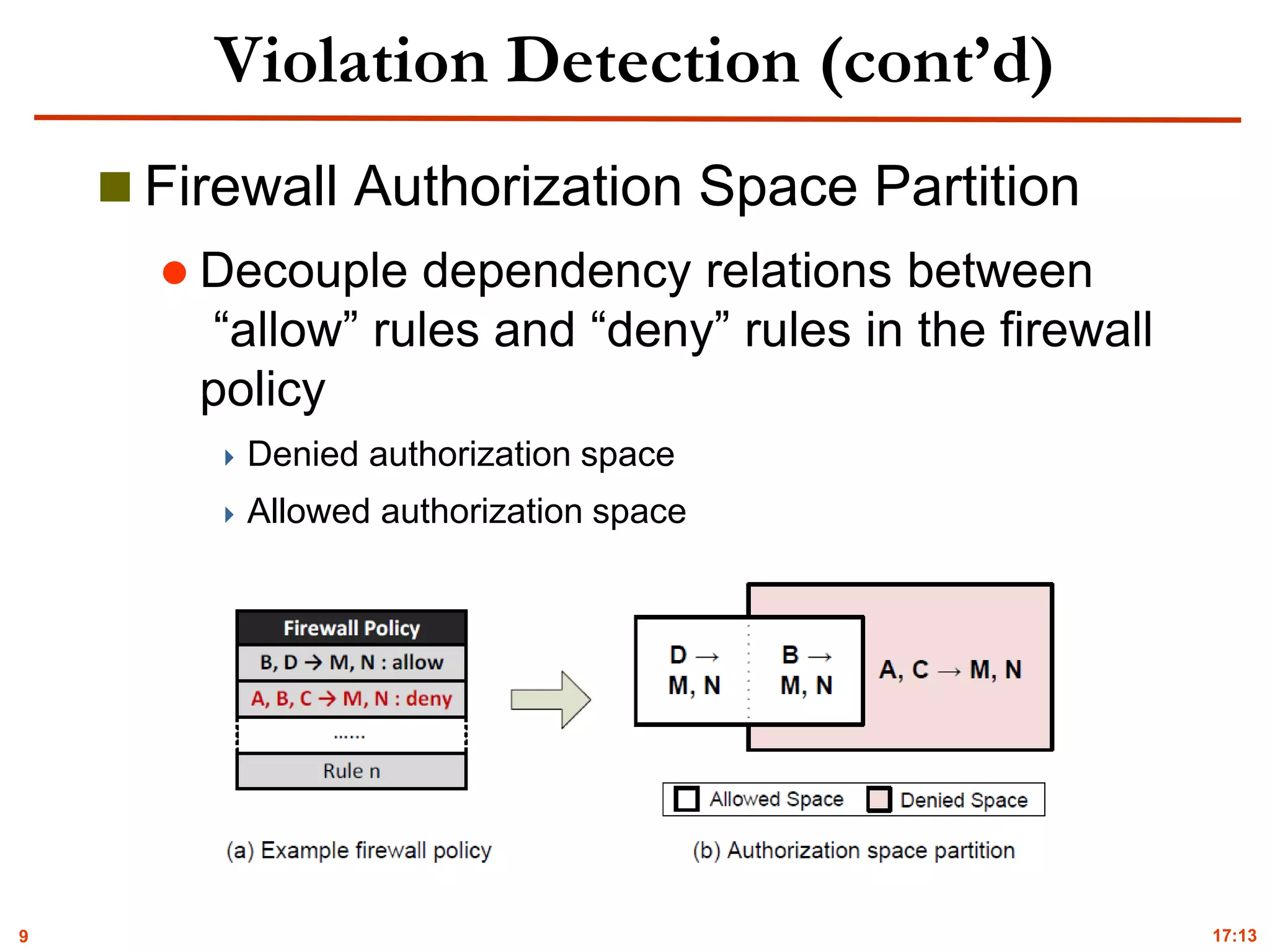
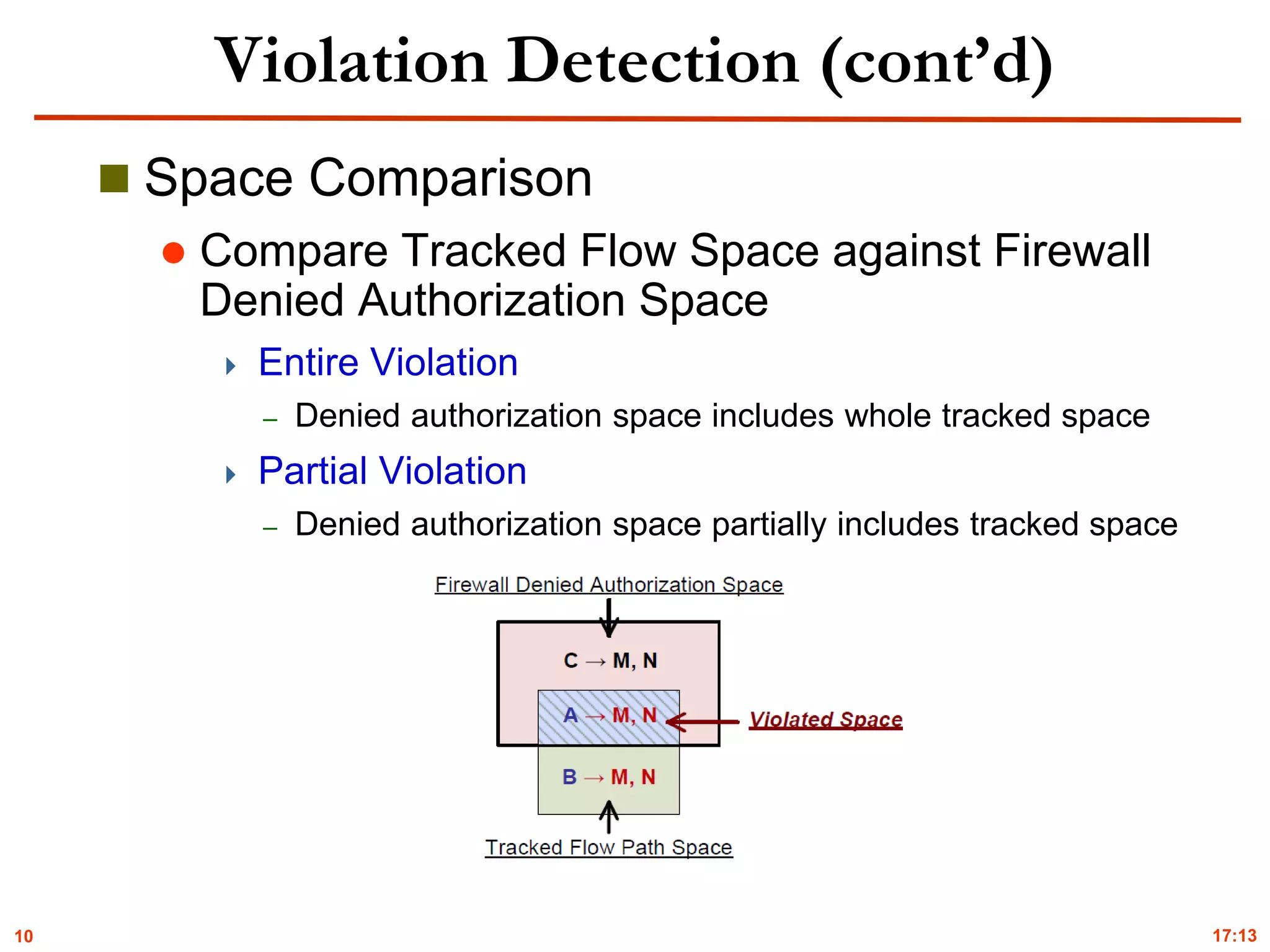
Violation Detection
Flow Path Space Analysis
Flow tracking (NetPlumber [Kazemian’13])
Dynamic packet modification
Rule dependency
Flow path space calculation
Incoming space
Outgoing space
Tracked space
17:13](https://image.slidesharecdn.com/ons2014-hongxinhu-researchtrackpart1-150323102648-conversion-gate01/75/SFA-Stateful-Forwarding-Abstraction-in-SDN-Data-Plane-10-2048.jpg)
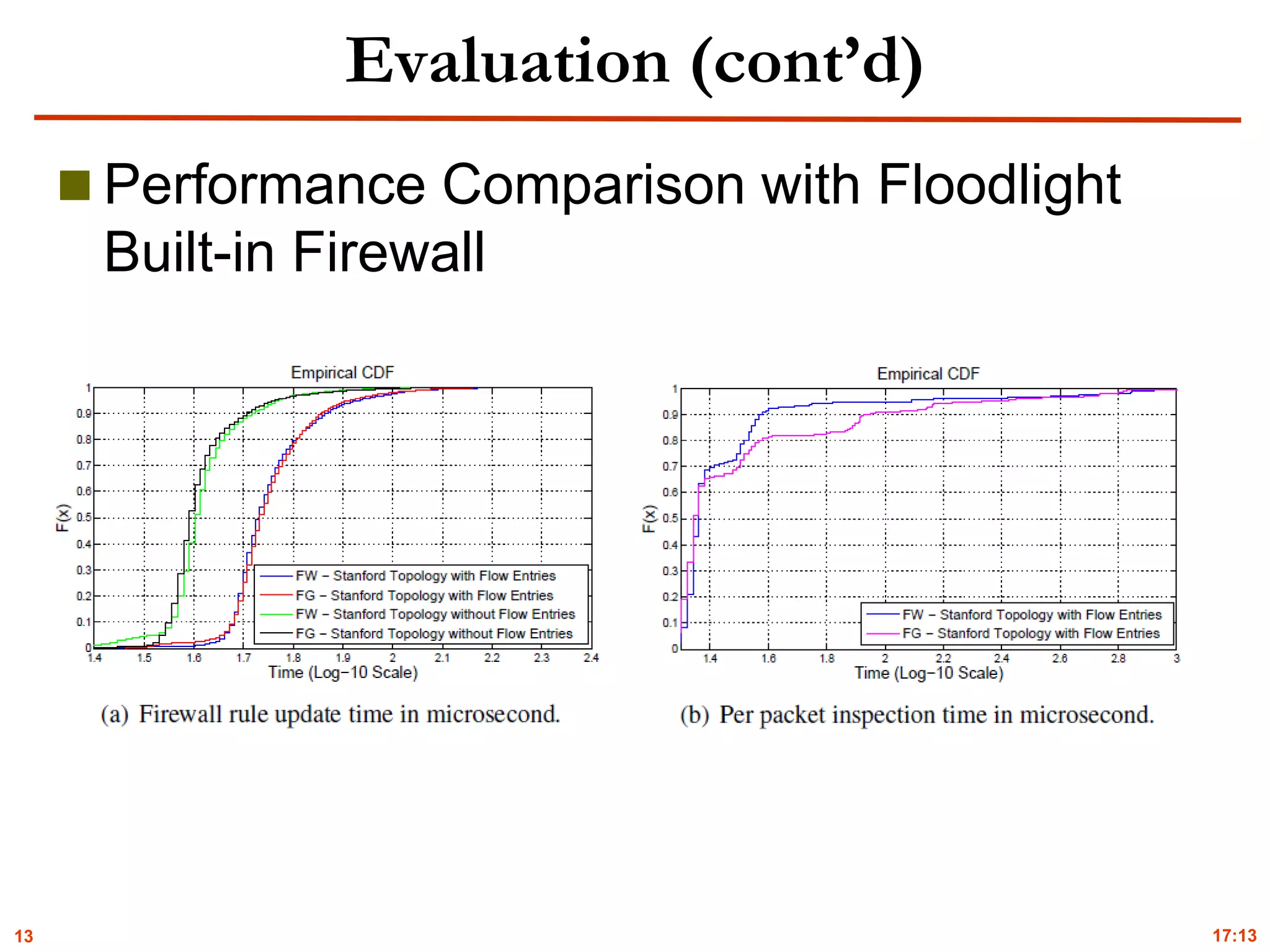
![12
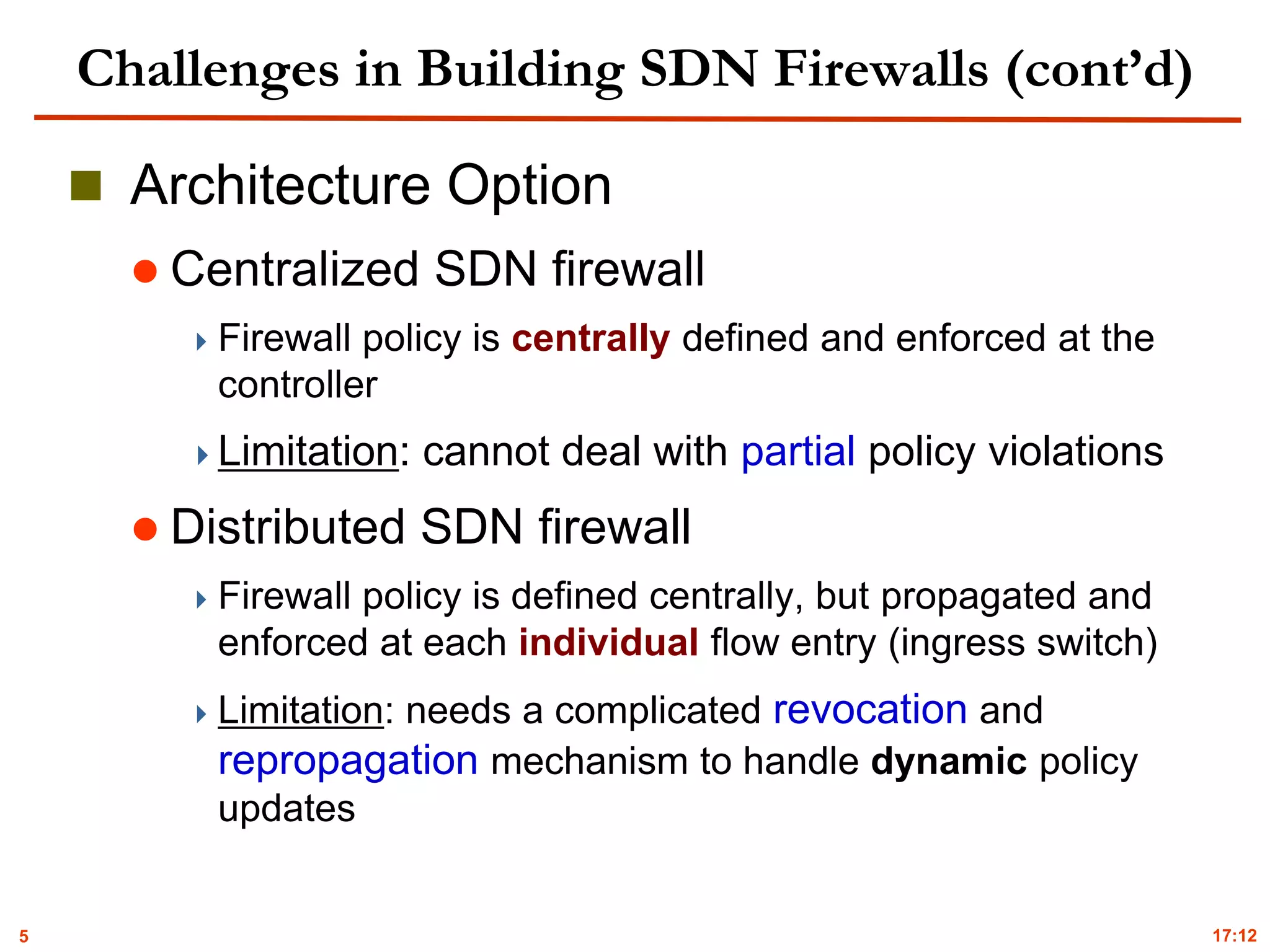
Implementation & Evaluation
Prototype of FlowGuard
Floodlight V 0.90
Evolution Environment
Real-world network topology
Stanford backbone network [kazemian’13]
Mininet 2.0
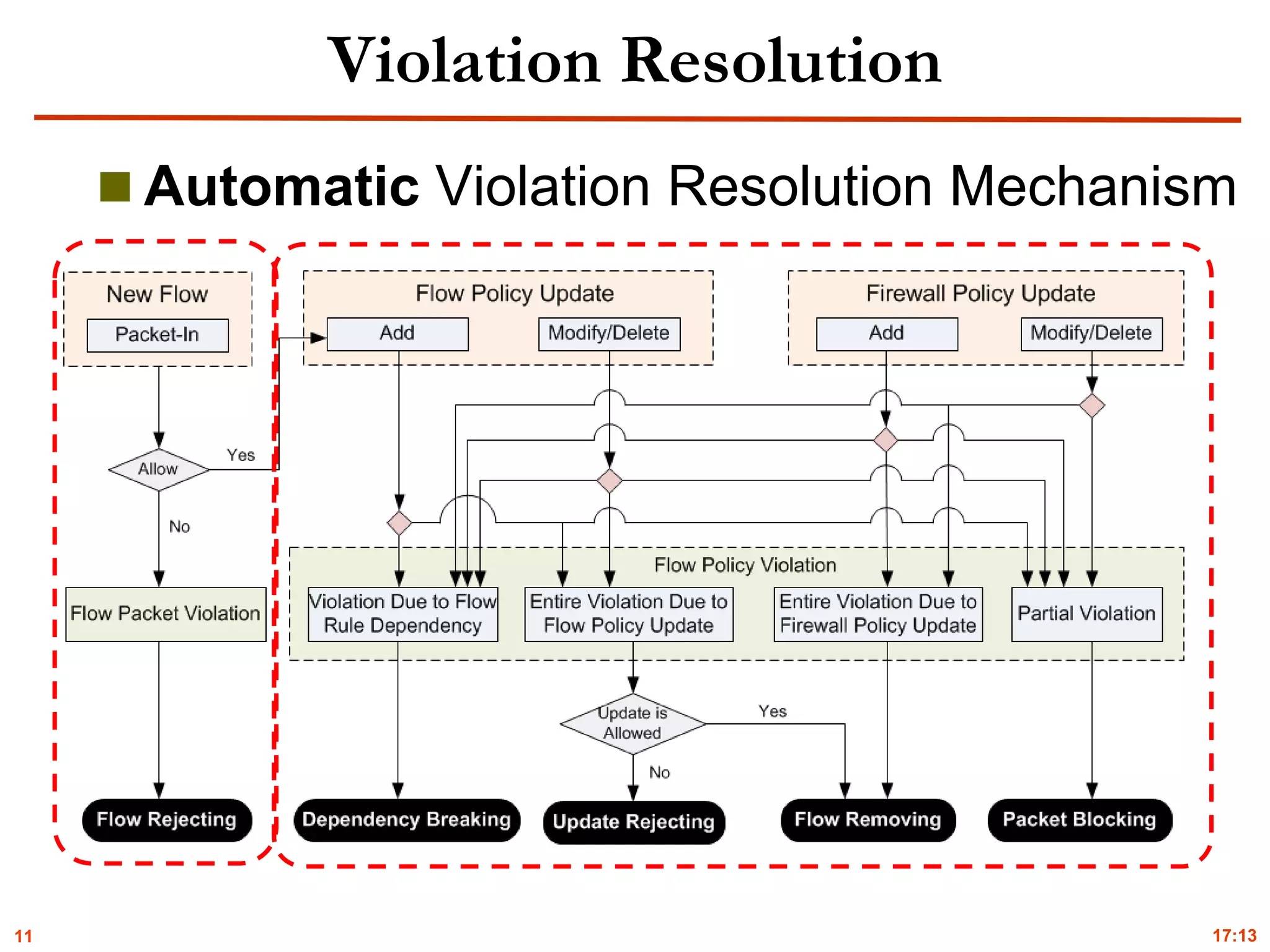
Violation Detection and Resolution
Table 1: Detection and resolution elapsed time (ms) for different resolution strategies
17:13](https://image.slidesharecdn.com/ons2014-hongxinhu-researchtrackpart1-150323102648-conversion-gate01/75/SFA-Stateful-Forwarding-Abstraction-in-SDN-Data-Plane-14-2048.jpg)

![16
Challenges in Building SDN Firewalls (cont’d)
Stateful Monitoring
Only inspects the first packet of each flow
Limited access to packet-level information in the
controller [Sajad13]
Forwarding plane is almost stateless [Hao13]
17:13](https://image.slidesharecdn.com/ons2014-hongxinhu-researchtrackpart1-150323102648-conversion-gate01/75/SFA-Stateful-Forwarding-Abstraction-in-SDN-Data-Plane-18-2048.jpg)