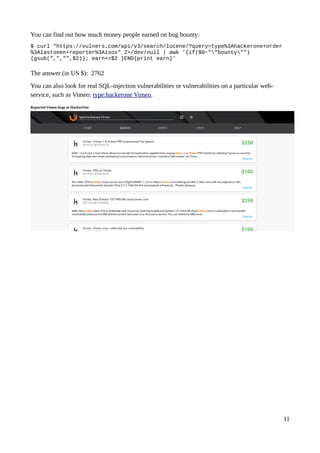
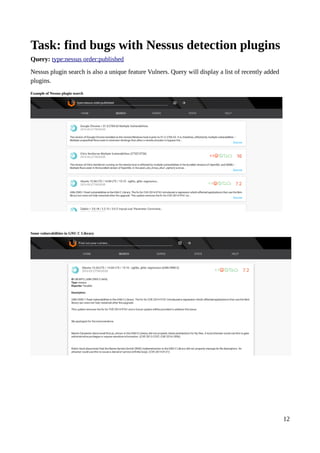
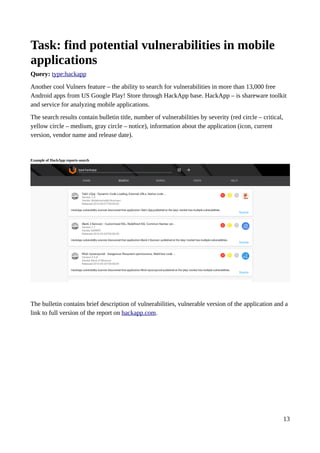
Vulners is a free and open vulnerability database and search engine that aggregates data from various sources such as CVE databases, vendor security bulletins, exploits, and bug bounty programs. It provides a fast search interface and API to query this consolidated data. The document provides examples of complex searches that can be performed on Vulners to find vulnerabilities by severity, vendor, exploits, detection plugins, and money earned through bug bounty programs. It also describes how the data is collected and structured and options for using the Vulners API and RSS feeds.




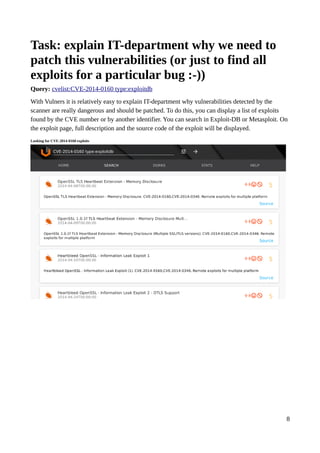
![Task: find critical CentOS bugs with public
exploits
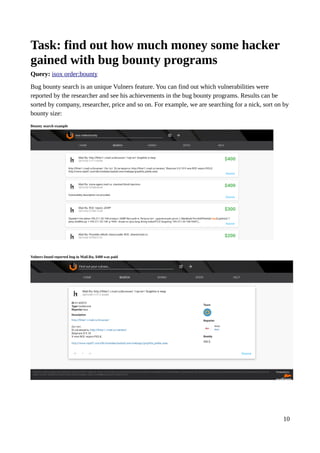
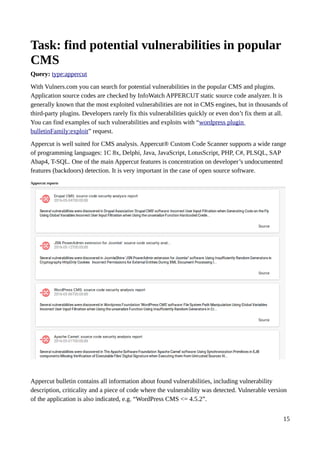
Query: type:centos order:published
Vulners allows you to filter search results and/or sort it by any field in bug description:
• by type of the bulletin;
• by CVSS Score;
• by date;
• by detection plugin number;
• by researcher name;
And so on.
That’s why we can form a complex queries like “type:centos cvss.score:[8 TO 10] order:published“,
which means “find all new critical CentOS bugs, with CVSS Base Score from 8 to 10”. Since
Vulners automatically add links to all collected data, you will see all related CVEs, detecting
plugins, and exploits on every CentOS CESA bulletin page in search results.
Search results for this query can be obtained via Vulners API – it is may be useful for scripting. You
just need to make a GET-request https://vulners.com/api/v3/search/lucene/?query=type:centos
%20cvss.score:[8%20TO%2010]%20order:published. The answer will be in JSON.
Another useful API-request option – references=true, which allows you to get not only security
objects (CentOS bulletins) in the query results, but all of related linked objects (detection plugins,
exploits, etc.). For example,
https://vulners.com/api/v3/search/lucene/?references=True&query=type:centos%20cvss.score:
[8%20TO%2010]%20order:published
GUI master for search requests
6](https://image.slidesharecdn.com/vulners-google-for-hacker-160818063254/85/Vulners-Google-for-hackers-6-320.jpg)




![Using the API
Since Vulners uses Elasticsearch, Vulners supports standard Apache Lucene queries. You can find
Field names for the search with API helper (https://vulners.com/api/v3/search/stats/). Any key from
“schemes” may be used as collector “key” in the Lucene query, for example:
• title
• description
• affectedPackage
• sourceData
• cvelist
Example of API search/lucene request for CVE-2014-0160: curl
https://vulners.com/api/v3/search/lucene/?query=type:cve%20id:CVE-2014-0160
Answer in JSON:
{
"data": {
"exactMatch": null,
"search": [
{
"_index": "bulletins",
"_score": 9.942732,
"_source": {
"type": "cve",
"title": "CVE-2014-0160: OpenSSL heartbeat information disclosure",
"published": "2014-04-07T18:55:03",
"objectVersion": "1.0",
"href": "https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-
0160",
"reporter": "NVD",
"modified": "2015-10-22T10:19:38",
"references": [
"http://www.securitytracker.com/id/1030081",
"http://public.support.unisys.com/common/public/vulnerability/NVD_Detail_Rpt.asp
x?ID=1",
"http://advisories.mageia.org/MGASA-2014-0165.html",
],
"description": "OpenSSL could allow a remote attacker to obtain
sensitive information, caused by an error in the TLS/DTLS heartbeat
functionality. An attacker could exploit this vulnerability to remotely read
system memory contents without needing to log on to the server. Successful
exploitation could allow an attacker to retrieve private keys, passwords or
other sensitive information.rnrnThis vulnerability is commonly referred to
as "Heartbleed".",
"lastseen": "2016-03-19T07:17:51",
"cvss": {
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:NONE/A:NONE/",
"score": 5.0
},
"id": "CVE-2014-0160",
"scanner": [],
"bulletinFamily": "NVD"
17](https://image.slidesharecdn.com/vulners-google-for-hacker-160818063254/85/Vulners-Google-for-hackers-17-320.jpg)
![},
"_id": "CVE-2014-0160",
"_type": "bulletin"
}
]
},
"result": "OK"
}
Vulners archive/collection call provides an easy way to export whole collections of security
bulletins.
For example, to download all CVEs you need to
wget “https://vulners.com/api/v3/archive/collection/?type=cve” -O cve.zip
The result will be cve.zip with cve.json inside.
The same file can be downloaded with GUI at Stats tab
Moreover, with this API call you can download security bulletins for a particular OS version:
wget “https://vulners.com/api/v3/archive/distributive/?os=centos&version=6” -O
centos.zip
It makes possible to get the data, which you won’t find anywhere else: the archives of exploits,
hackerone history, all CentOS vulnerabilities, etc. This functionality might be useful if you want to
make your own tools and data synchronization, if you already use some knowledge base.
No problem if you forgot “type” values. Just enter a nonexistent type, and you get a full list of
available values:
https://vulners.com/api/v3/archive/collection/?type=FAKE
“Error”: “There is no type ‘FAKE’Available collection types:. [ ‘Nessus’, ‘cve’, ‘exploitdb’,
‘xssed’, ‘zdt’, ‘hackapp’, ‘threatpost’, ‘redhat’, ‘debian’, ‘ubuntu’, ‘cert’, ‘metasploit’, ‘freebsd’,
‘zdi’, ‘oraclelinux’, ‘suse’, ‘centos’,’cisco ‘,’hackerone ‘,’vulnerlab ‘,’f5 ‘,’mozilla ‘,’ics’,
‘archlinux’, ‘ptsecurity’, ‘rdot’, ‘erpscan’, ‘huawei’, ‘xen’, ‘openssl’, ‘opera’, ‘vmware’,
‘wpvulndb’, ‘samba’, ‘postgresql’, ‘drupal’, ‘lenovo’, ‘msvr’, ‘paloalto’, ‘nginx’] “
18](https://image.slidesharecdn.com/vulners-google-for-hacker-160818063254/85/Vulners-Google-for-hackers-18-320.jpg)