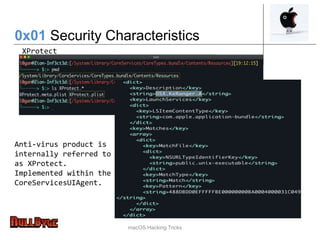
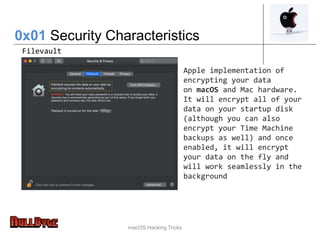
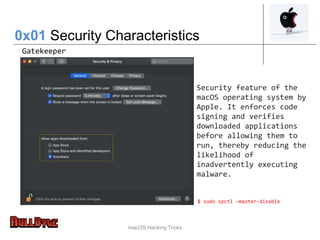
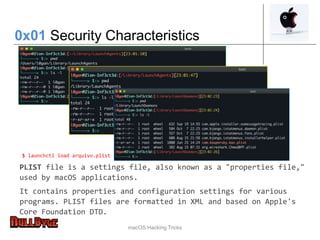
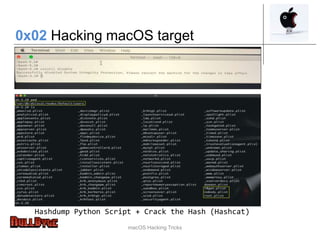
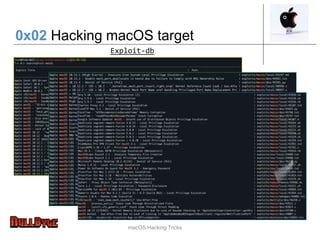
The document presents an overview of macOS security and hacking techniques, authored by Ricardo Logan, a security specialist with extensive experience. It details security features like System Integrity Protection (SIP), FileVault, and Gatekeeper, as well as common vulnerabilities and hacking methodologies targeting macOS. Additionally, it discusses various tools for exploiting and analyzing macOS systems, alongside references for further exploration in the field of macOS security research.