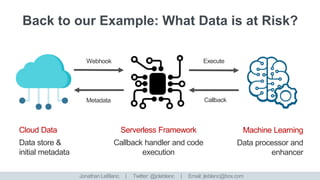
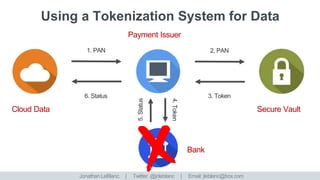
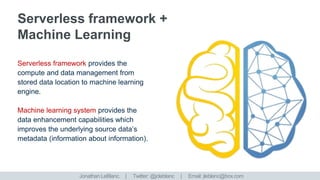
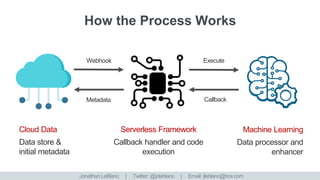
The document discusses enhancing and securing data in a world of interconnected devices, focusing on machine learning capabilities and serverless frameworks. It also highlights regulatory compliance challenges and strategies related to data retention, encryption, and data access tokens. Several case studies illustrate practical implementations, including metadata enhancement for video content and security measures for personal data.







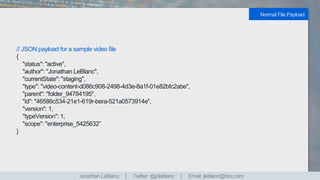
![// JSON payload for a sample video file with additional metadata
{
"token": { …read / write tokens for restricted access… }
"transcription": {[
"start_time" : "1523550398",
"end_time" : " 1523551036",
"text": "text transcription",
"tone": "emotion analysis of tone",
"image": "image capture of person speaking",
"data": { …user data analysis… }
]},
"status": "active",
"author": "Jonathan LeBlanc",
"currentState": "staging",
…
}
Enhanced File Payload
Jonathan LeBlanc. | Twitter: @jcleblanc | Email: jleblanc@box.com](https://image.slidesharecdn.com/moderncloudsecurity042018-180415075145/85/Modern-Cloud-Data-Security-Practices-11-320.jpg)