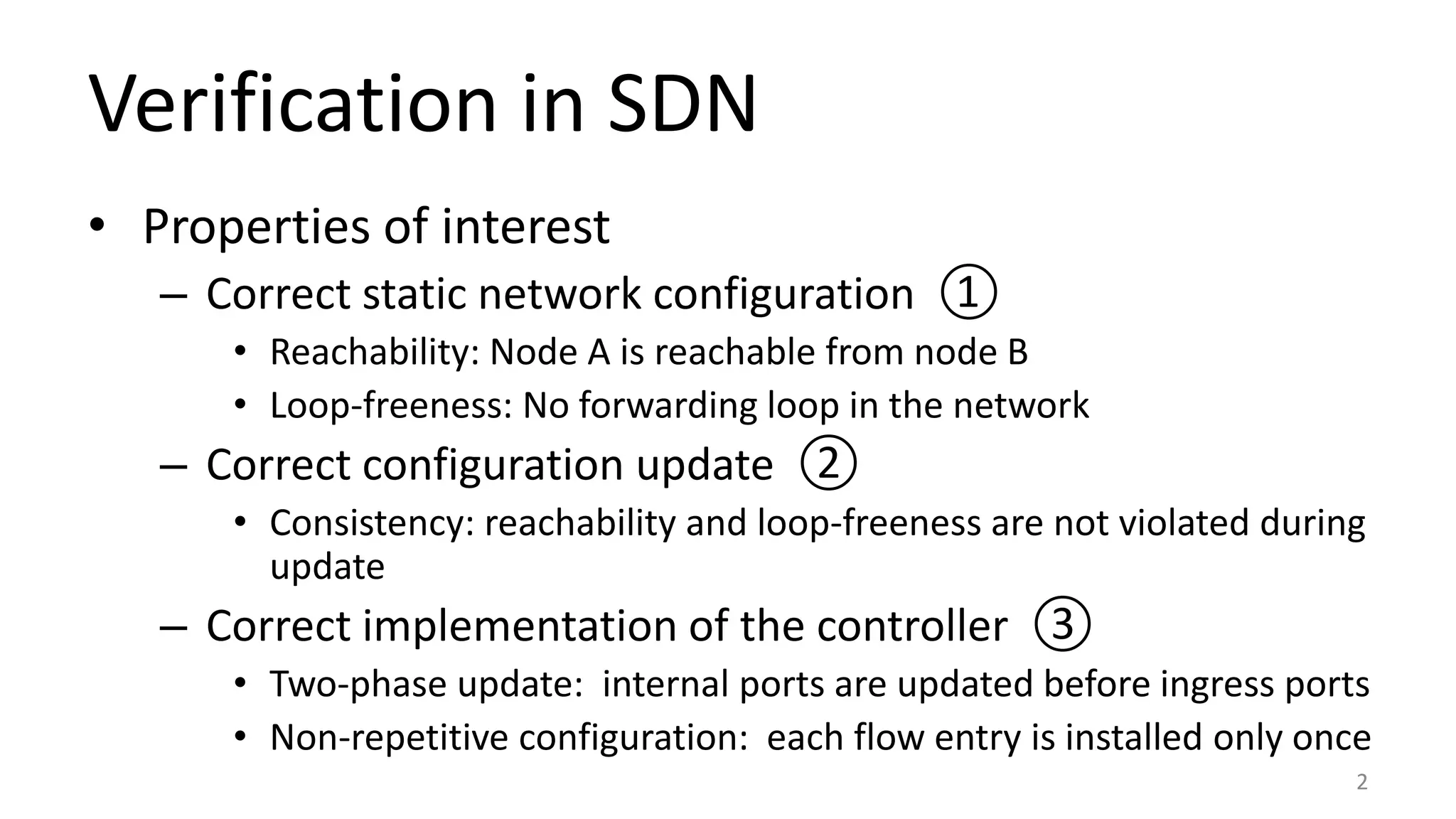
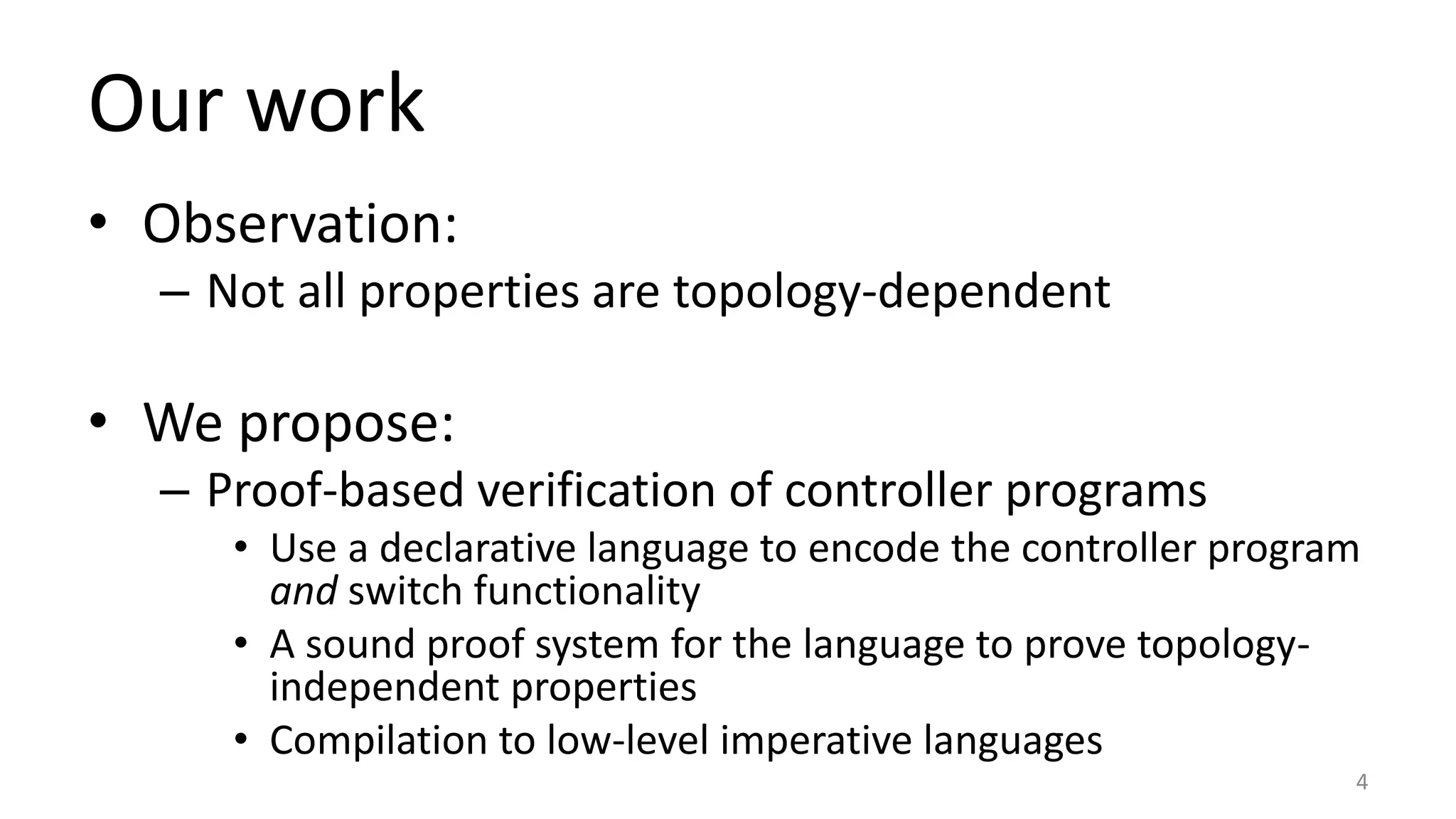
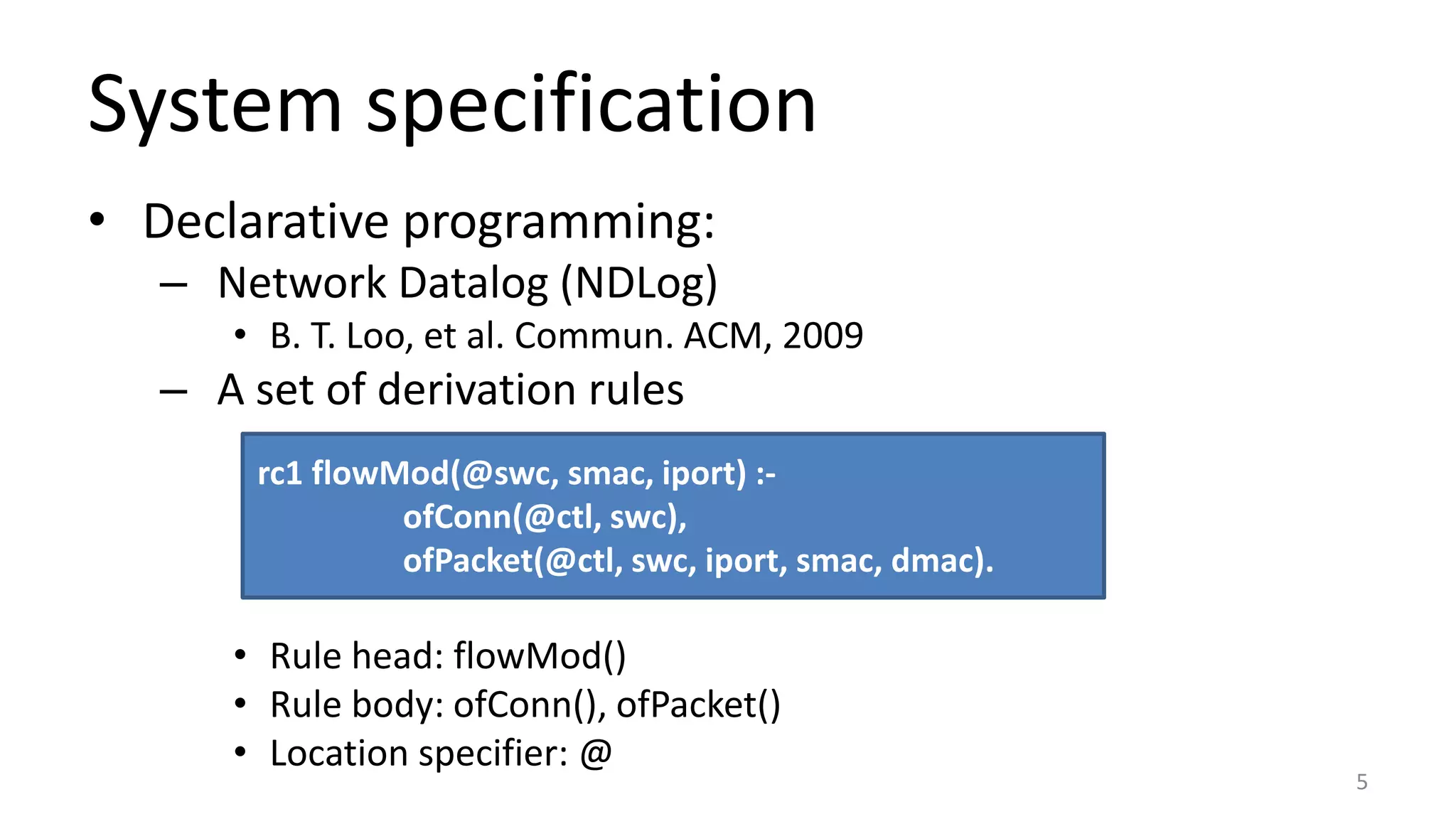
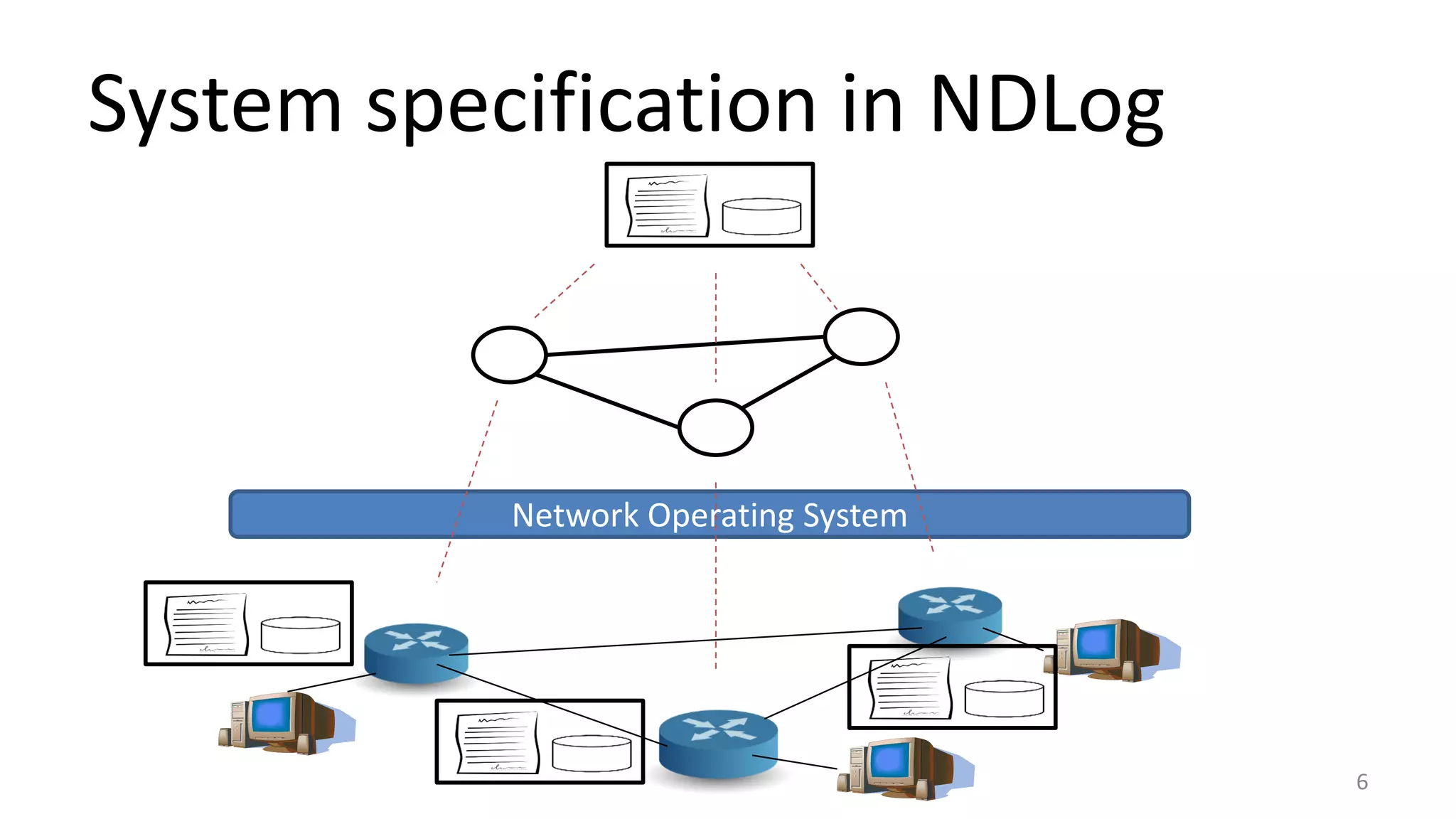
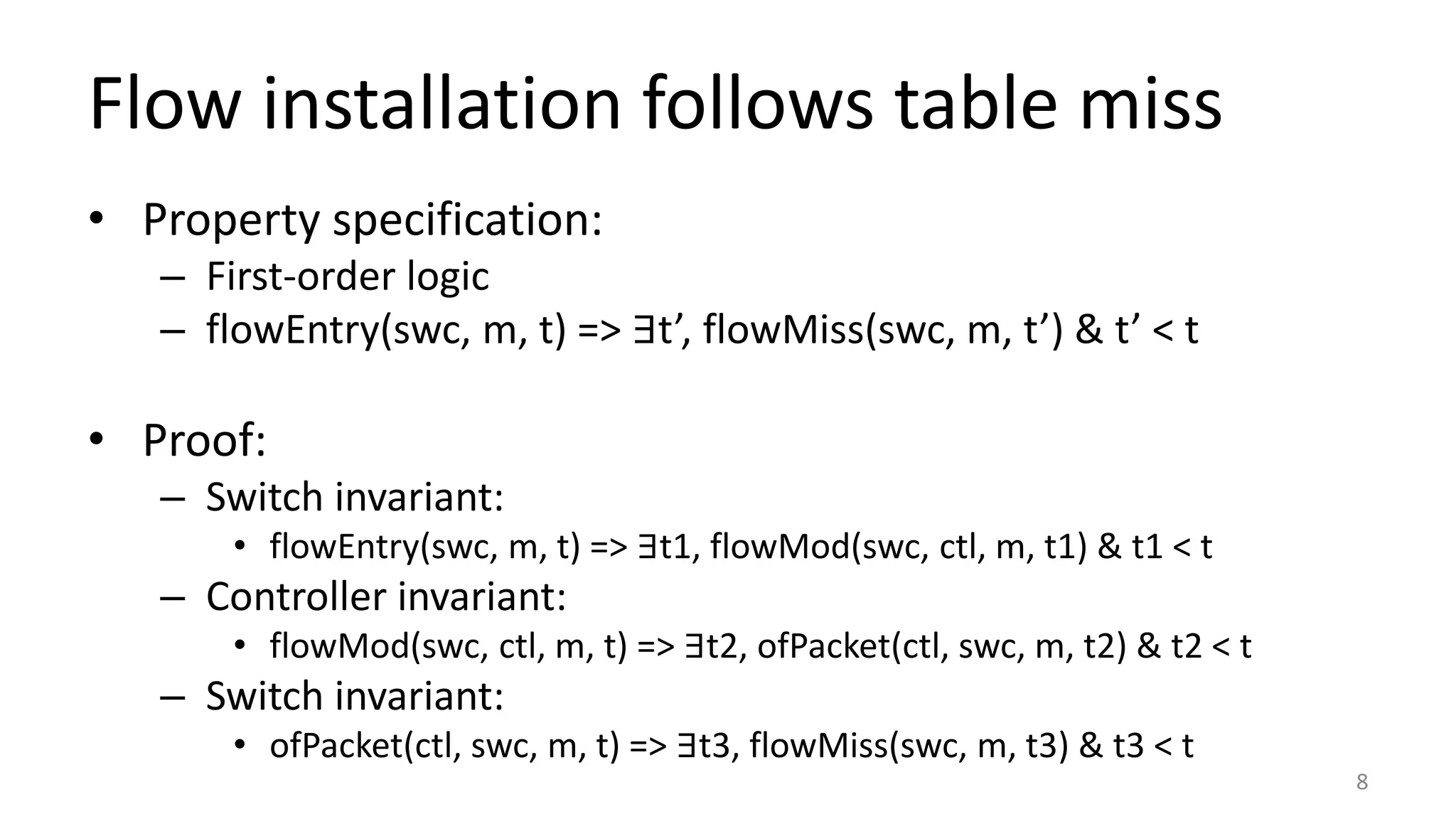
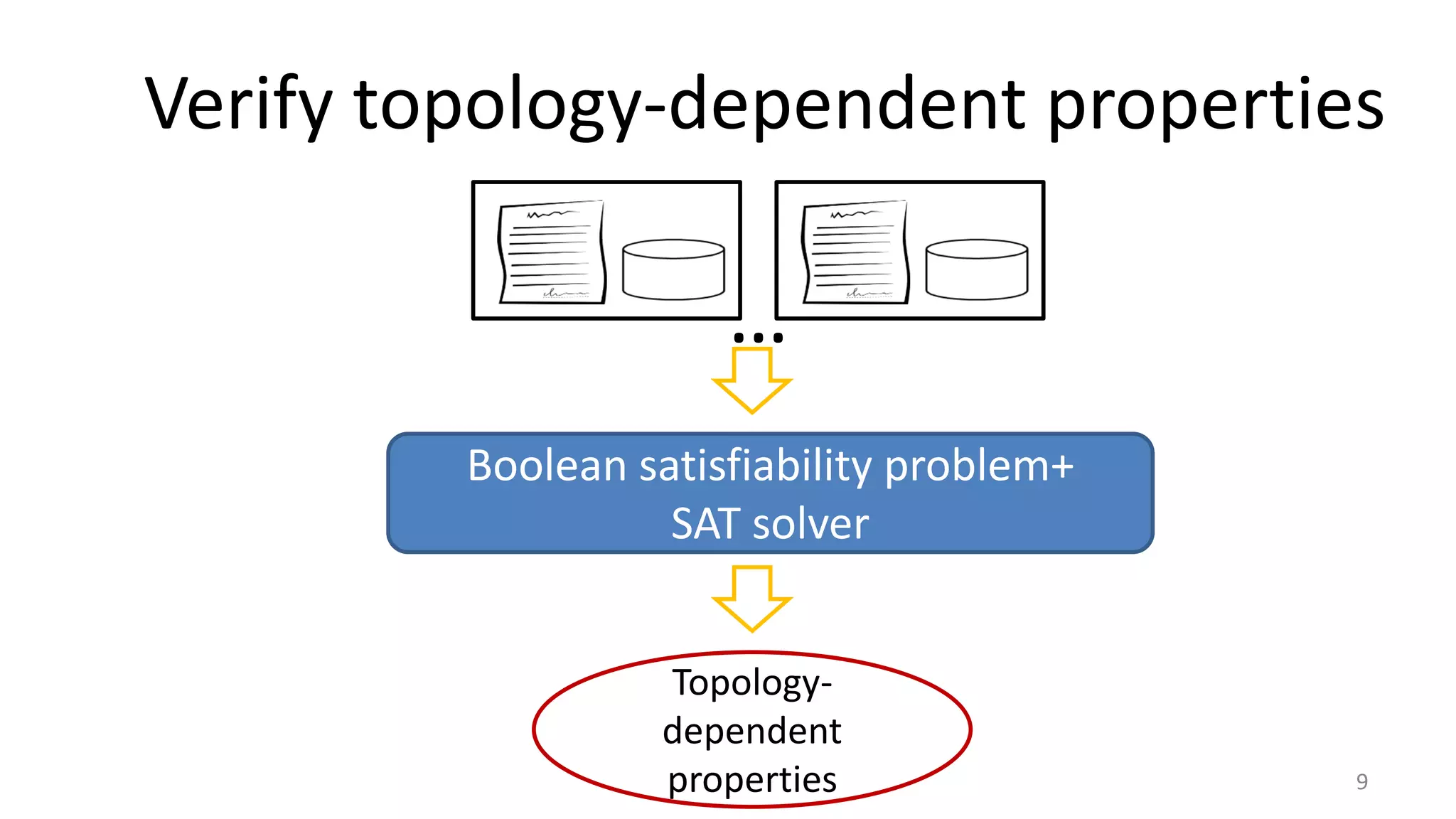
The document discusses proof-based verification methods for Software Defined Networks (SDN), focusing on properties like reachability and loop-freeness during configuration updates. The authors propose a declarative language, Network Datalog (NDLOG), for encoding controller programs and verifying topology-independent properties through a sound proof system. Current challenges include network state explosion and the need for proof automation to handle additional security properties.