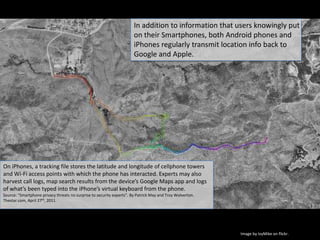
This document discusses mobile security and privacy issues. It notes that smartphones contain a large amount of personal information and location data but many users are unaware of security risks if their phone is lost or stolen. While businesses struggle to securely manage employee devices, simple solutions for individuals include enabling passcodes and changing privacy settings. The document advocates educating oneself on security options to protect information on mobile devices.