Embed presentation
Download as ODP, PPTX









![A few examples UNARY_NEGATIVE: -TOS BINARY_ADD: TOS1 + TOS SLICE+3: TOS2[TOS1:TOS] UNPACK_SEQUENCE LOAD_CONST CALL_FUNCTION_VAR_KW](https://image.slidesharecdn.com/djangocon2009bytecode-090910133841-phpapp02/85/Dive-into-CPython-Bytecode-15-320.jpg)


![A tale of 2 functions >>> def f(): ... return [x for x in xrange(10)] >>> def g(): ... o = [] ... for x in xrange(10): ... o.append(x) ... return o](https://image.slidesharecdn.com/djangocon2009bytecode-090910133841-phpapp02/85/Dive-into-CPython-Bytecode-18-320.jpg)

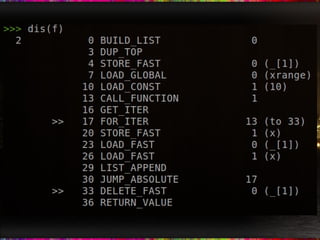




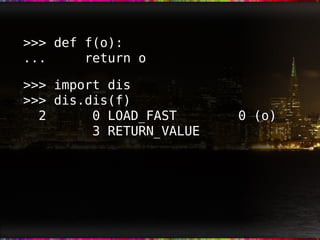
The document discusses how CPython creates bytecode from Python source code by tokenizing, parsing, building a symbol table, and compiling to bytecode. It provides an example of using the dis module to disassemble bytecode and lists some example bytecode instructions. It notes that the Python virtual machine is stack-based and that understanding bytecode can provide optimizations like using fewer or more specialized bytecode instructions to make code run faster.














![A few examples UNARY_NEGATIVE: -TOS BINARY_ADD: TOS1 + TOS SLICE+3: TOS2[TOS1:TOS] UNPACK_SEQUENCE LOAD_CONST CALL_FUNCTION_VAR_KW](https://image.slidesharecdn.com/djangocon2009bytecode-090910133841-phpapp02/85/Dive-into-CPython-Bytecode-15-320.jpg)


![A tale of 2 functions >>> def f(): ... return [x for x in xrange(10)] >>> def g(): ... o = [] ... for x in xrange(10): ... o.append(x) ... return o](https://image.slidesharecdn.com/djangocon2009bytecode-090910133841-phpapp02/85/Dive-into-CPython-Bytecode-18-320.jpg)




