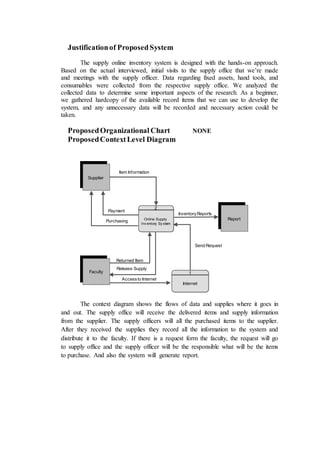
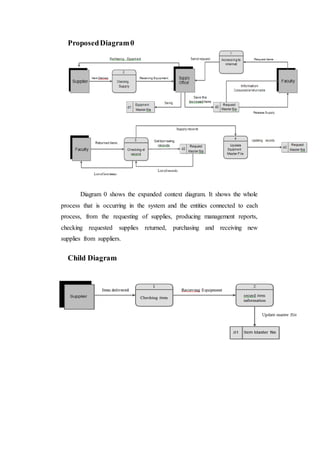
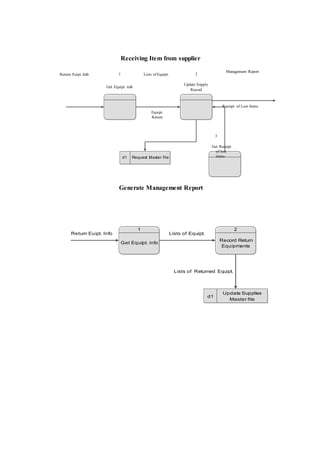
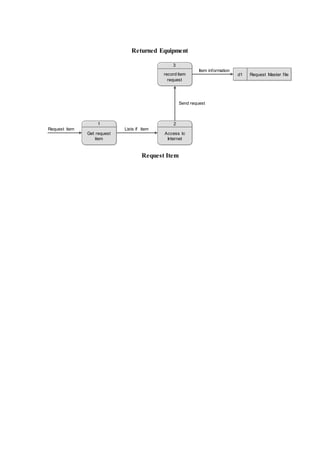
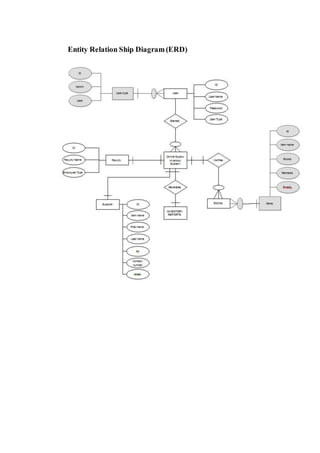
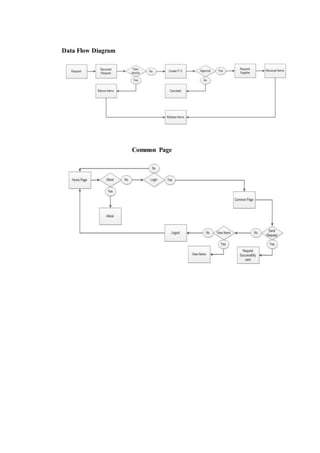
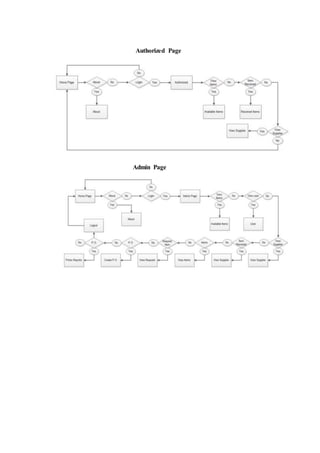
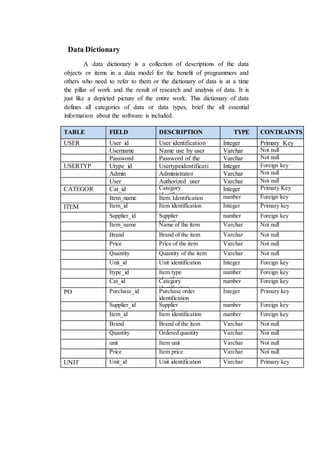
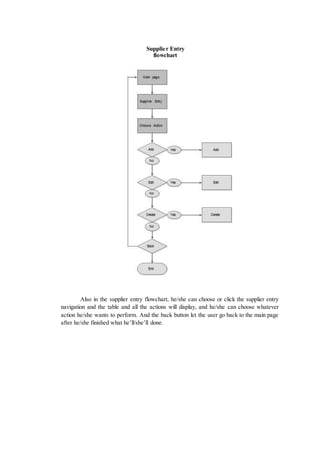
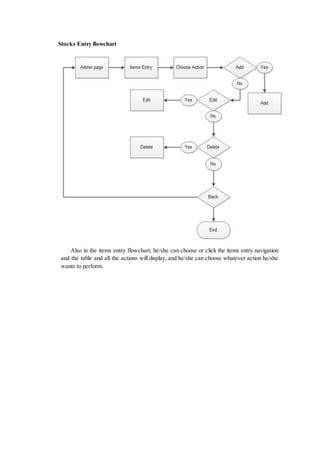
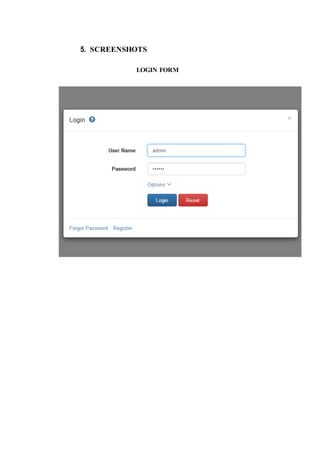
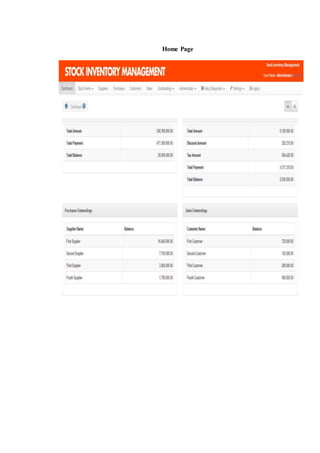
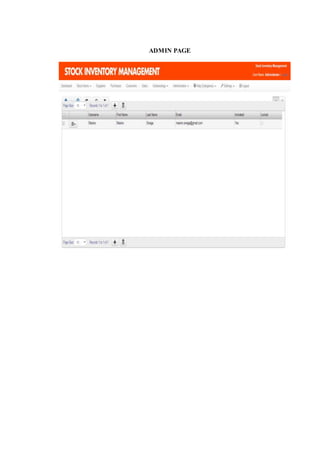
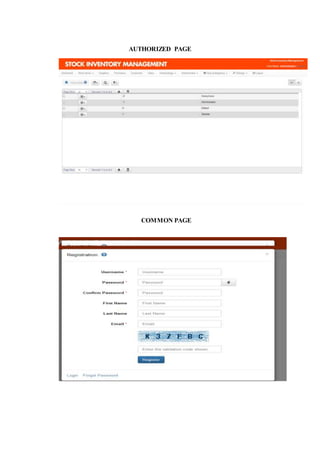
The document outlines the methodology for developing an inventory management system for CBST External Studies Center Supply Office. It discusses the functional and non-functional requirements including performance, information, economic, control, efficiency and service requirements. It also defines the business and technology constraints of the proposed system. The system will automate the inventory processes to track inventory levels in real-time and generate reports. It will allow authorized users to view inventory information through a secure login. The study aims to enhance the inventory management processes at the Supply Office.





























![// Page URL
function PageUrl() {
$PageUrl = ew_CurrentPage() . "?";
return $PageUrl;
}
// Message
function getMessage() {
return
@$_SESSION[EW_SESSION_MESSAGE];
}](https://image.slidesharecdn.com/onlinesupplyinventorysystem-170421172657/85/Online-supply-inventory-system-52-320.jpg)
![function setMessage($v) {
ew_AddMessage($_SESSION[EW_SESSION_MESSA
GE], $v);
}
function getFailureMessage() {
return
@$_SESSION[EW_SESSION_FAILURE_MESSAGE];
}
function setFailureMessage($v) {](https://image.slidesharecdn.com/onlinesupplyinventorysystem-170421172657/85/Online-supply-inventory-system-53-320.jpg)
![ew_AddMessage($_SESSION[EW_SESSION_FAILUR
E_MESSAGE], $v);
}
function getSuccessMessage() {
return
@$_SESSION[EW_SESSION_SUCCESS_MESSAGE];
}
function setSuccessMessage($v) {](https://image.slidesharecdn.com/onlinesupplyinventorysystem-170421172657/85/Online-supply-inventory-system-54-320.jpg)
![ew_AddMessage($_SESSION[EW_SESSION_SUCCES
S_MESSAGE], $v);
}
function getWarningMessage() {
return
@$_SESSION[EW_SESSION_WARNING_MESSAGE];
}
function setWarningMessage($v) {
ew_AddMessage($_SESSION[EW_SESSION_WARNI](https://image.slidesharecdn.com/onlinesupplyinventorysystem-170421172657/85/Online-supply-inventory-system-55-320.jpg)
![NG_MESSAGE], $v);
}
// Methods to clear message
function ClearMessage() {
$_SESSION[EW_SESSION_MESSAGE] = "";
}
function ClearFailureMessage() {
$_SESSION[EW_SESSION_FAILURE_MESSAGE] =
"";](https://image.slidesharecdn.com/onlinesupplyinventorysystem-170421172657/85/Online-supply-inventory-system-56-320.jpg)
![}
function ClearSuccessMessage() {
$_SESSION[EW_SESSION_SUCCESS_MESSAGE] =
"";
}
function ClearWarningMessage() {
$_SESSION[EW_SESSION_WARNING_MESSAGE]
= "";](https://image.slidesharecdn.com/onlinesupplyinventorysystem-170421172657/85/Online-supply-inventory-system-57-320.jpg)
![}
function ClearMessages() {
$_SESSION[EW_SESSION_MESSAGE] = "";
$_SESSION[EW_SESSION_FAILURE_MESSAGE] =
"";
$_SESSION[EW_SESSION_SUCCESS_MESSAGE] =
"";
$_SESSION[EW_SESSION_WARNING_MESSAGE]](https://image.slidesharecdn.com/onlinesupplyinventorysystem-170421172657/85/Online-supply-inventory-system-58-320.jpg)

![display
if (!$hidden)
$sMessage = "<button
type="button" class="close" data-
dismiss="alert">×</button>" . $sMessage;
$html .= "<div class="alert alert-info
ewInfo">" . $sMessage . "</div>";
$_SESSION[EW_SESSION_MESSAGE]
= ""; // Clear message in Session
}
// Warning message](https://image.slidesharecdn.com/onlinesupplyinventorysystem-170421172657/85/Online-supply-inventory-system-60-320.jpg)

![$_SESSION[EW_SESSION_WARNING_MESSAGE]
= ""; // Clear message in Session
}
// Success message
$sSuccessMessage = $this->getSuccessMessage();
$this->Message_Showing($sSuccessMessage,
"success");
if ($sSuccessMessage <> "") { // Message in
Session, display
if (!$hidden)](https://image.slidesharecdn.com/onlinesupplyinventorysystem-170421172657/85/Online-supply-inventory-system-62-320.jpg)
![$sSuccessMessage = "<button
type="button" class="close" data-
dismiss="alert">×</button>" . $sSuccessMessage;
$html .= "<div class="alert alert-success
ewSuccess">" . $sSuccessMessage . "</div>";
$_SESSION[EW_SESSION_SUCCESS_MESSAGE] =
""; // Clear message in Session
}
// Failure message
$sErrorMessage = $this->getFailureMessage();](https://image.slidesharecdn.com/onlinesupplyinventorysystem-170421172657/85/Online-supply-inventory-system-63-320.jpg)
![$this->Message_Showing($sErrorMessage,
"failure");
if ($sErrorMessage <> "") { // Message in
Session, display
if (!$hidden)
$sErrorMessage = "<button
type="button" class="close" data-
dismiss="alert">×</button>" . $sErrorMessage;
$html .= "<div class="alert alert-danger
ewError">" . $sErrorMessage . "</div>";
$_SESSION[EW_SESSION_FAILURE_MESSAGE] =](https://image.slidesharecdn.com/onlinesupplyinventorysystem-170421172657/85/Online-supply-inventory-system-64-320.jpg)

![// Valid Post
function ValidPost() {
if (!$this->CheckToken || !ew_IsHttpPost())
return TRUE;
if (!isset($_POST[EW_TOKEN_NAME]))
return FALSE;
$fn = $this->CheckTokenFn;
if (is_callable($fn))
return
$fn($_POST[EW_TOKEN_NAME], $this->TokenTimeout);
return FALSE;
}](https://image.slidesharecdn.com/onlinesupplyinventorysystem-170421172657/85/Online-supply-inventory-system-66-320.jpg)

![}
//
// Page class constructor
//
function __construct() {
global $conn, $Language;
global $UserTable, $UserTableConn;
$GLOBALS["Page"] = &$this;
$this->TokenTimeout =
ew_SessionTimeoutTime();](https://image.slidesharecdn.com/onlinesupplyinventorysystem-170421172657/85/Online-supply-inventory-system-68-320.jpg)
![// Language object
if (!isset($Language)) $Language = new
cLanguage();
// Page ID
if (!defined("EW_PAGE_ID"))
define("EW_PAGE_ID", 'default',
TRUE);
// Start timer
if (!isset($GLOBALS["gTimer"]))
$GLOBALS["gTimer"] = new cTimer();](https://image.slidesharecdn.com/onlinesupplyinventorysystem-170421172657/85/Online-supply-inventory-system-69-320.jpg)


























