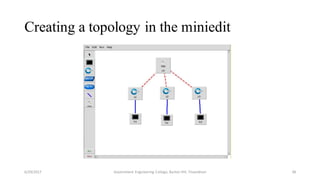
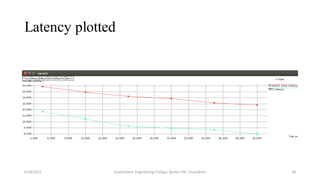
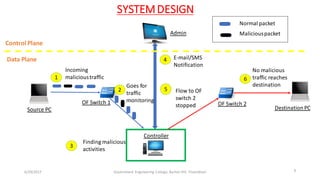
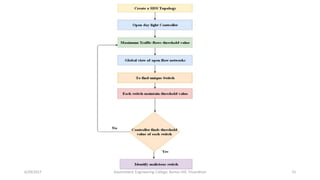
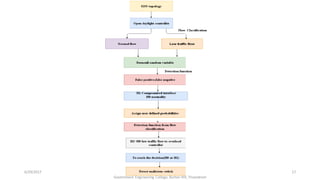
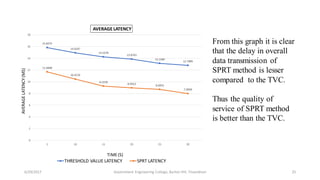
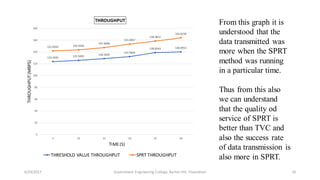
The document discusses a proposed system for detecting malicious switches and DDoS attacks in Software Defined Networking (SDN) by using a statistical approach known as the Sequential Probability Ratio Test (SPRT). It contrasts this method with existing threshold value control (TVC) techniques which are vulnerable to various attacks. The results demonstrate that the SPRT method provides better performance in terms of lower latency and higher throughput compared to TVC, concluding that SPRT is a more effective solution for malicious traffic detection in SDN environments.
![TRAFFIC-BASED MALICIOUS
SWITCH And DDoS DETECTION
IN SOFTWARE DEFINED
NETWORKING
By:
Akshaya Arunan
Roll No: 1
MTech [IT]
Guided By:
Simi Krishna K.R
AssistantProfessor[IT]](https://image.slidesharecdn.com/finalprestn-180306083827/75/Traffic-Based-Malicious-Switch-and-DDoS-Detection-in-Software-Defined-Network-1-2048.jpg)

![INTRODUCTION
Software Defined Network [SDN]:
• Complexity of the network shifts towards the controller.
• Brings simplicity and abstraction to the network operator.
• SDN decouples the control plane from the data plane.
• Migrates to a logically centralized software-based network controller.
• Controller is network-aware.
• Dynamic updating of traffic rules.
6/29/2017 3Government Engineering College, Barton Hill, Trivandrum](https://image.slidesharecdn.com/finalprestn-180306083827/85/Traffic-Based-Malicious-Switch-and-DDoS-Detection-in-Software-Defined-Network-3-320.jpg)
![SDN Architecture [3]
6/29/2017 Government Engineering College, Barton Hill, Trivandrum 4](https://image.slidesharecdn.com/finalprestn-180306083827/85/Traffic-Based-Malicious-Switch-and-DDoS-Detection-in-Software-Defined-Network-4-320.jpg)

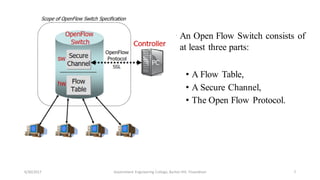
![OpenFlow [6]:
• Communication protocol
• A protocol - SDN controller communication with the network devices.
• Standardizes the communication - a software-based controller and switches - Open
Flow channel.
• An OpenFlow-compliant switch exposes an abstraction of its forwarding table to
the Open Flow controller.
6/29/2017 6Government Engineering College, Barton Hill, Trivandrum](https://image.slidesharecdn.com/finalprestn-180306083827/85/Traffic-Based-Malicious-Switch-and-DDoS-Detection-in-Software-Defined-Network-6-320.jpg)







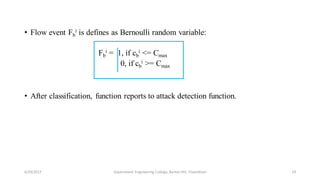
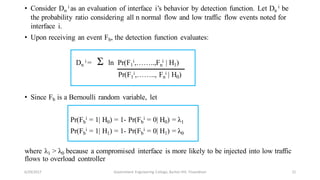
![Flow Classification[2]:
• Normal flow
• Low traffic flow
Assignments:
• Pr - Probability
• Fb
i – Flow event corresponding to sequence of flows
• xi – sequence of flows
• cb
i - packet counts of flows in a flow event F
• C – Threshold value ( can be obtained and recalibrated)
• b – Observations (1,2,…, n)
• H – Hypothesis
• α – False positive
• β – False negative
• D – Detection function
6/29/2017 18Government Engineering College, Barton Hill, Trivandrum](https://image.slidesharecdn.com/finalprestn-180306083827/85/Traffic-Based-Malicious-Switch-and-DDoS-Detection-in-Software-Defined-Network-18-320.jpg)





![FUTURE WORKS
• Implementation of a security method like OpenSec[4] can be implemented as a
further protection in SDN.
• Various types networks (tree, hierarchy) can be used to implement this method and
an comparison can be done to find the better network performance.
6/29/2017 28Government Engineering College, Barton Hill, Trivandrum](https://image.slidesharecdn.com/finalprestn-180306083827/85/Traffic-Based-Malicious-Switch-and-DDoS-Detection-in-Software-Defined-Network-28-320.jpg)