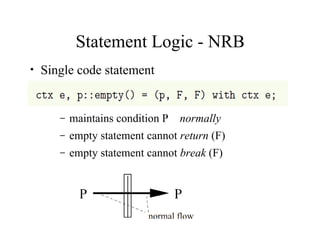
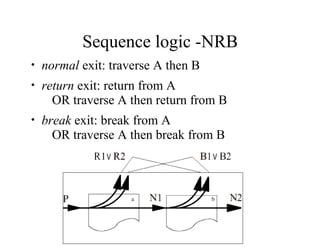
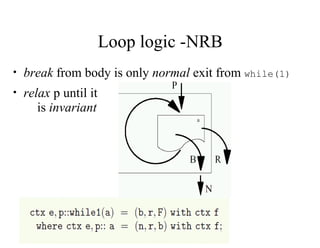
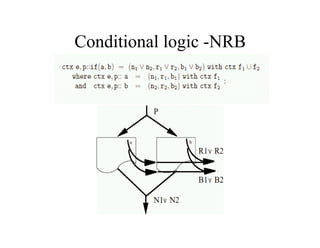
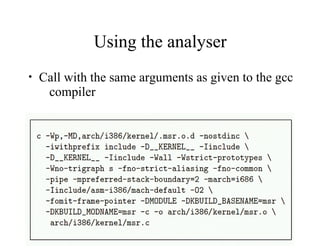
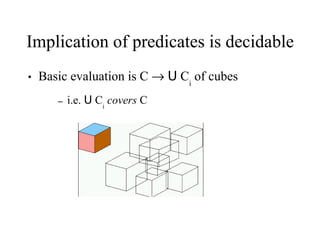
The document discusses the application of formal methods to analyze errors in the Linux kernel, particularly focusing on the effectiveness of these methods in handling millions of lines of C code. It provides examples of issues such as 'sleep under spinlock' and describes the logic and techniques involved in the analysis system, including statement logic and programmable triggers. Although promising for non-experts, limitations include challenges in tracking program state and extending to new problem classes.











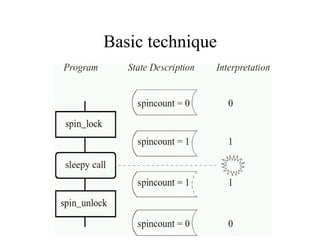
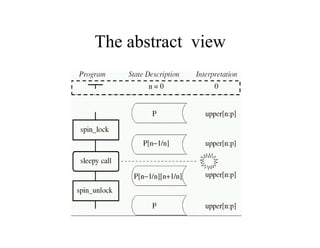
![Components of analysis system
• Description of statements as logic transformers
– p .... p[n-1/n]
• Trigger/action system for raising alarms!
• Combining logic NRB
• Guiding abstract interpretation s to state x
x ∈s ∩ p
stops dead code evaluation, etc.](https://image.slidesharecdn.com/mc-needle-130917090739-phpapp02/85/Abstract-Interpretation-meets-model-checking-near-the-1000000-LOC-mark-Finding-errors-in-the-Linux-Kernel-Source-AVIS-06-14-320.jpg)