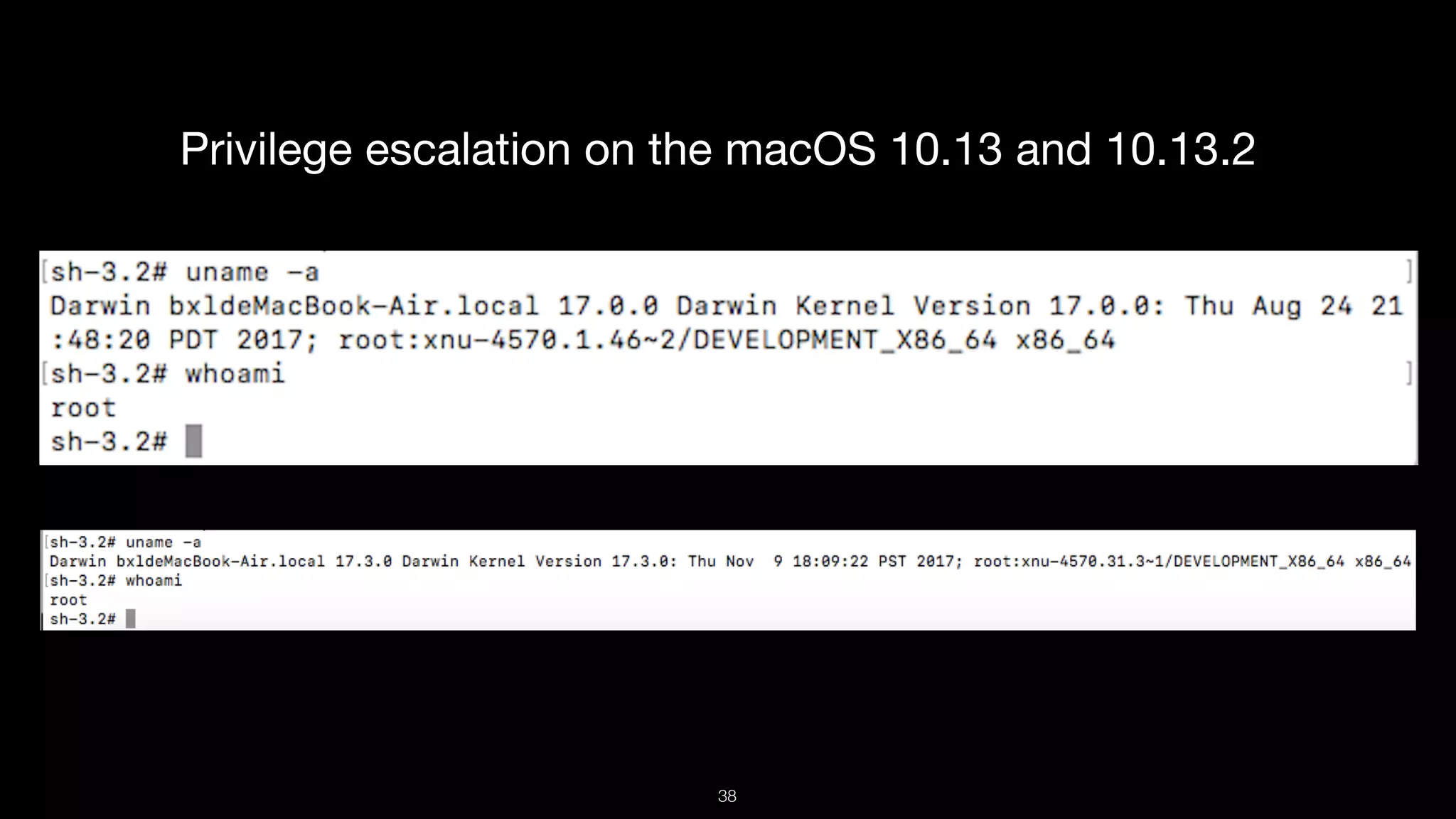
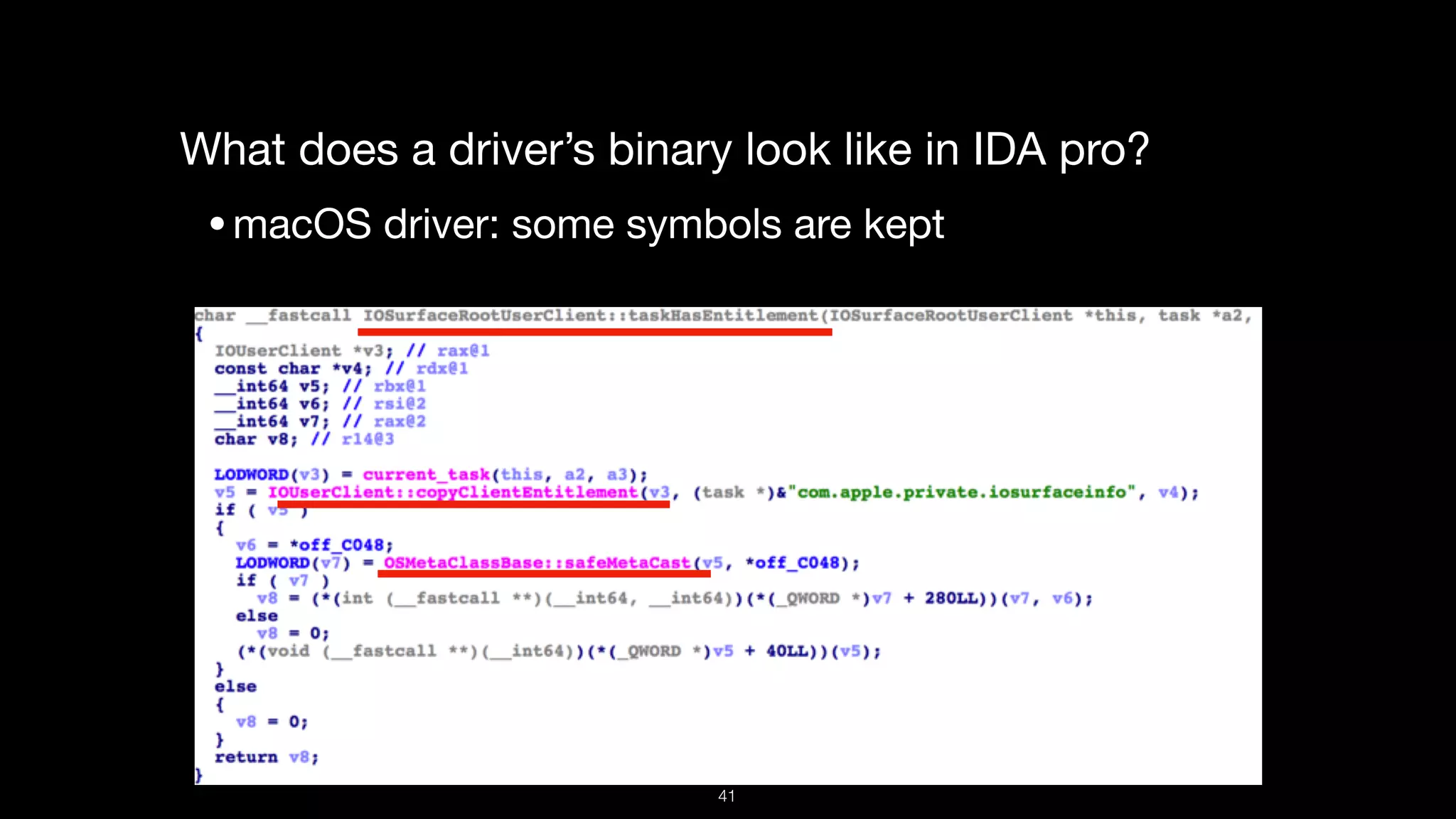
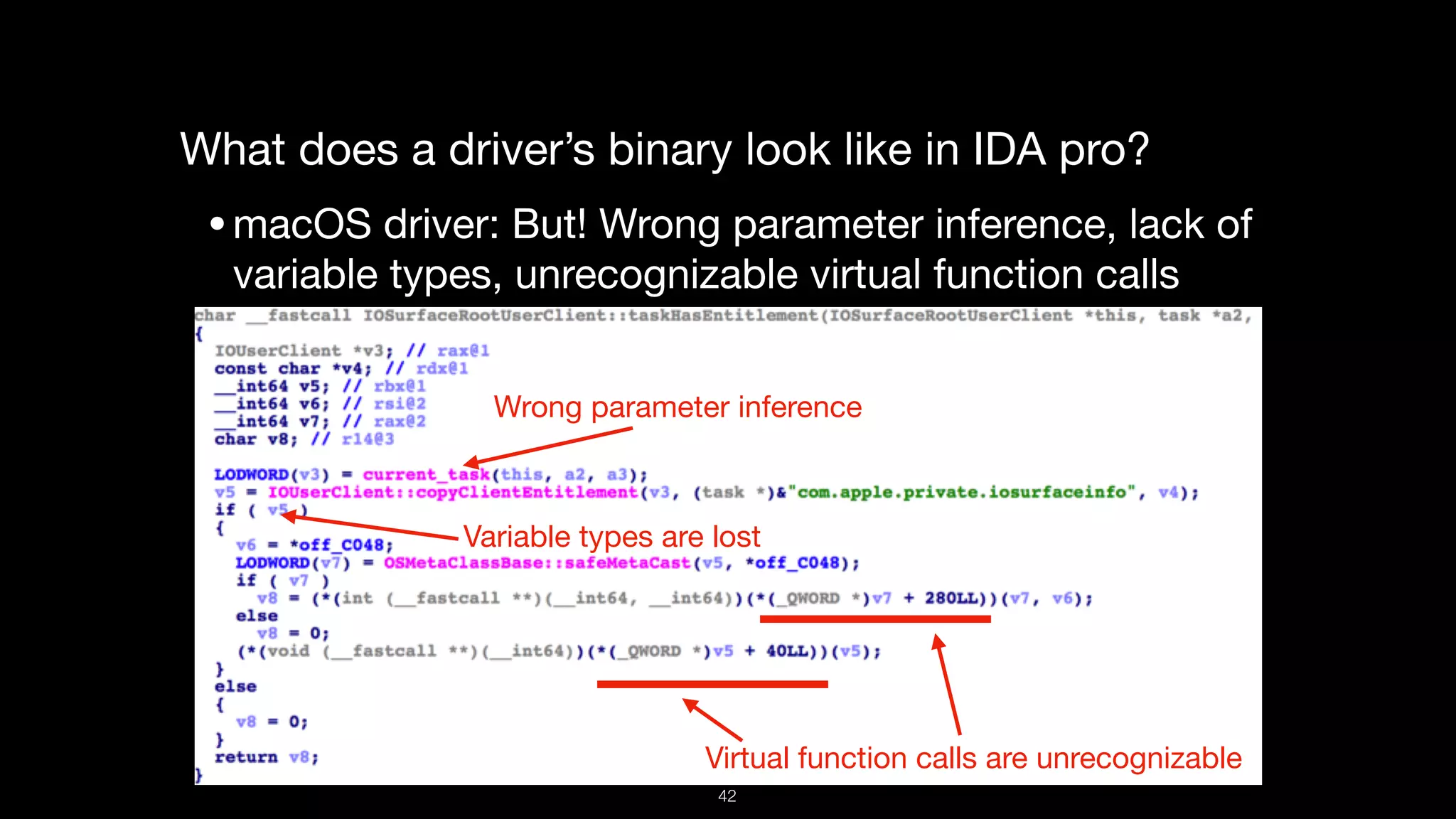
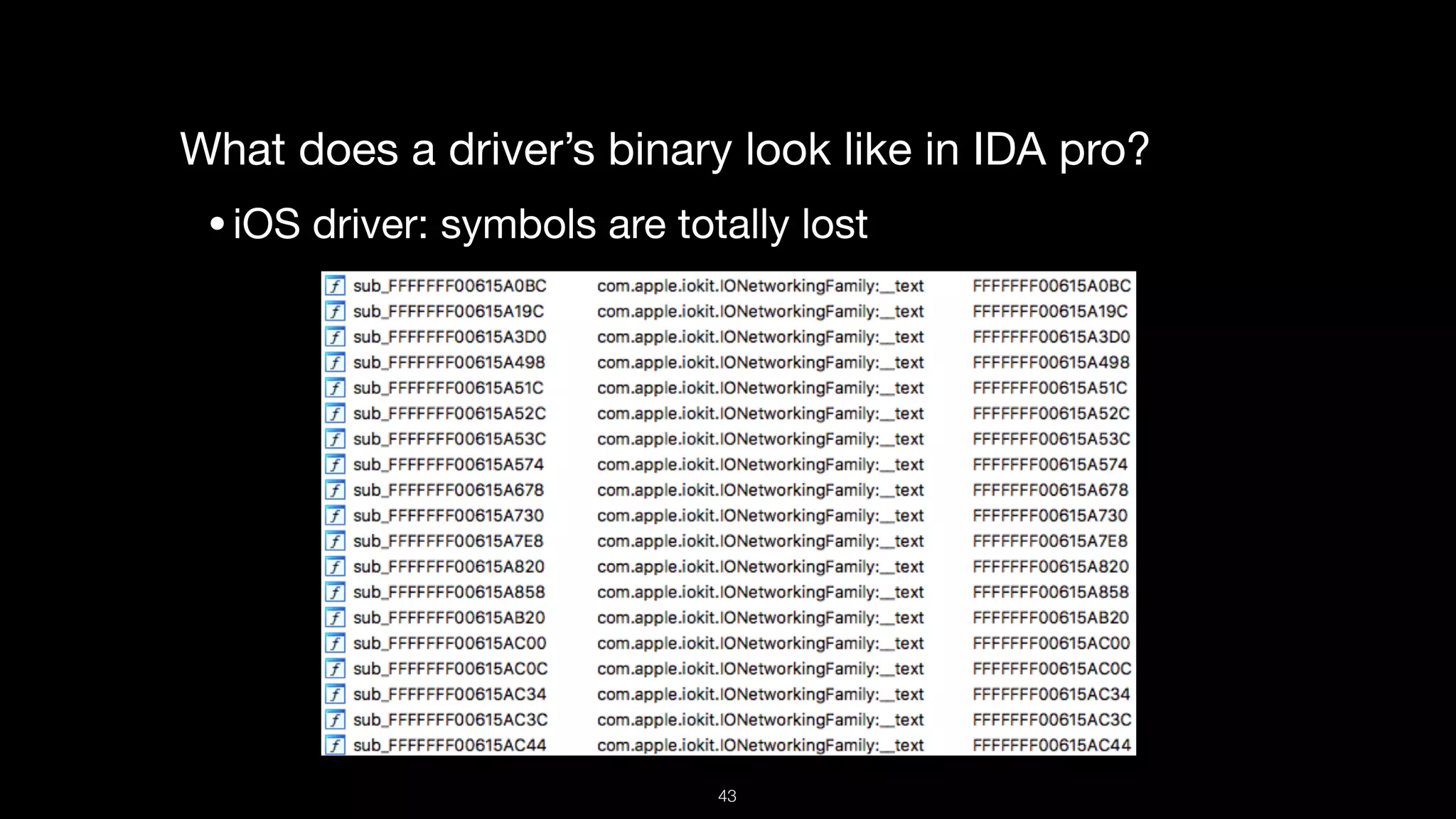
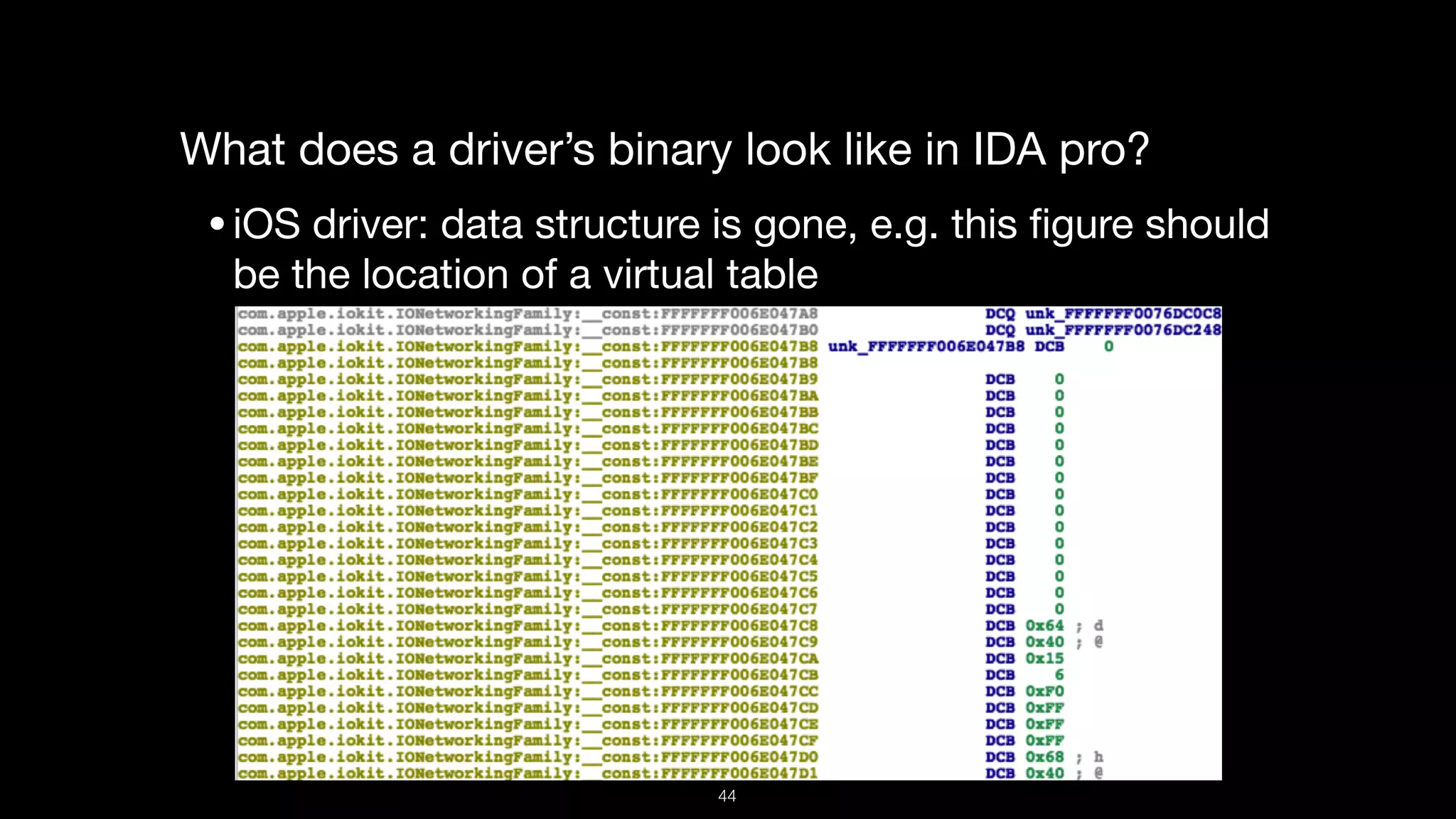
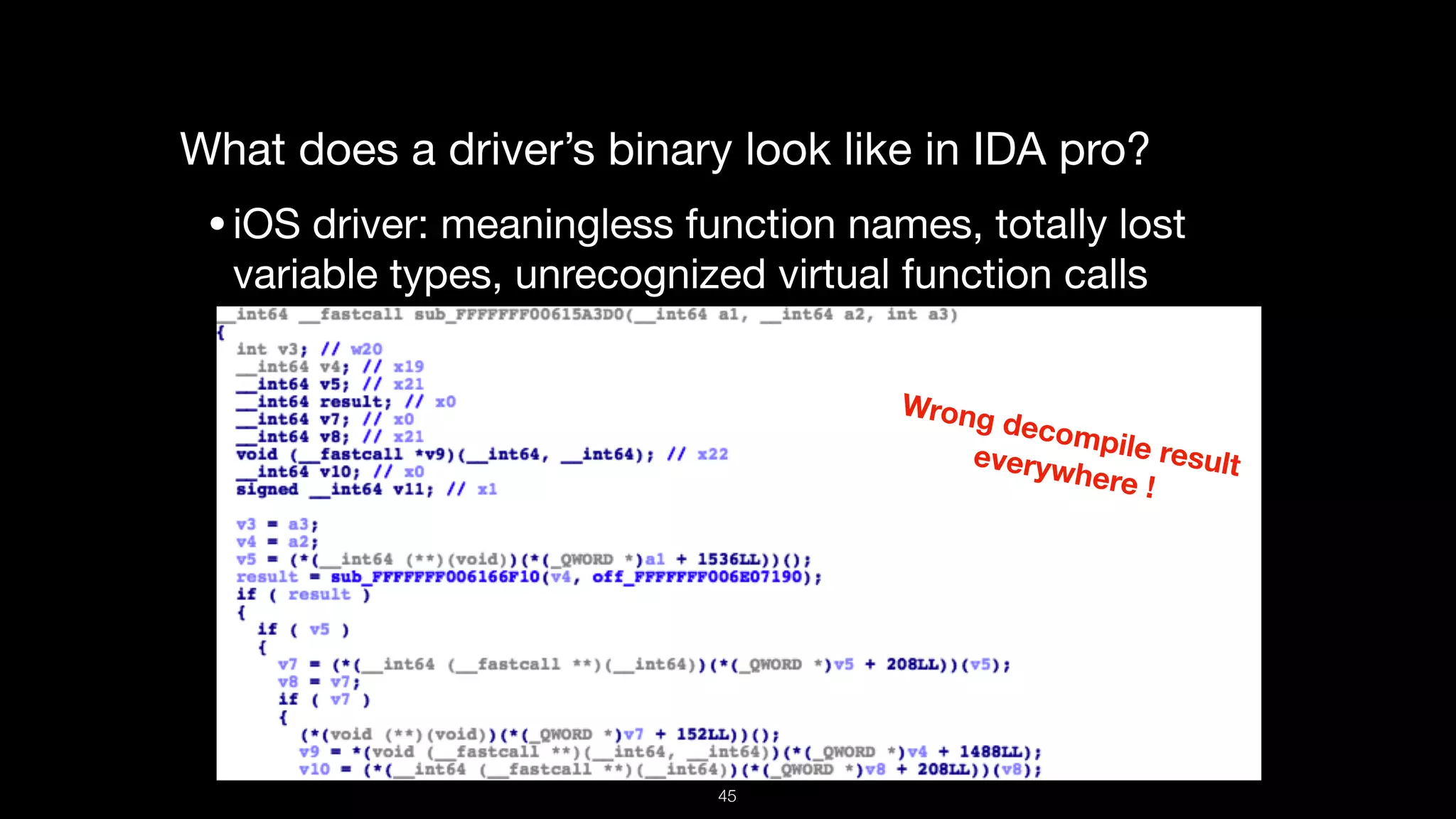
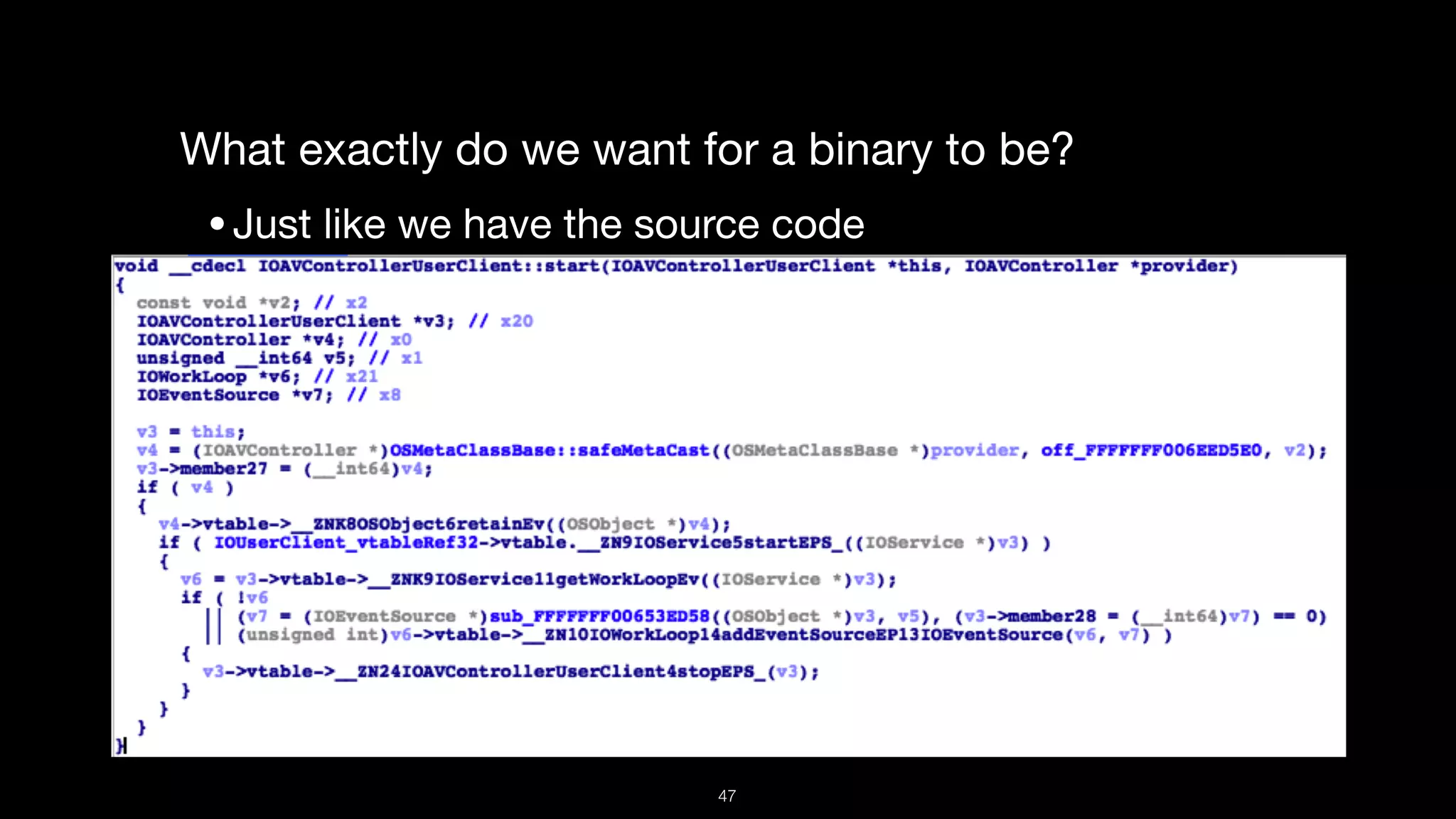
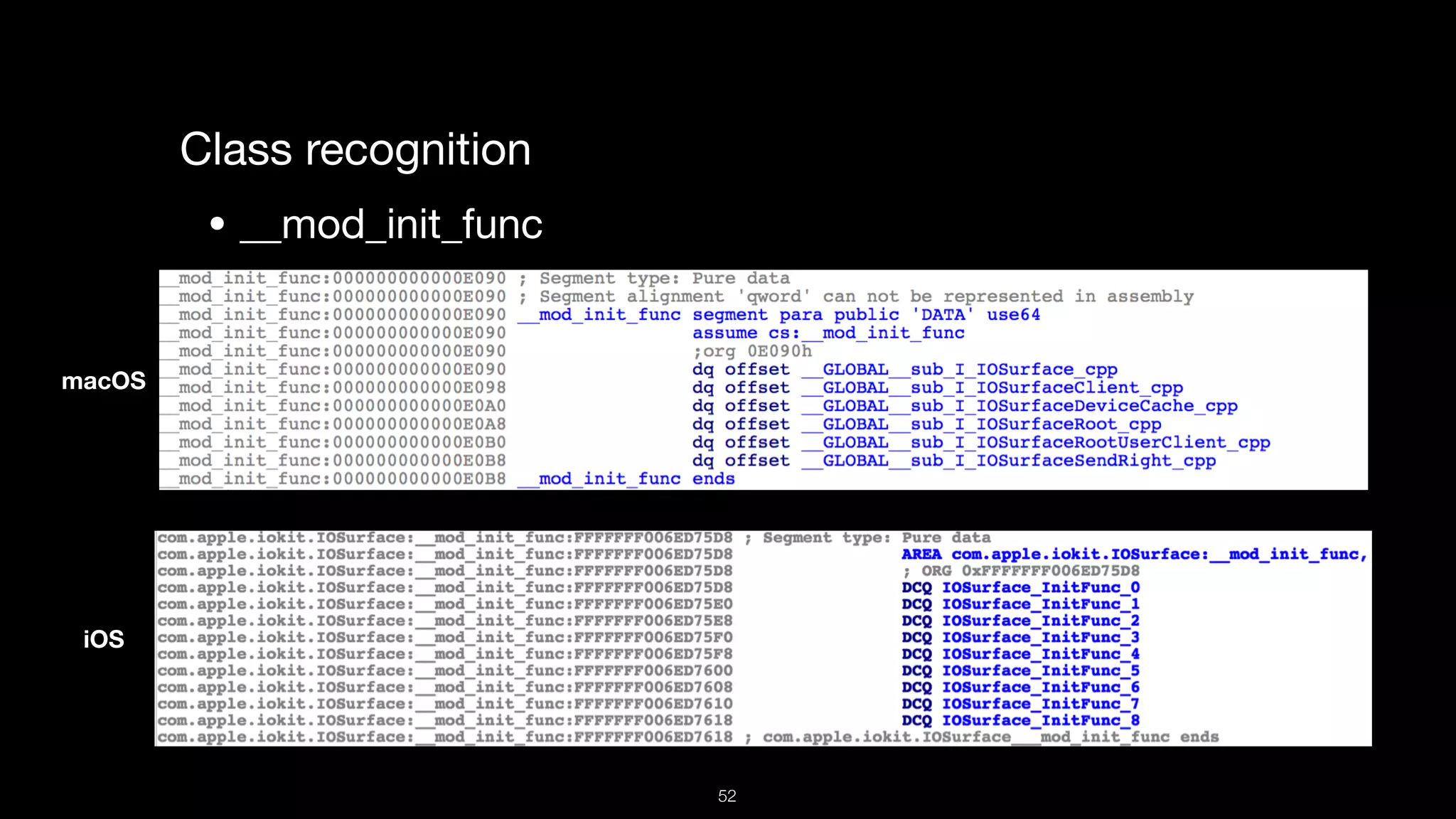
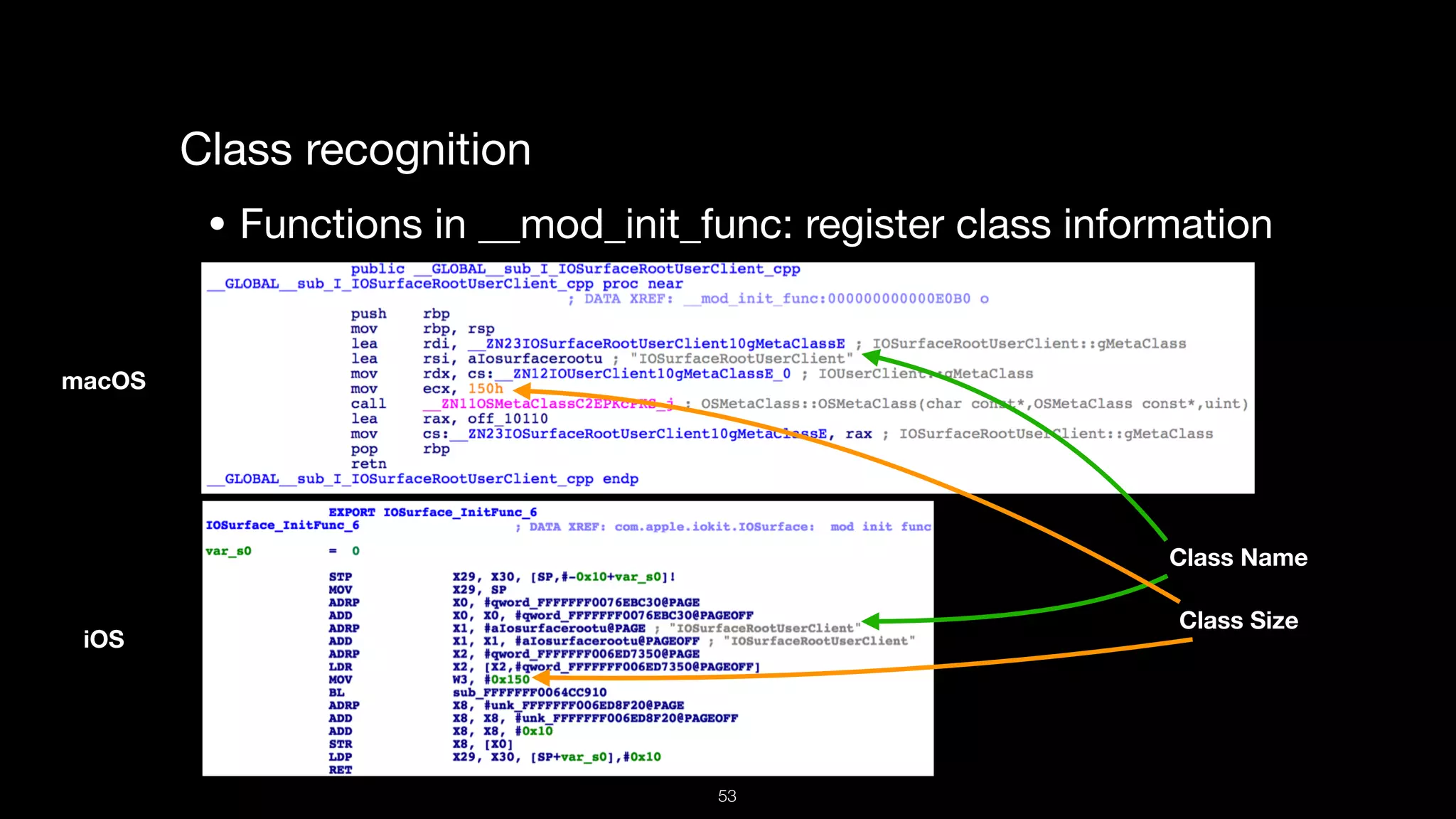
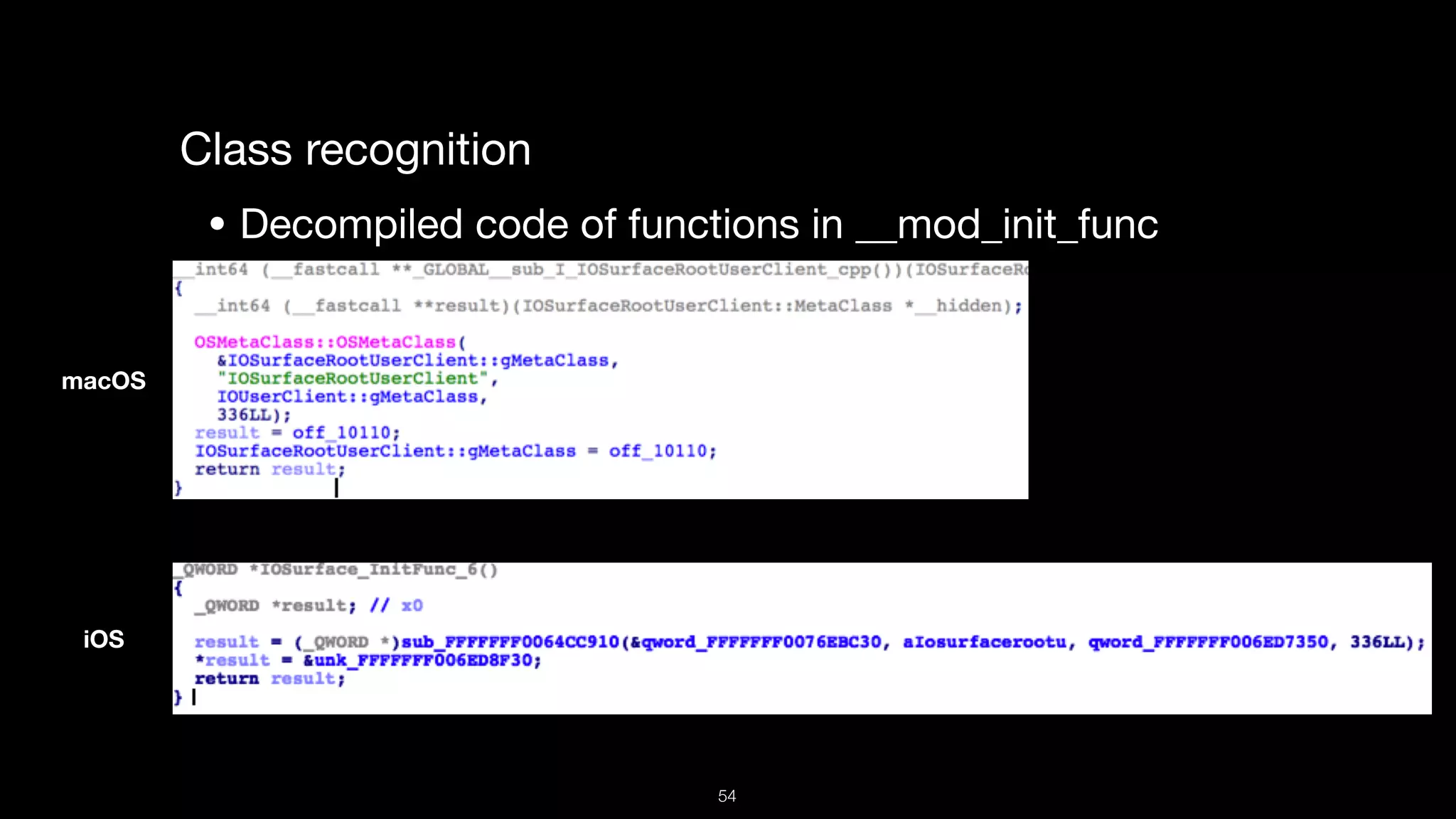
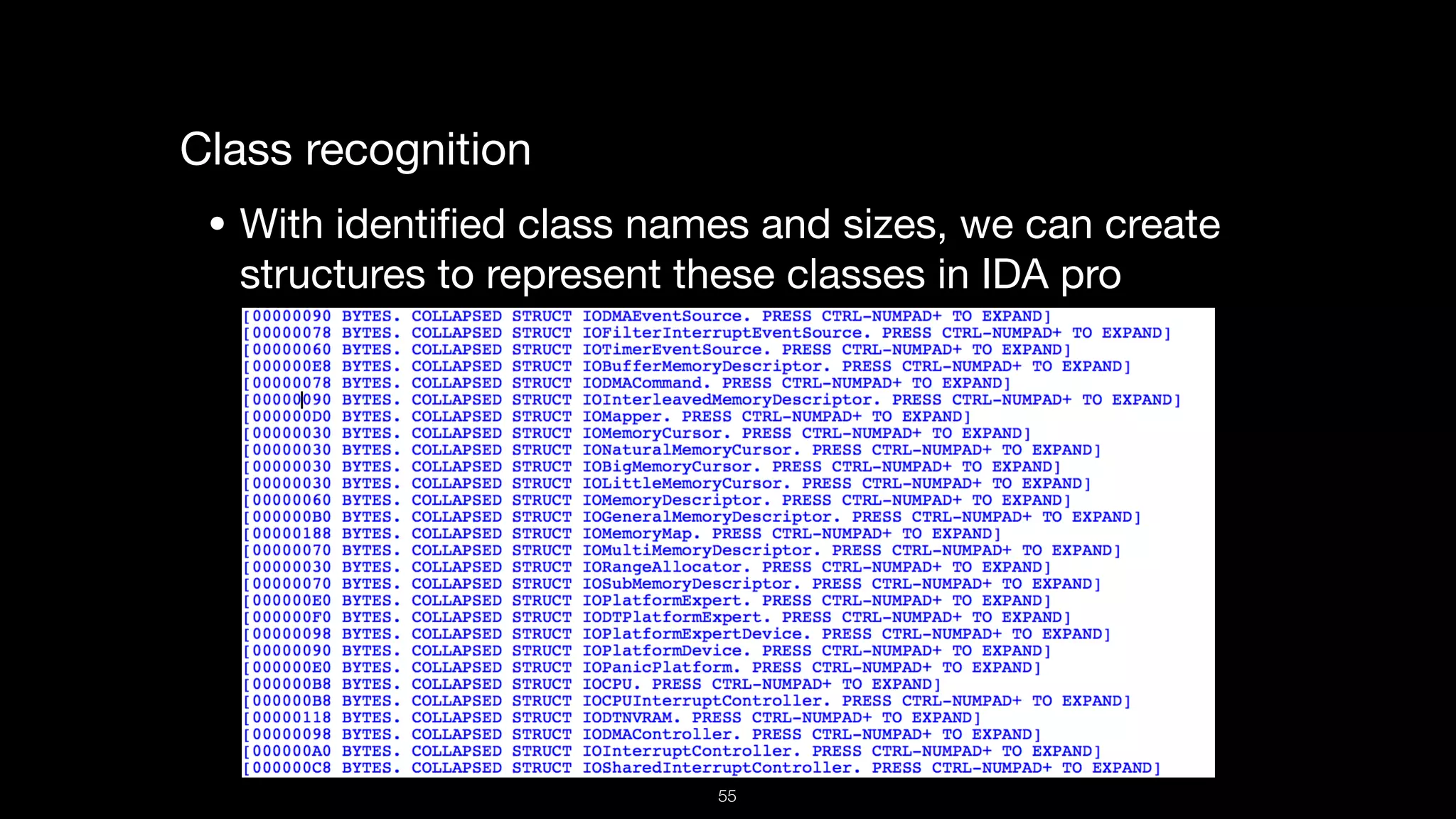
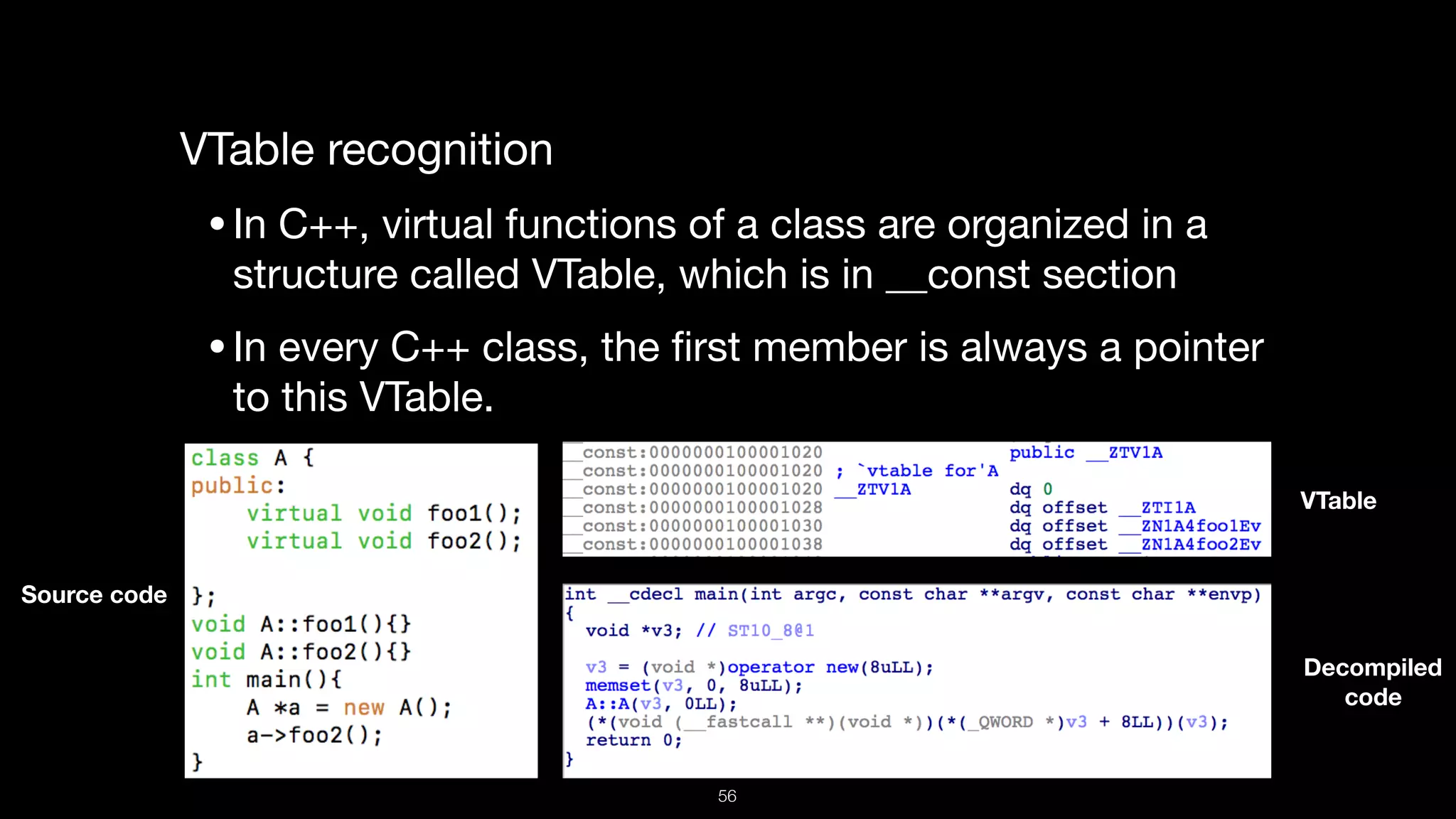
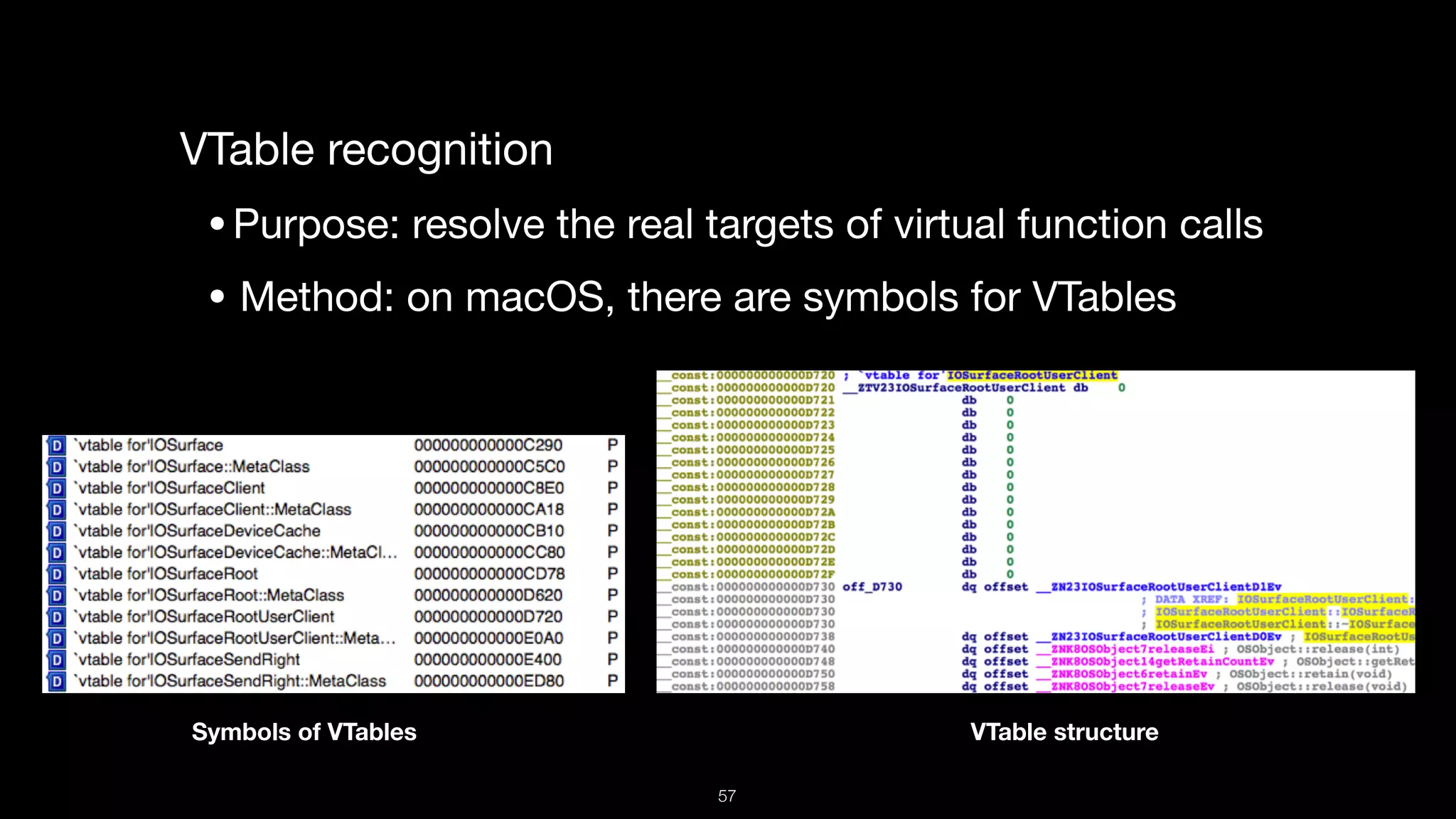
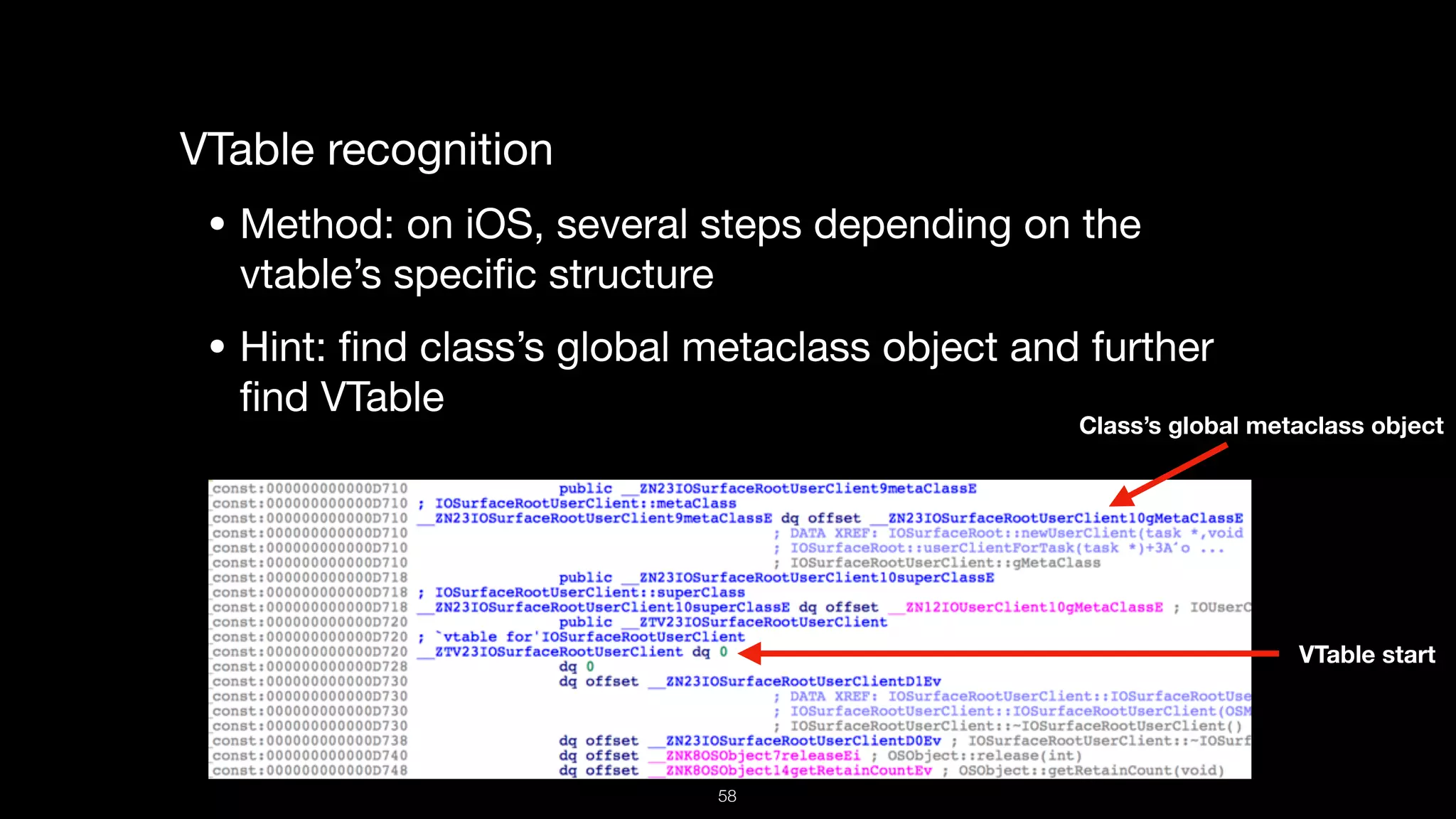
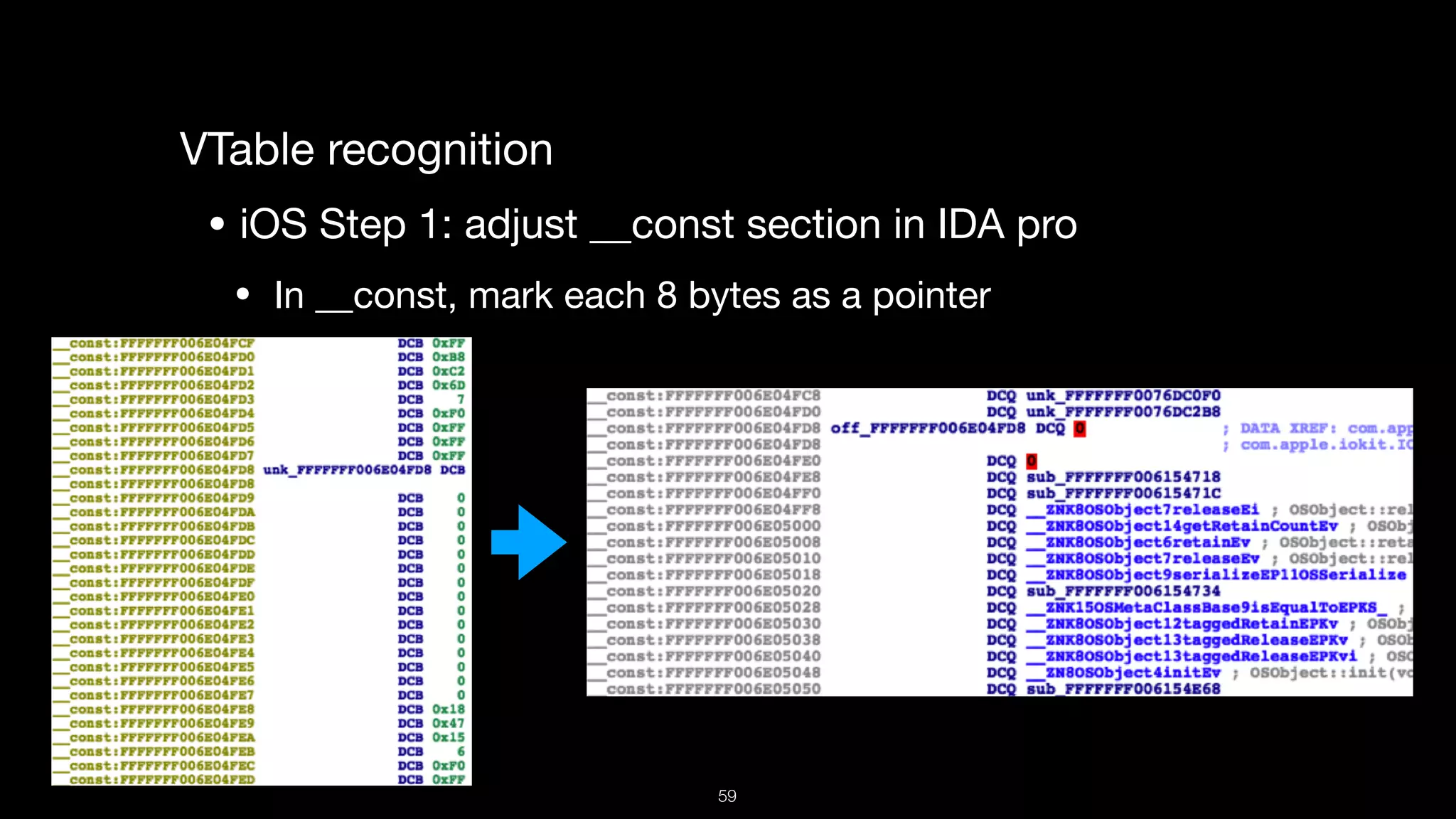
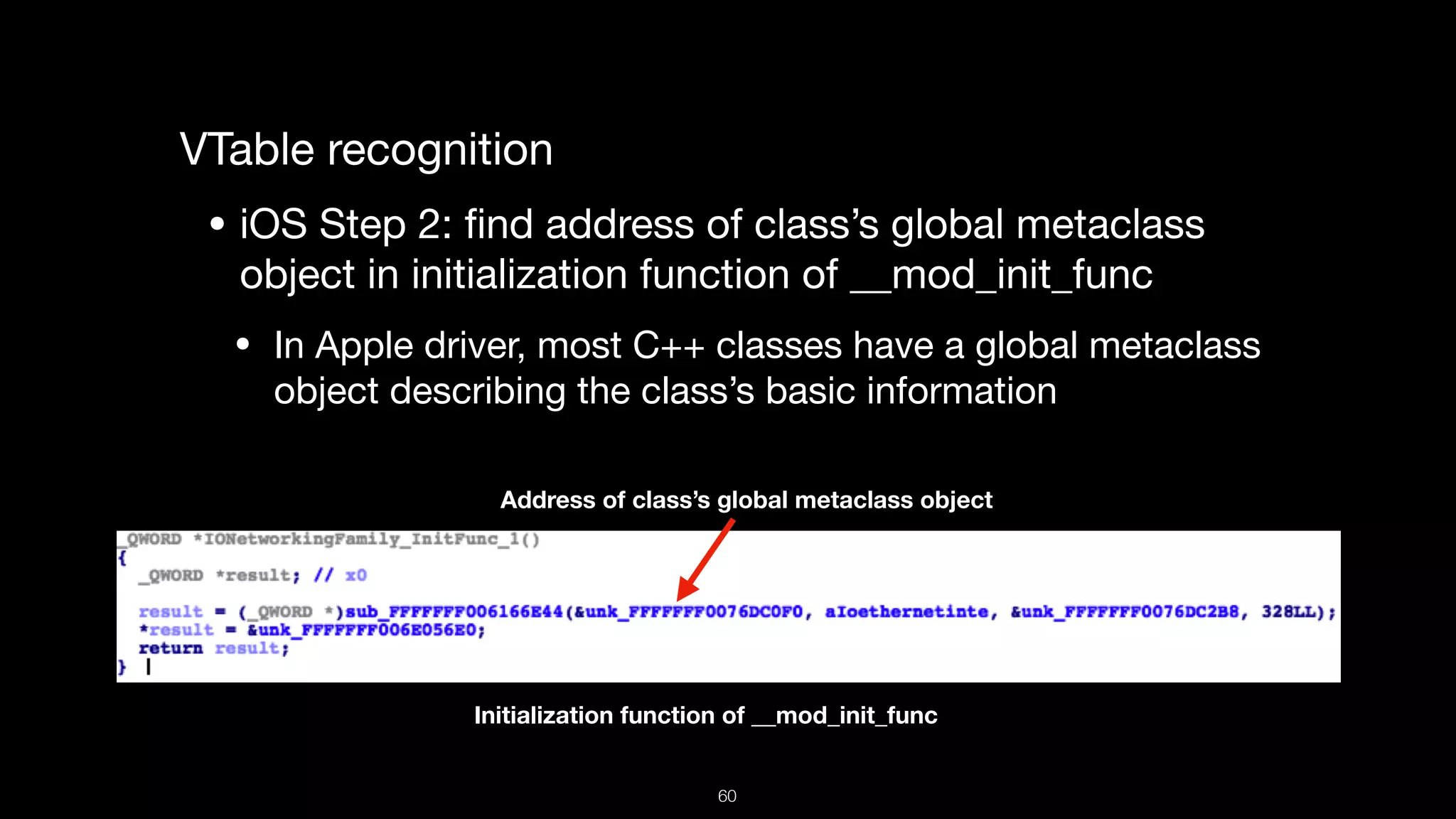
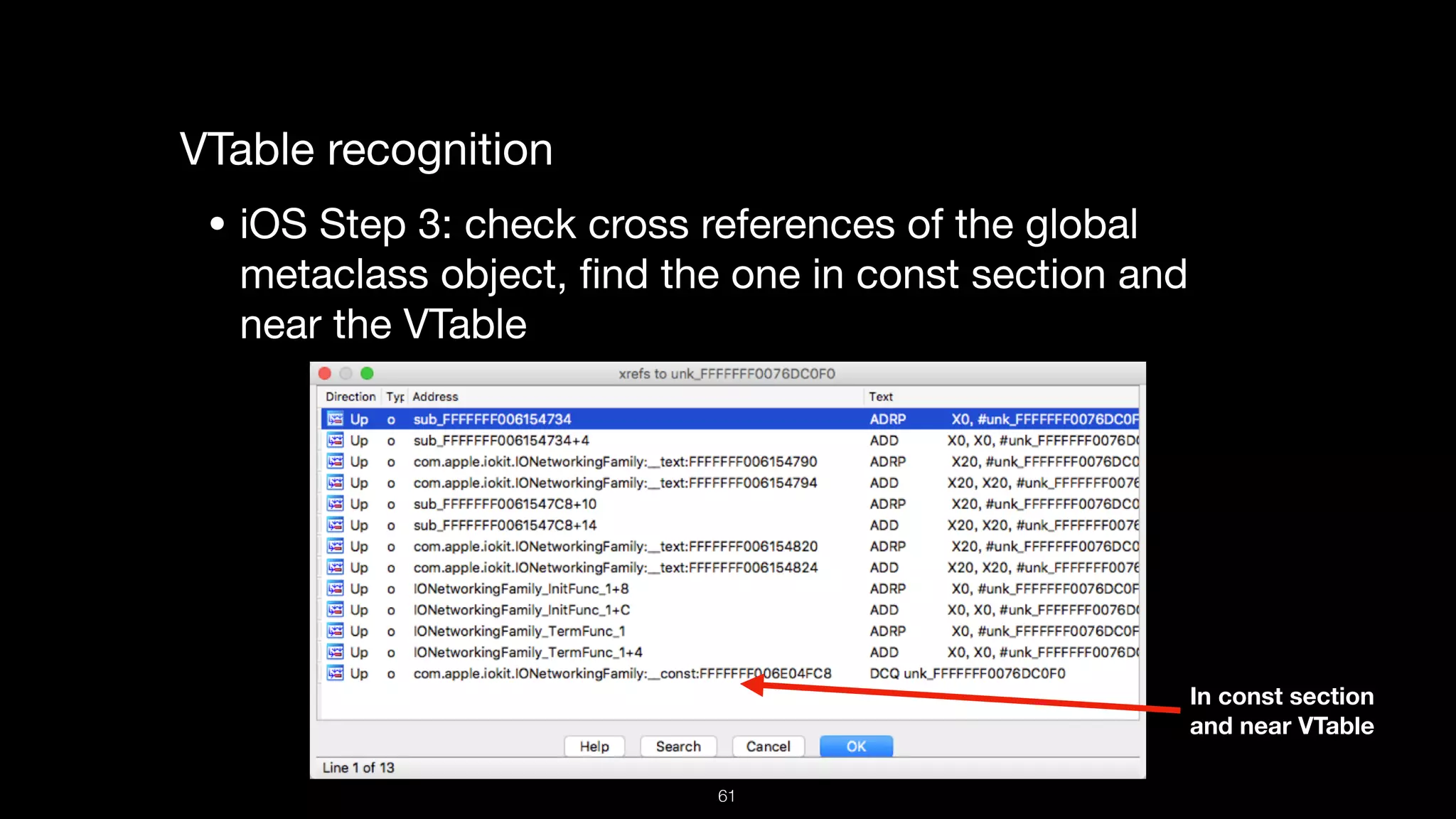
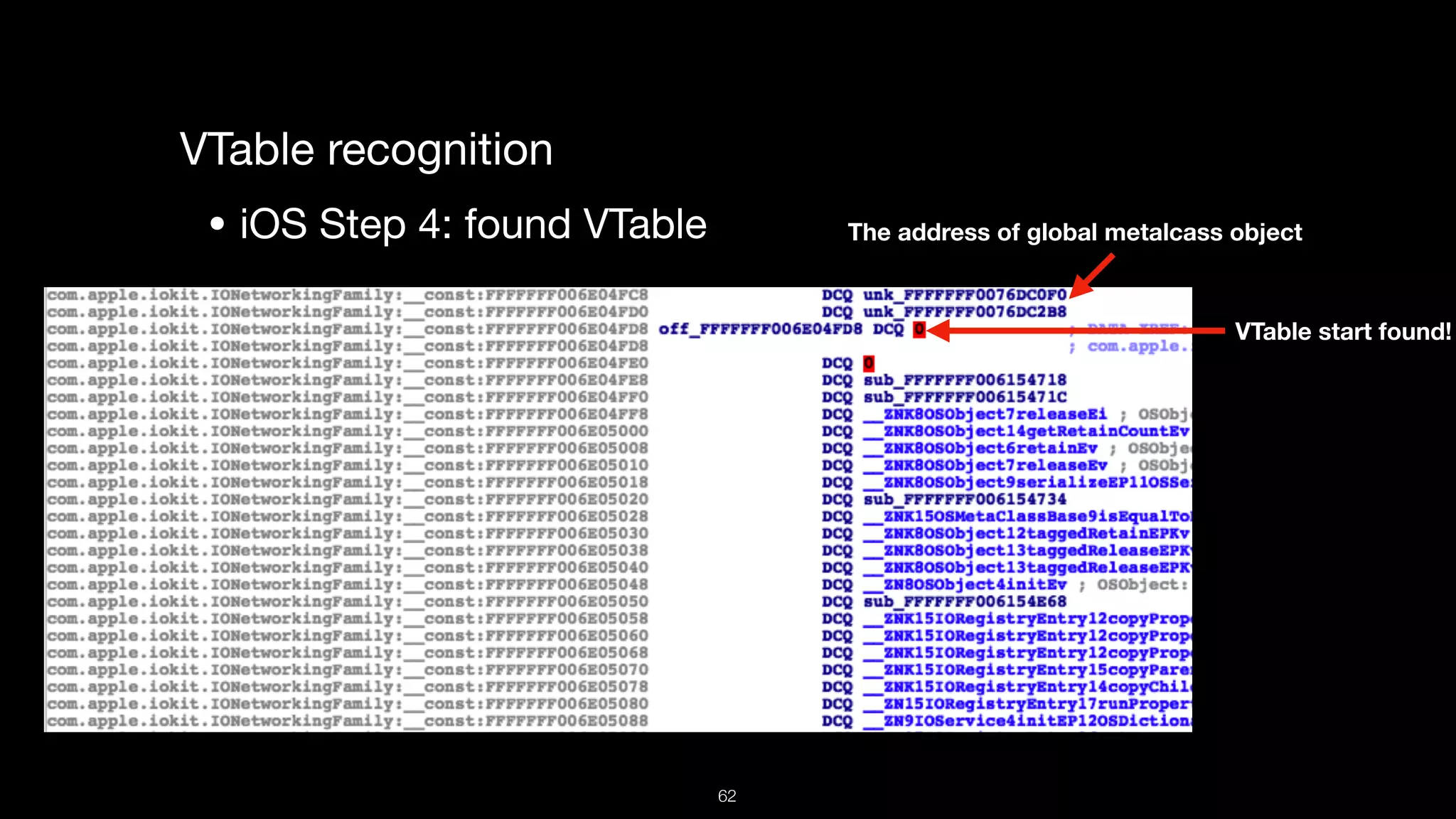
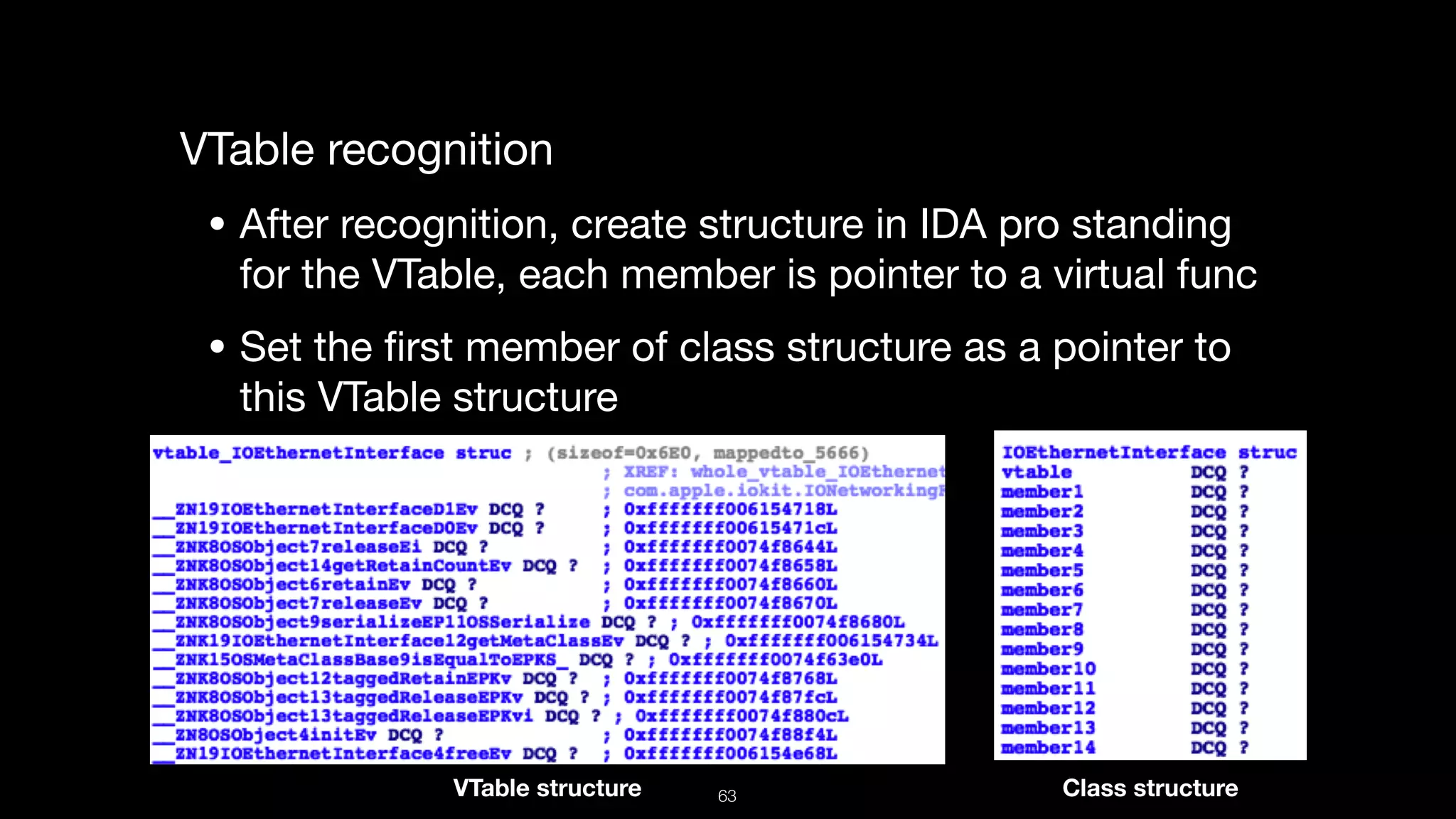
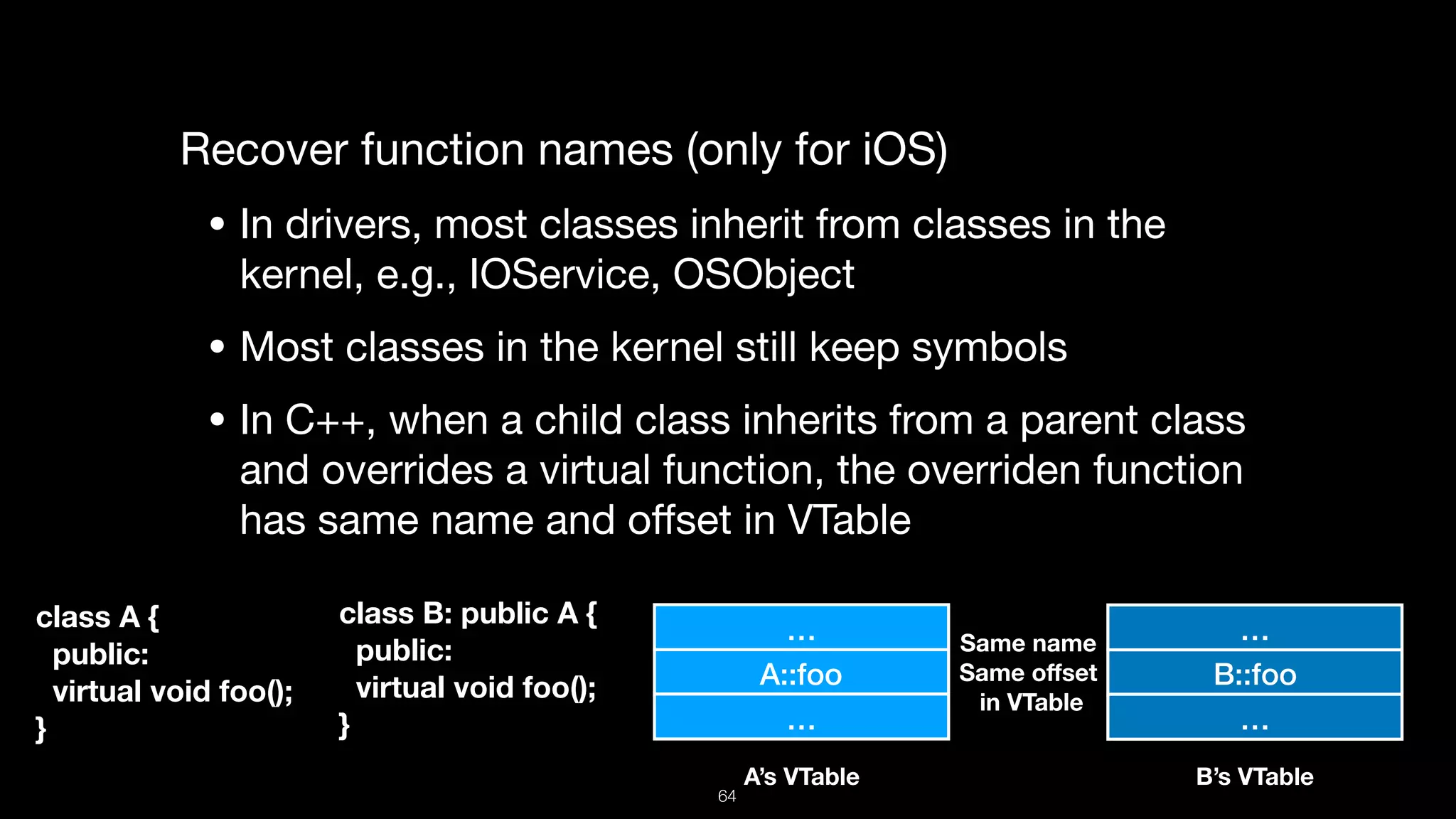
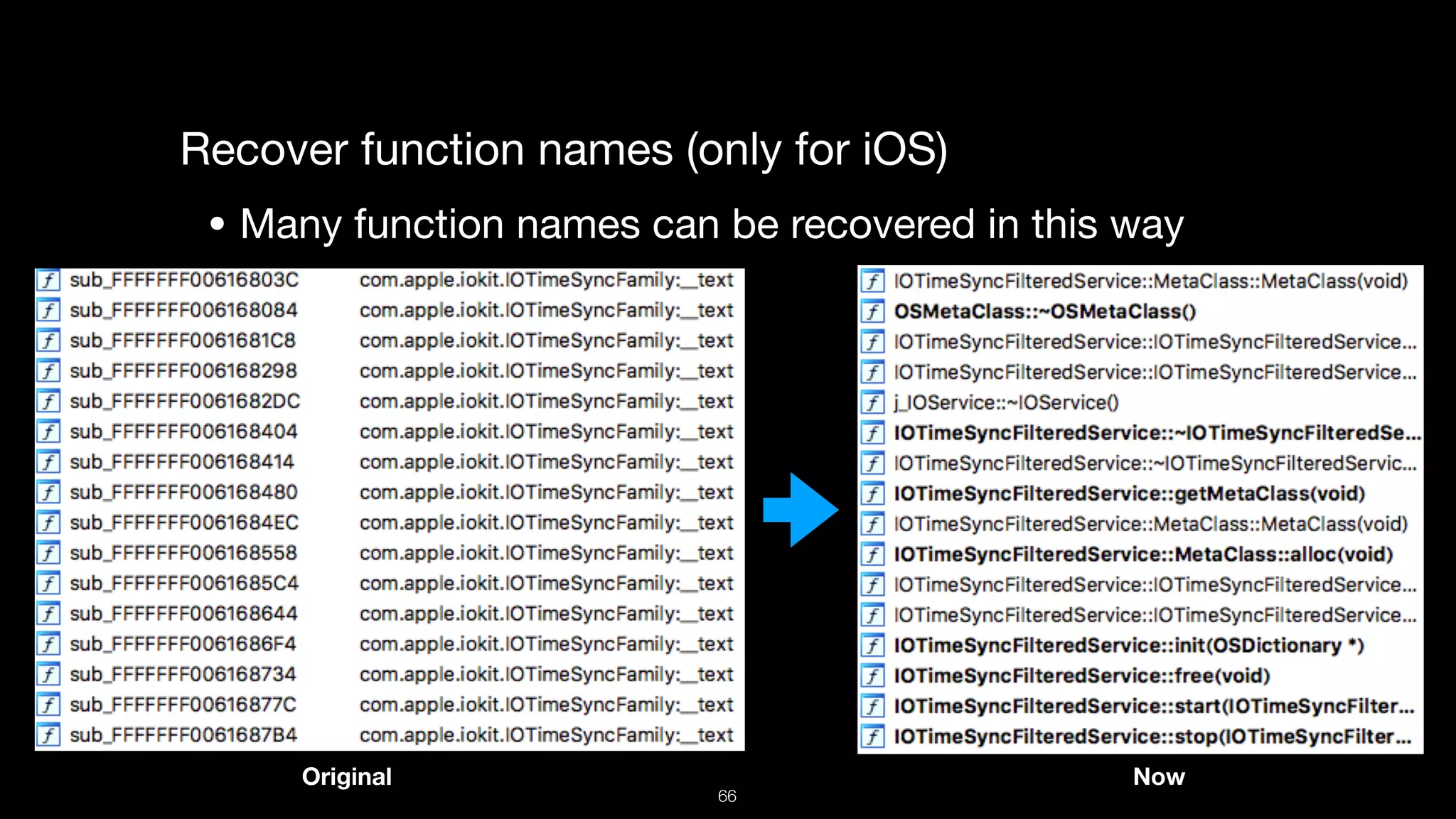
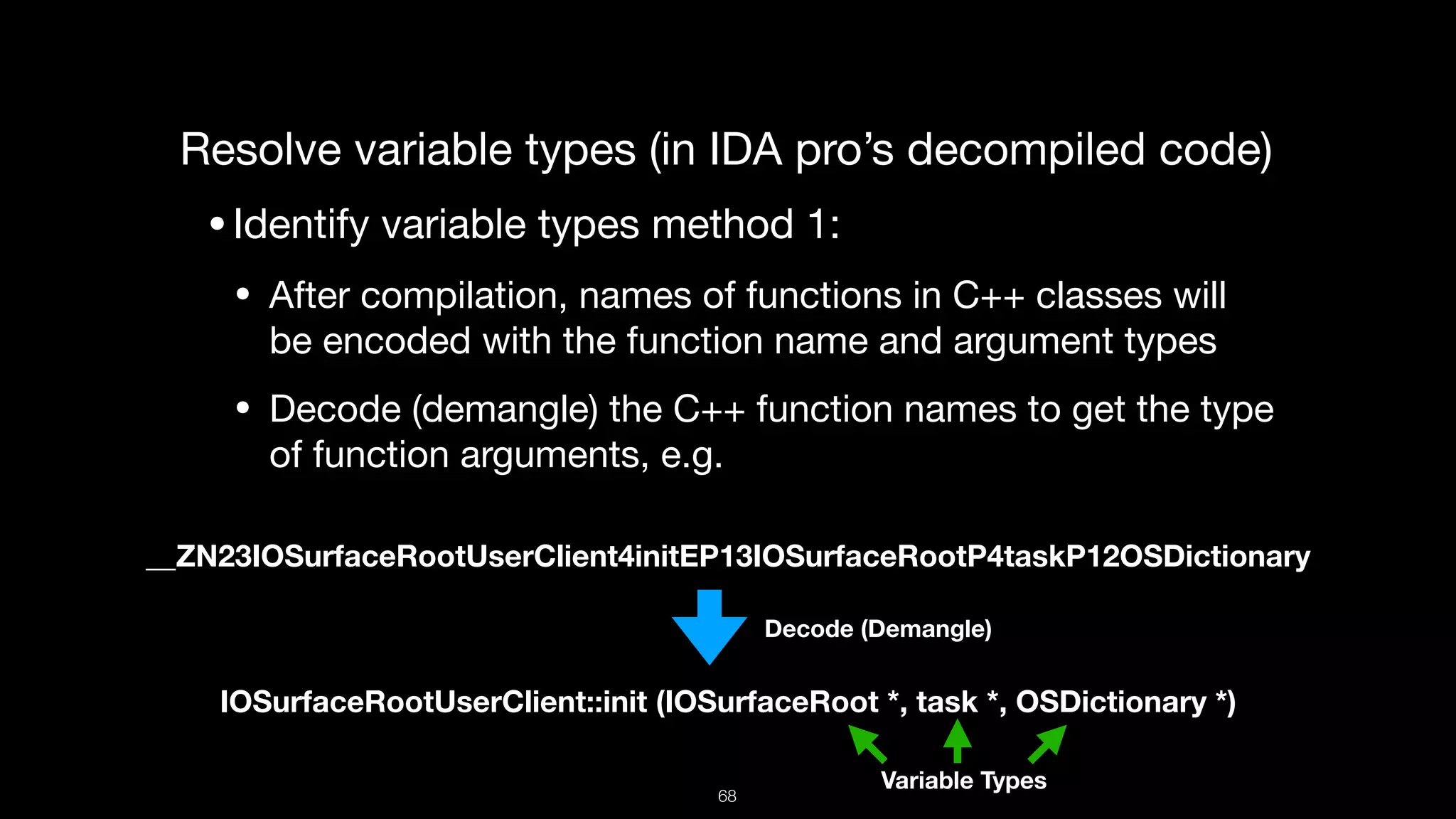
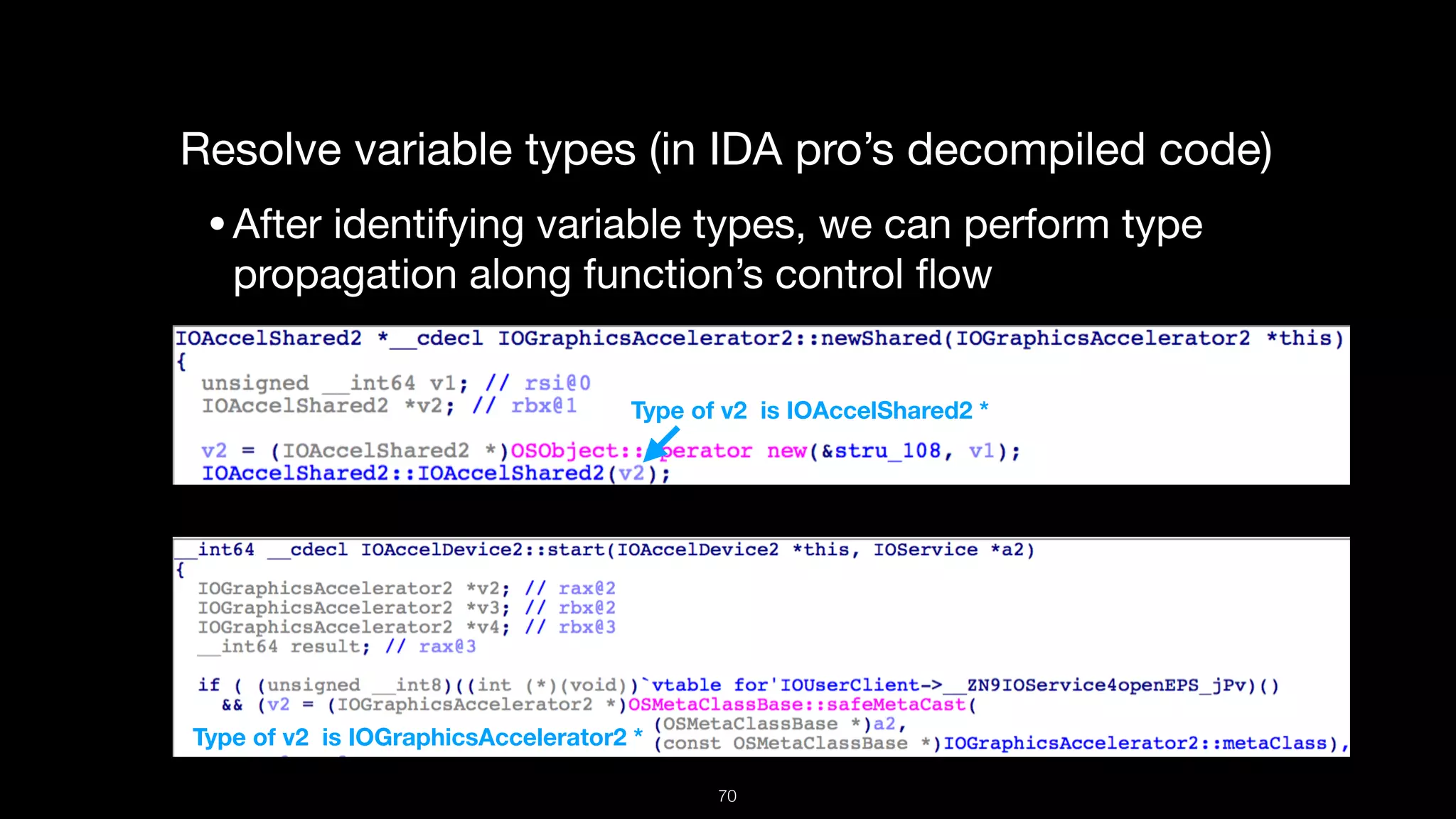
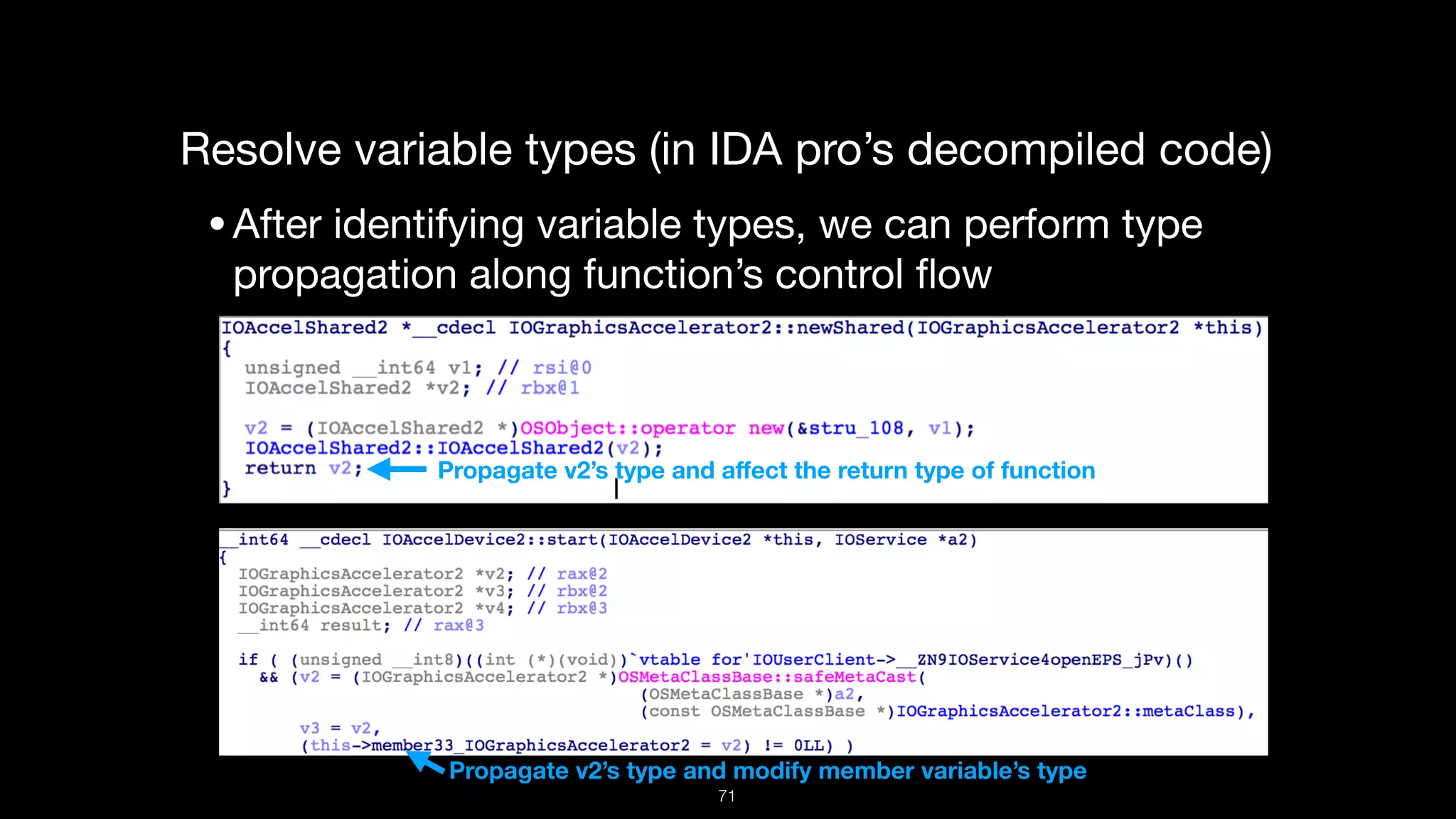
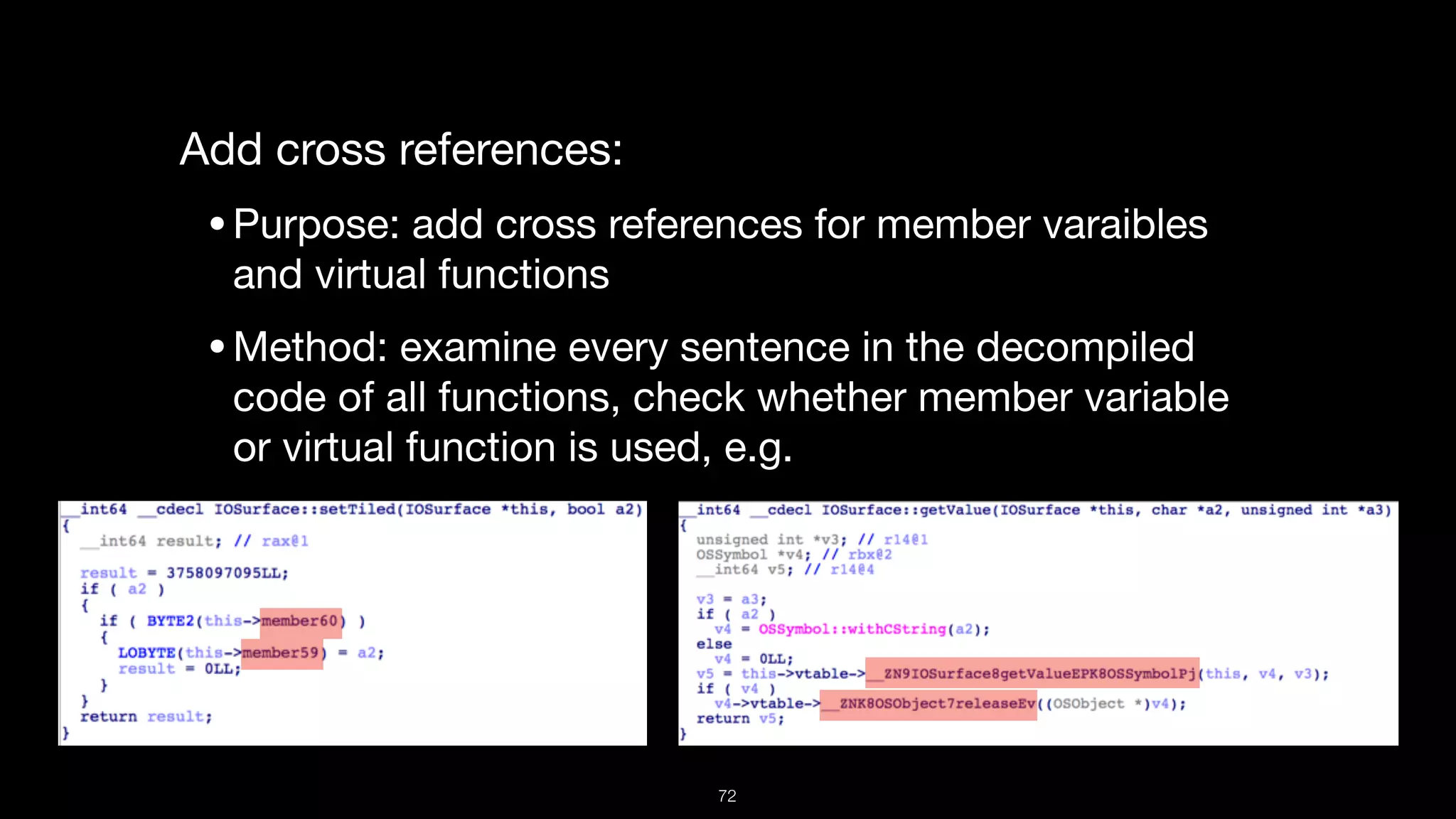
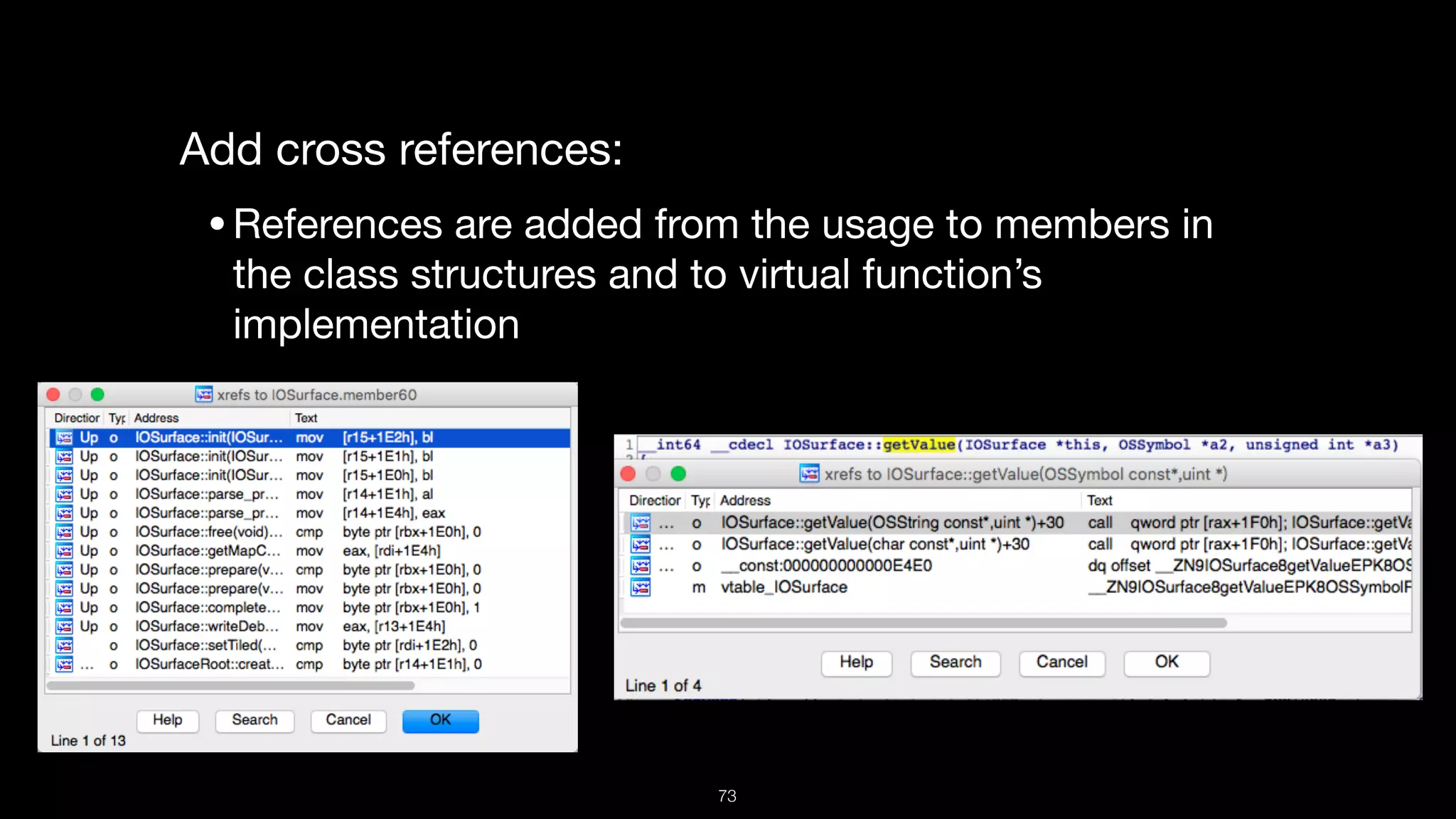
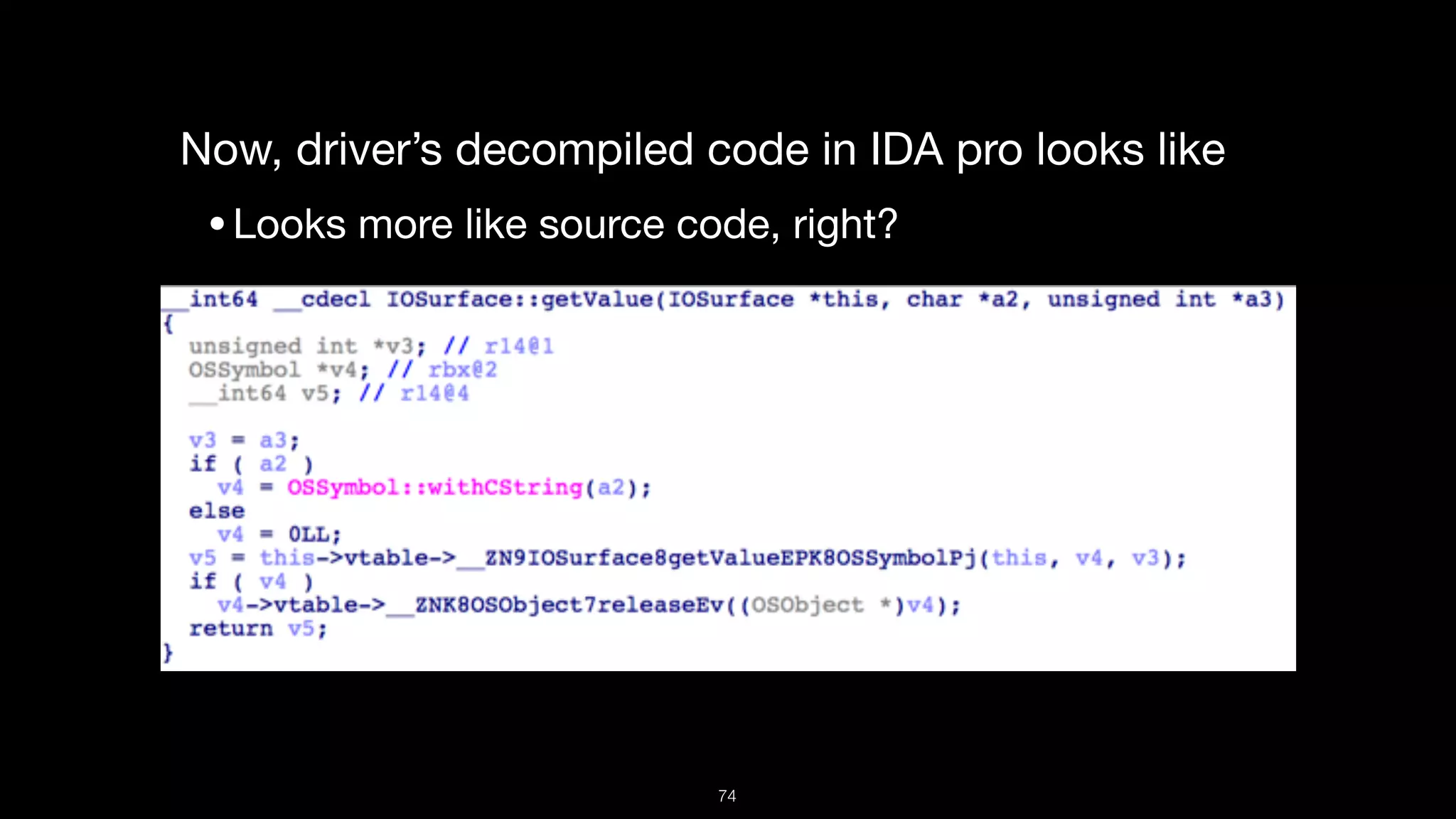
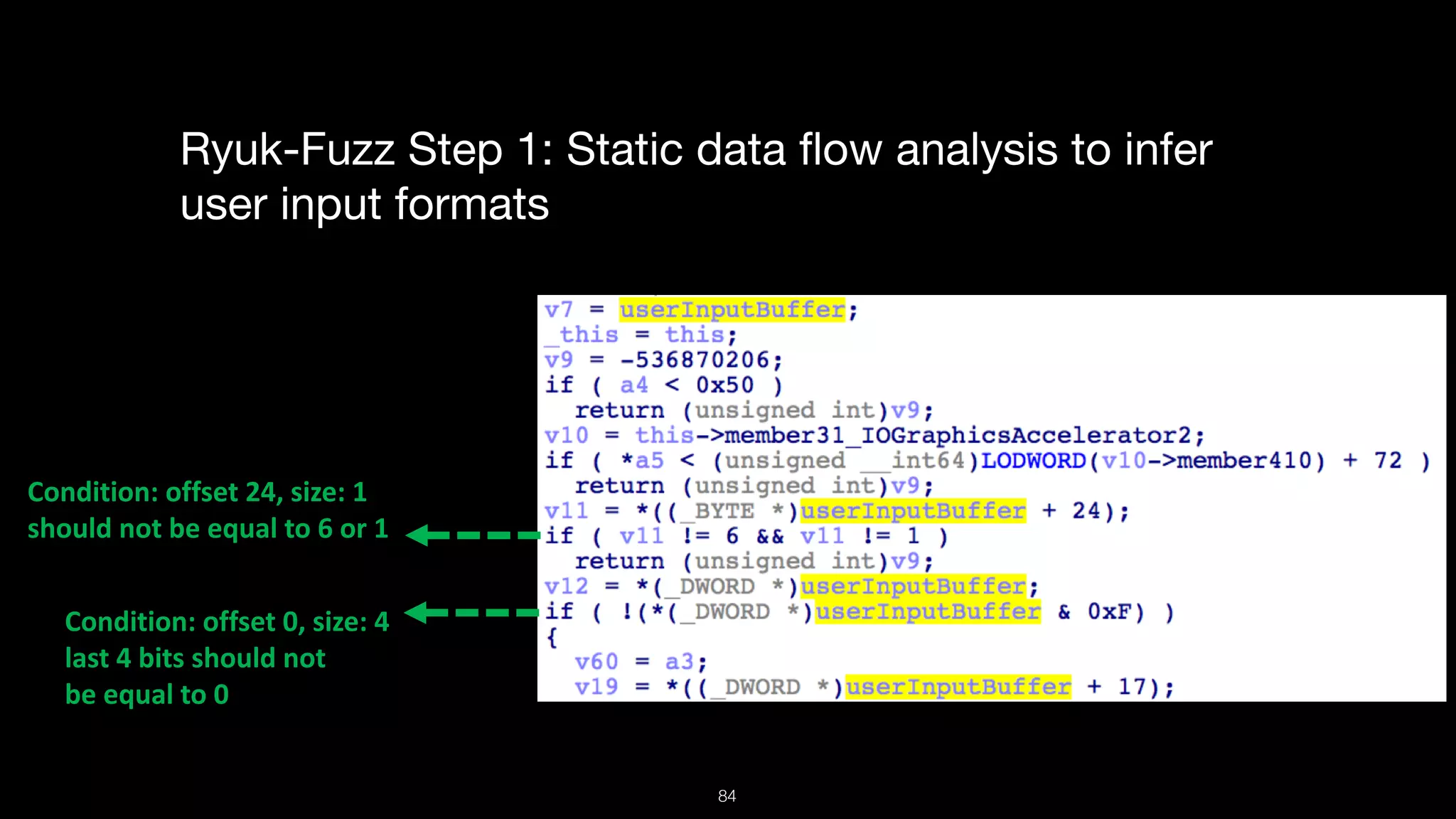
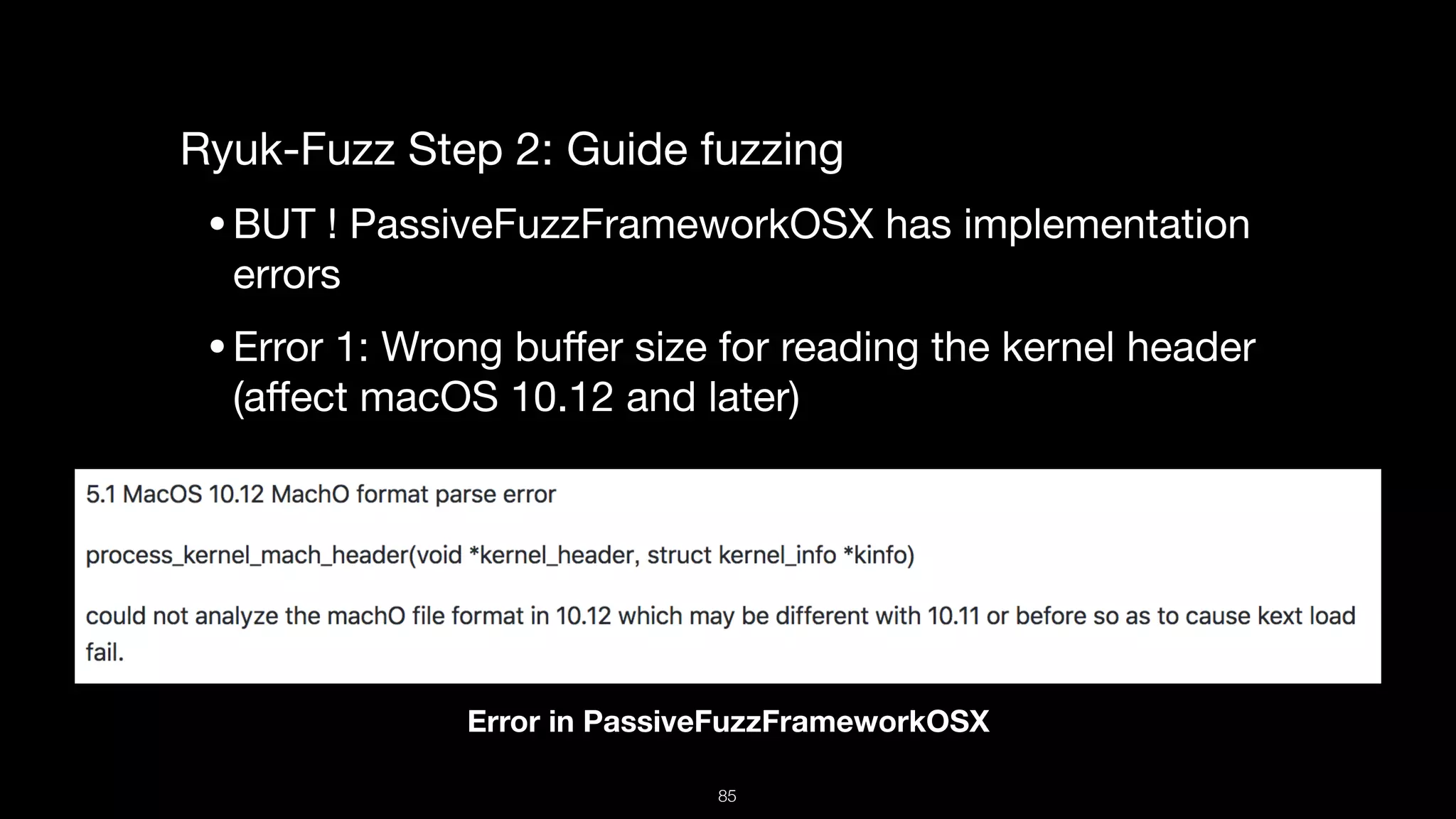
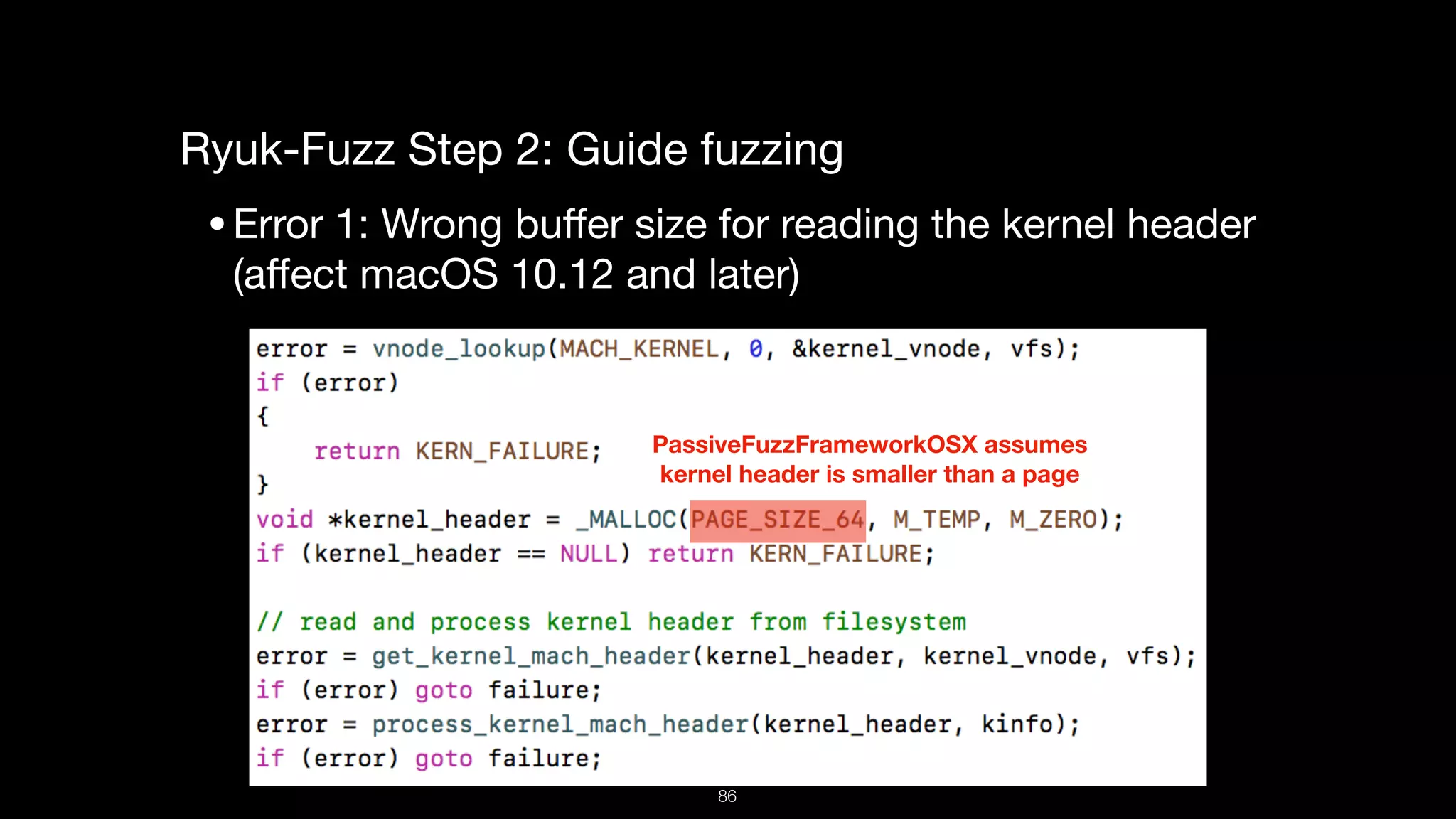
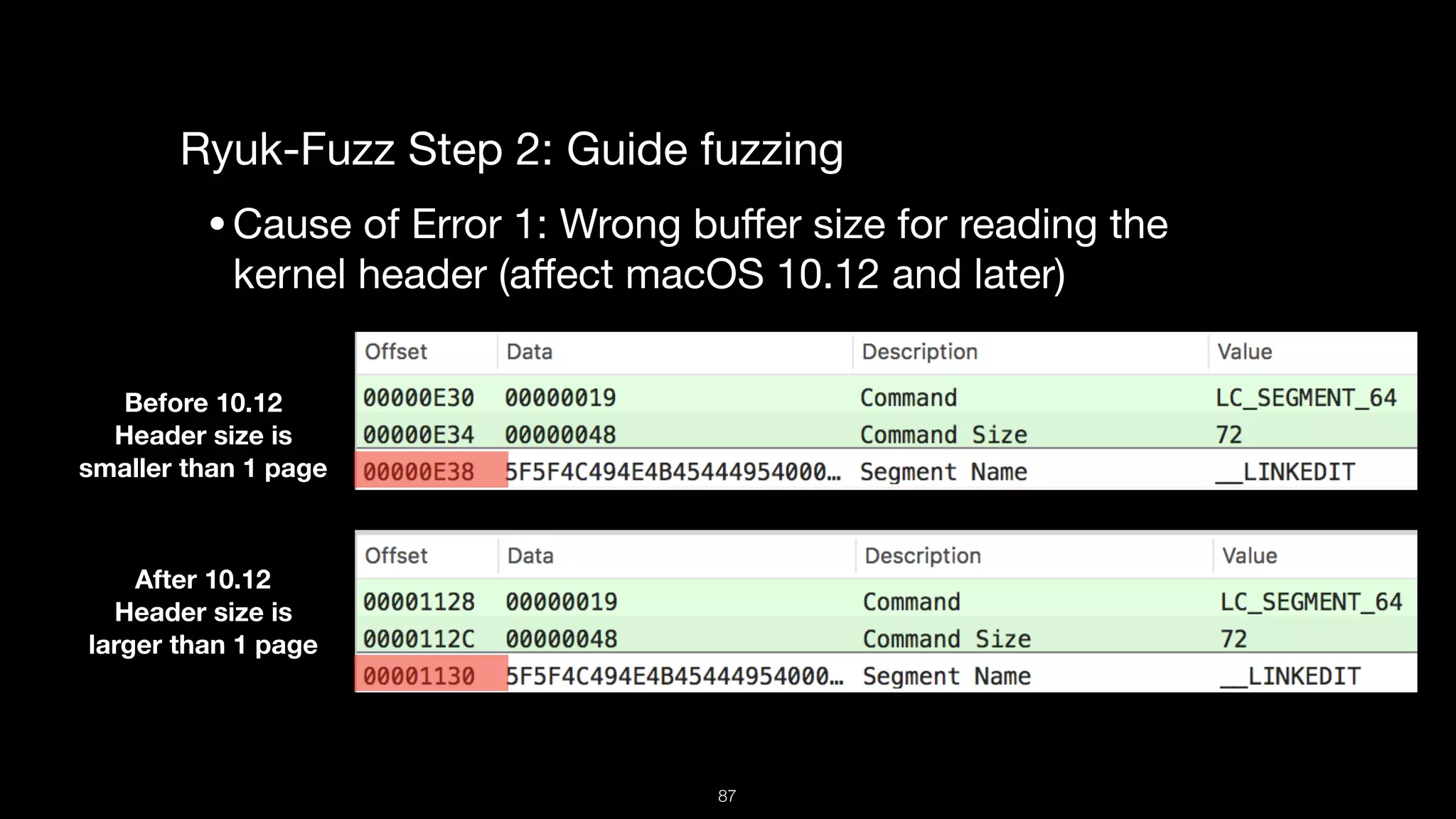
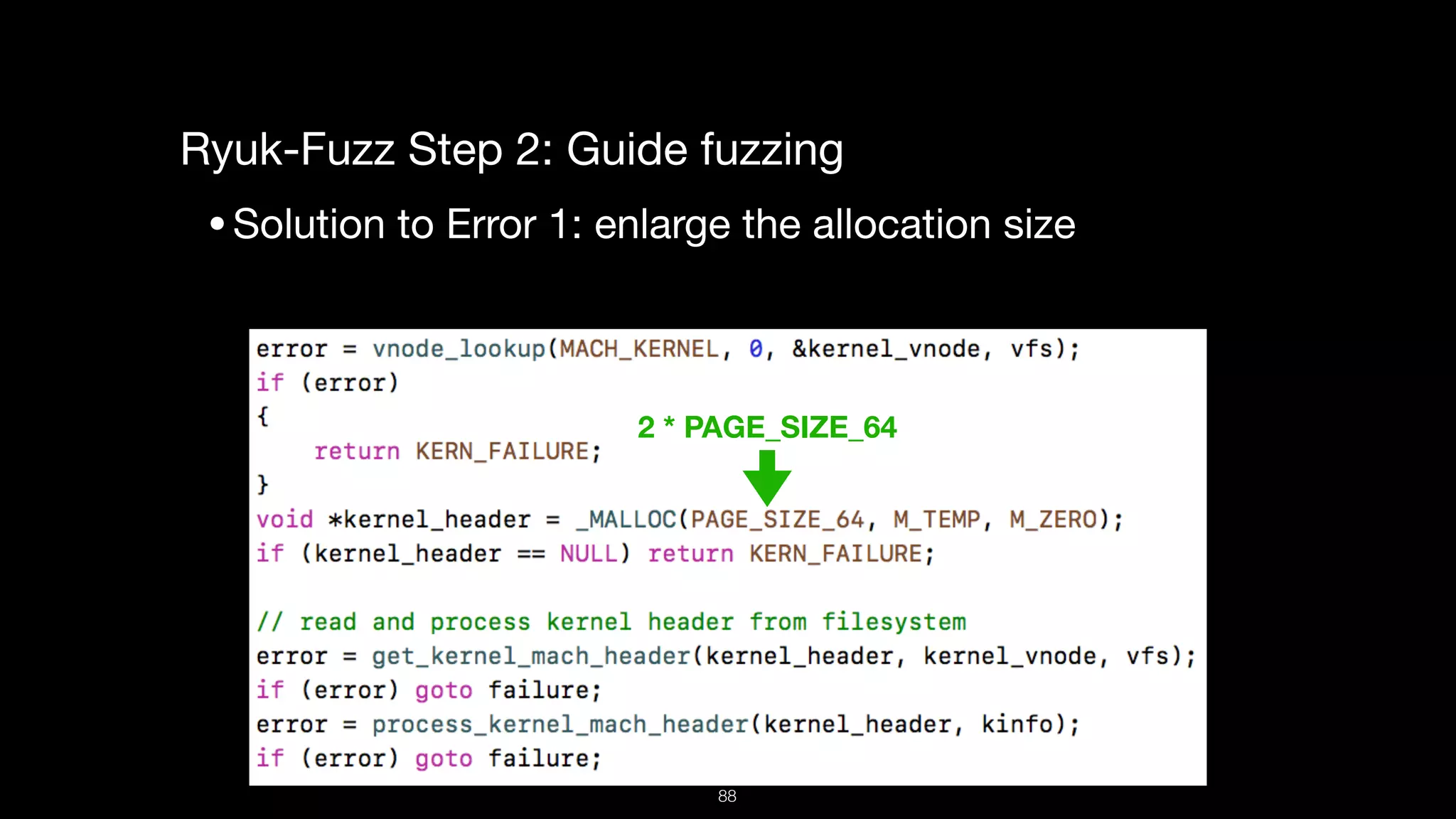
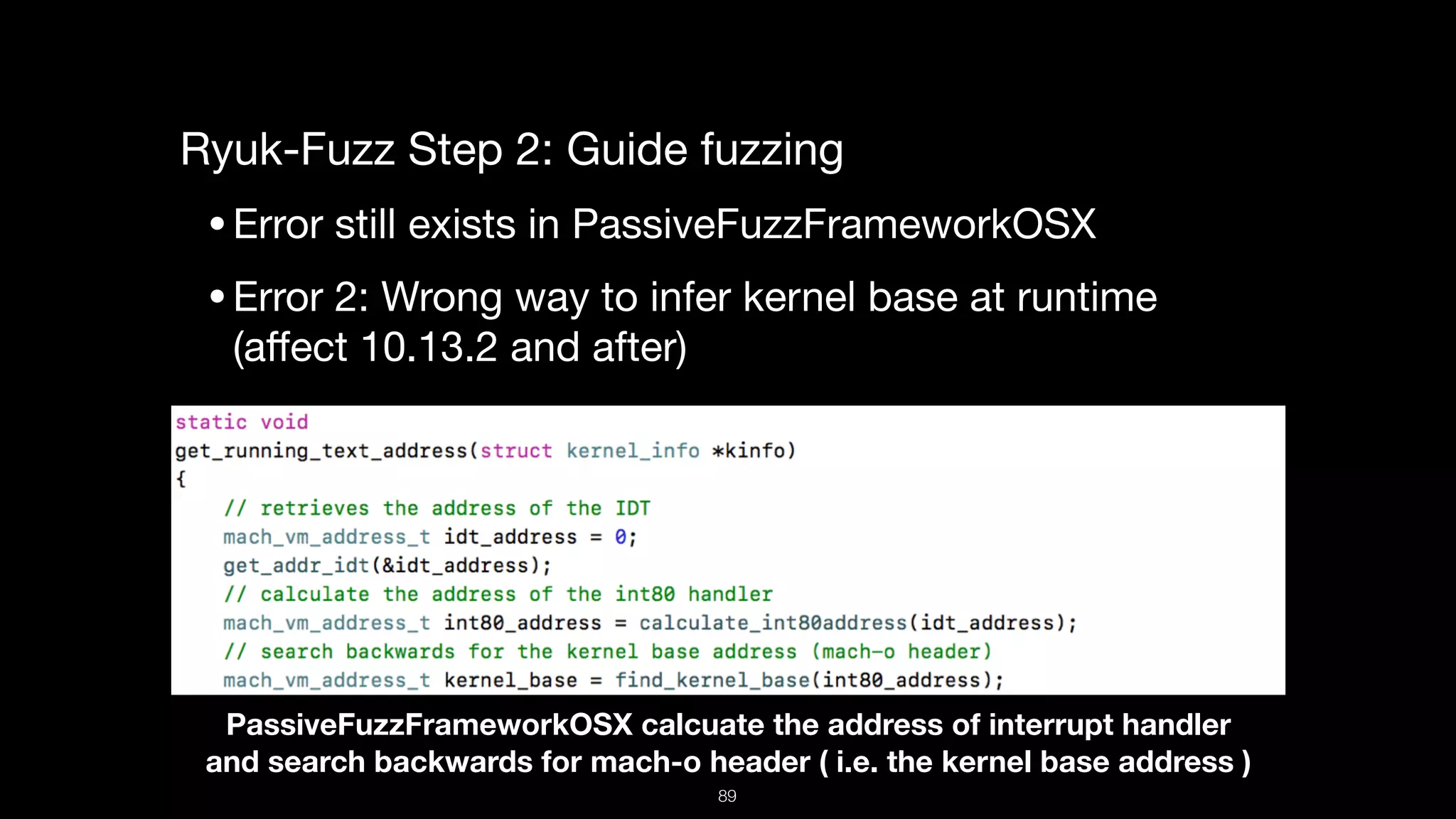
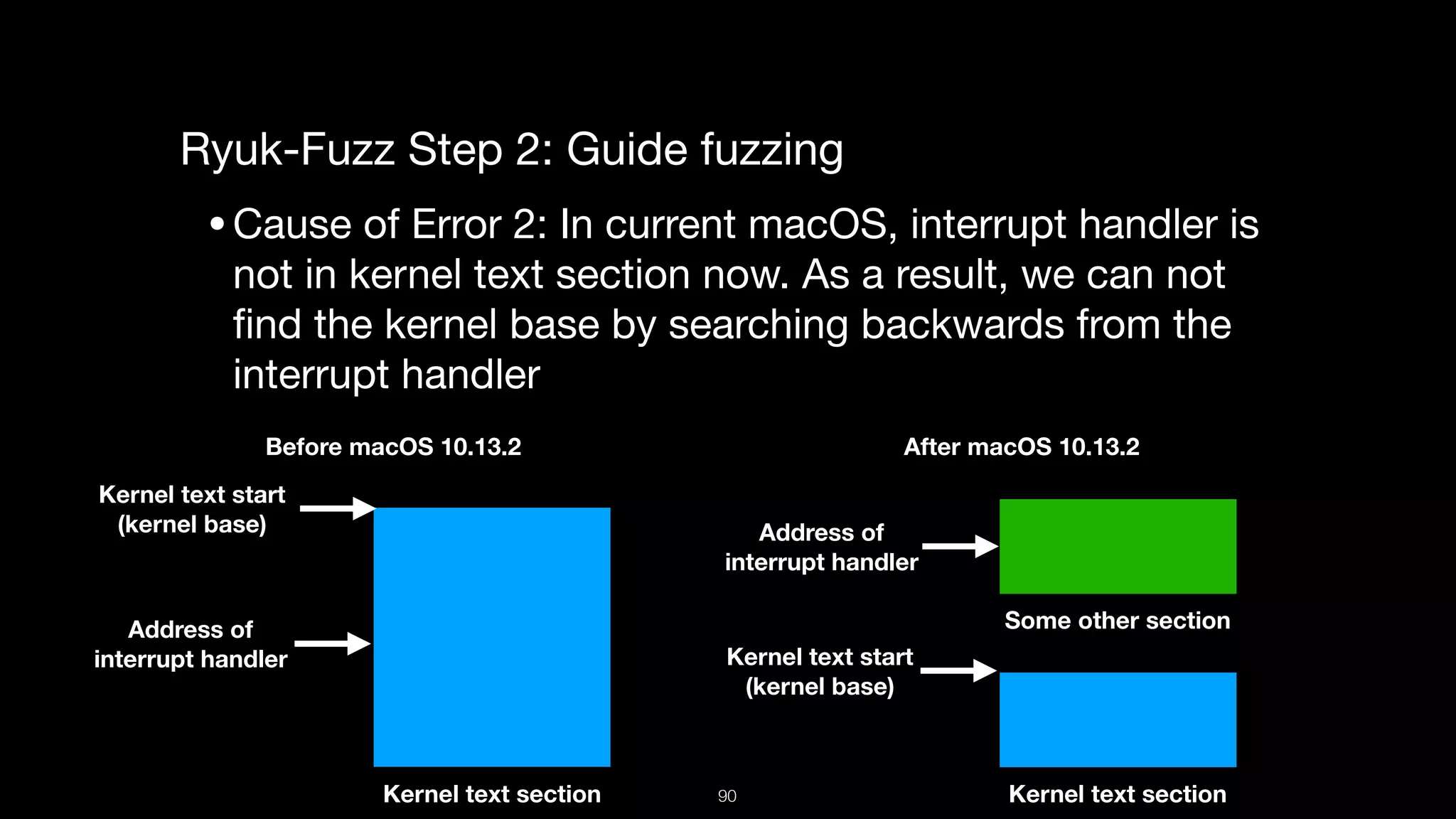
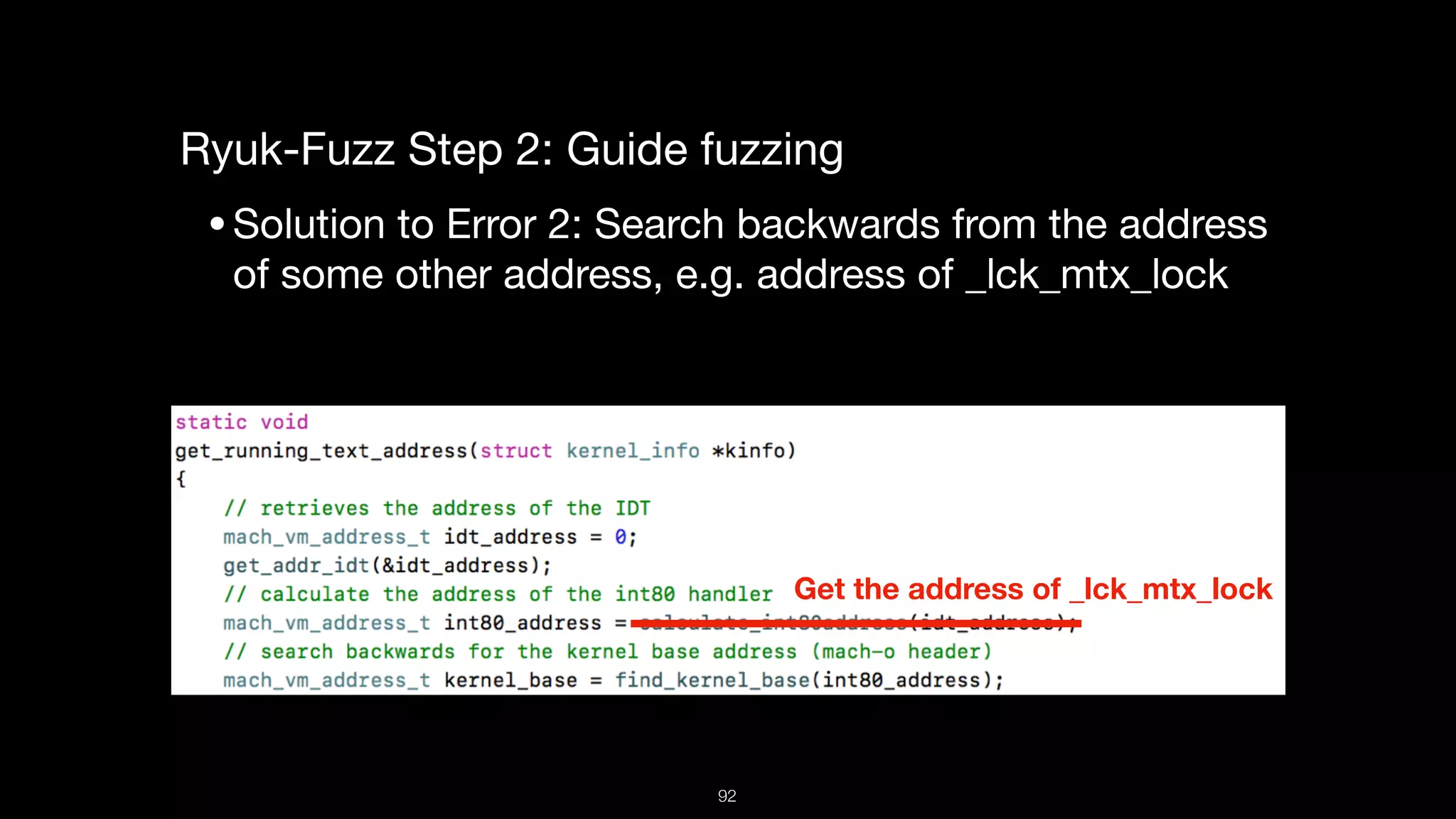
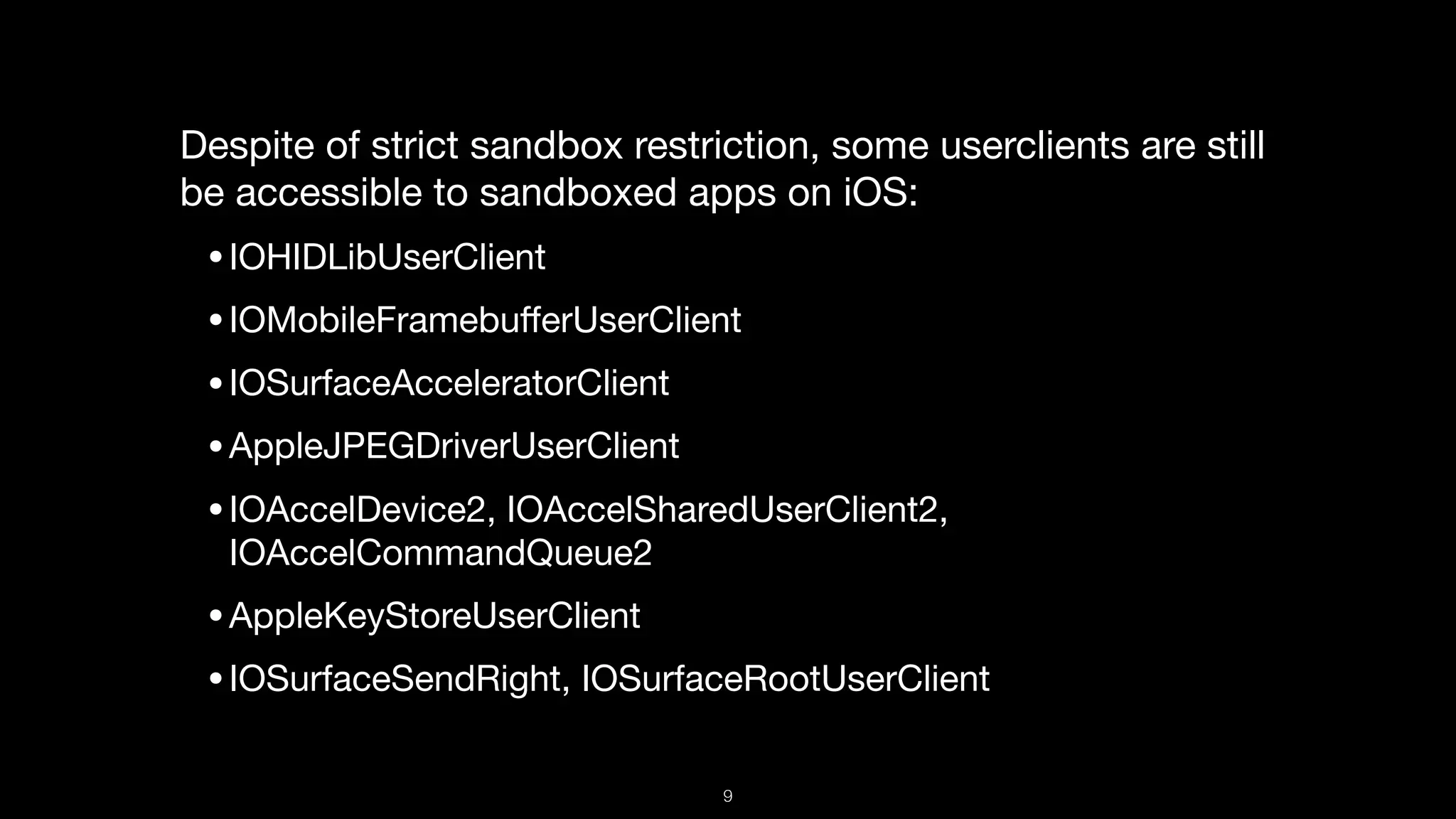
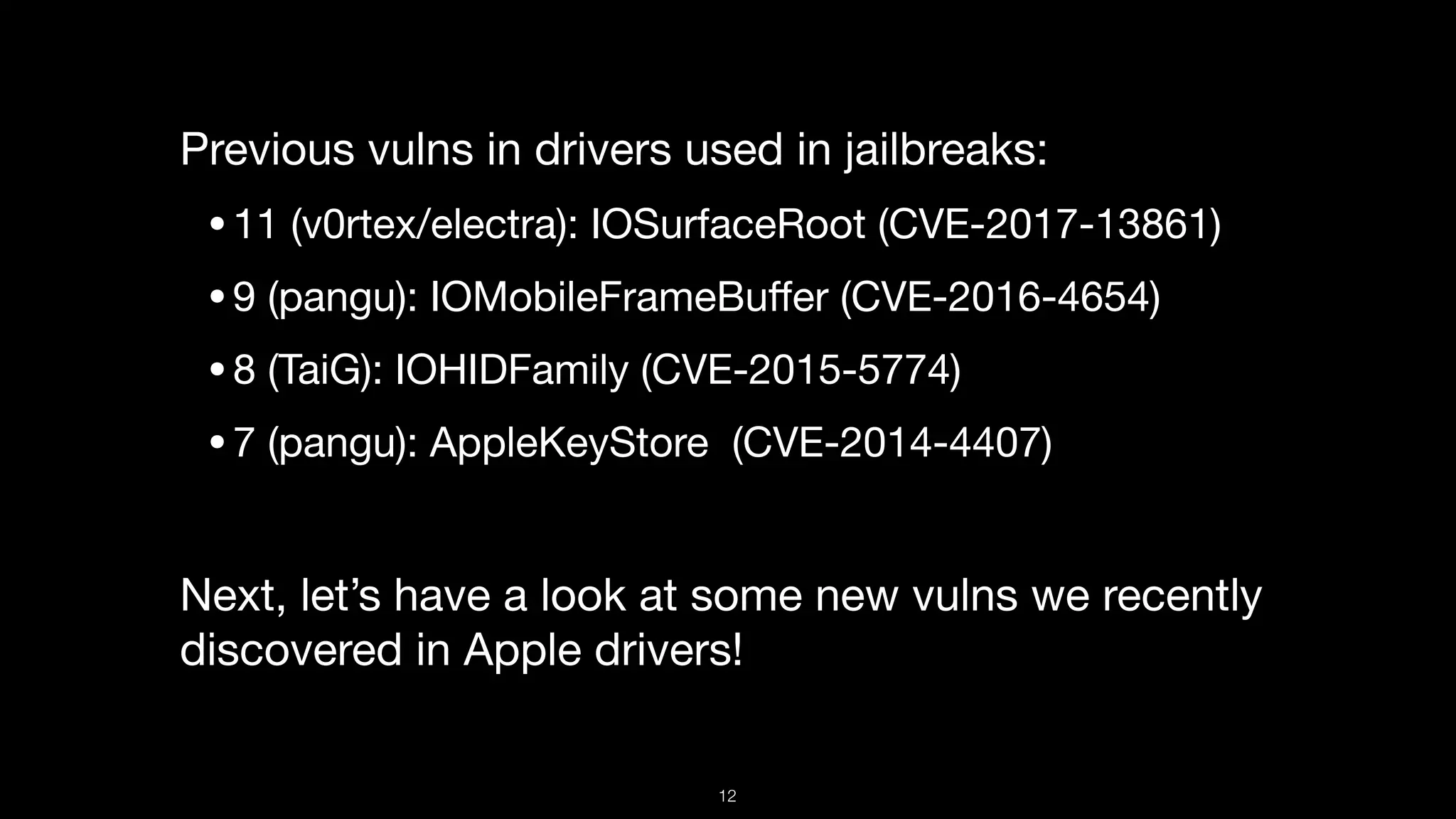
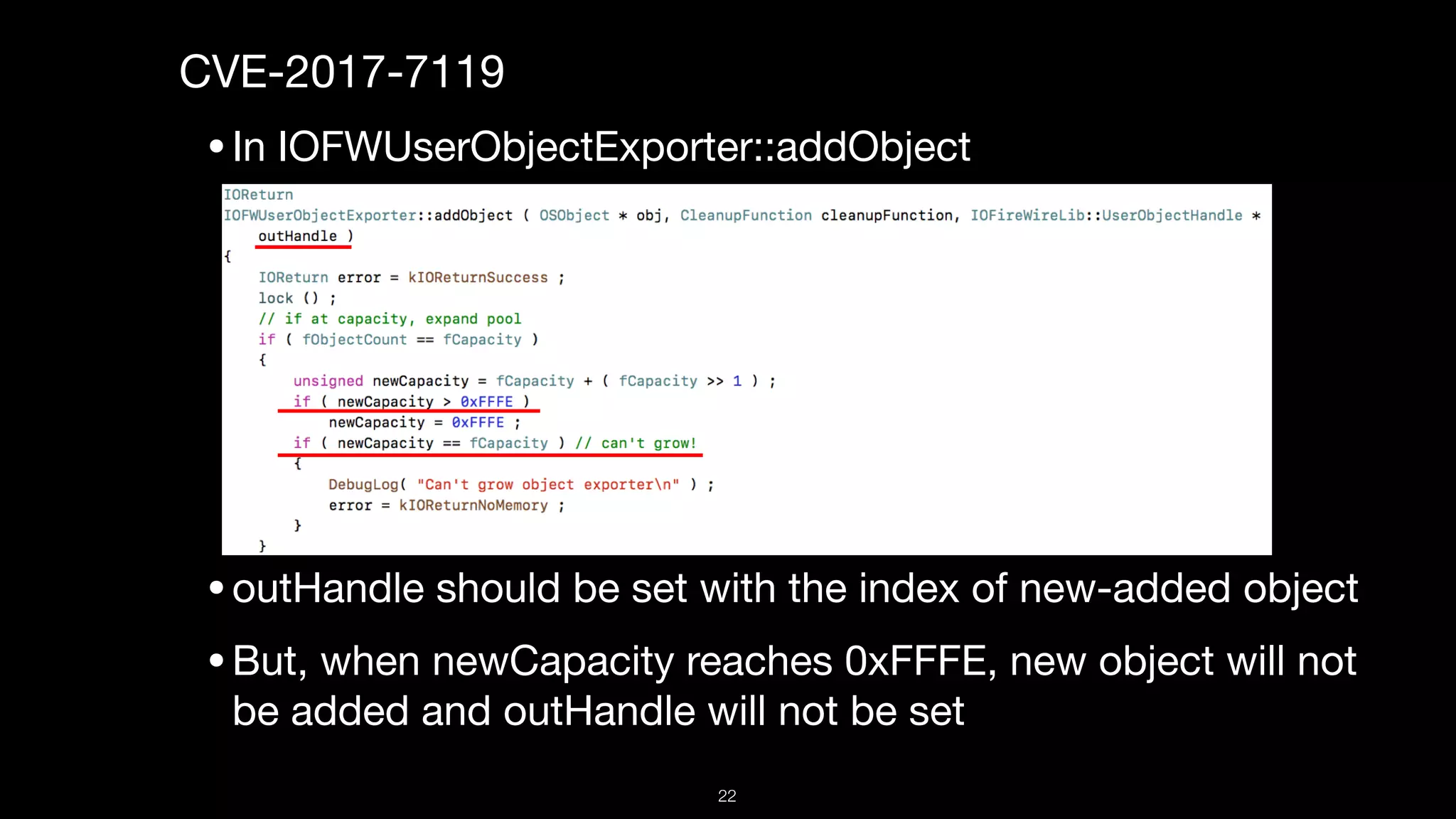
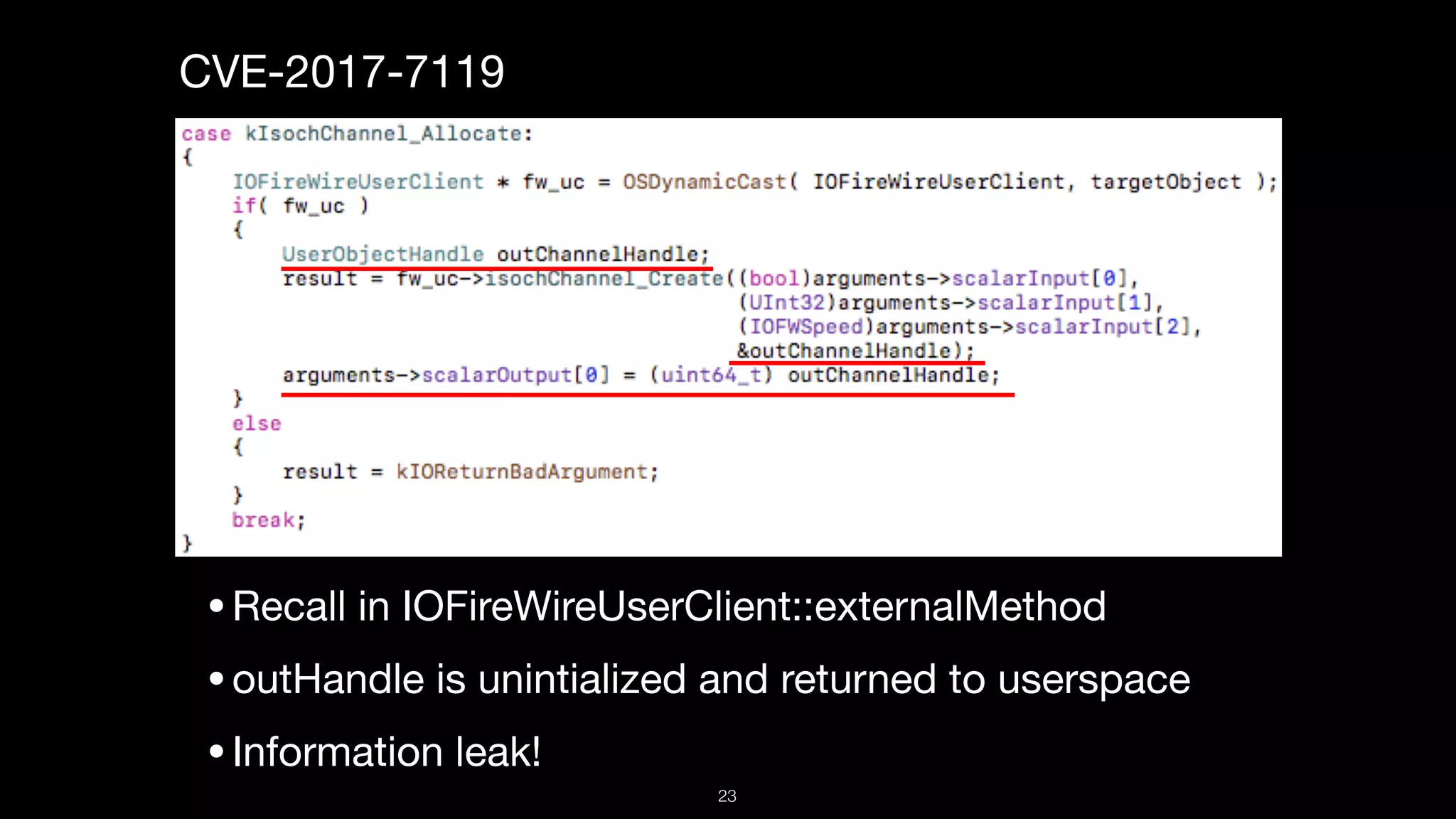
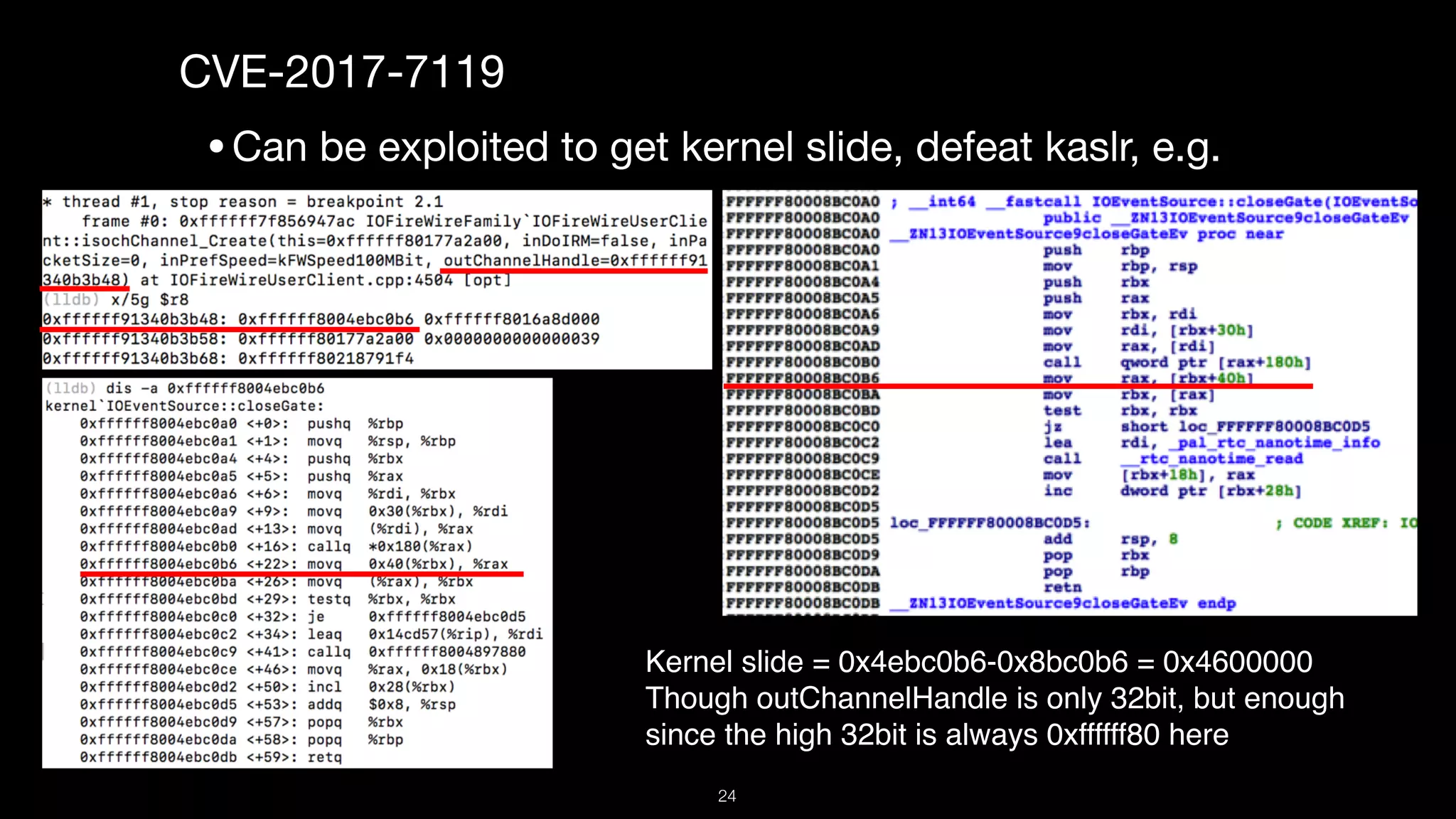
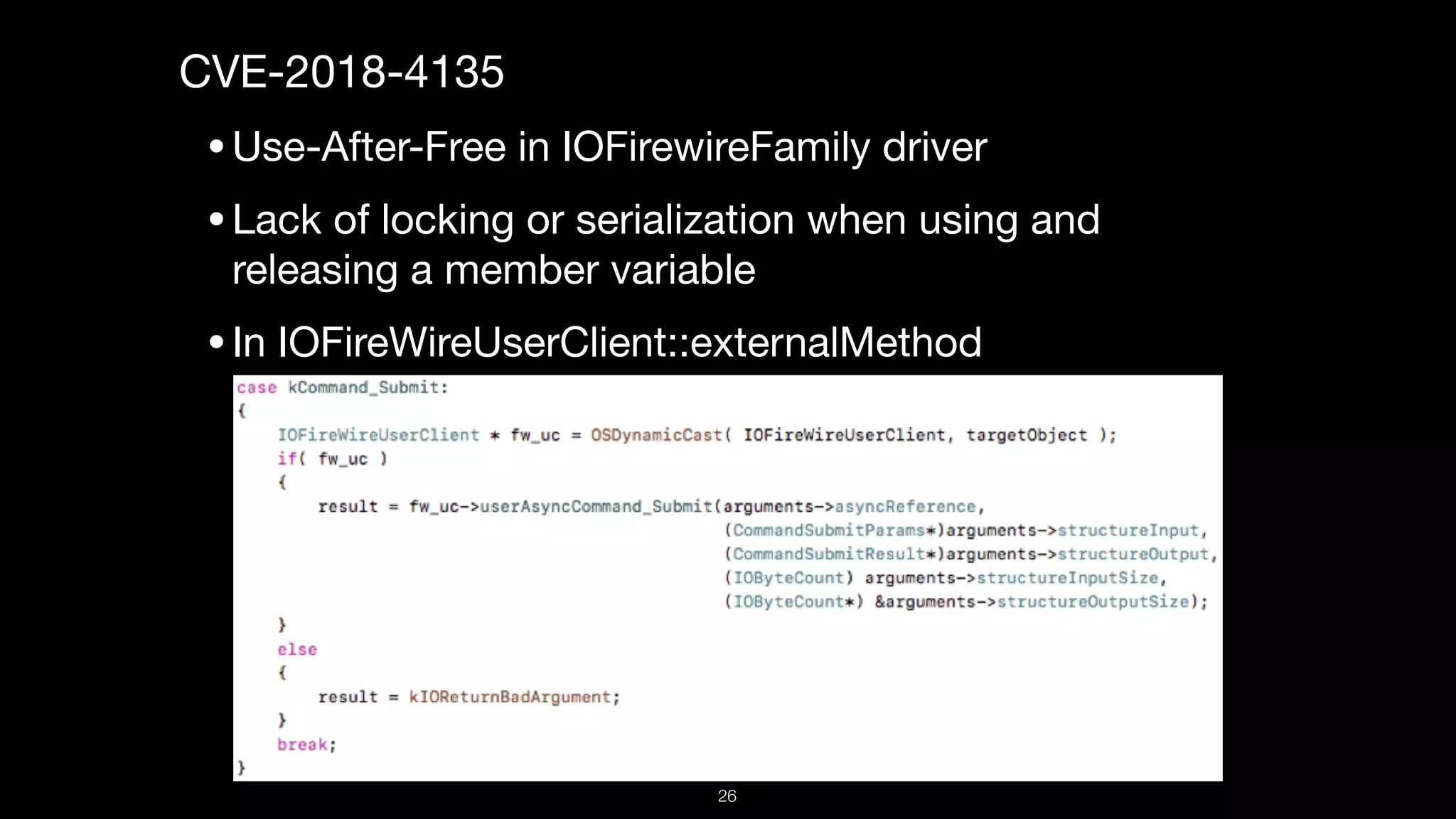
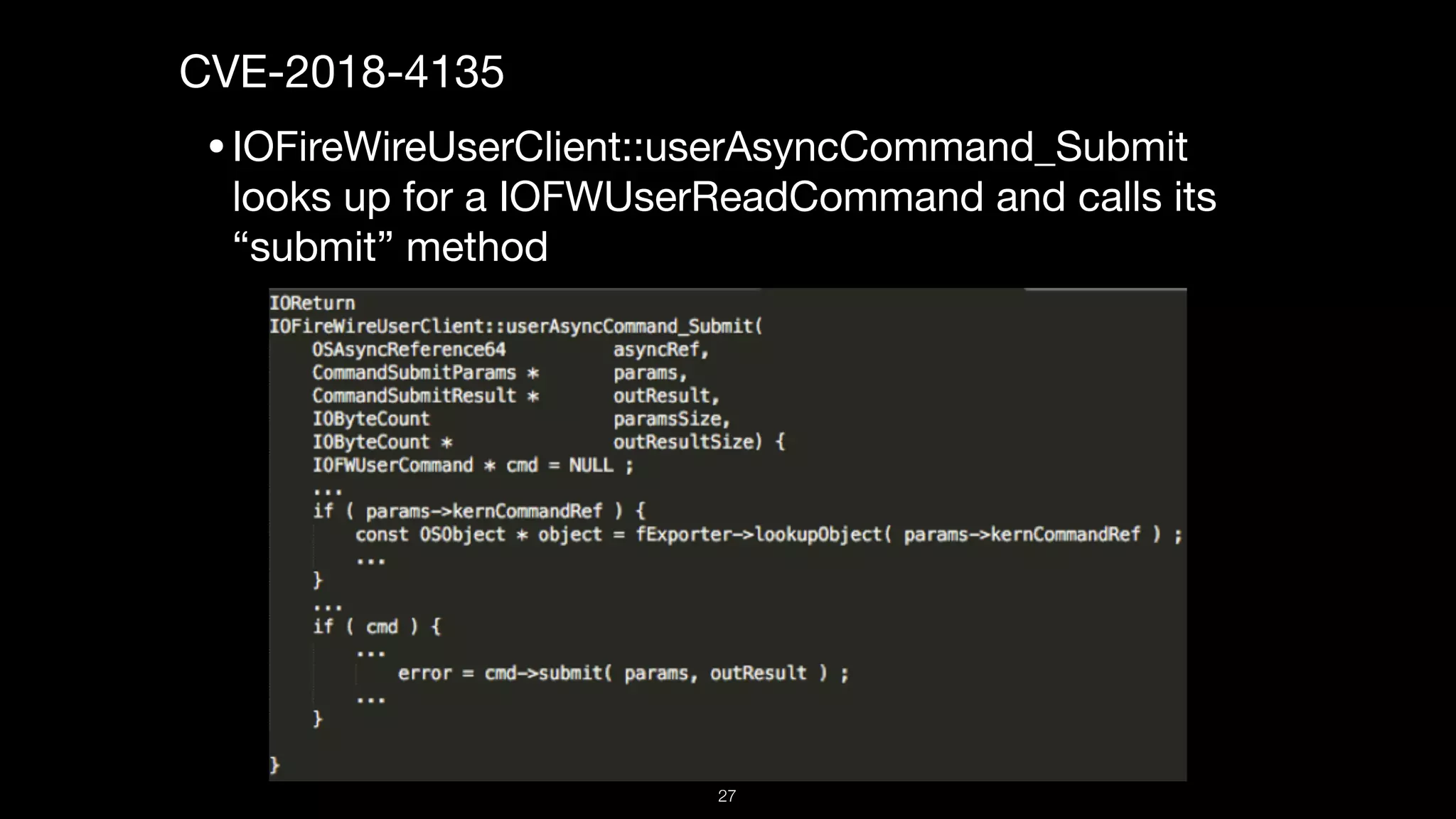
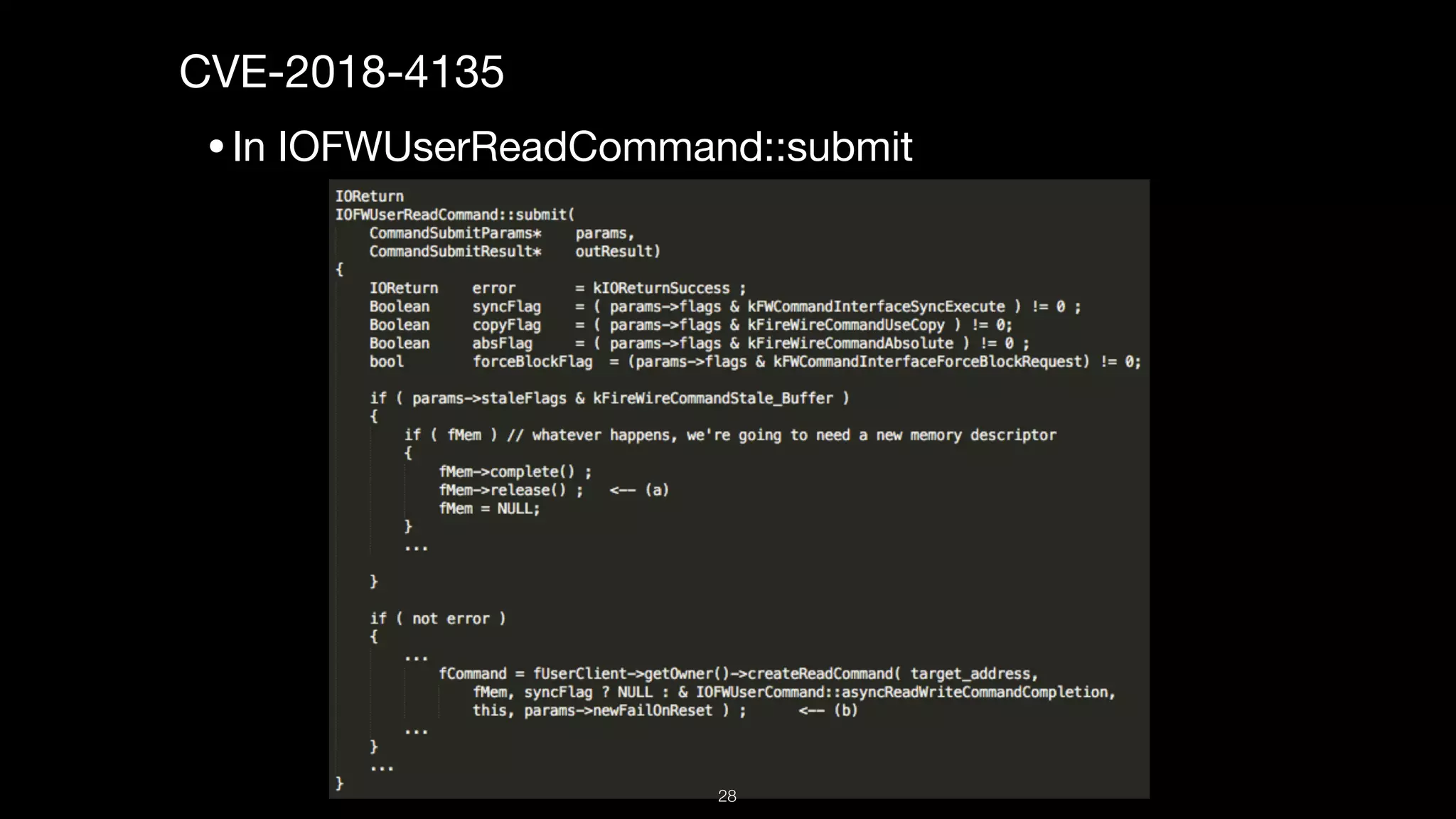
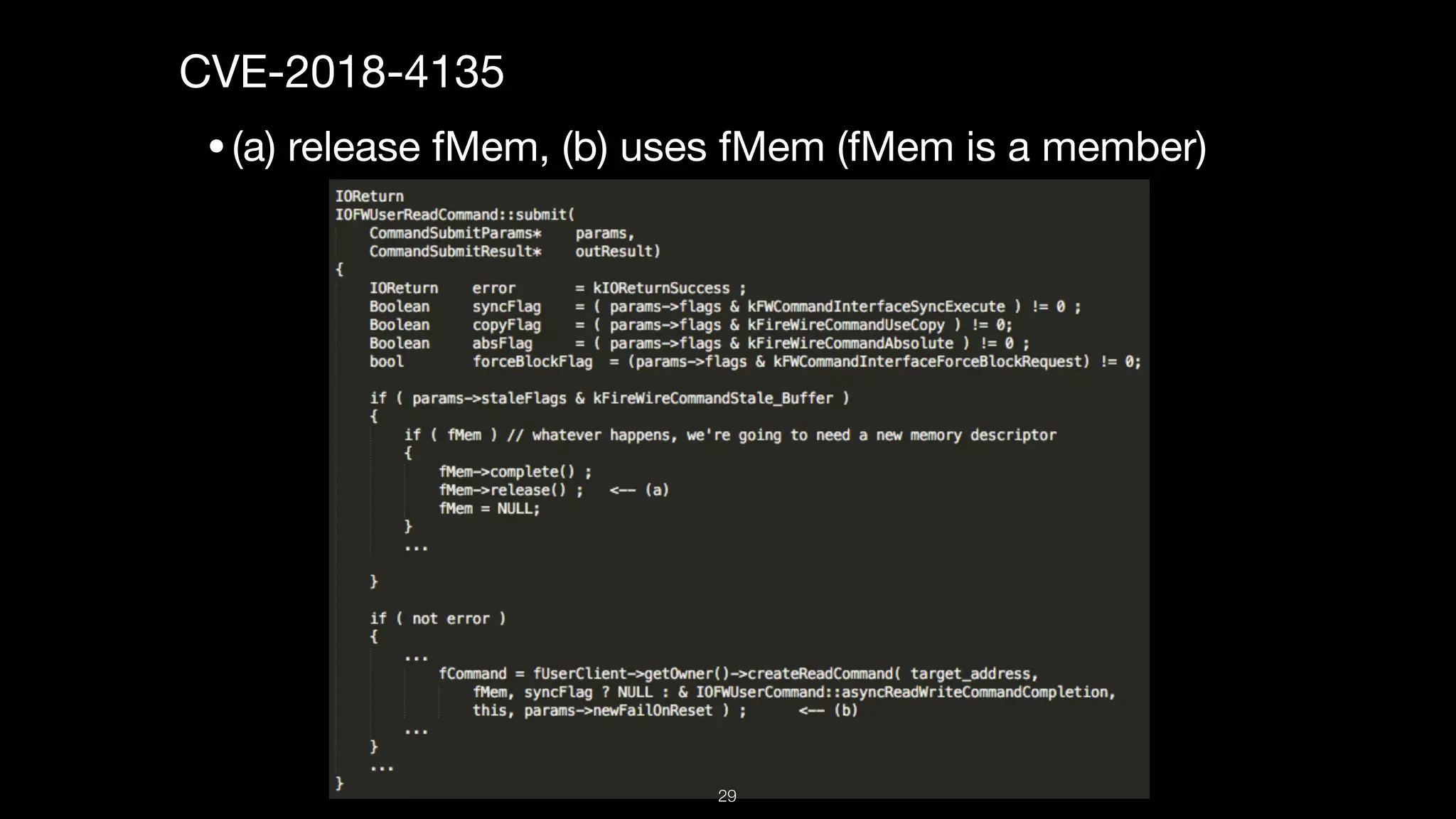
This document presents a comprehensive analysis of vulnerabilities in Apple kernel drivers, detailing new exploits discovered in drivers such as ioacceleratorfamily2 and iofirewirefamily. It introduces a static analysis tool called Ryuk designed to aid in the reverse engineering of these drivers to address challenges posed by their closed-source nature. The analysis discusses various methods for exploiting drivers and highlights the importance of understanding driver structure and function in security research.






![Layout of gadgets in a ROP chain
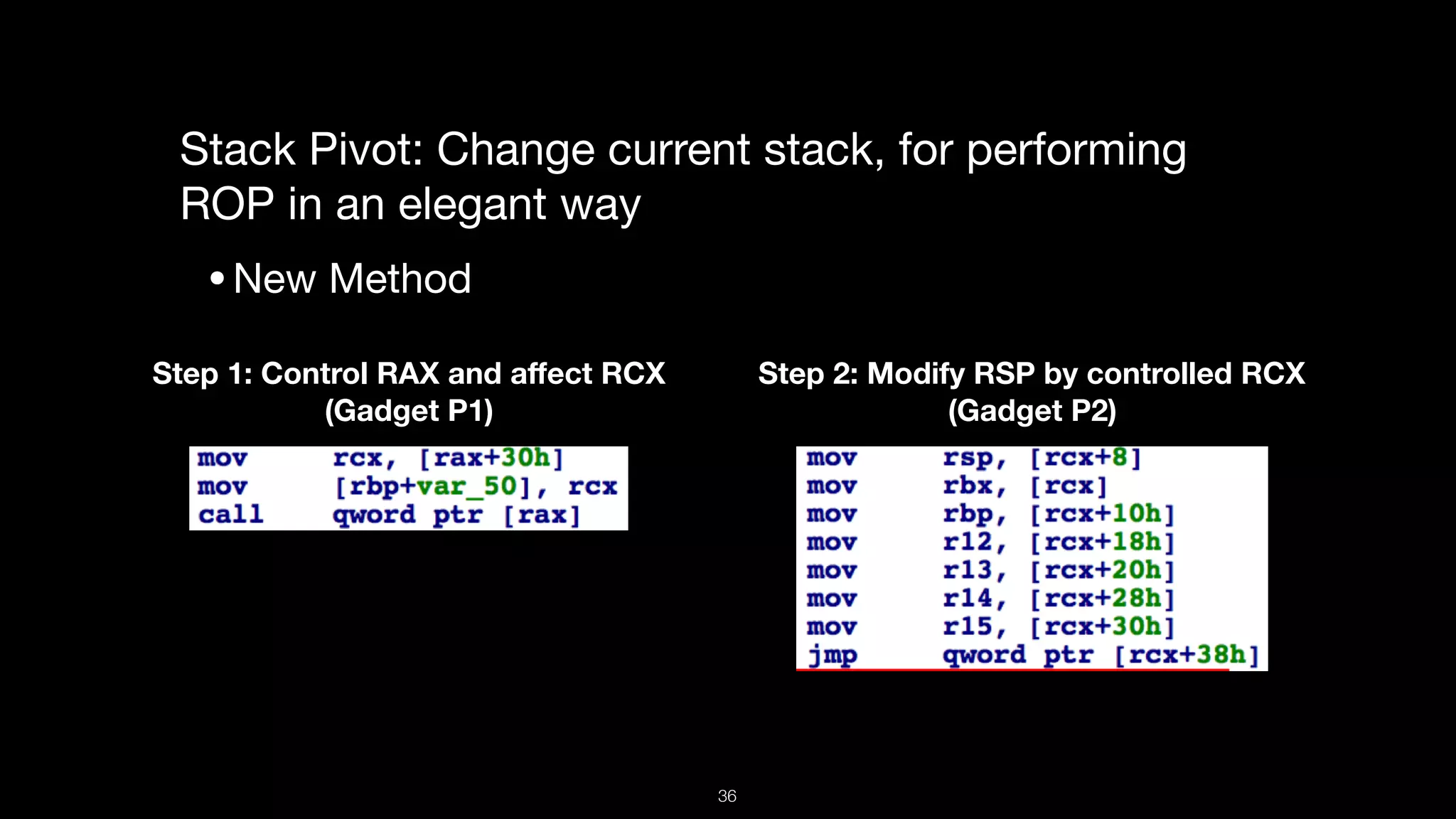
•Assume: RAX is controlled and [RAX+0x10] is to be called
•Store address X in RAX, X contains a ROP chain
Addr of Gadget P2
New RSP: X+0x50
Addr of Gadget P1
X
Addr of Gadget “NOP; RET;”
Addr of _current_proc and Gadget “MOV RDI, RAX”
Address of _proc_ucred and Gadget “MOV RDI, RAX”
Address of _posix_cred_get and Gadget “MOV RDI, RAX”
Addr of _bzero
X
X+0x8
Addr of G_thread_exception_return
…
X+0x10, ROP starts from here
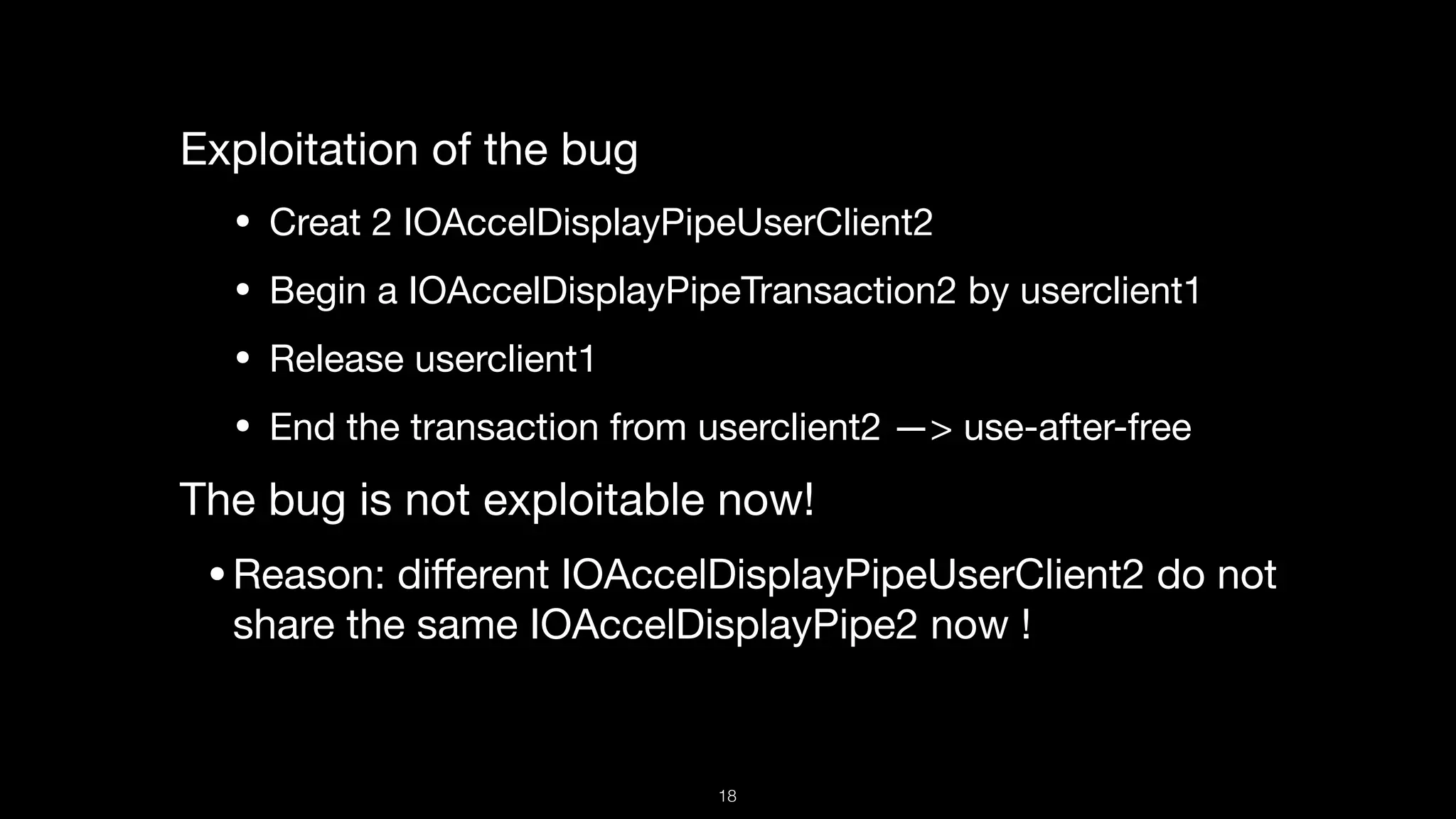
X+0x30
X+0x38
X+0x40, start privilege escalation
Content Address
37](https://image.slidesharecdn.com/defcon-26-xiaolong-bai-and-min-zheng-one-bite-and-all-your-dreams-will-come-true-180925080322/75/One-bite-and-all-your-dreams-will-come-true-Analyzing-and-Attacking-Apple-Kernel-Drivers-37-2048.jpg)