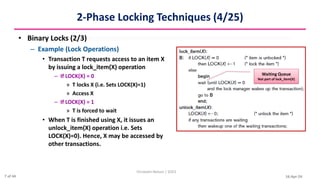
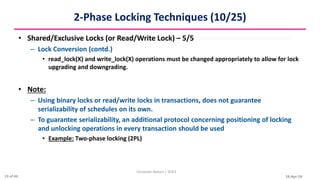
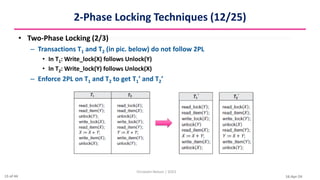
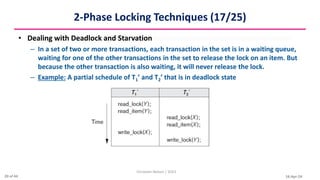
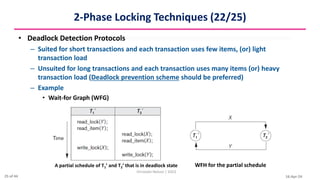
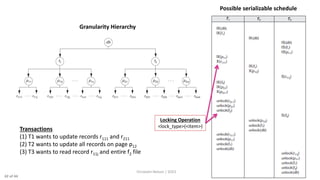
This document discusses various techniques for concurrency control, including two-phase locking techniques. It describes two-phase locking protocols that use binary locks or shared/exclusive locks to synchronize access to data among concurrent transactions. Transactions must acquire all necessary locks in an expanding phase before beginning their shrinking phase where locks are released. Variations like conservative two-phase locking require predeclaring lock needs, while strict two-phase locking does not release exclusive locks until transaction completion.