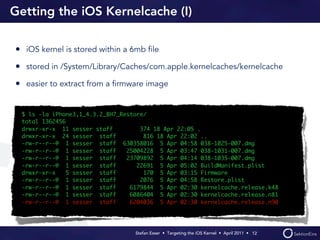
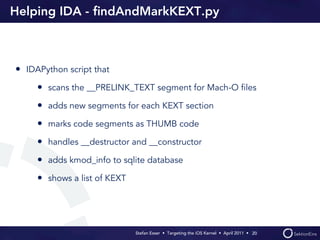
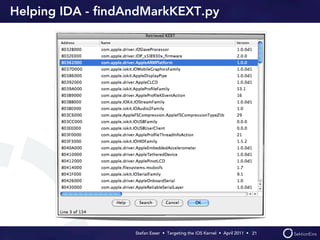
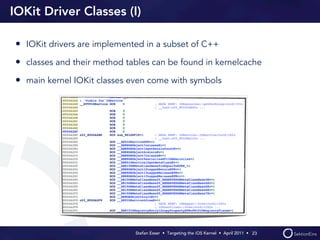
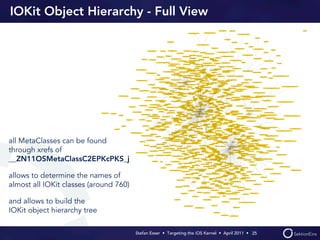
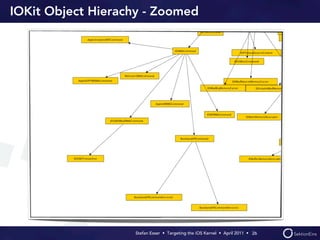
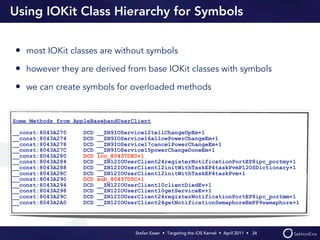
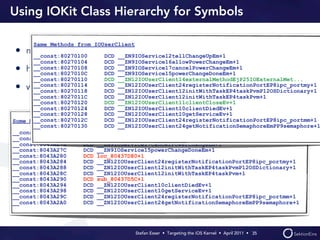
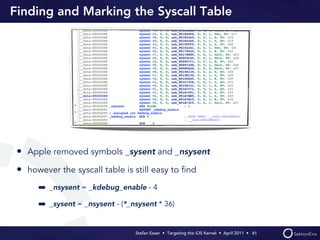
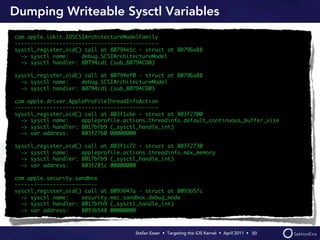
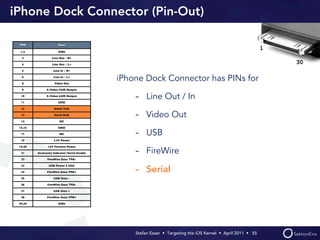
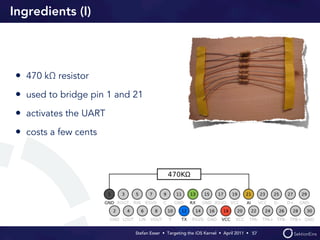
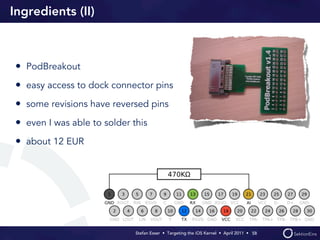
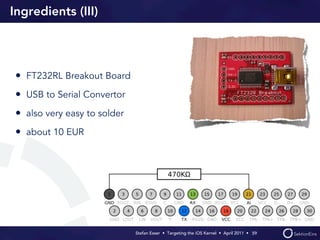
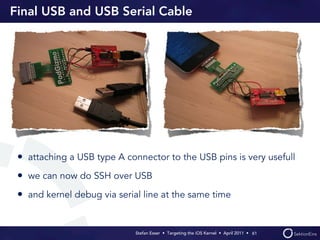
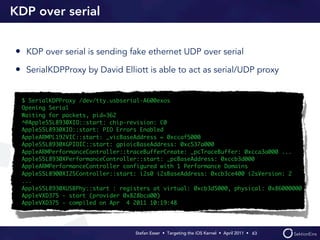
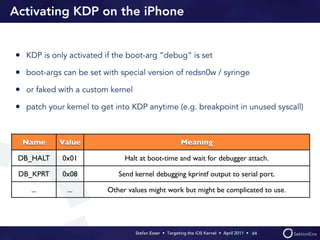
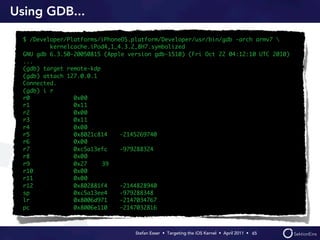
Stefan Esser's presentation focuses on finding vulnerabilities in the iOS kernel, highlighting the kernel's reliance on various protective measures and the limited public exploit payloads available. The session outlines methodologies for obtaining the iOS kernelcache, analyzing its contents, and utilizing tools for debugging, while also addressing the challenges of symbol extraction. Additionally, Esser discusses the differences between the iOS and OS X kernels and emphasizes the need for advanced techniques to better understand and potentially exploit iOS systems.