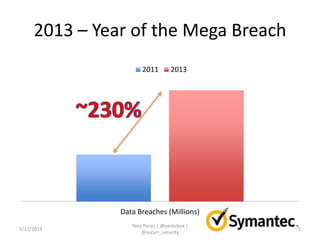
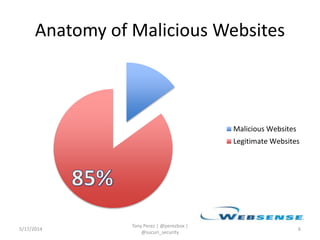
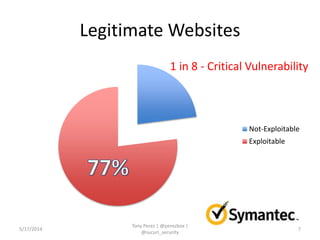
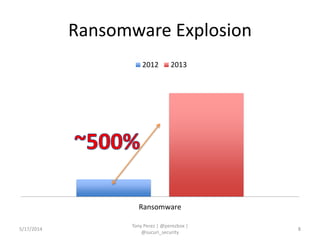
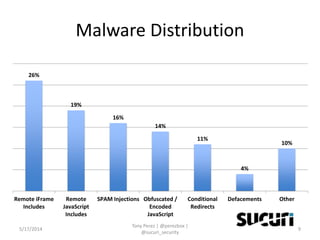
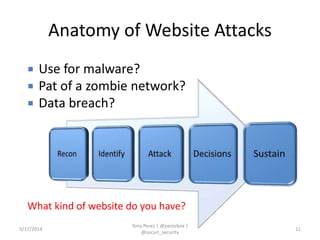
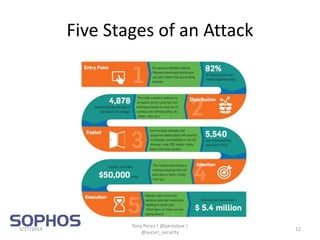
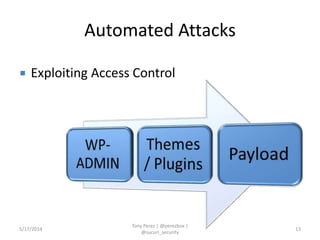
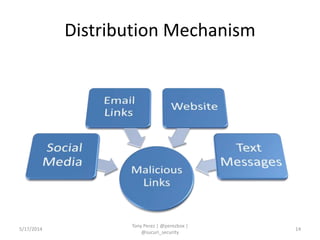
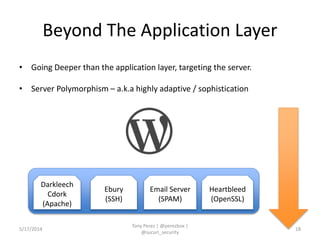
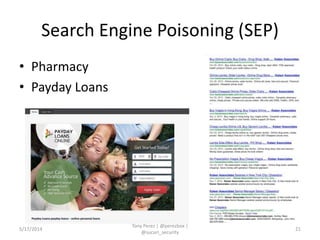
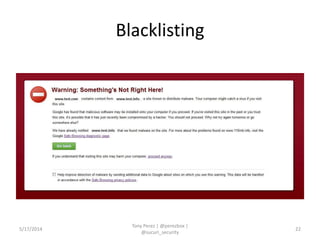
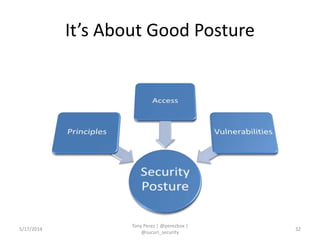
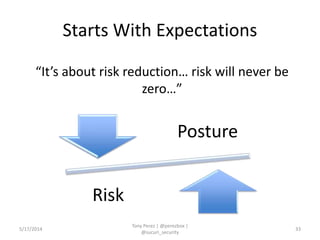
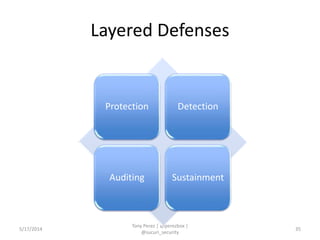
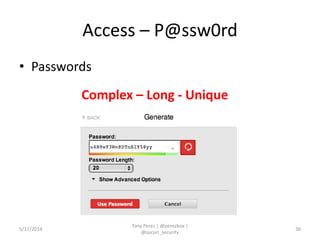
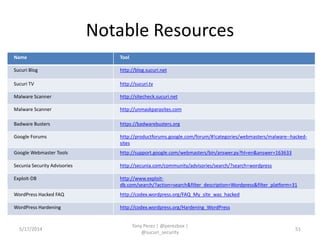
Tony Perez of Sucuri, Inc. gave a presentation on website security, with a focus on WordPress sites. Some key points included: Sucuri scans over 2 million domains and blocks 4 million attacks per month; in 2013 there was an increase in major data breaches; common attacks on websites include exploiting vulnerabilities, malware distribution through remote files/scripts, ransomware explosions, and search engine poisoning; defenses include strong credentials, limiting access and privileges, keeping software updated, using a website firewall, and monitoring activity through logging. Perez emphasized having security as the default posture through a defense-in-depth approach with layered protections.