This document discusses different authentication methods for a Box application including:
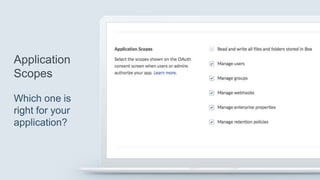
1. Long-lived access tokens that are restricted to certain API functionality and contain a permission screen.
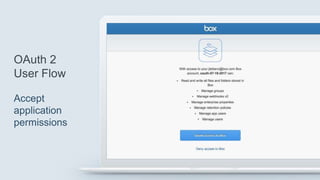
2. OAuth 2 authentication that requires managing user identities and content.
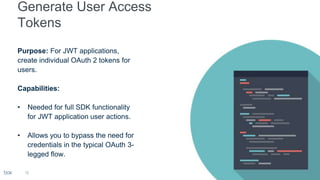
3. Application access tokens that need to be refreshed every hour and bypass OAuth authentication.
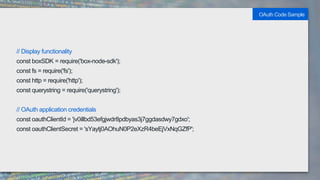
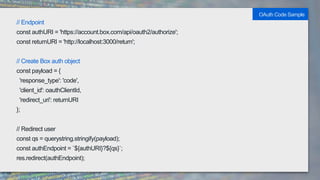
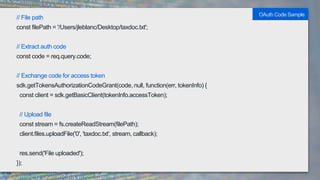
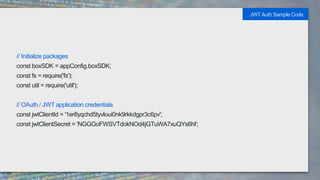
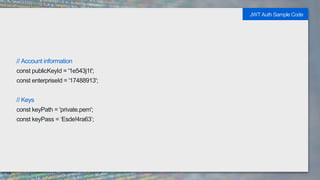
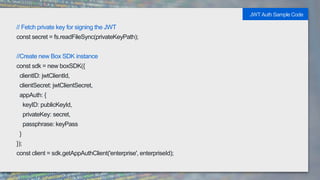
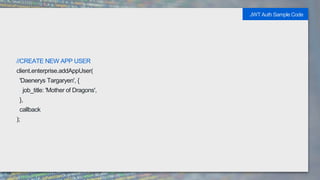
It also provides code samples for OAuth 2 authentication flows and initializing a Box SDK client using JWT authentication with an app's client ID, secret, and signing keys.