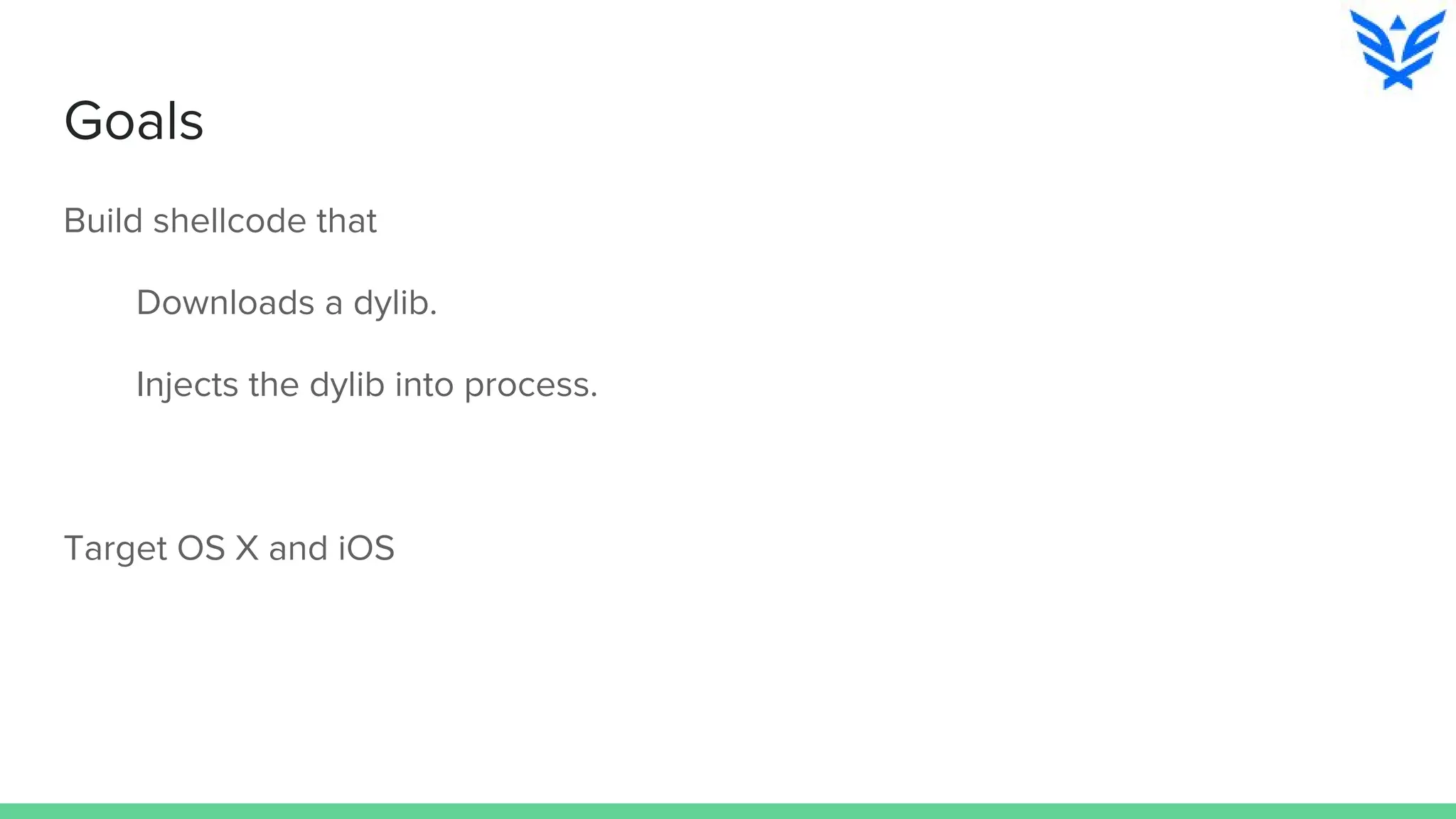
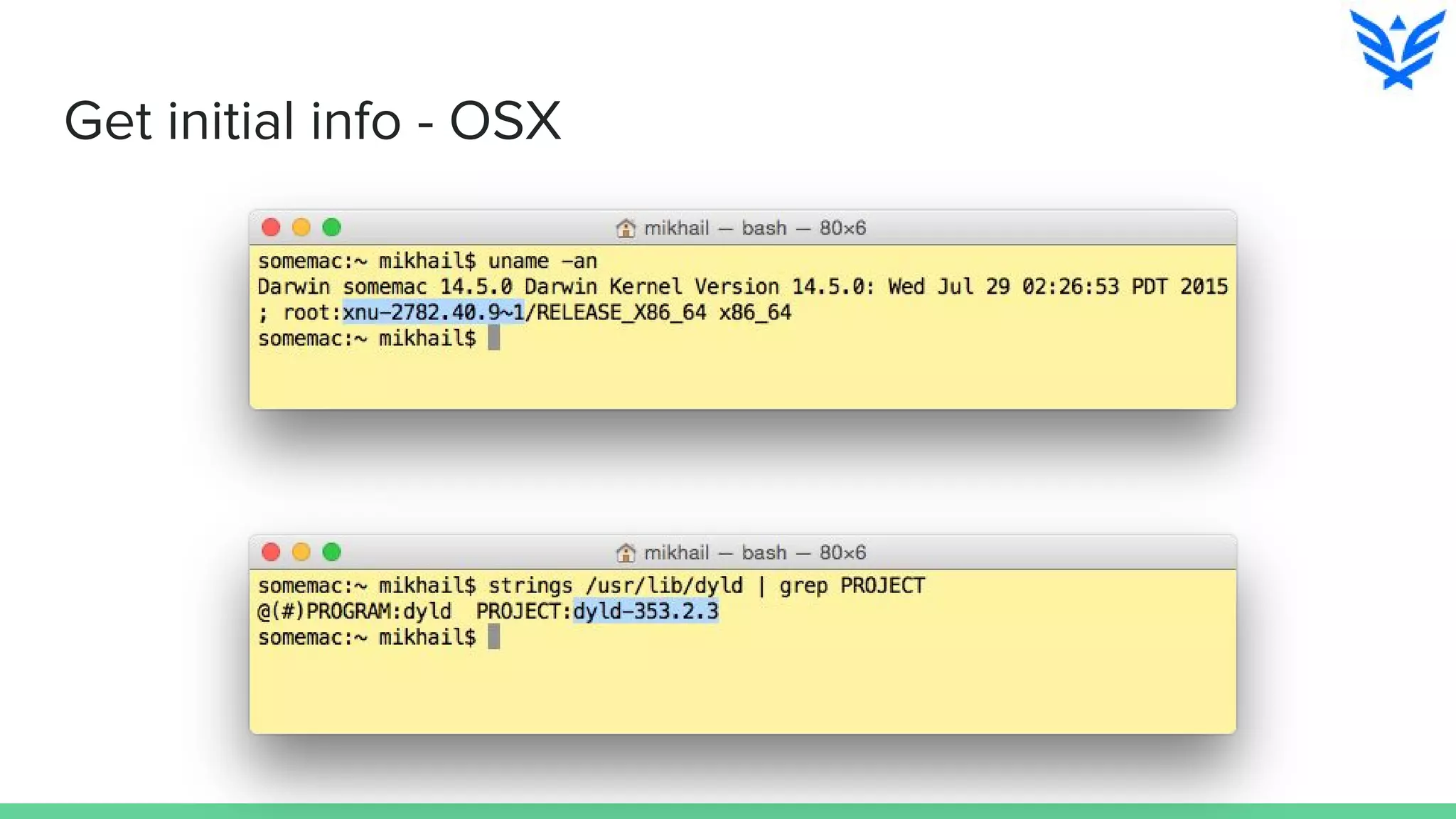
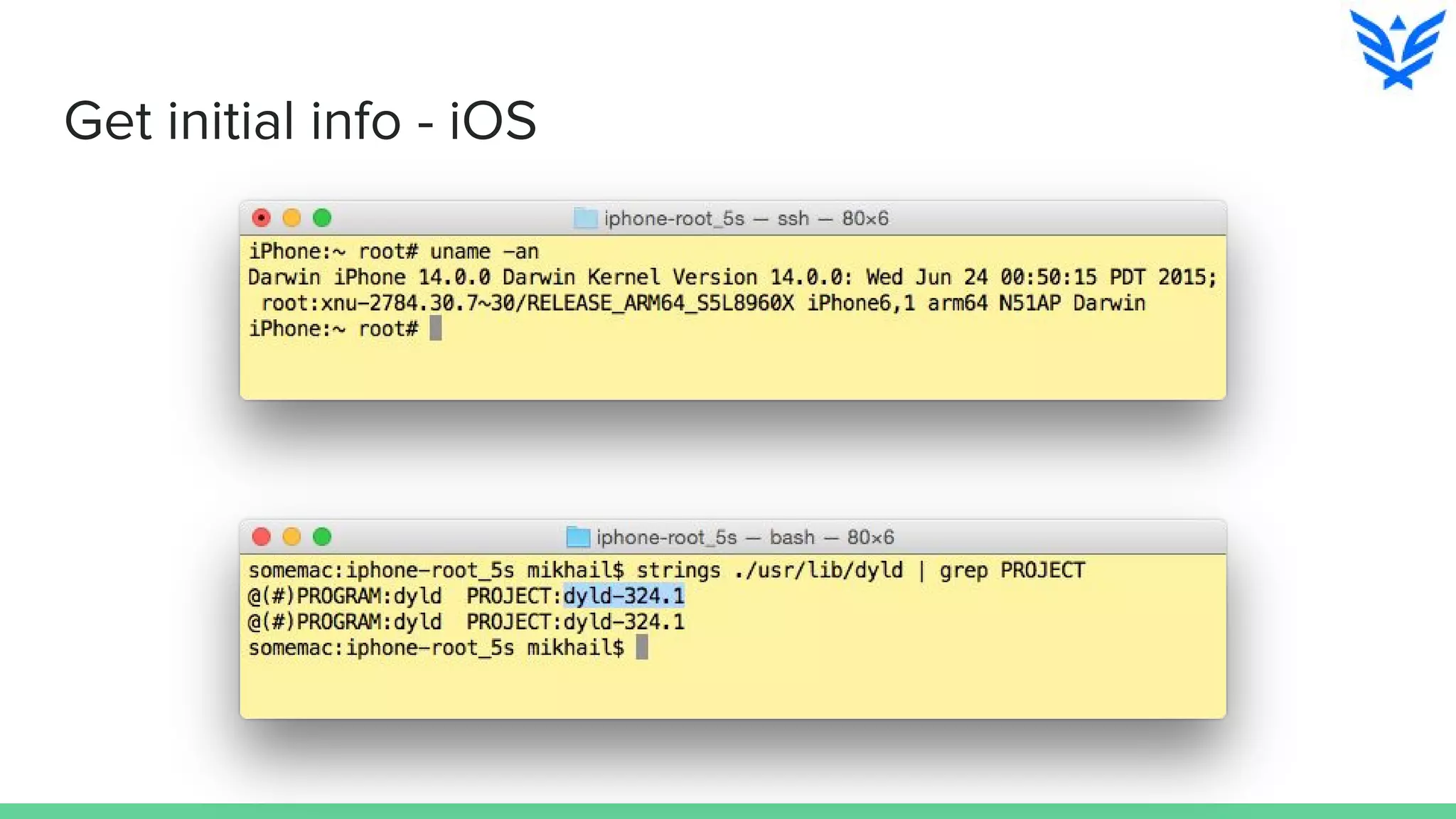
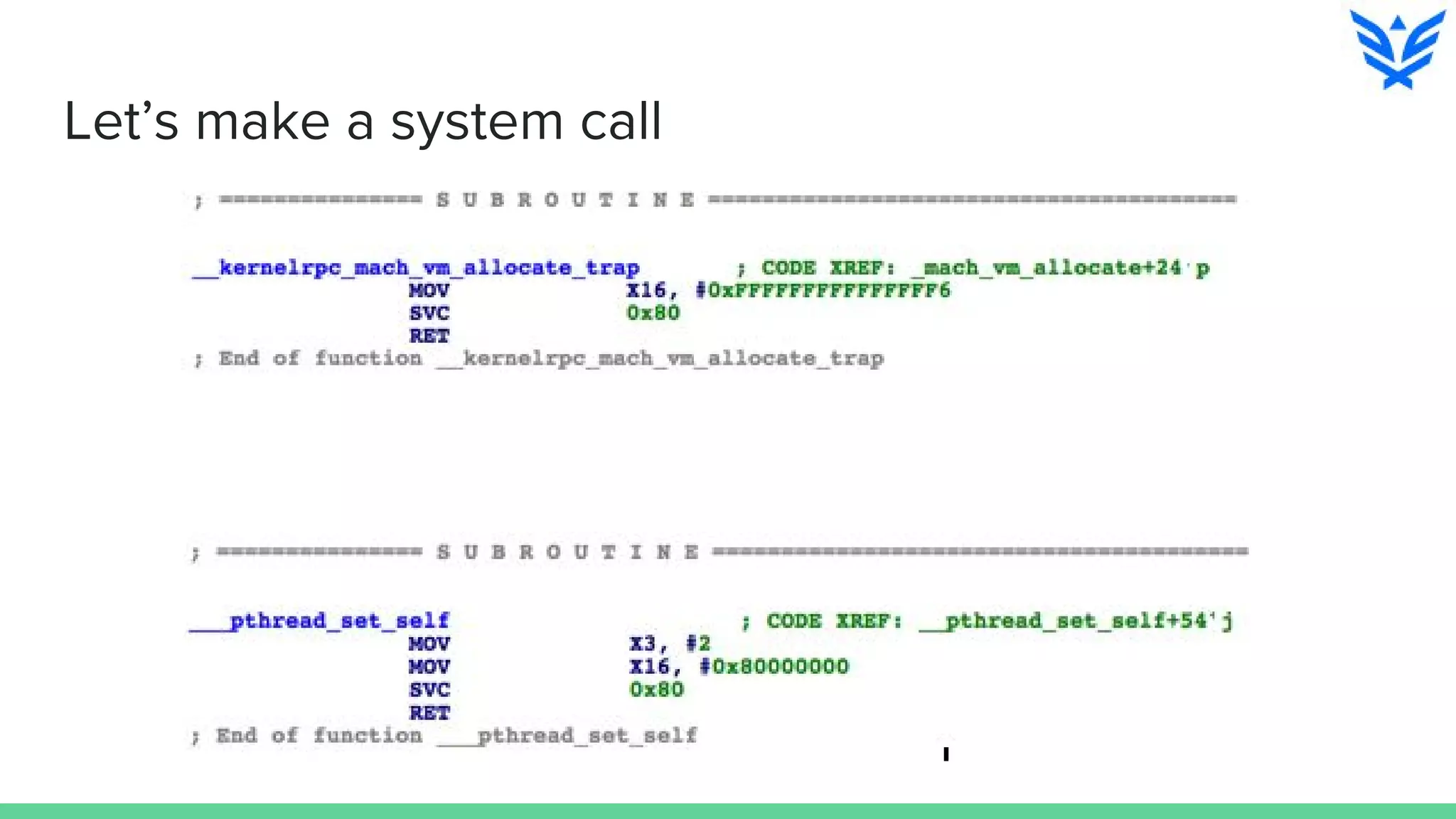
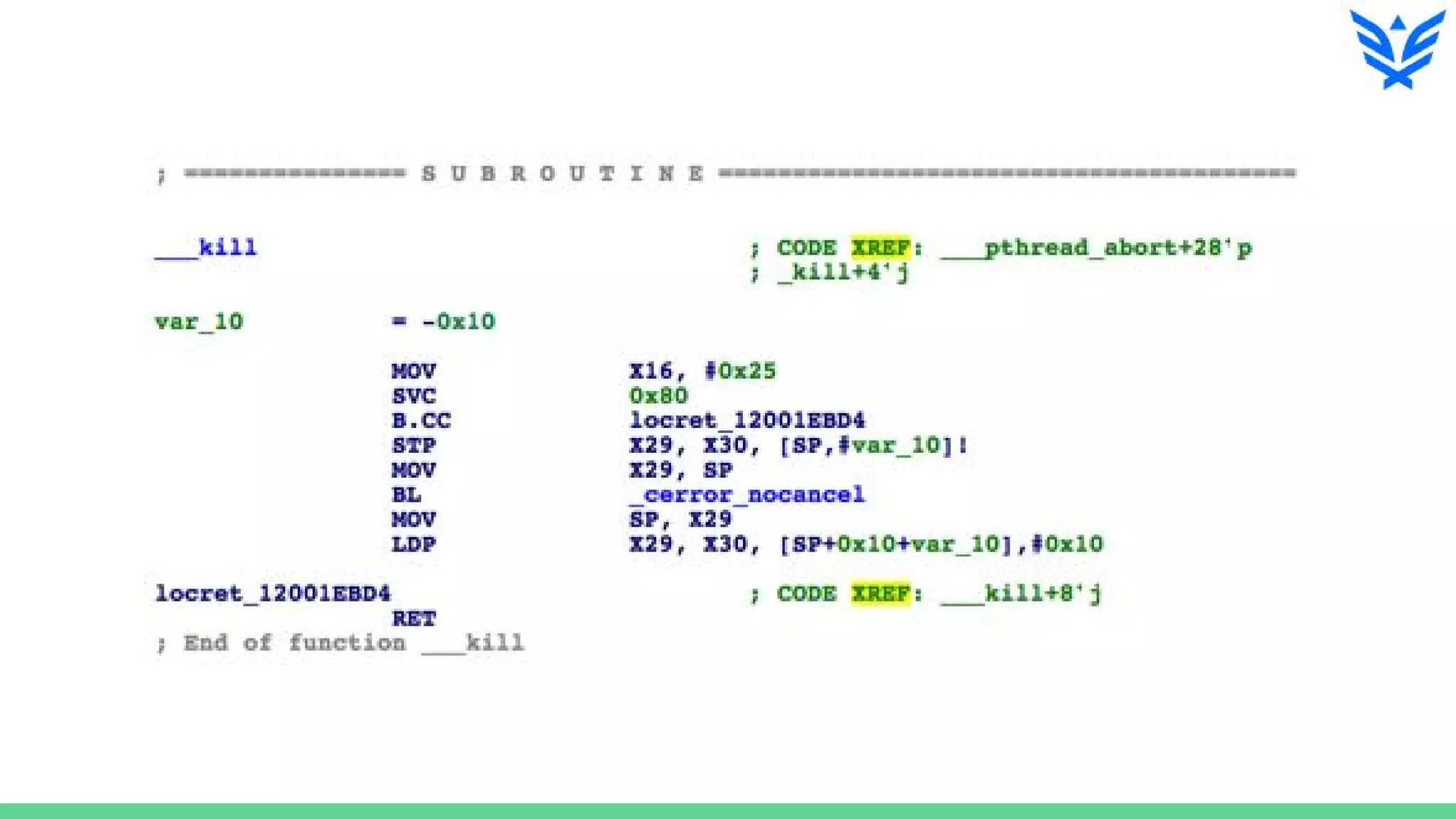
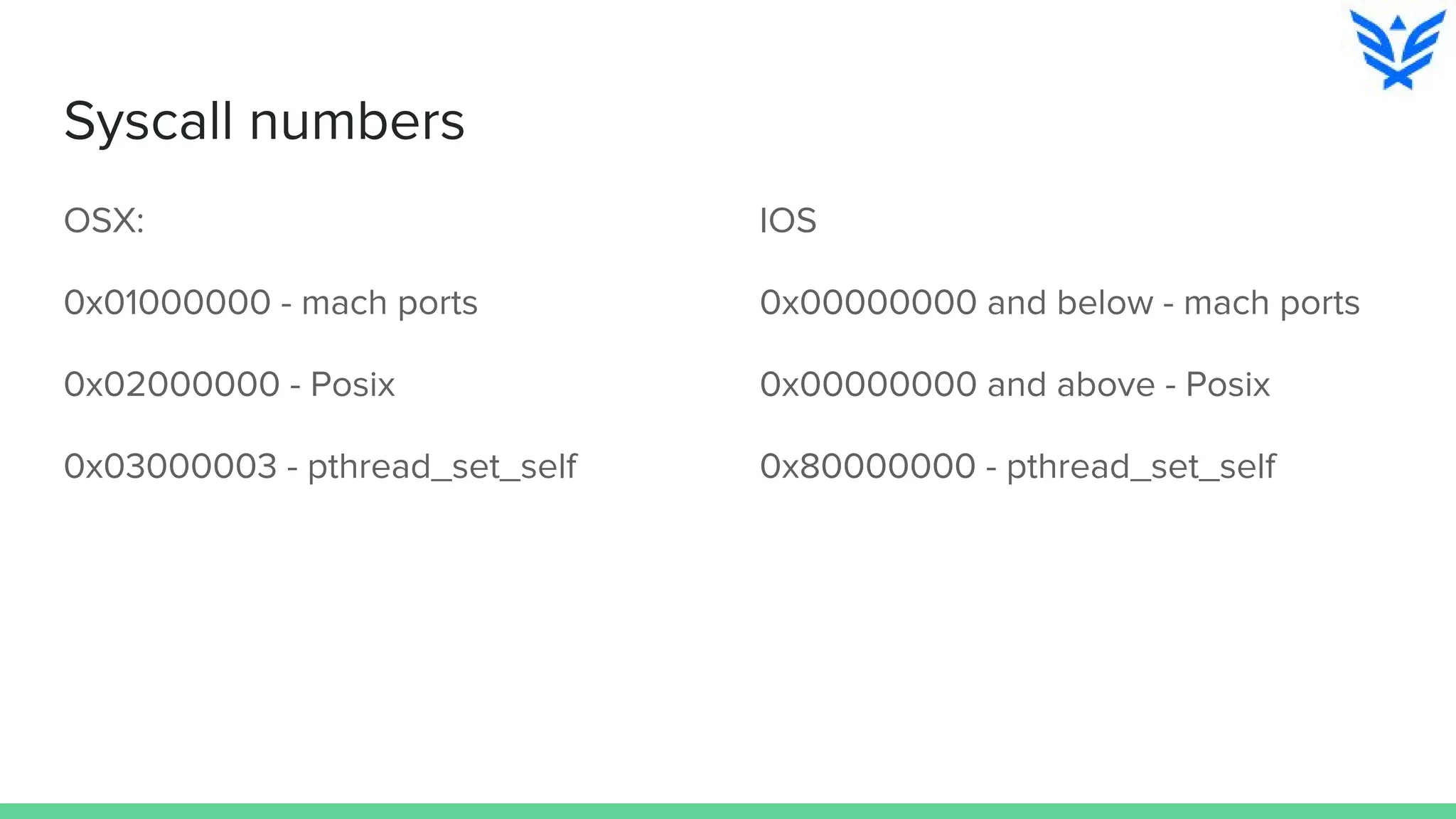
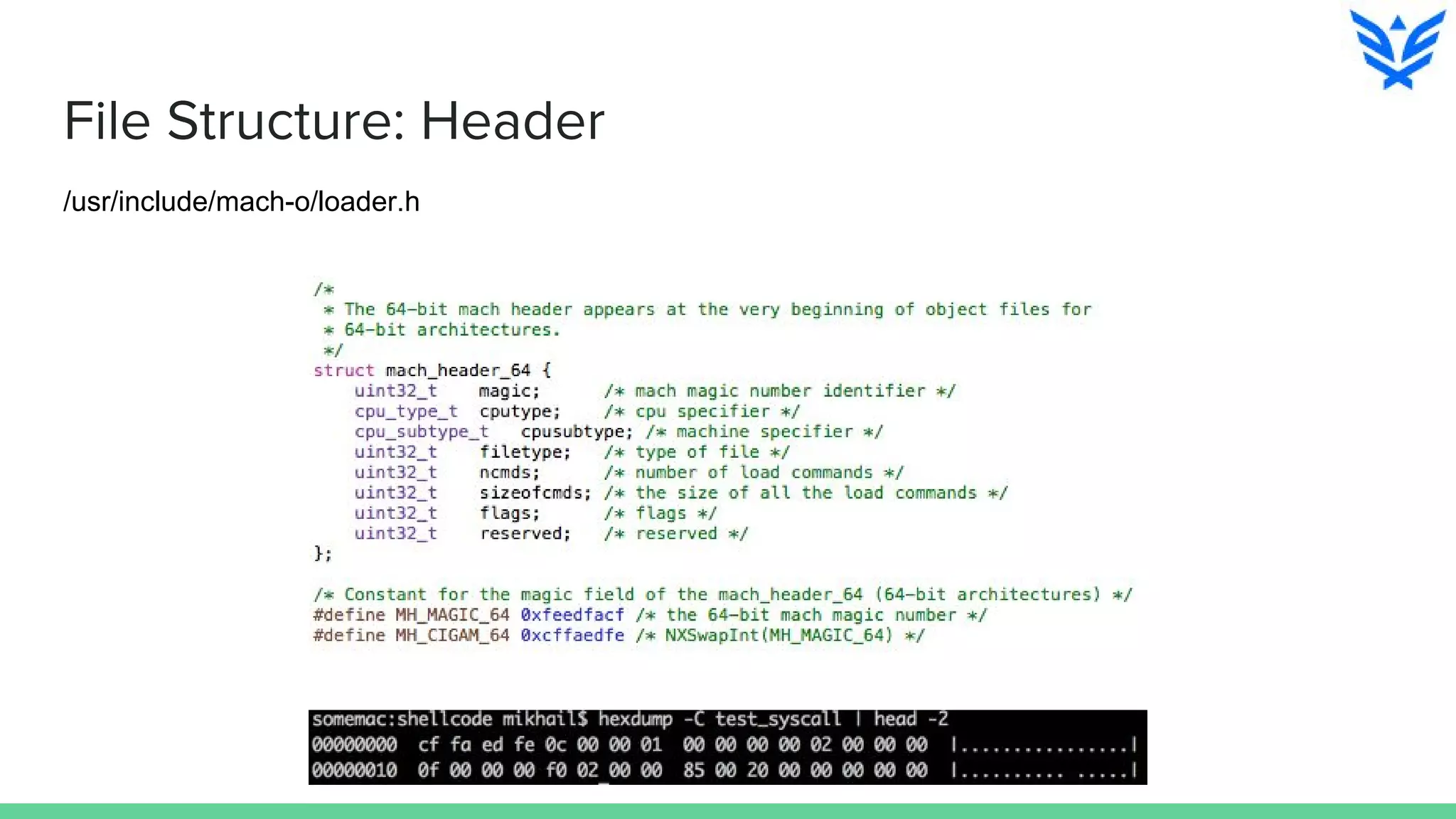
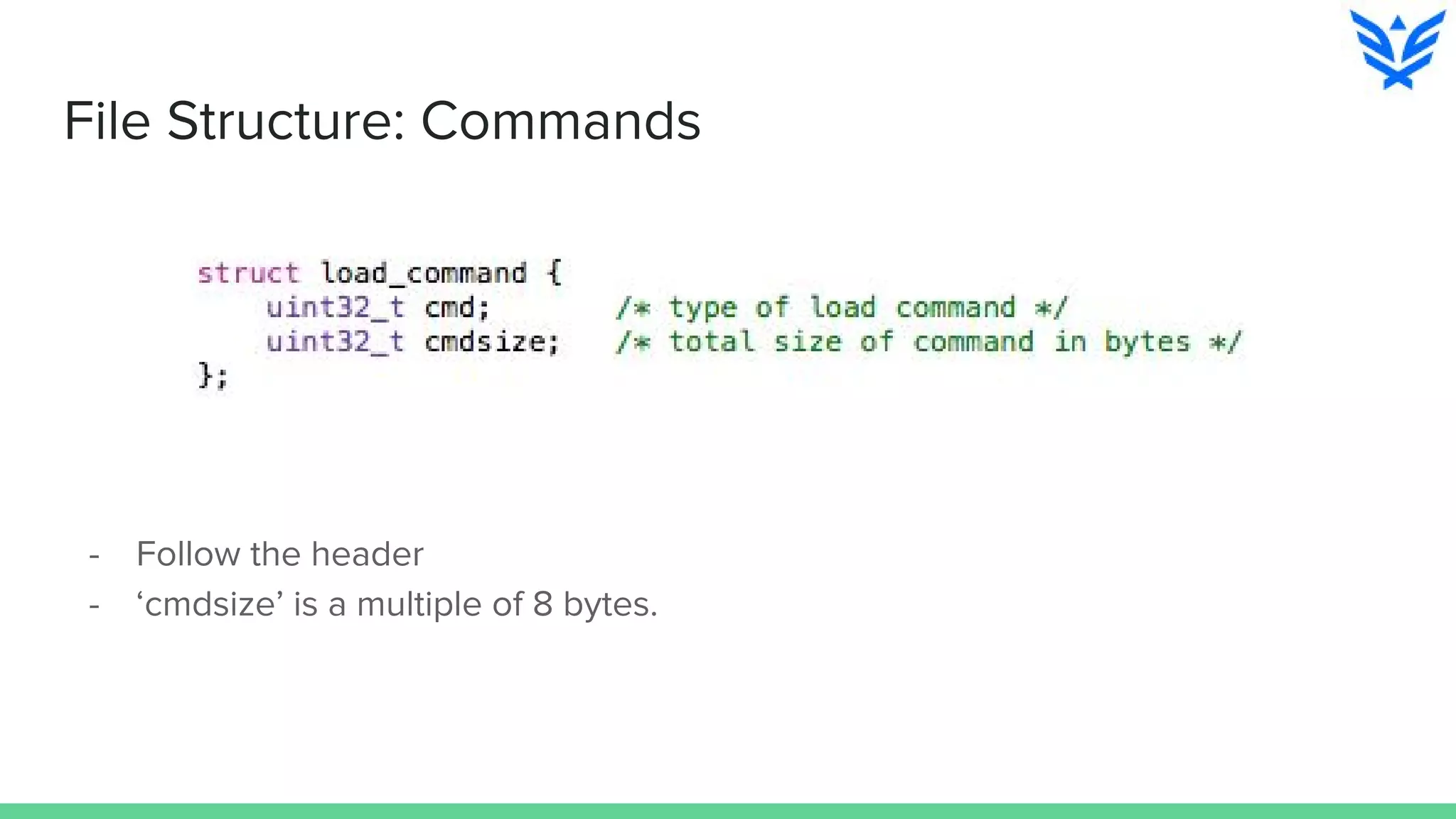
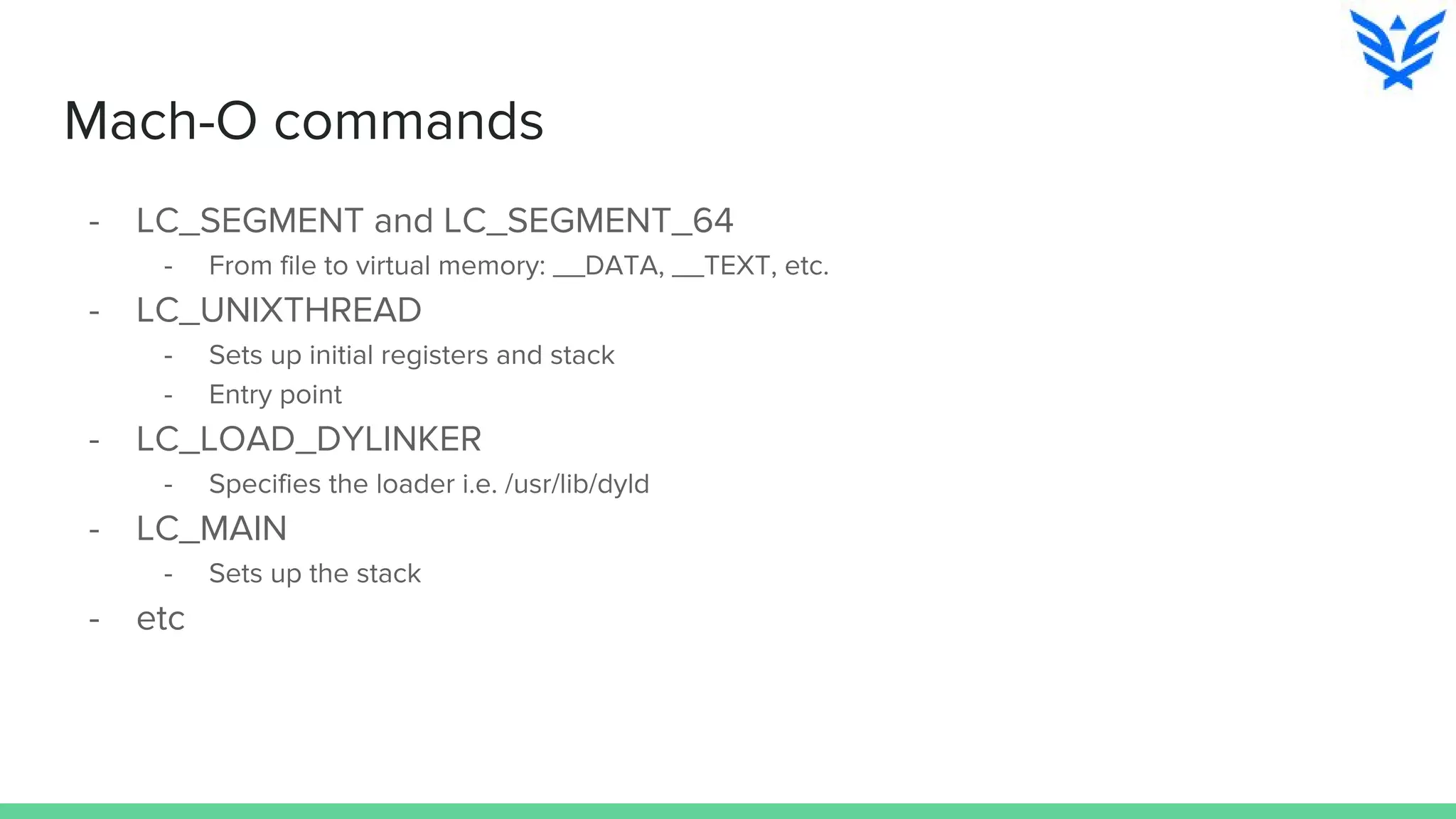
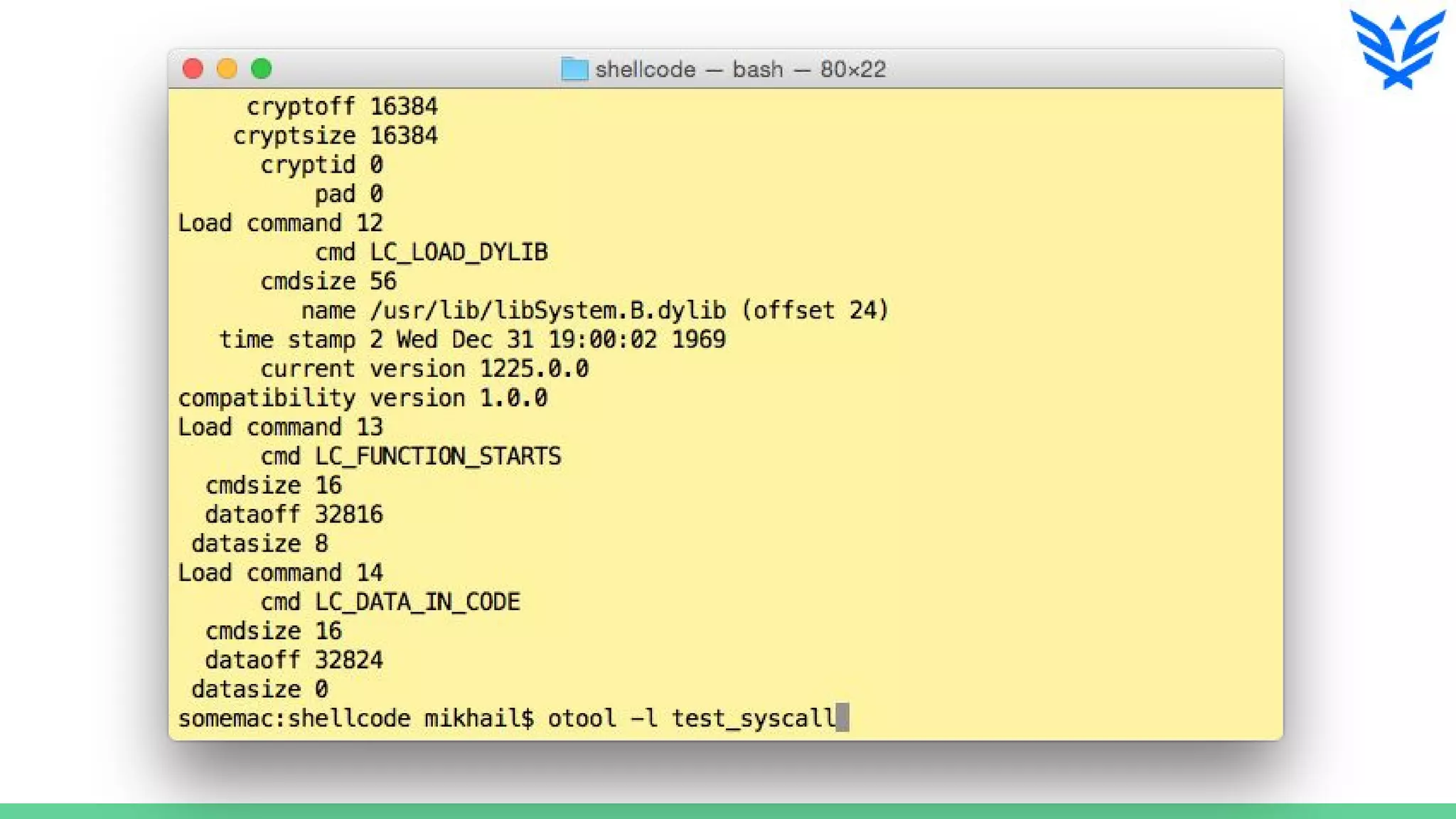
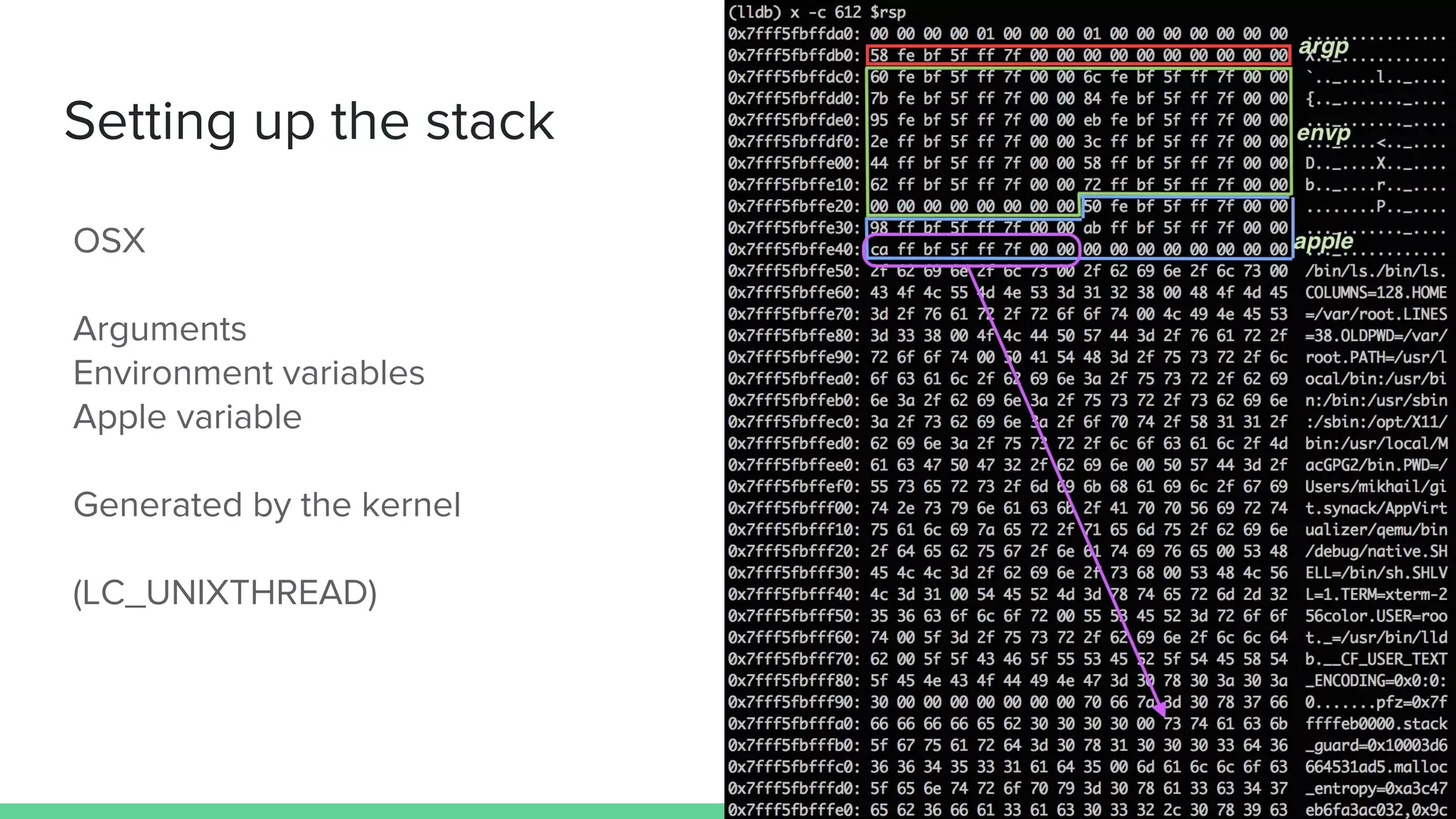
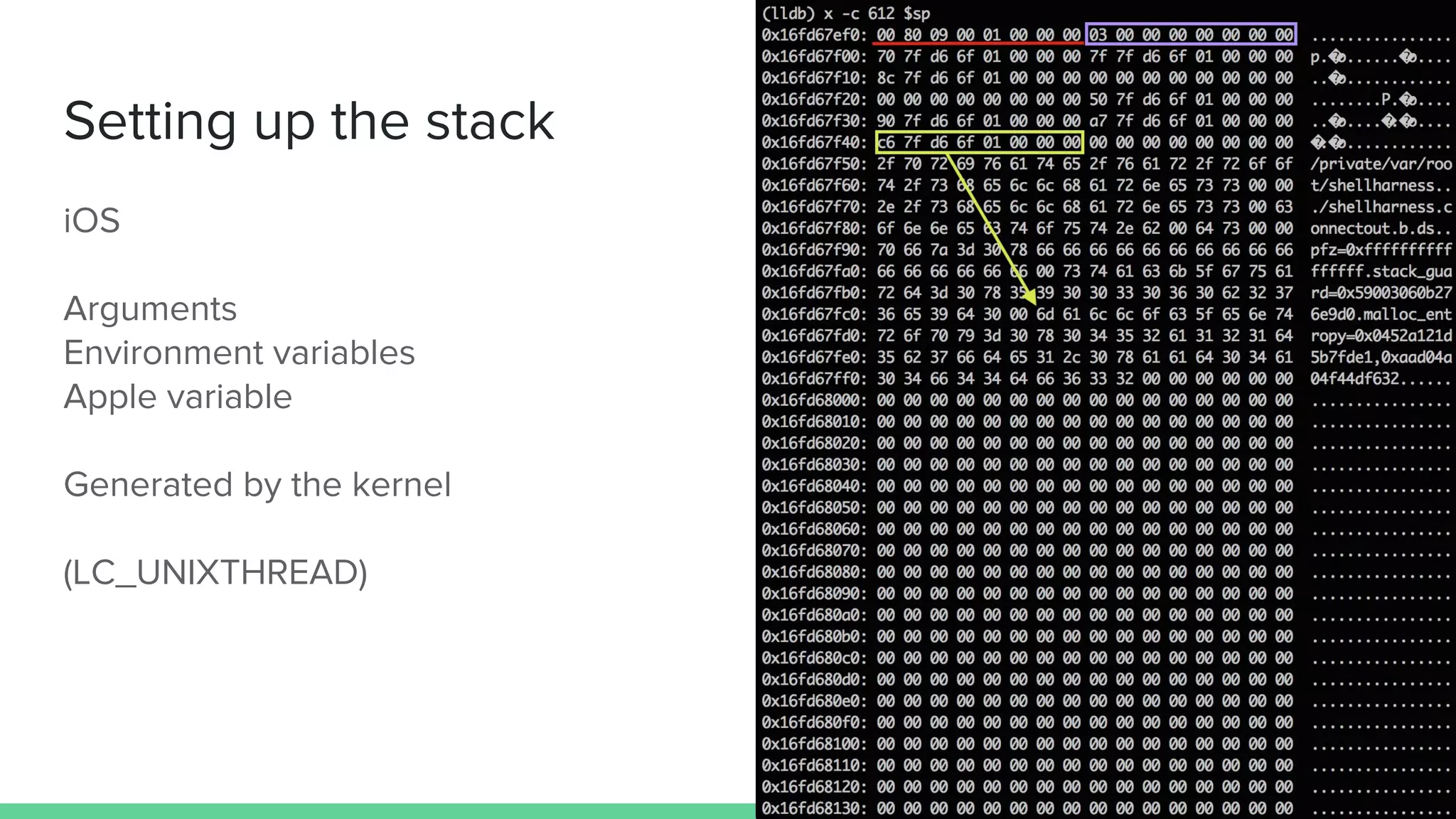
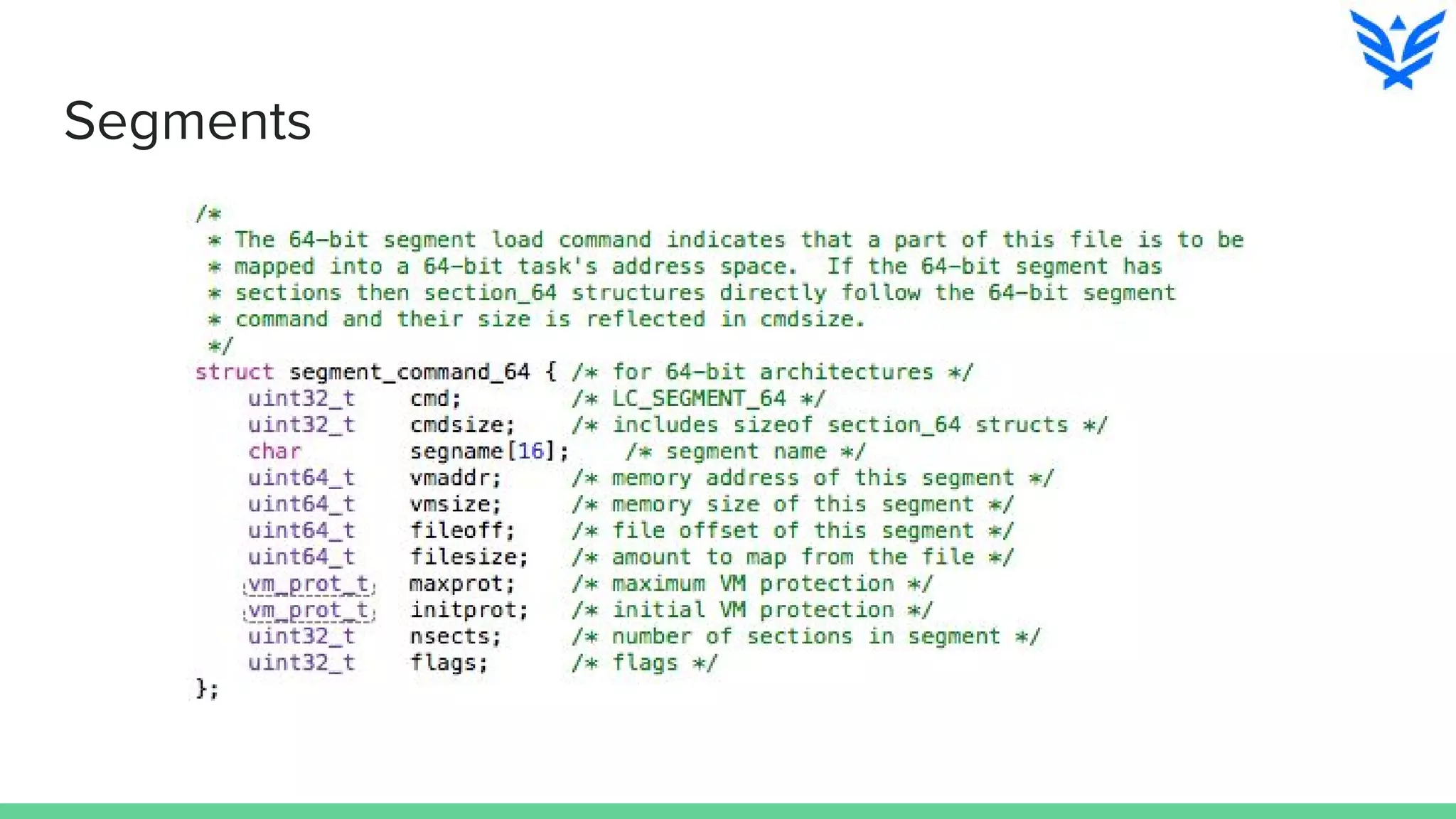
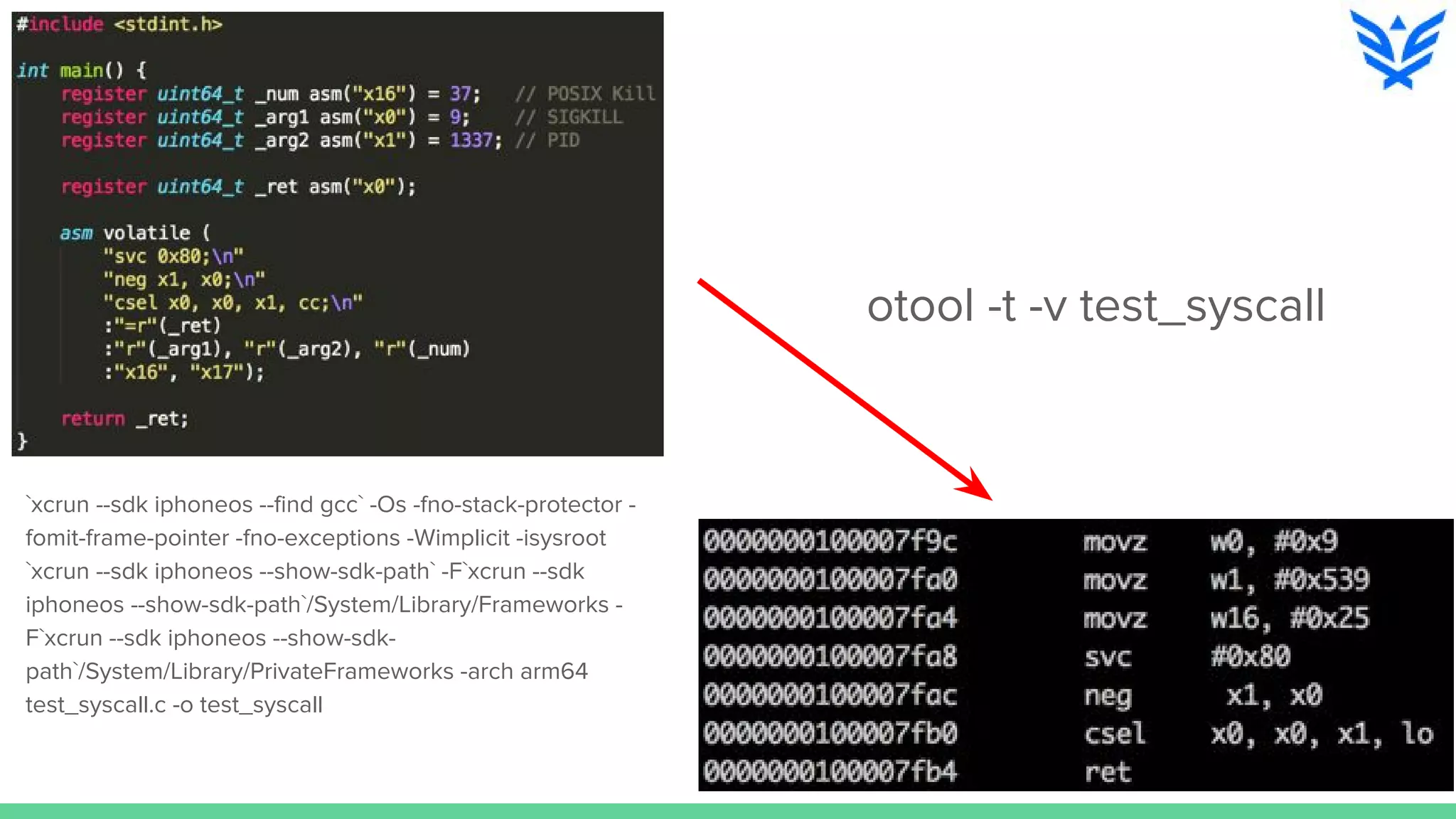
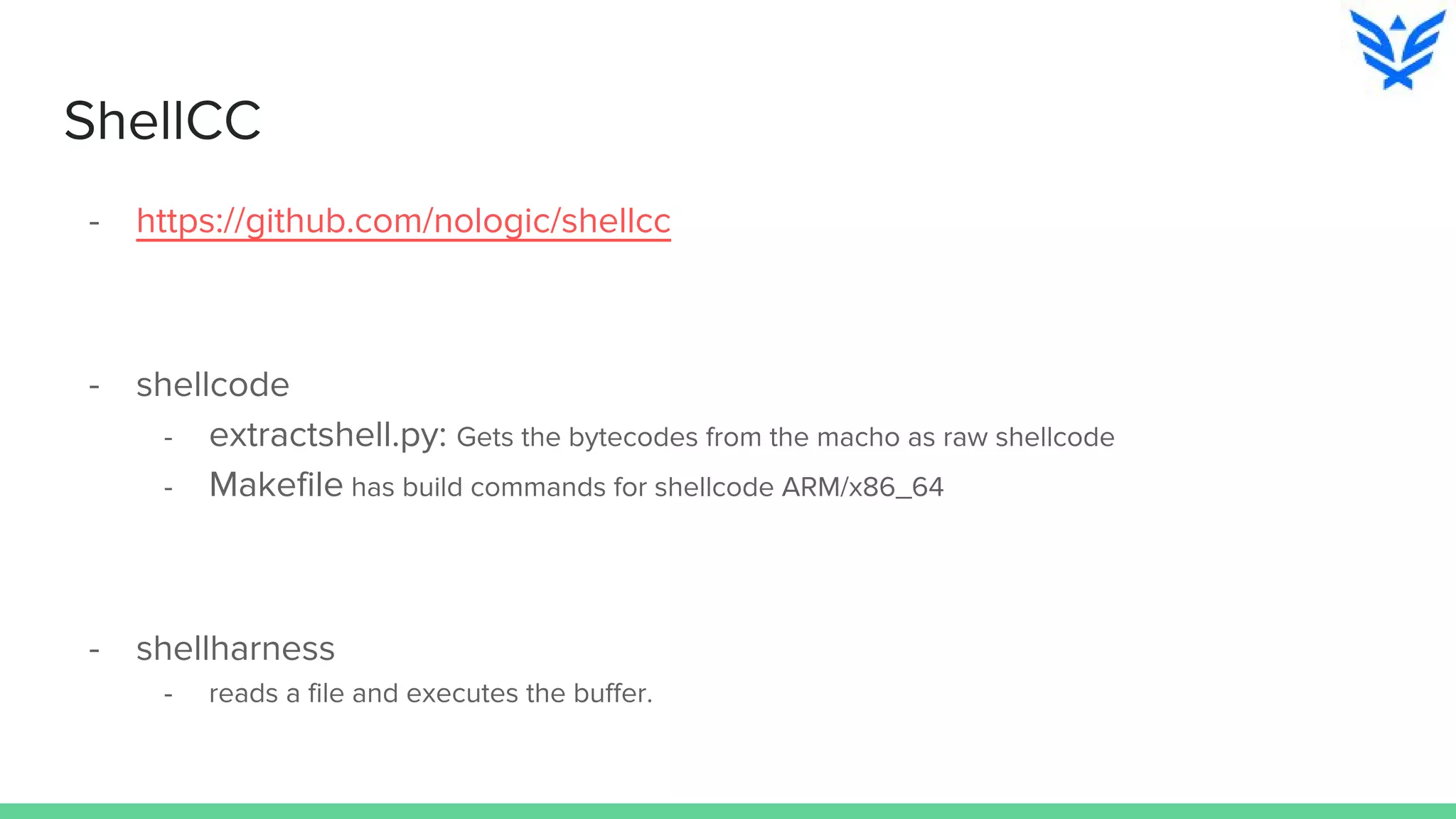
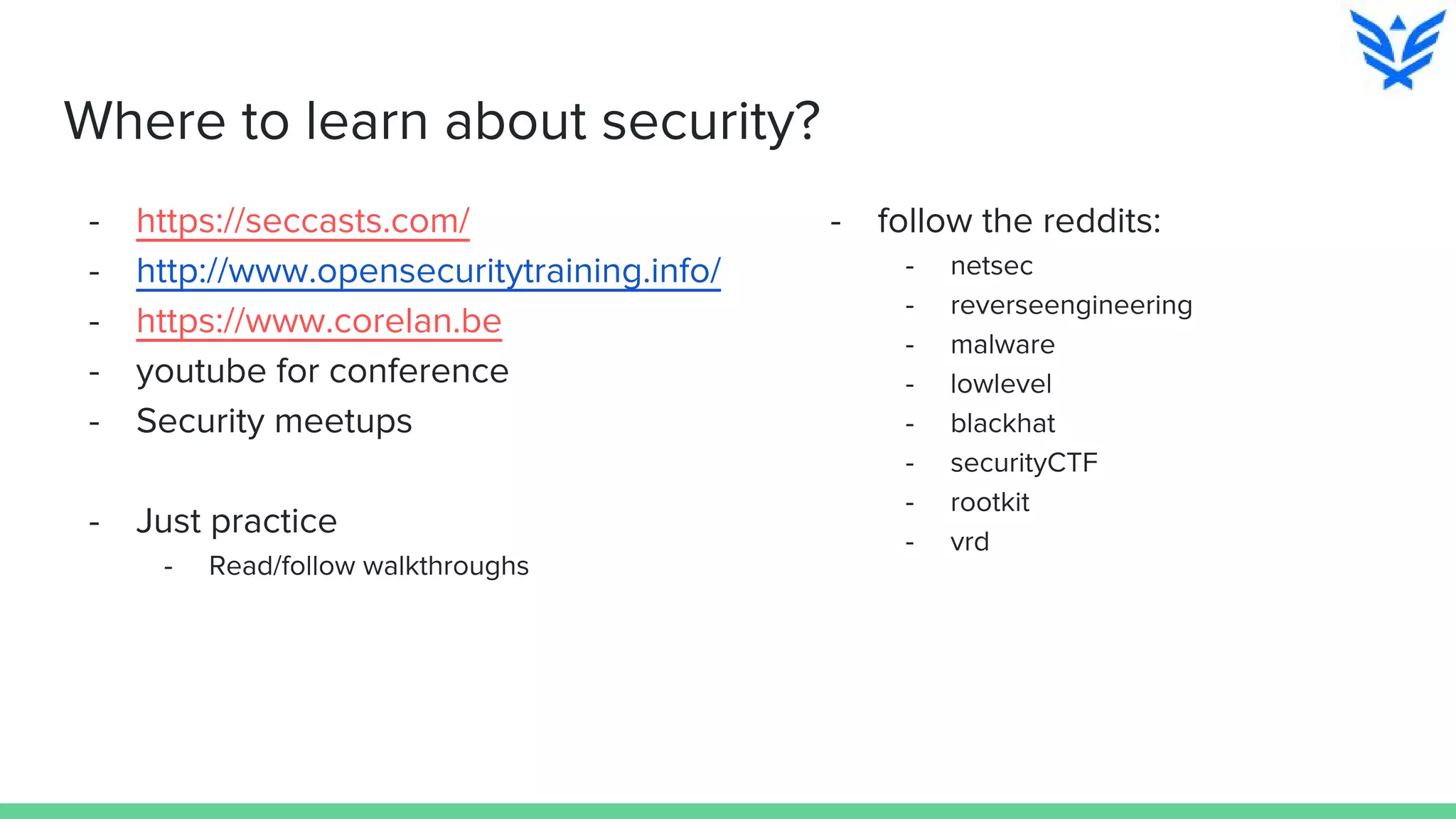
The document discusses vulnerabilities in iOS and OS X, highlighting the importance of security measures during the development lifecycle. It addresses various hacking techniques, tools, and approaches for exploiting these platforms, including fuzzing, code reading, and dynamic/static analysis. Additionally, it provides insights into shellcode development, system calls, and resource links for learning about security and the hacking community.