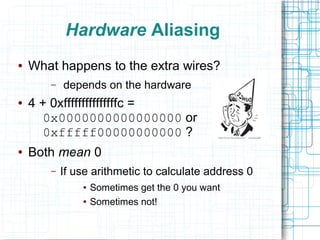
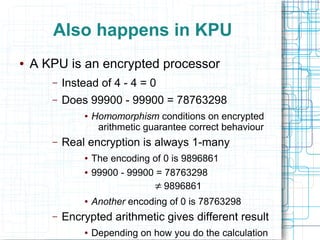
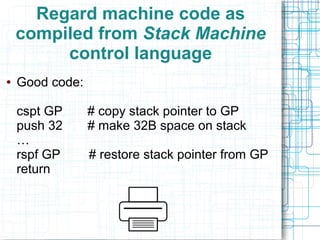
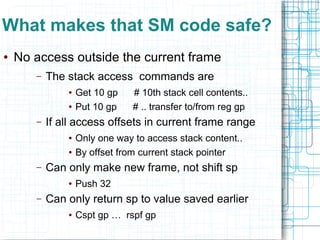
The document discusses certifying machine code as safe from hardware aliasing issues, particularly in the context of arithmetic operations on memory addresses that can yield inconsistent results. It addresses the constraints of stack frame access and introduces a verification process that involves disassembly and typing based on a stack machine model. The authors propose an inference-guided disassembly approach to ensure that machine code behaves correctly and adheres to the defined safety constraints.






![Example
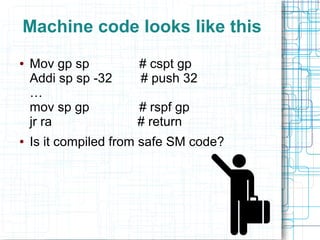
● Think about a 32B current frame
{ sp=c32
!10; (10)=x }
ld gp 10(sp) [get 10 gp]
{sp=c32
!10; (10)=gp=x}
●
'c32
!10' means pointer to 32B
– Already written at offset 10
● (10)=x means stack cell 10 has an x-thing
● Machine code is 'ld gp 10(sp)'
– Load reg gp from offset 10 from stack ptr
● Name of the rule is 'get 10 gp'](https://image.slidesharecdn.com/oc2013a-130923165743-phpapp02/85/Certifying-RISC-Machine-Code-Safe-from-Aliasing-OpenCert-2013-14-320.jpg)