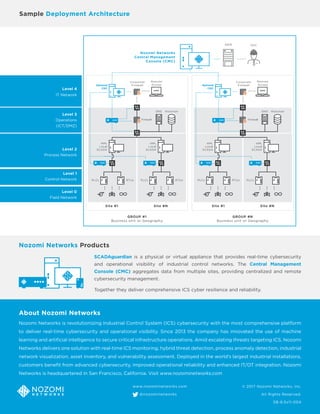
Nozomi Networks provides a comprehensive cybersecurity solution for industrial control systems, emphasizing real-time visibility, hybrid threat detection, and automated vulnerability assessments. It scales to monitor thousands of industrial sites while seamlessly integrating with IT/OT environments, ensuring enhanced cybersecurity, operational reliability, and reduced troubleshooting efforts. Major organizations worldwide have implemented this solution to mitigate cyber risks and improve efficiencies, leveraging machine learning and artificial intelligence for advanced monitoring and threat detection.