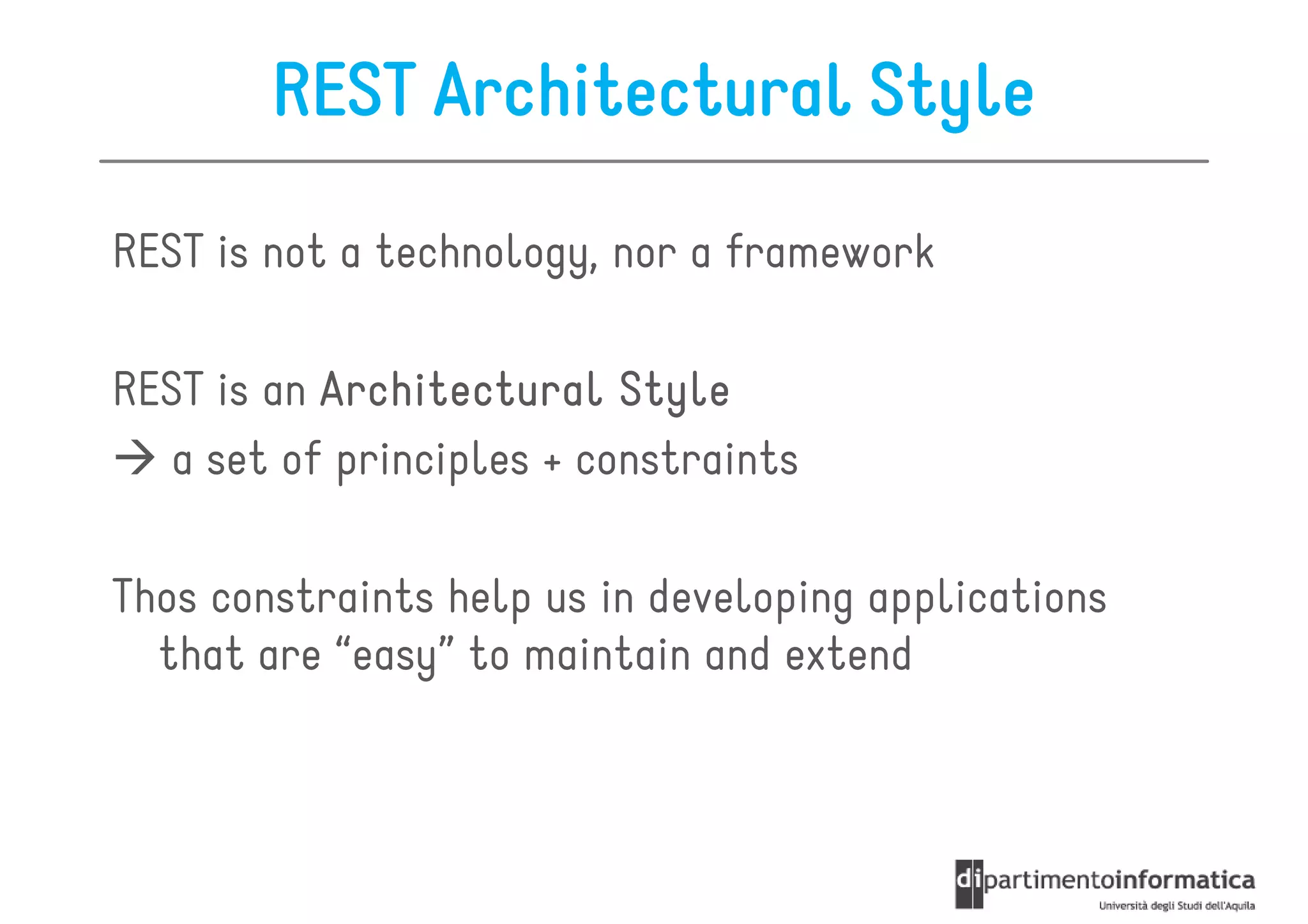
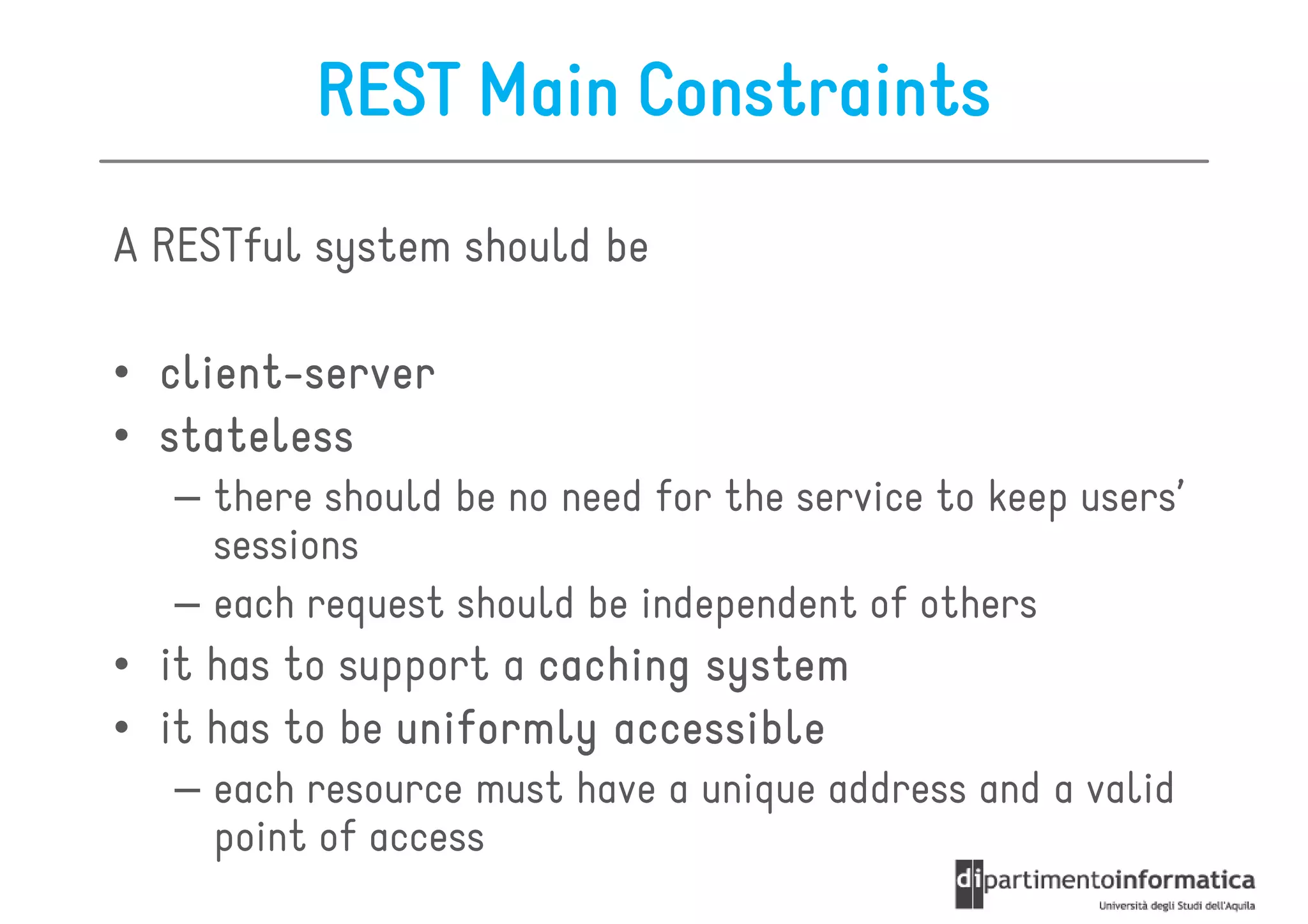
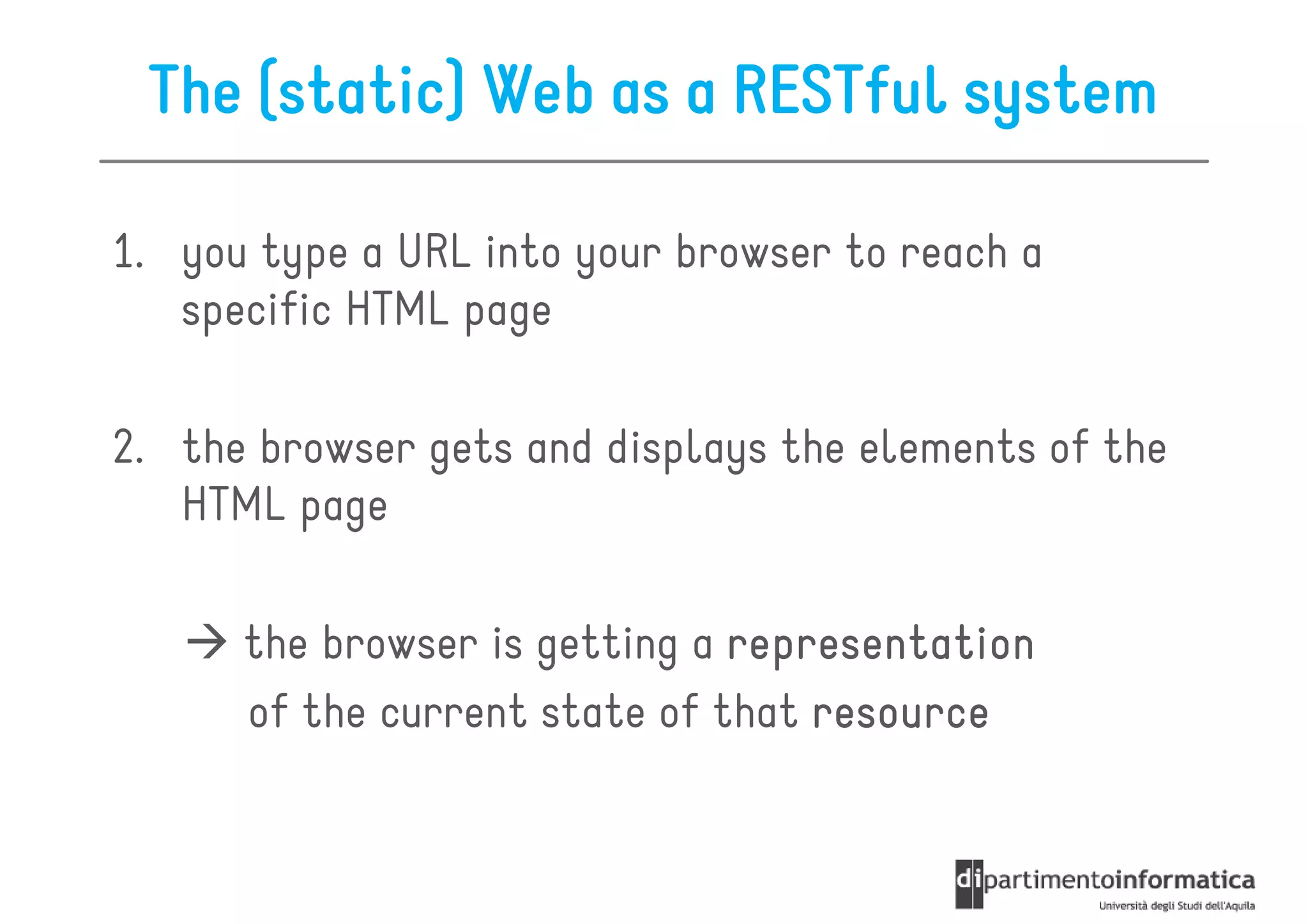
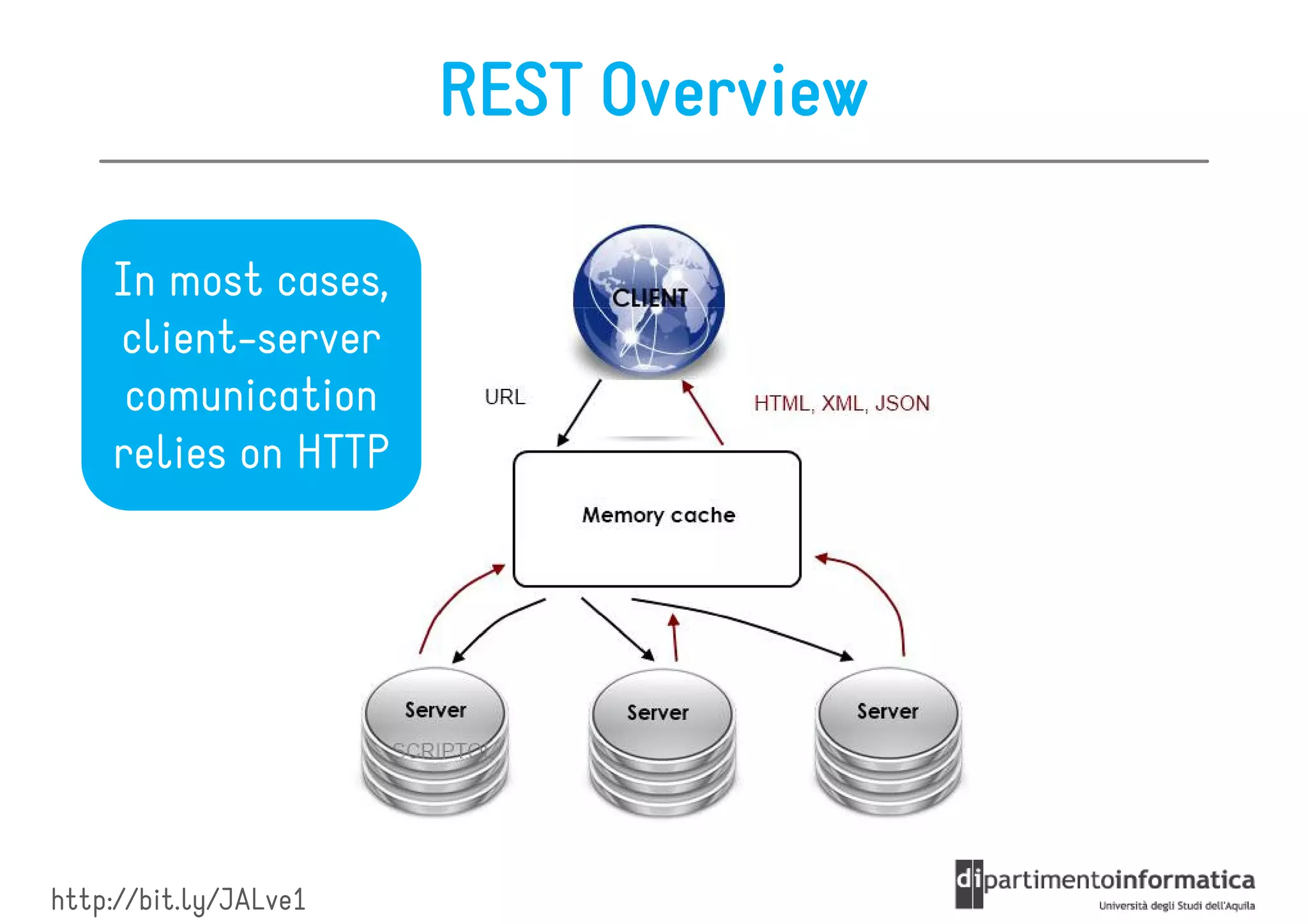
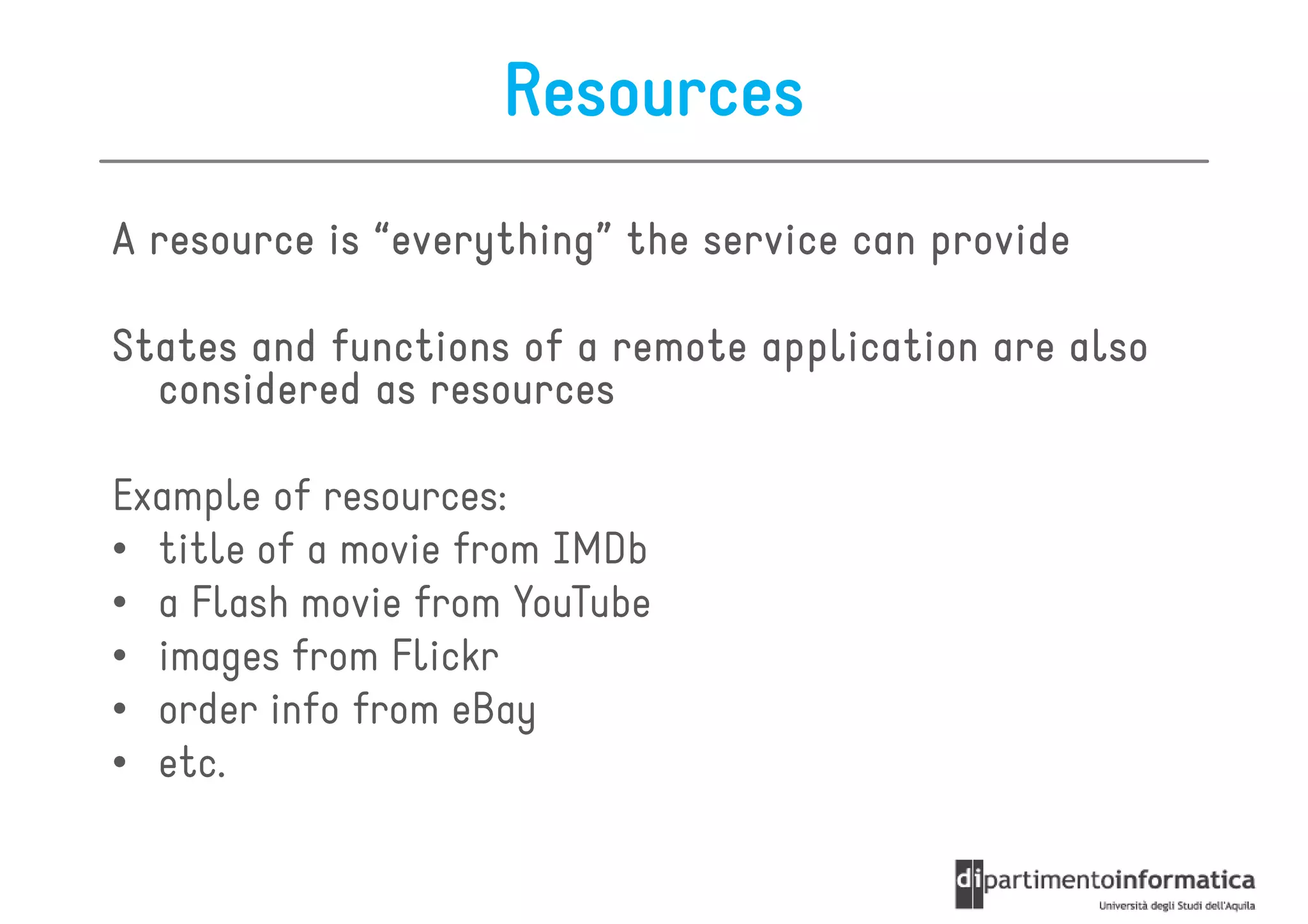
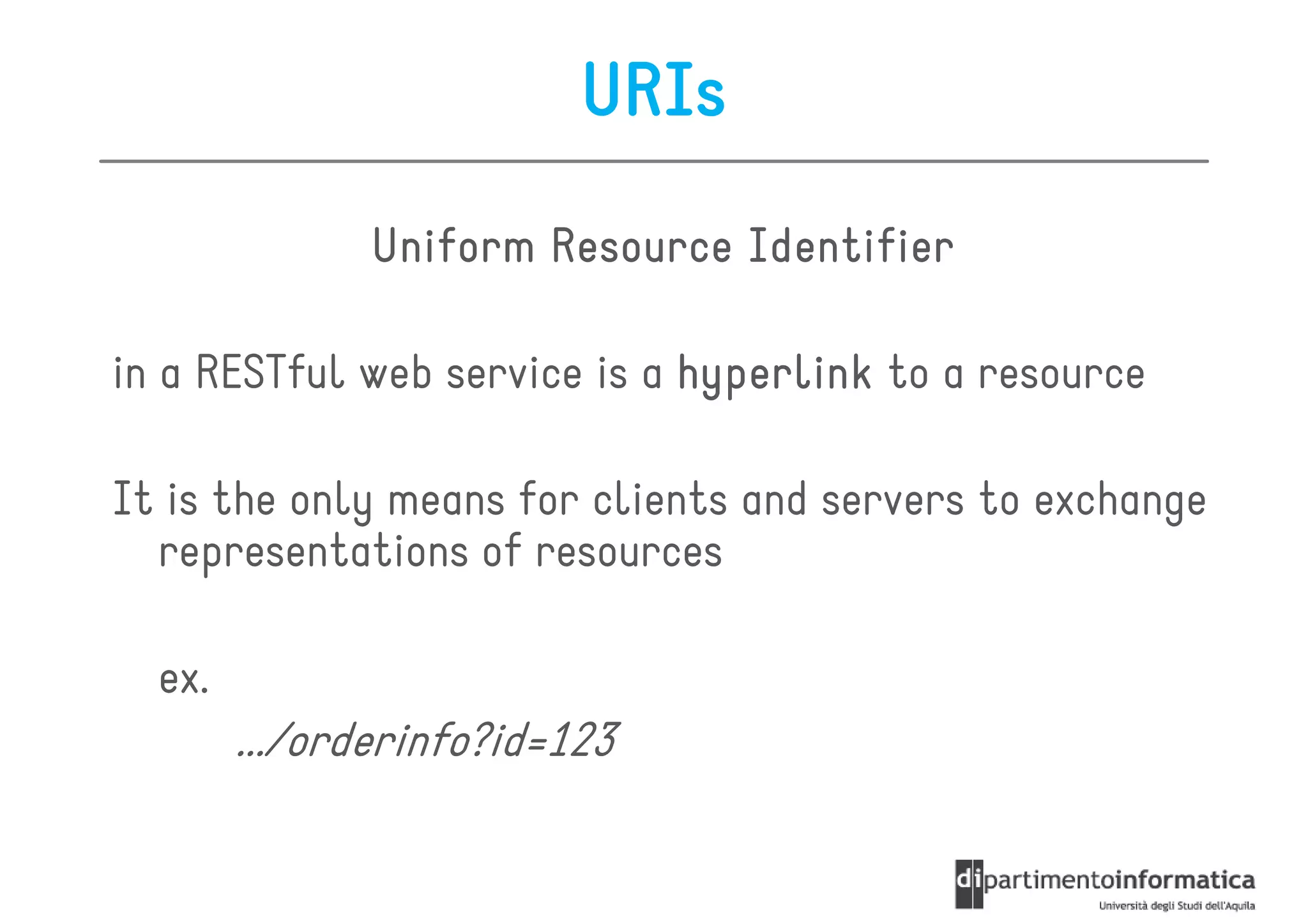
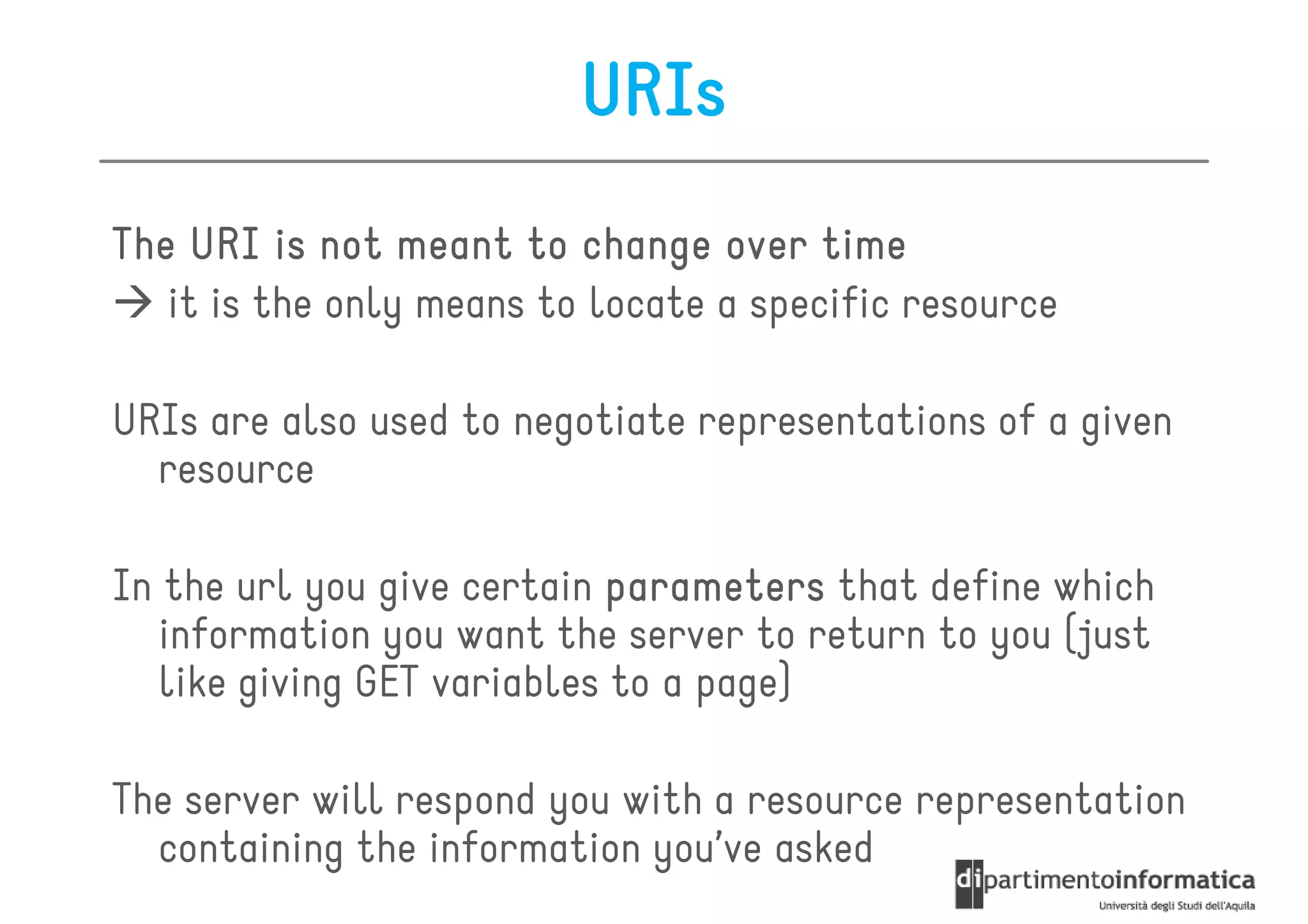
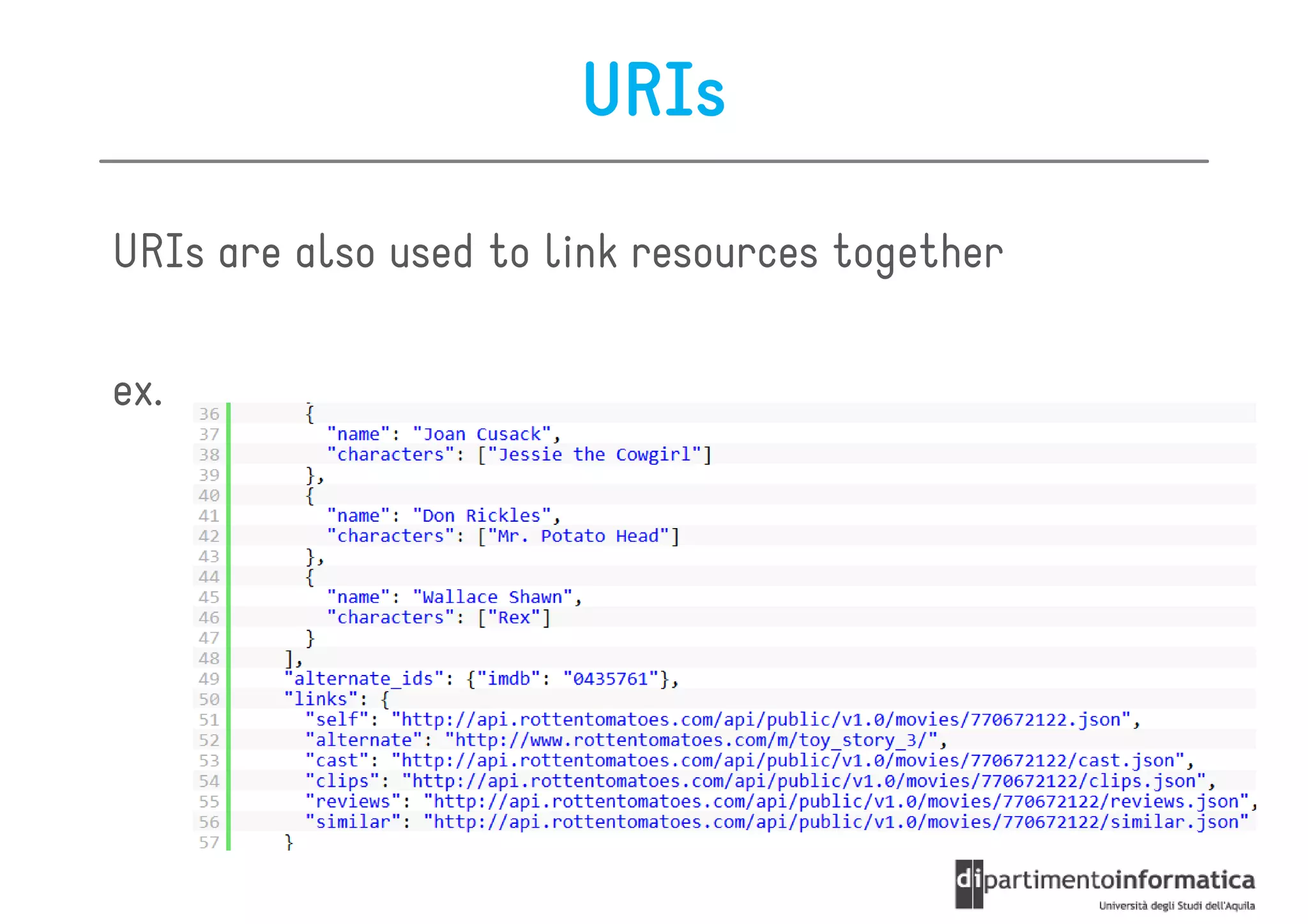
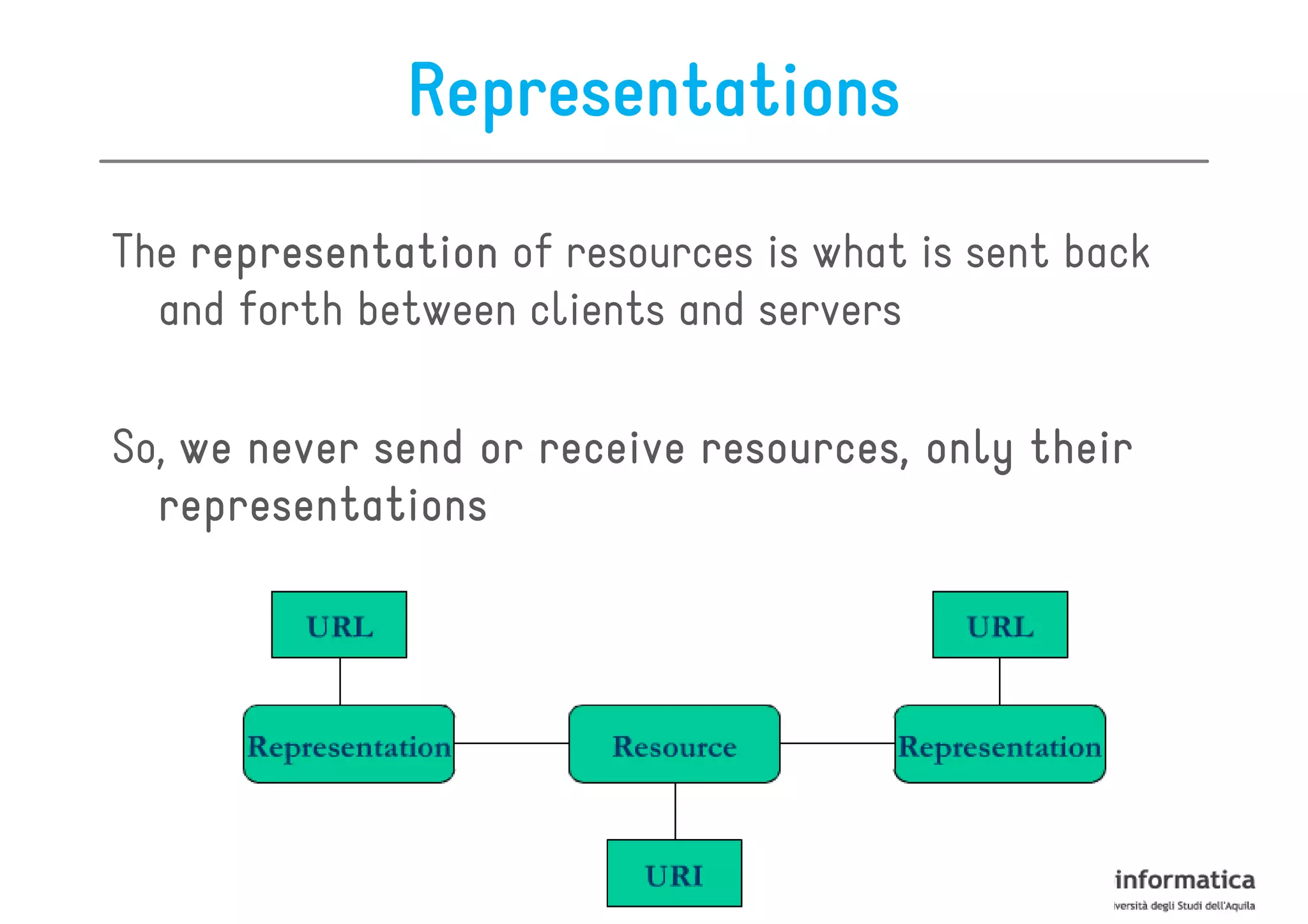
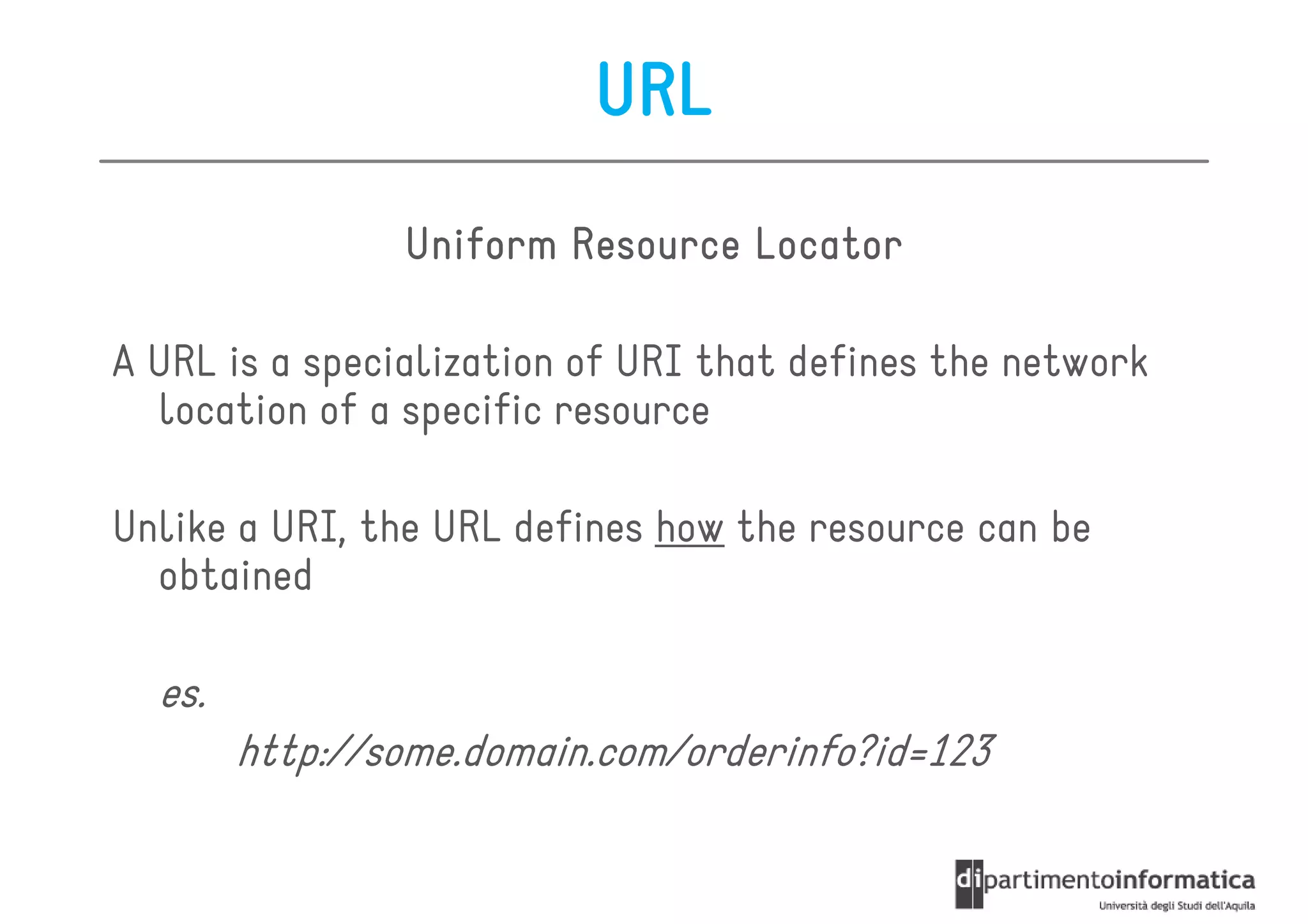
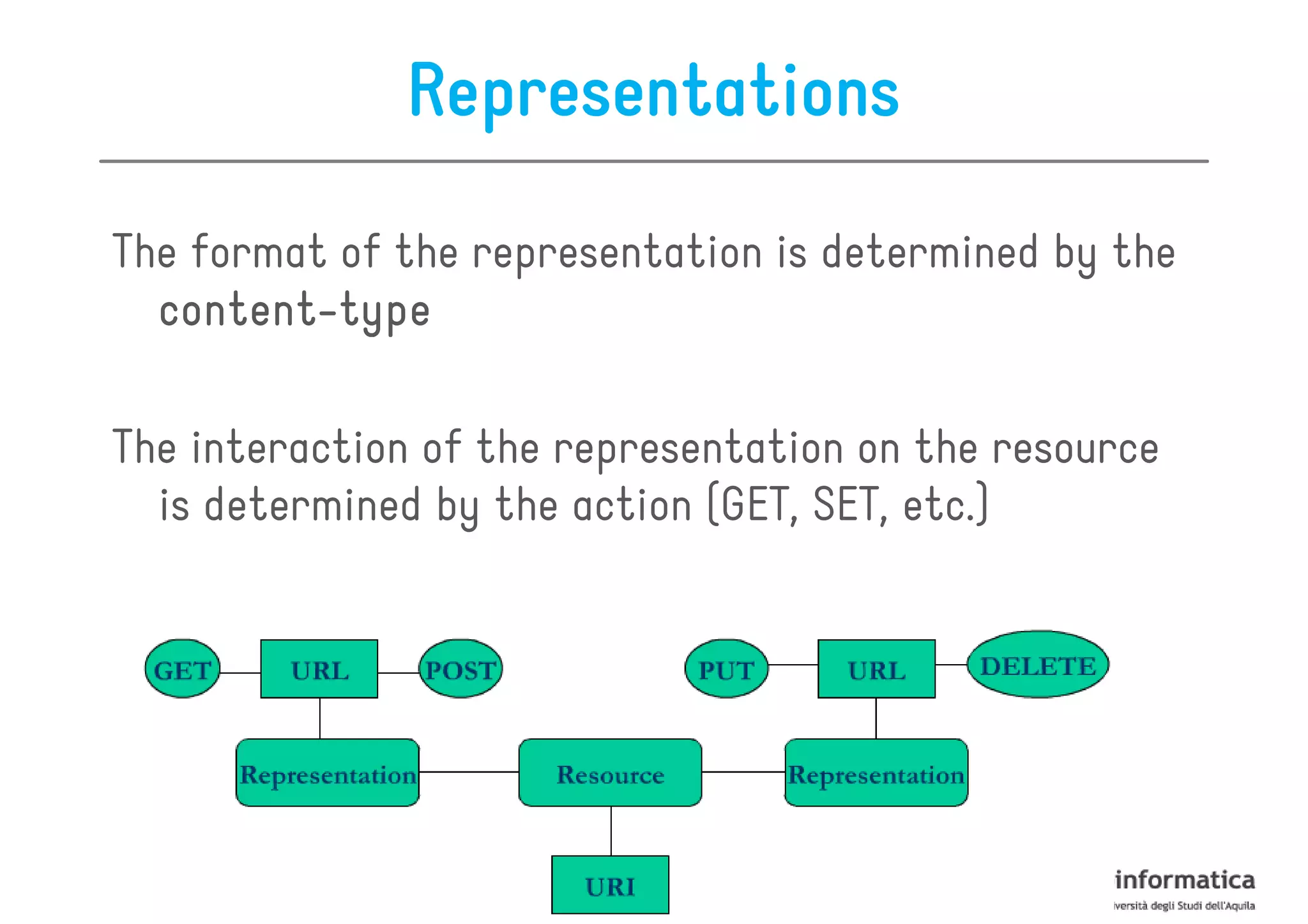
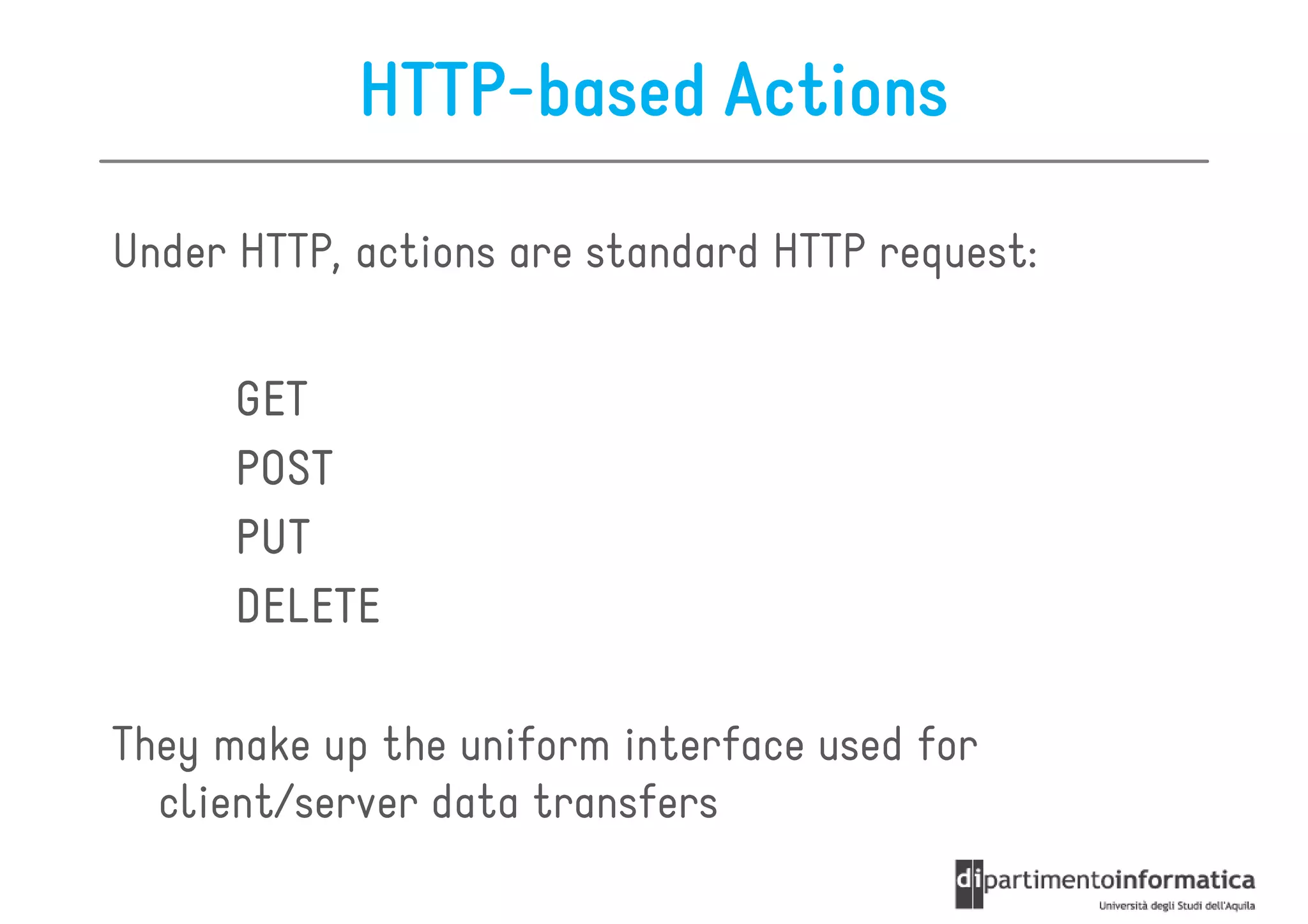
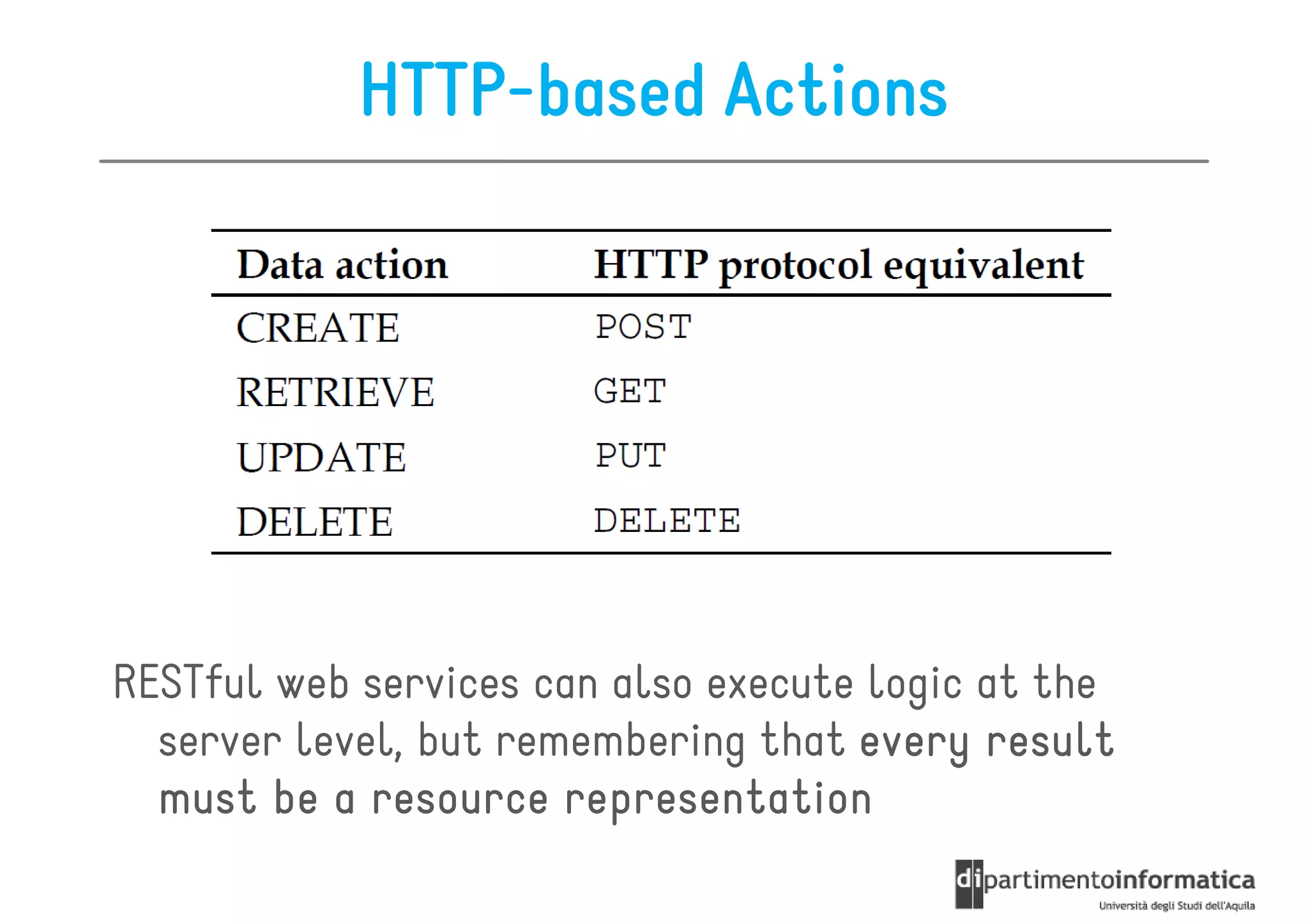
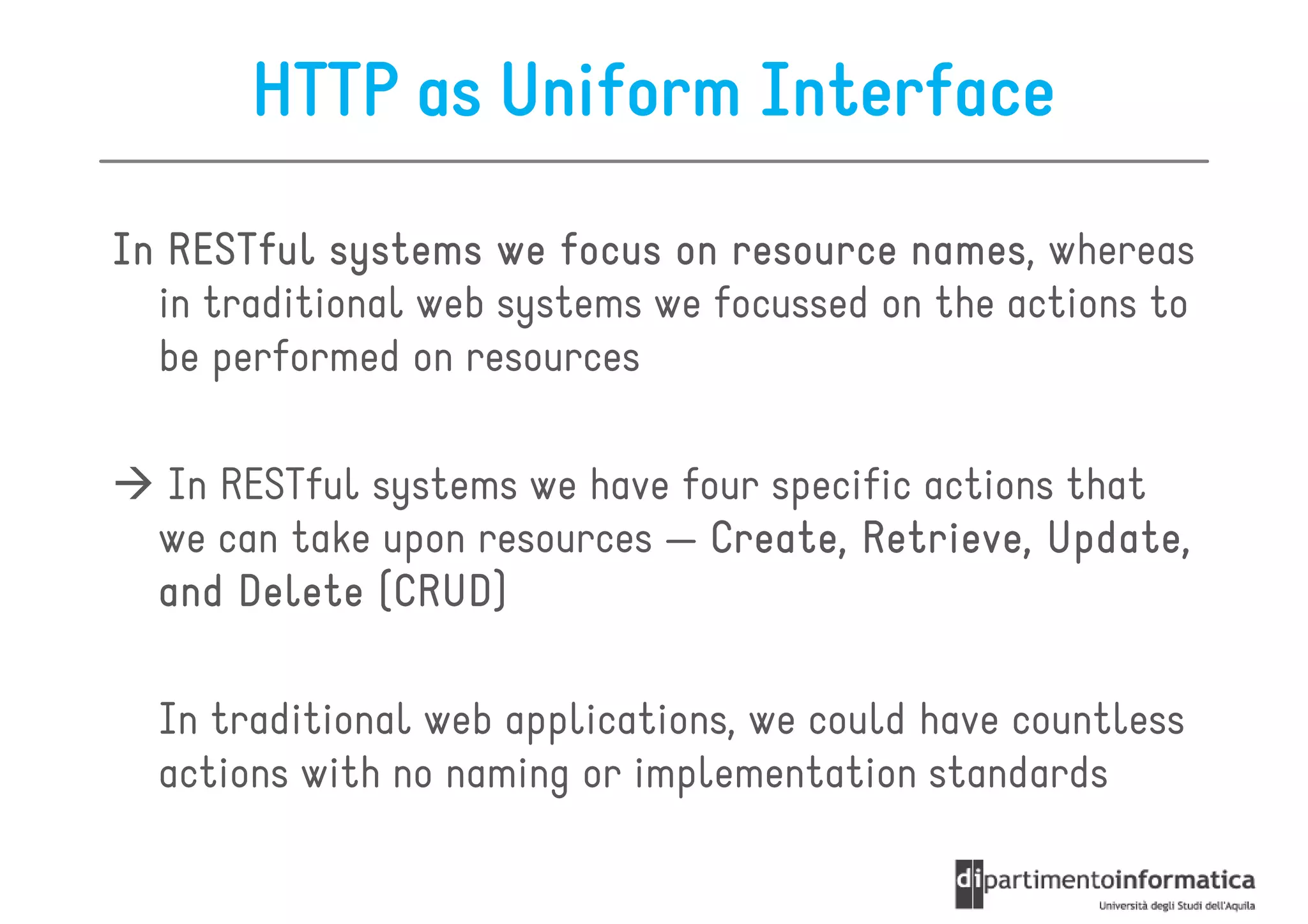
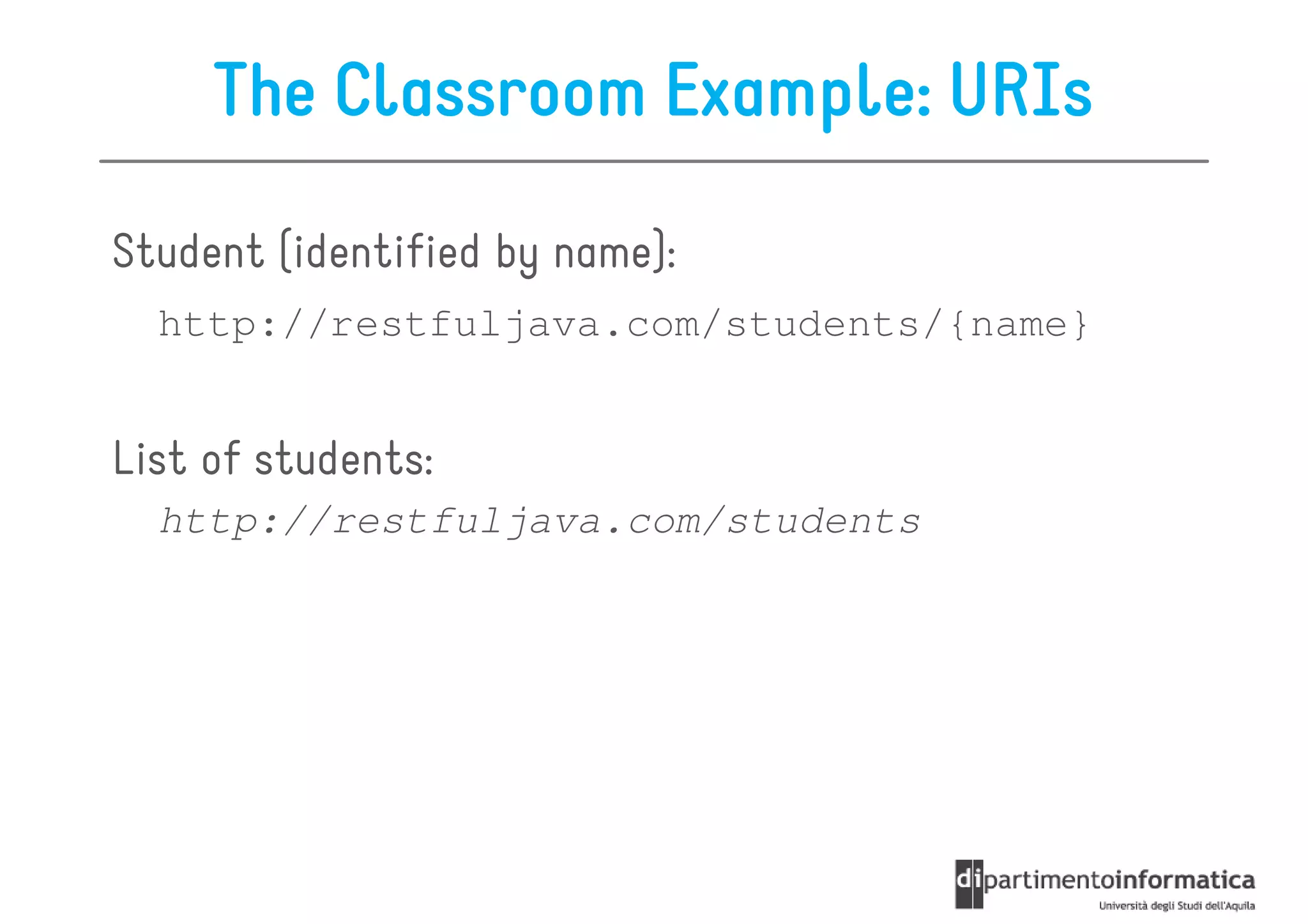
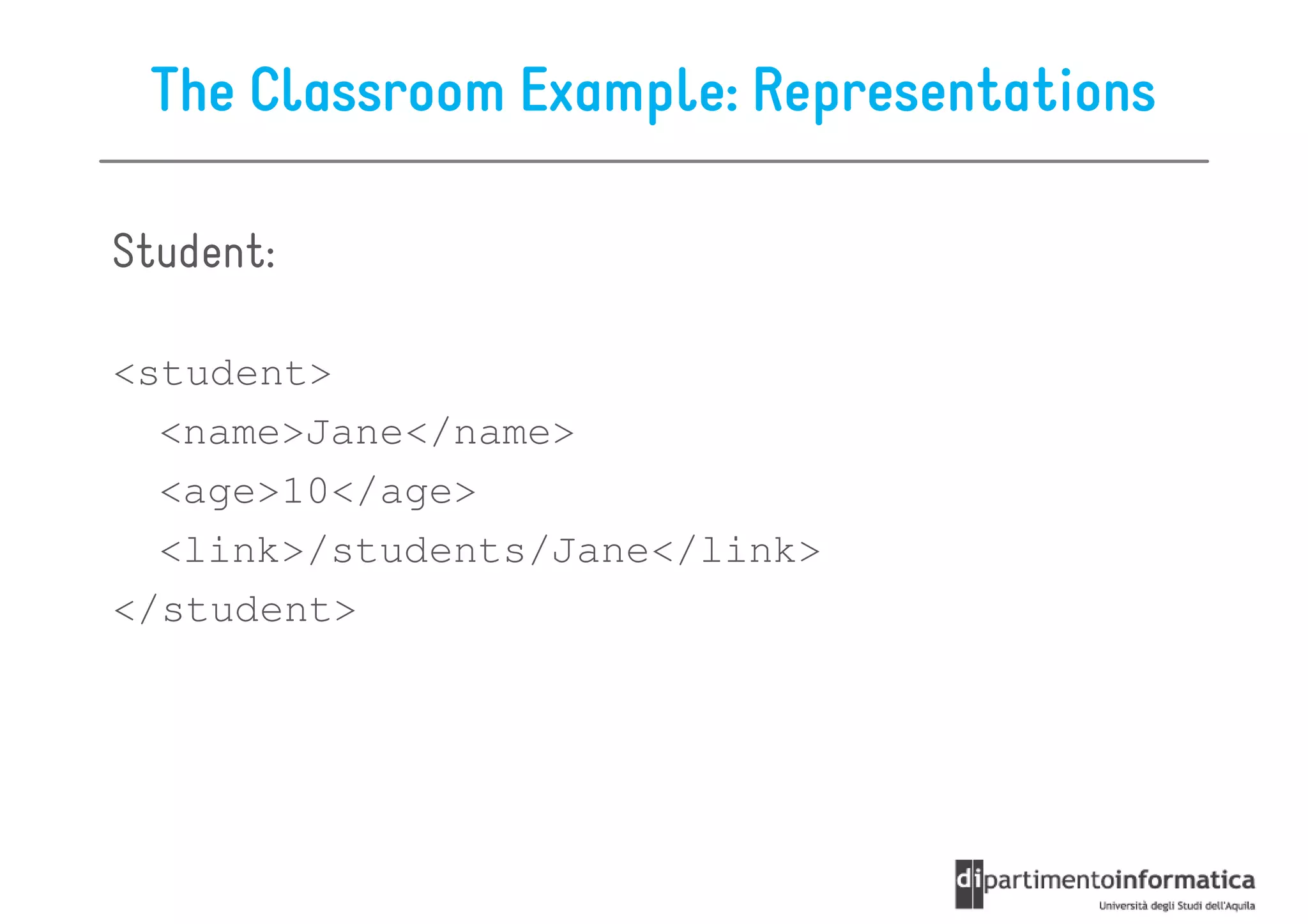
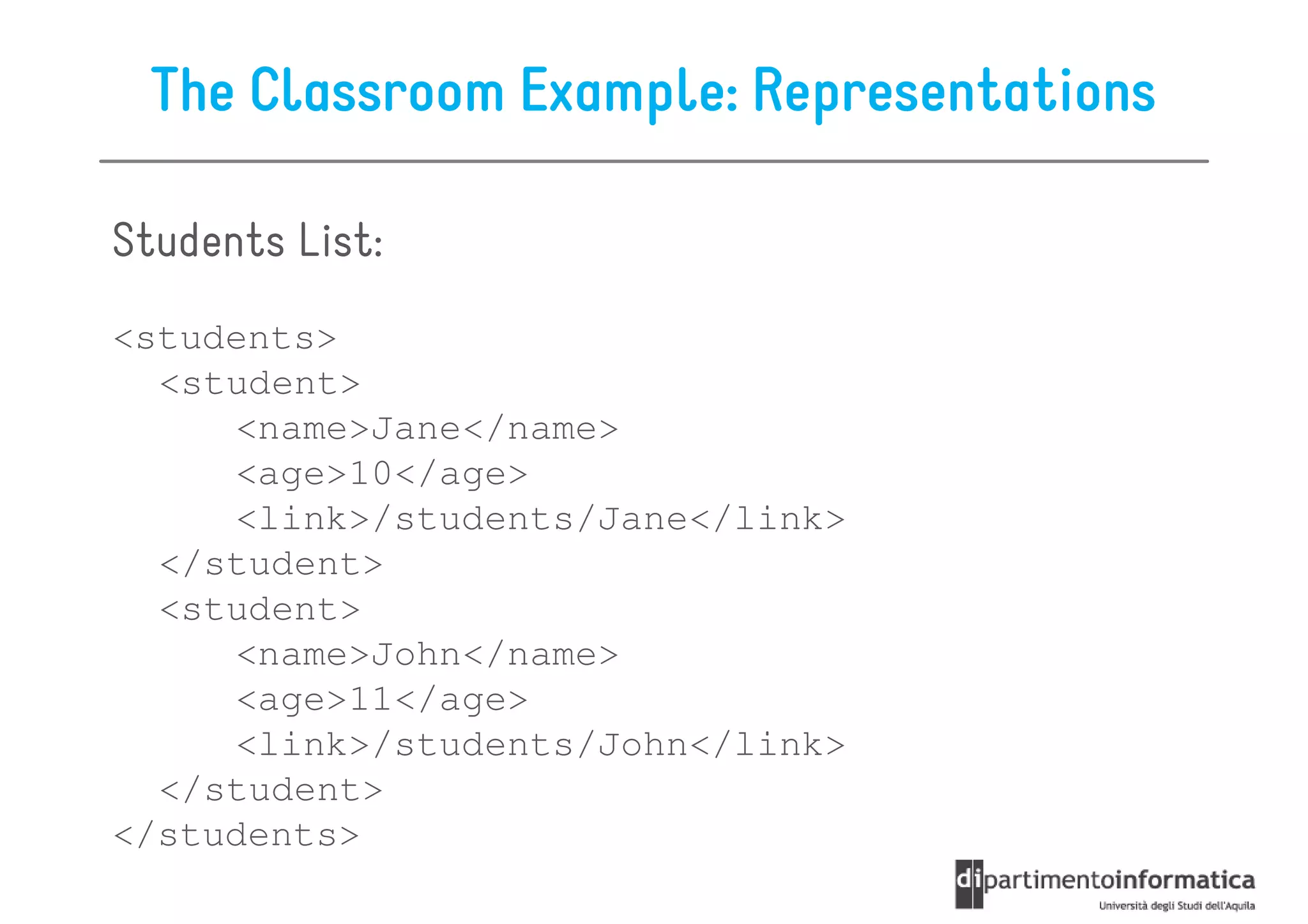
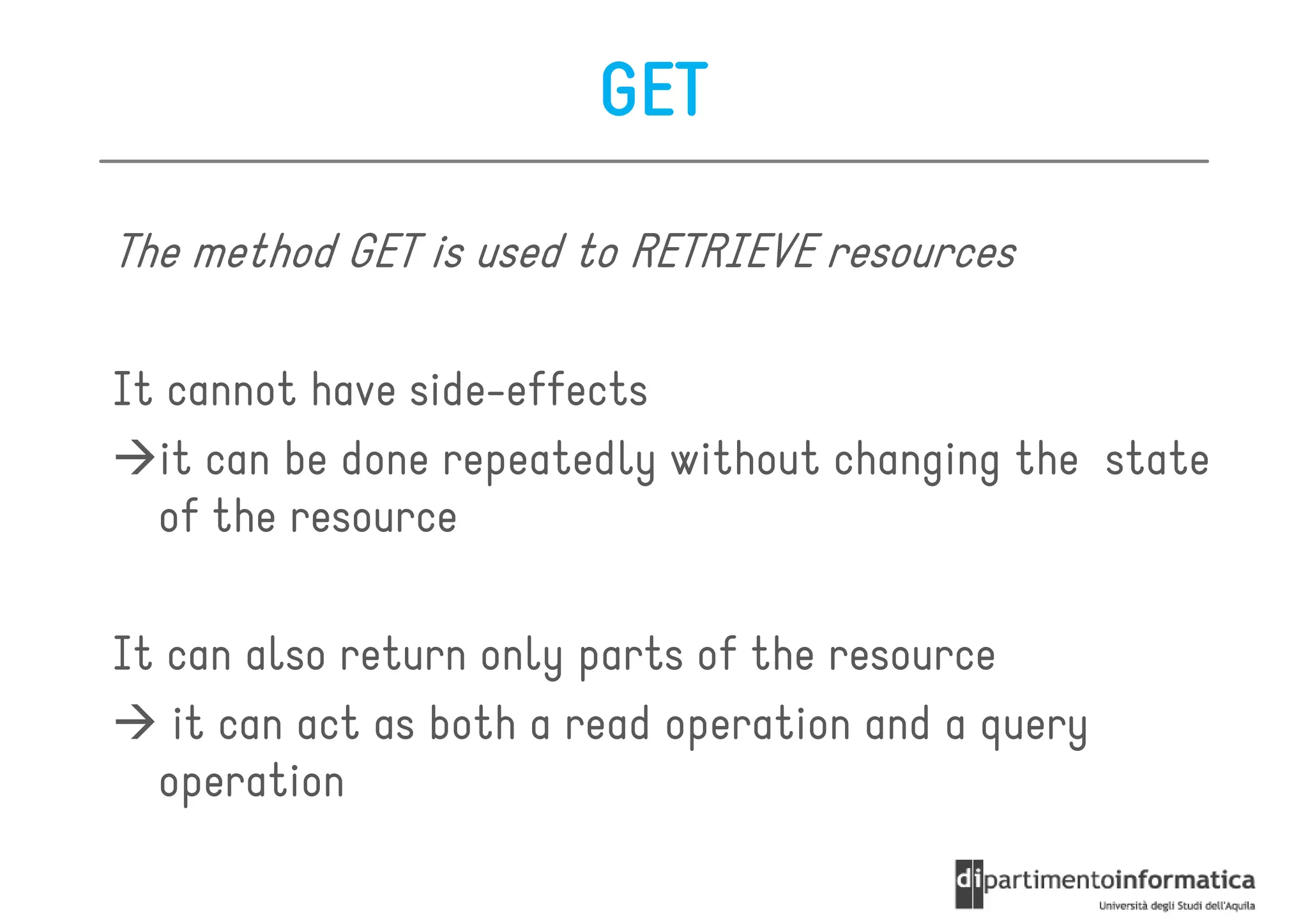
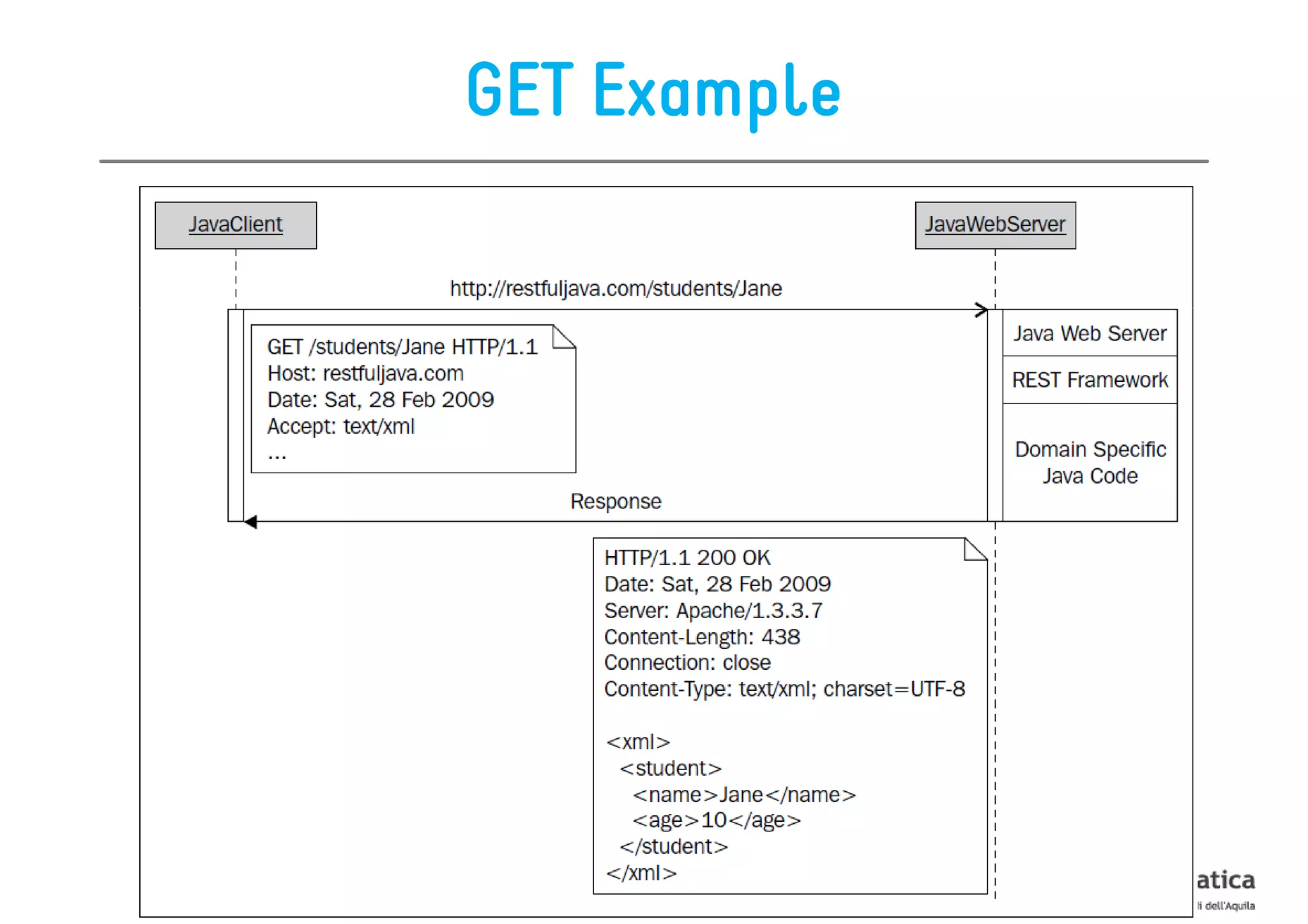
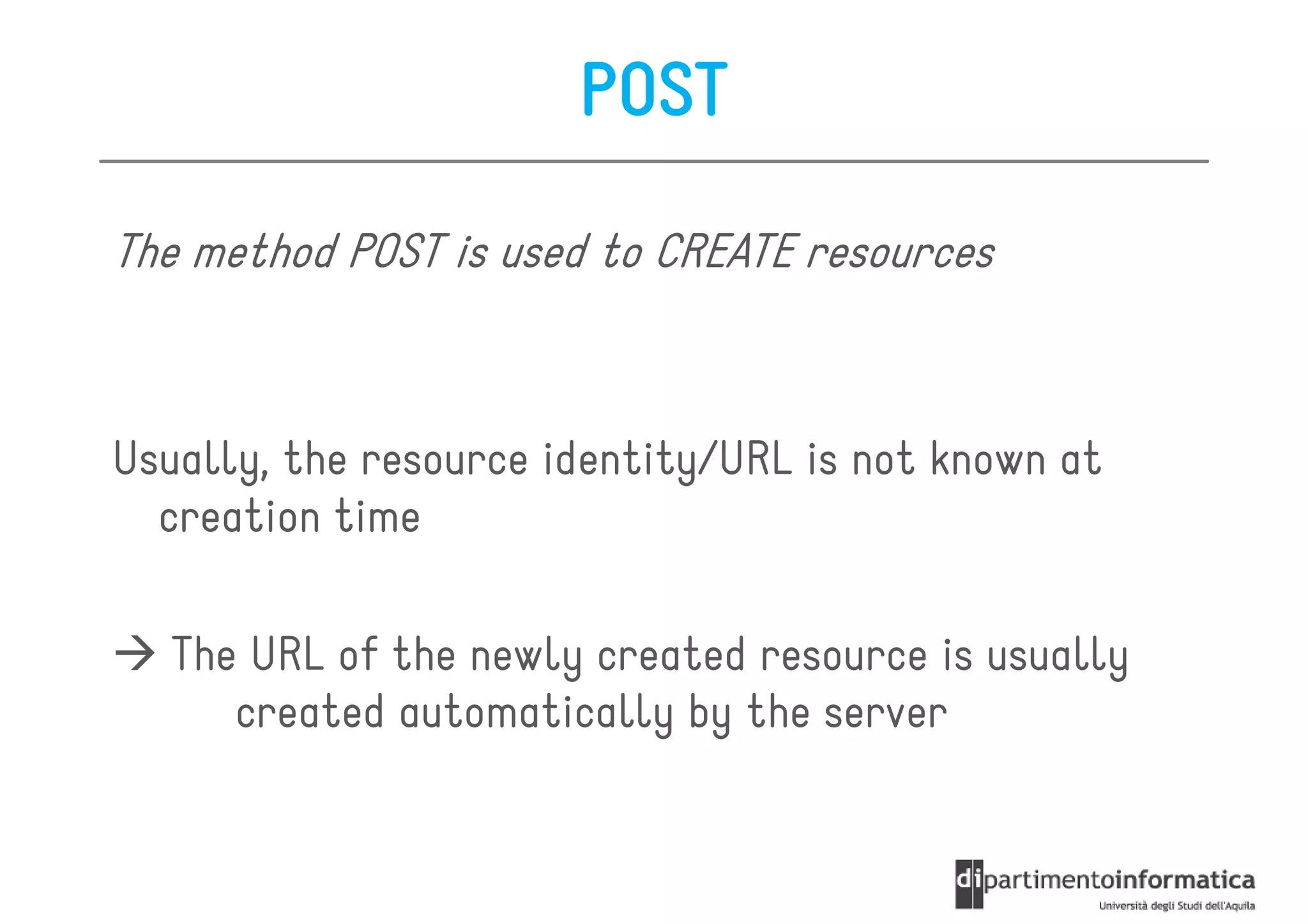
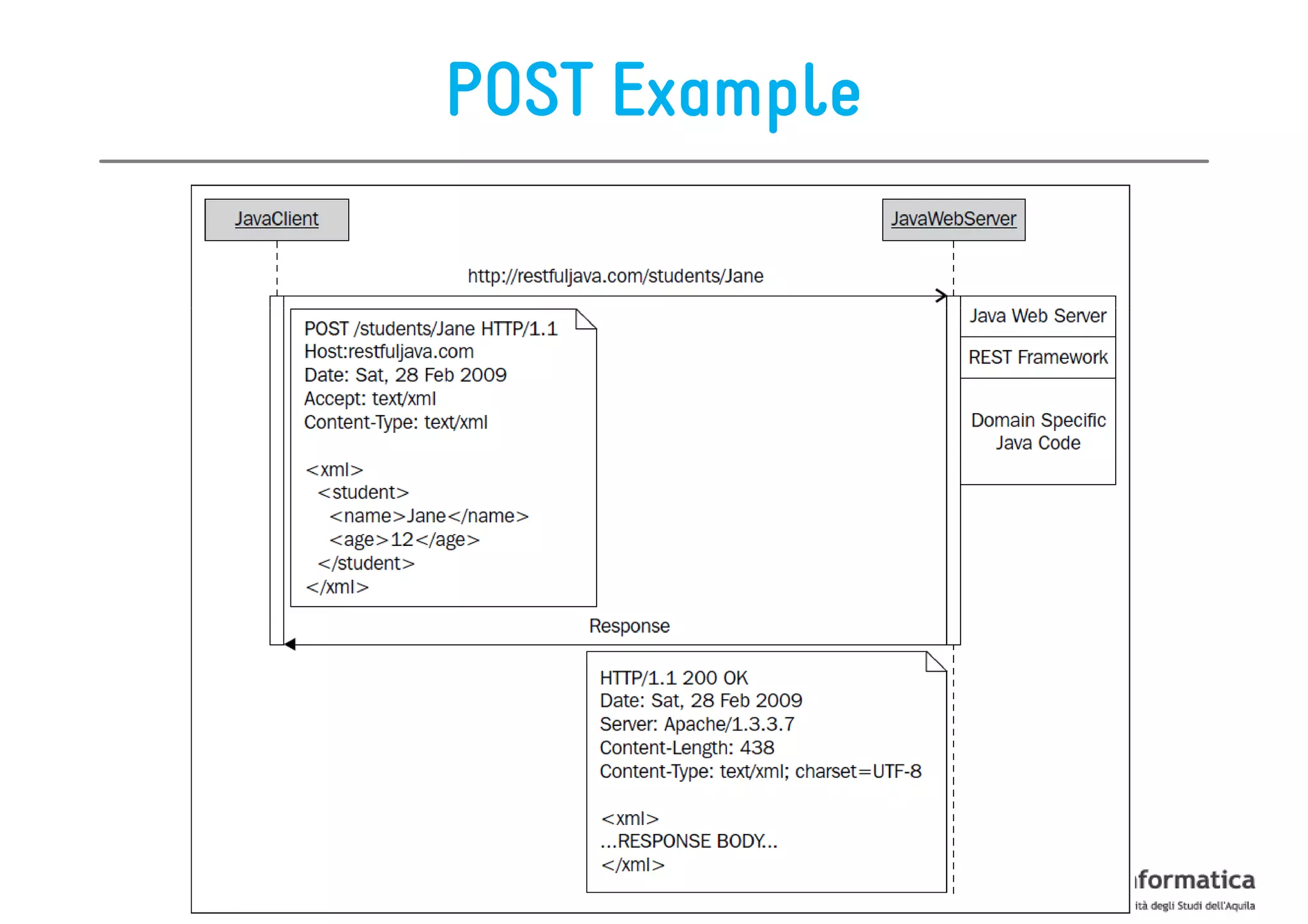
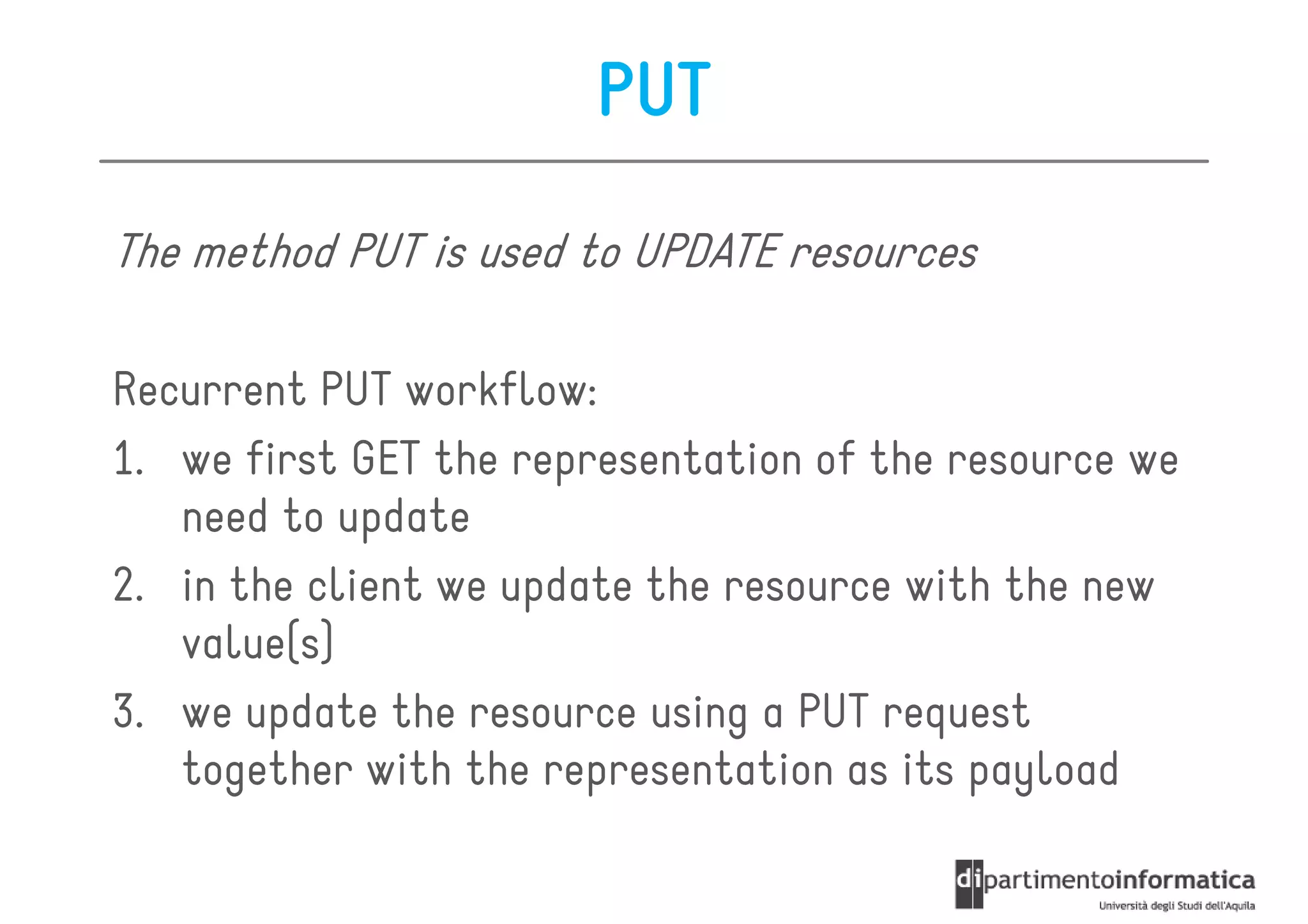
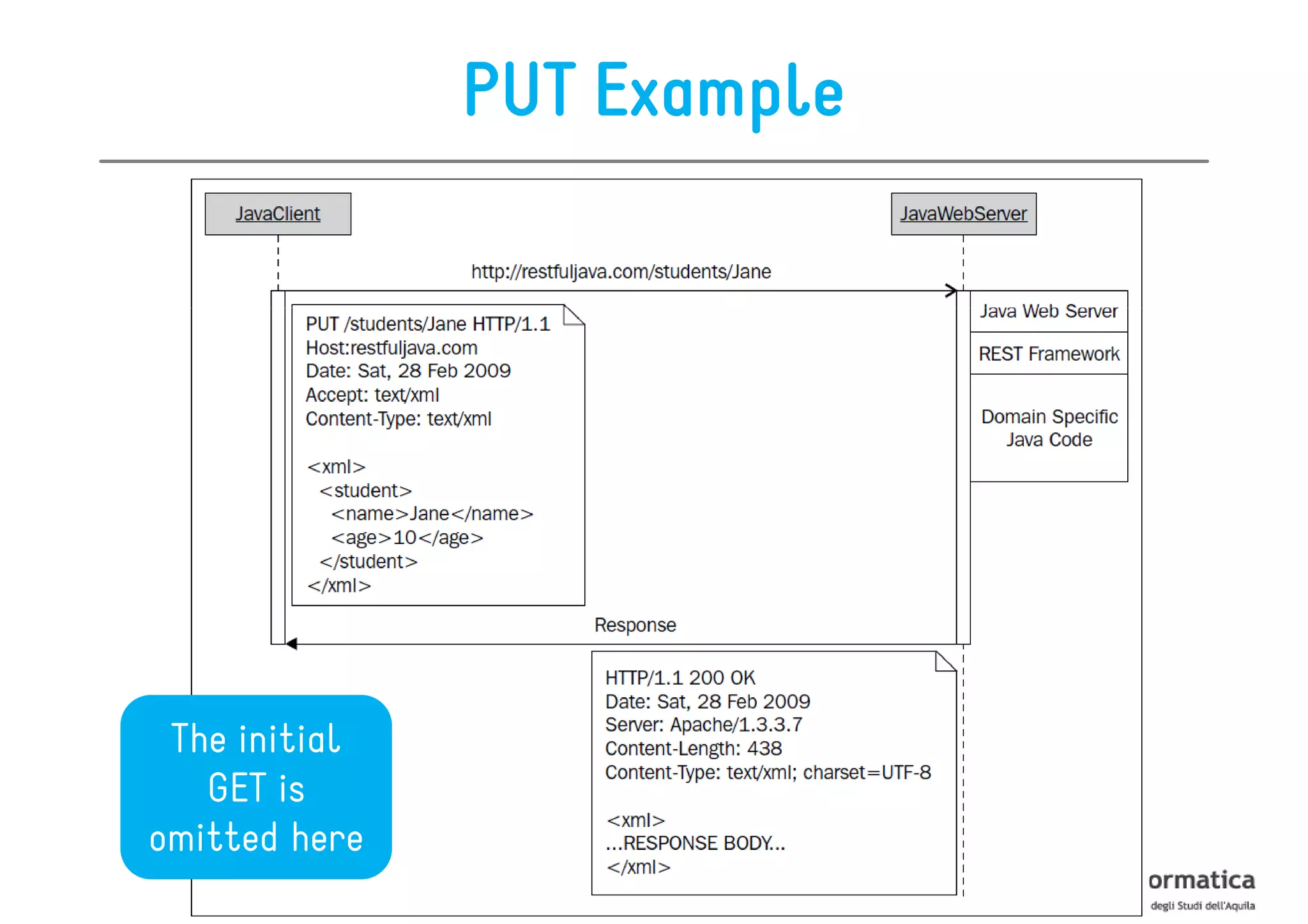
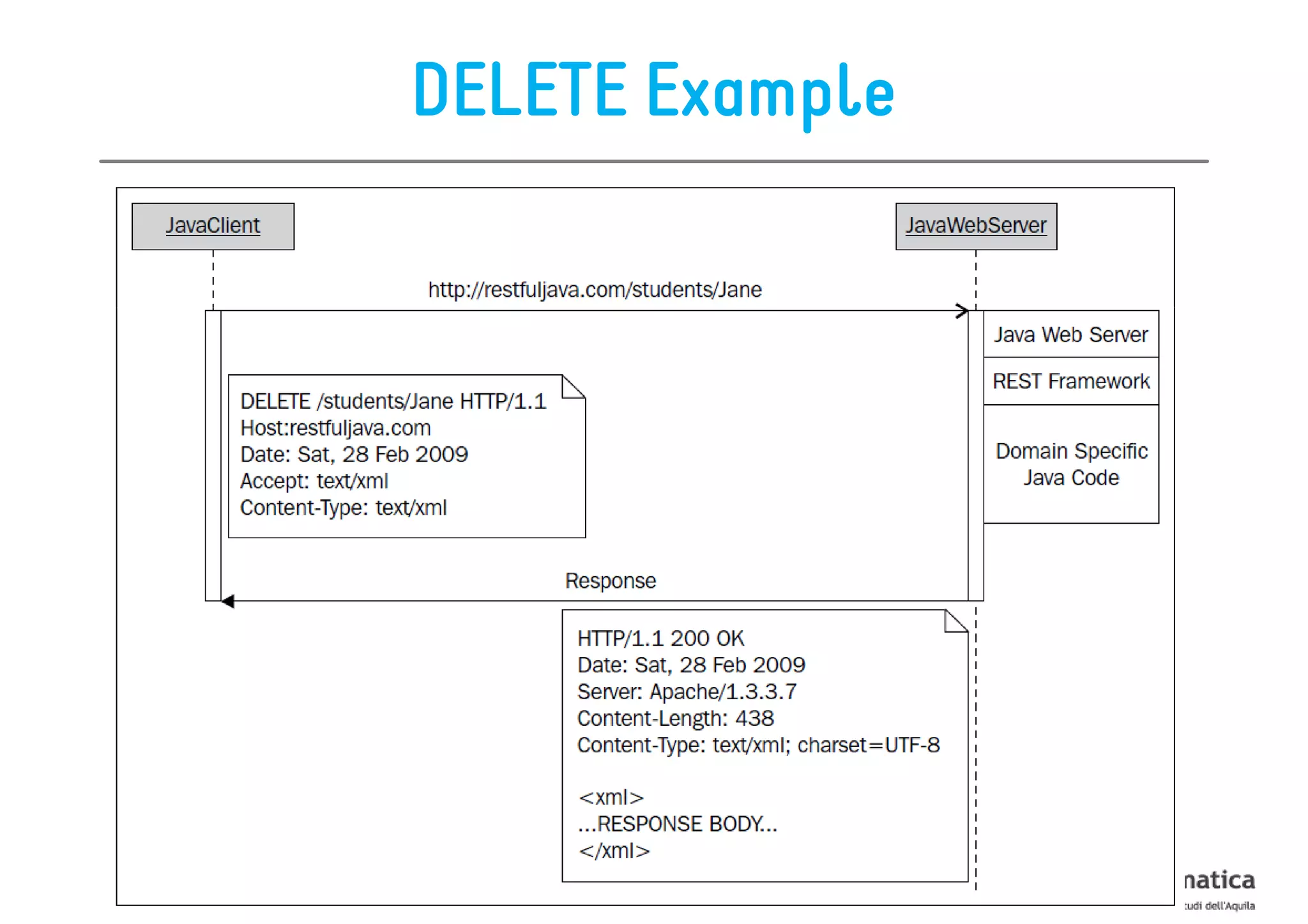
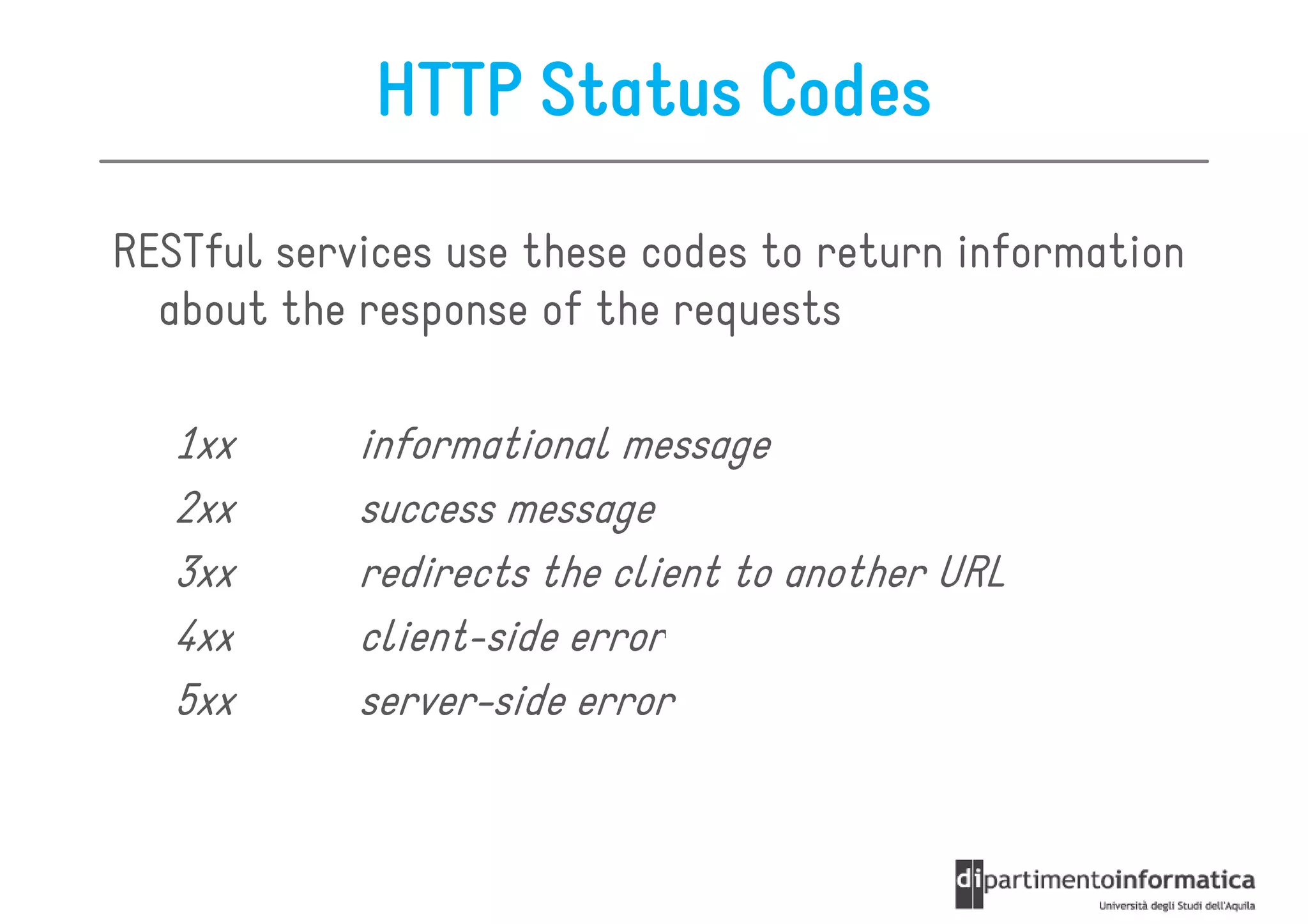
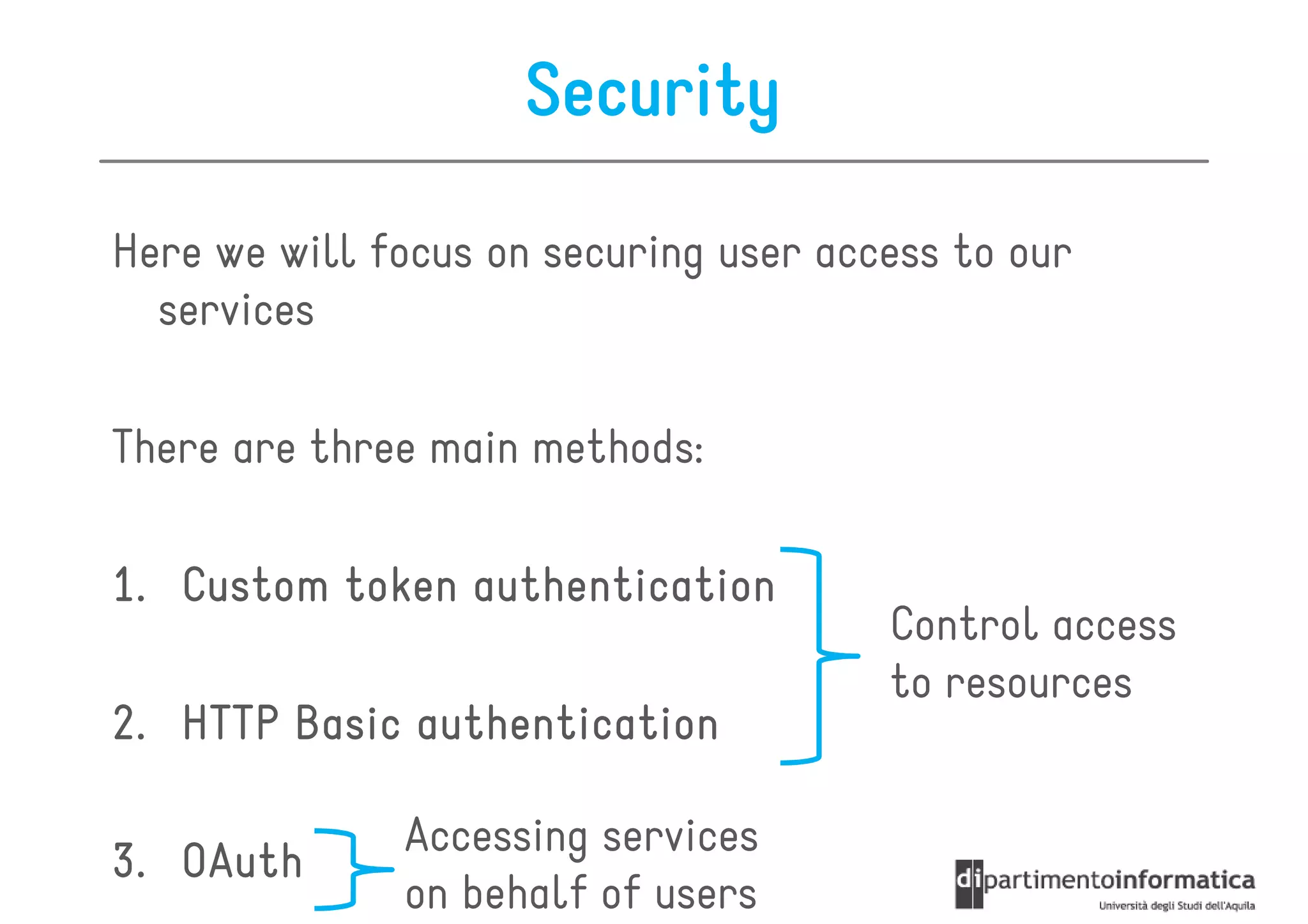
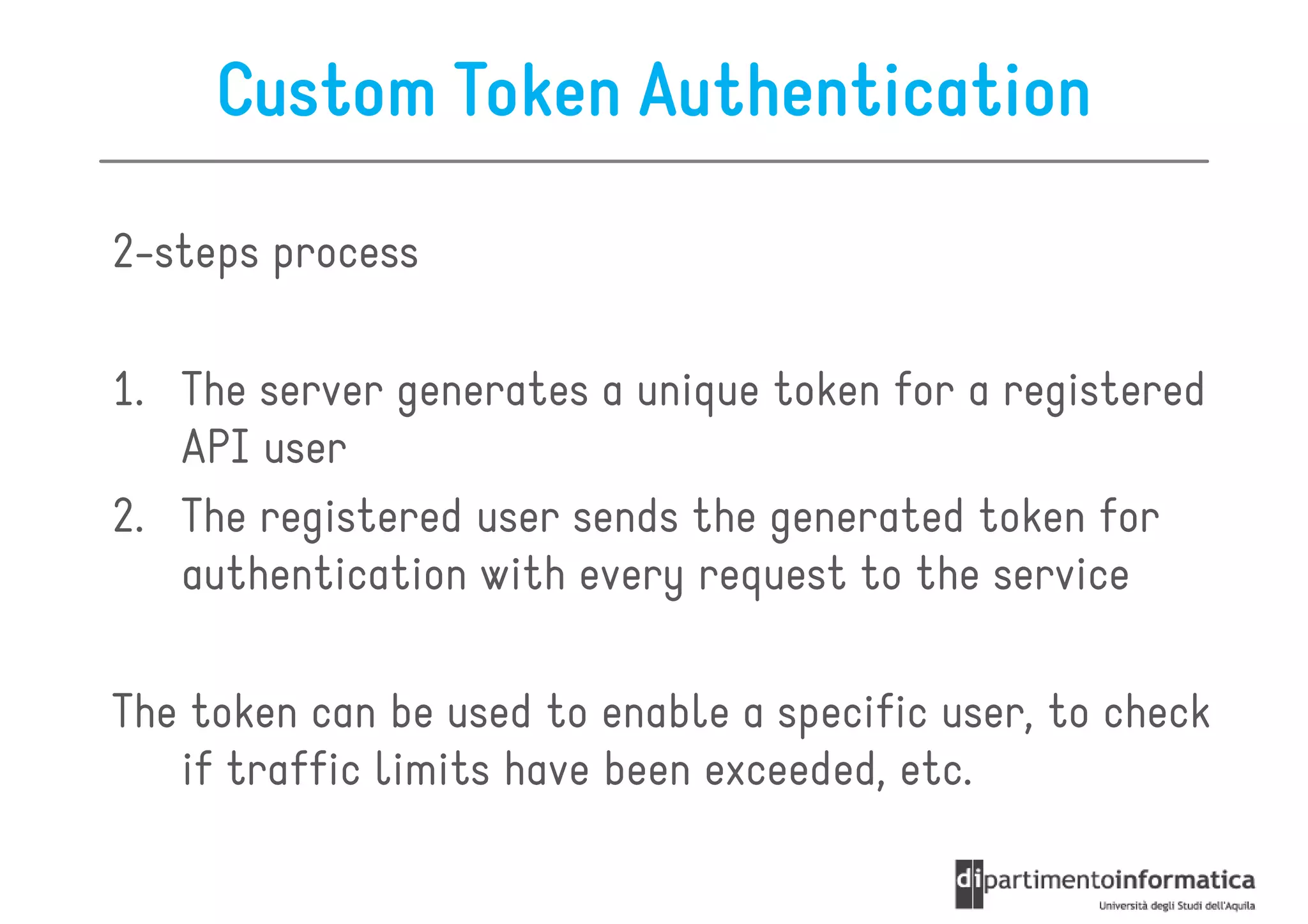
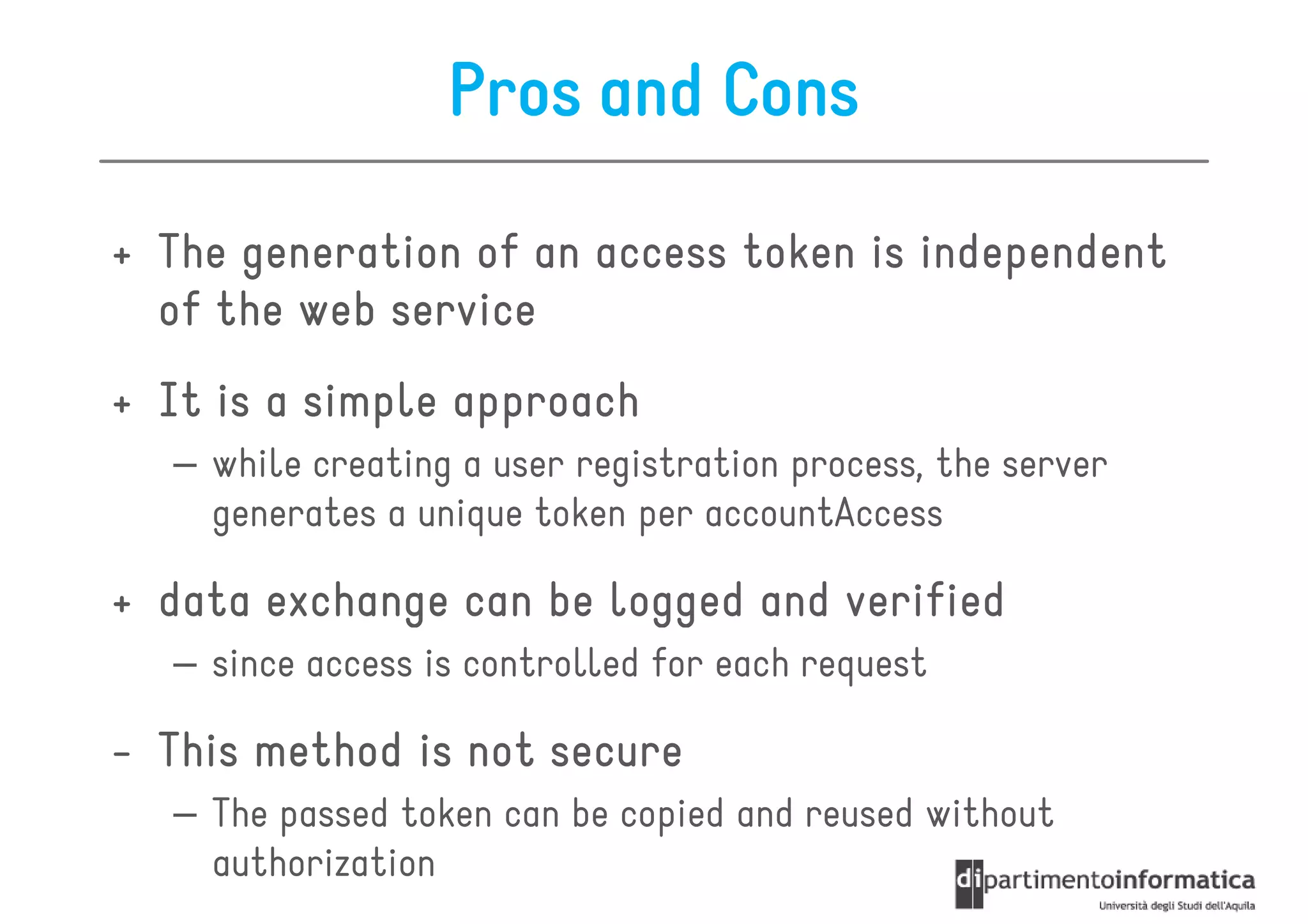
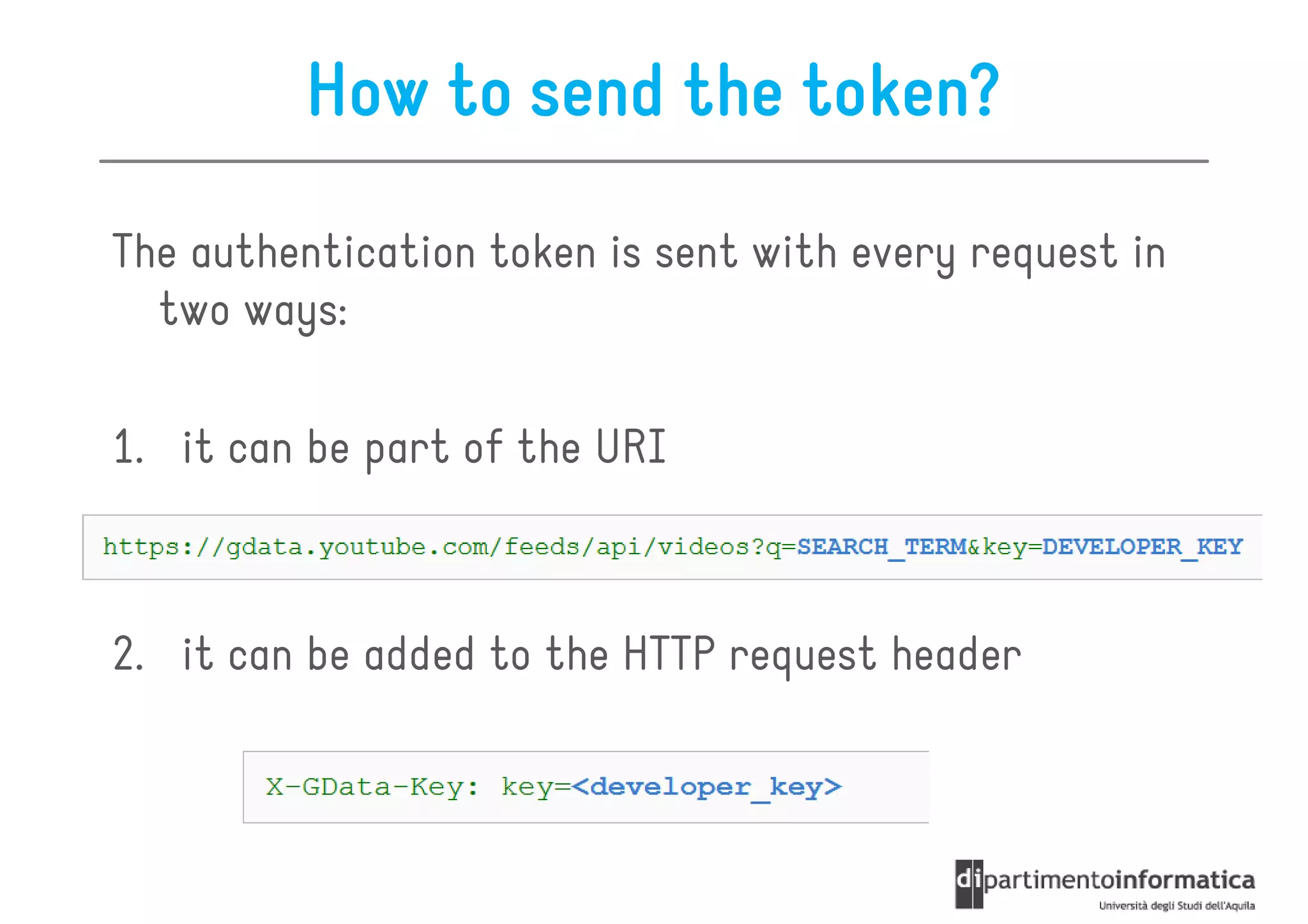
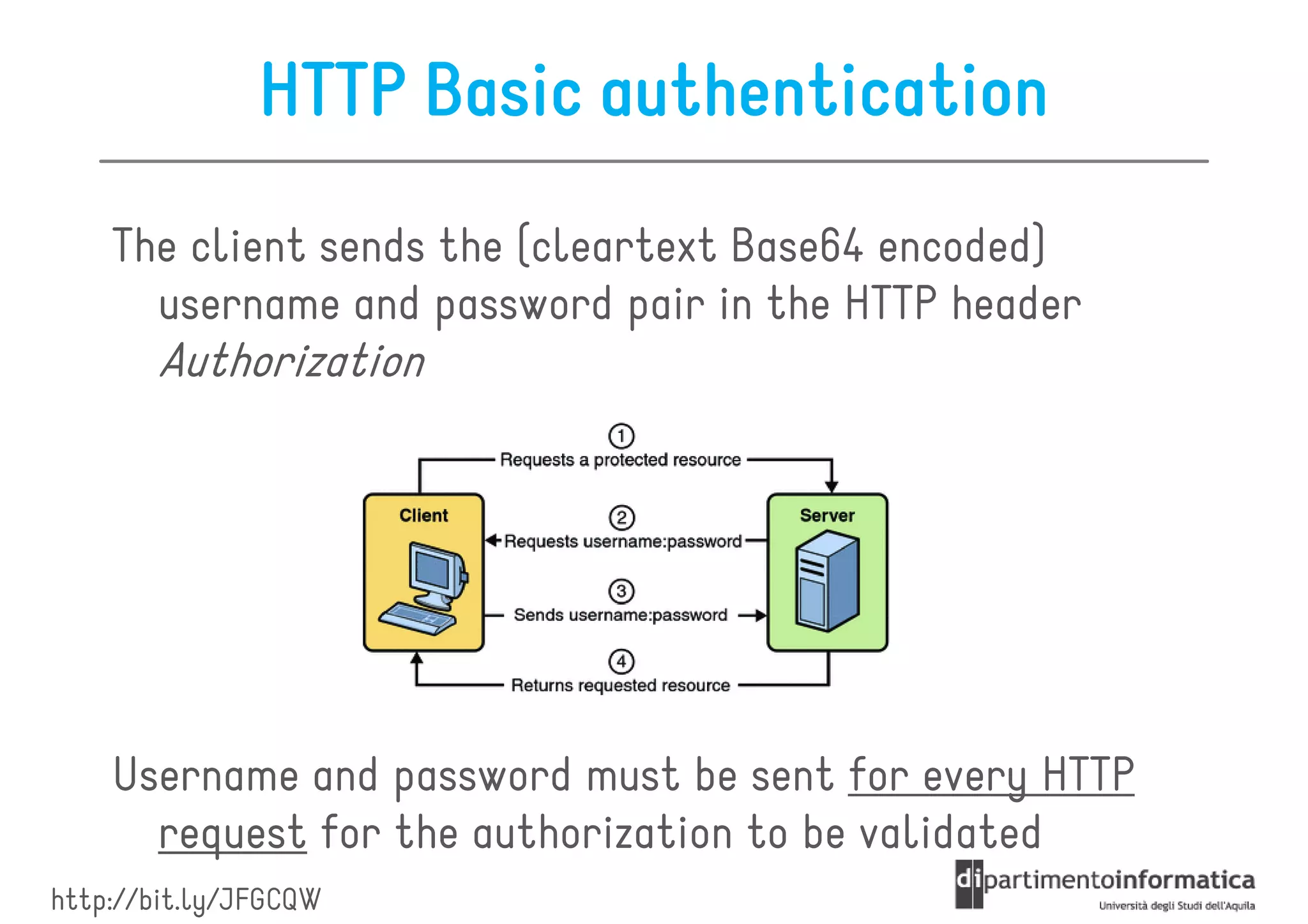
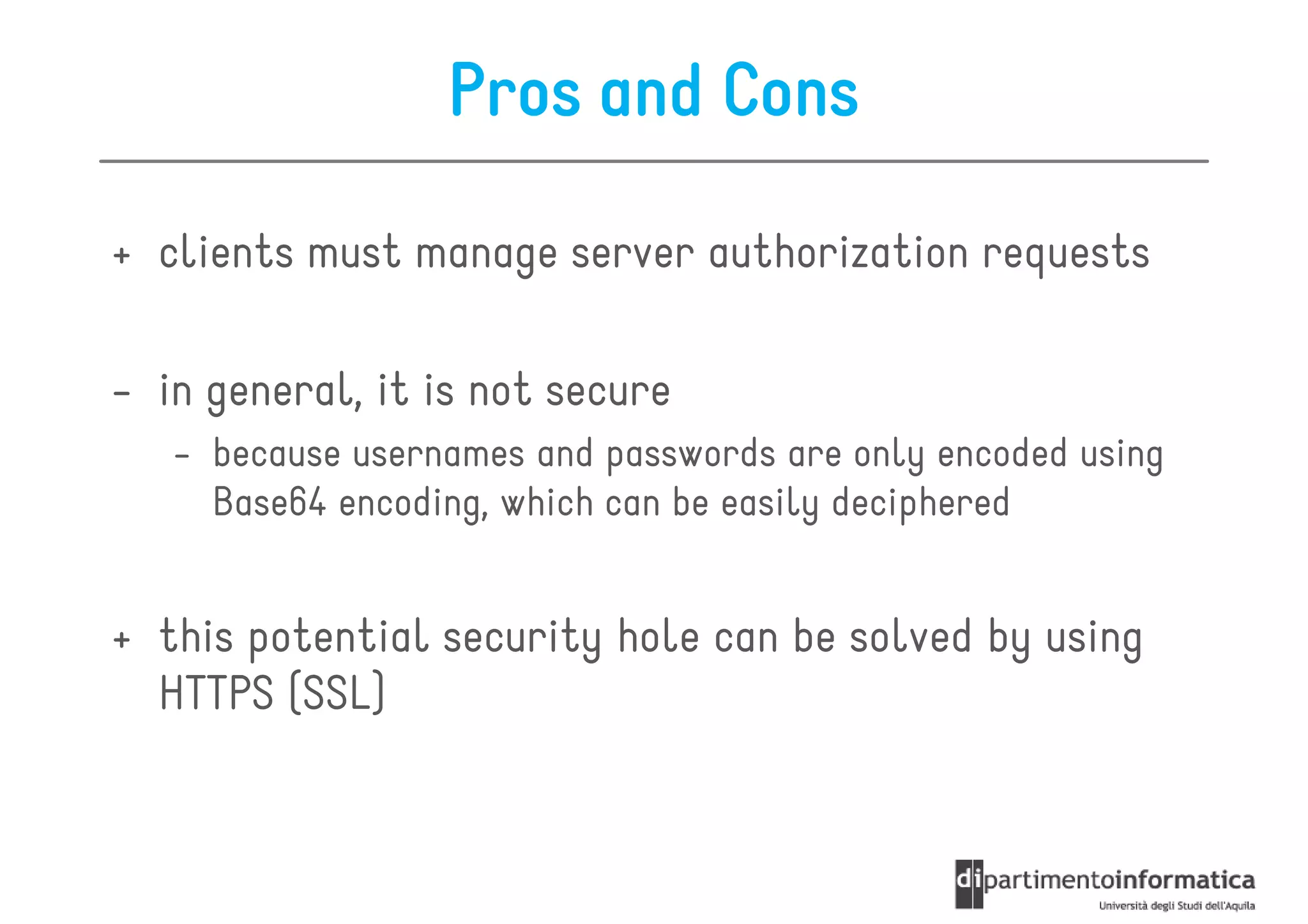
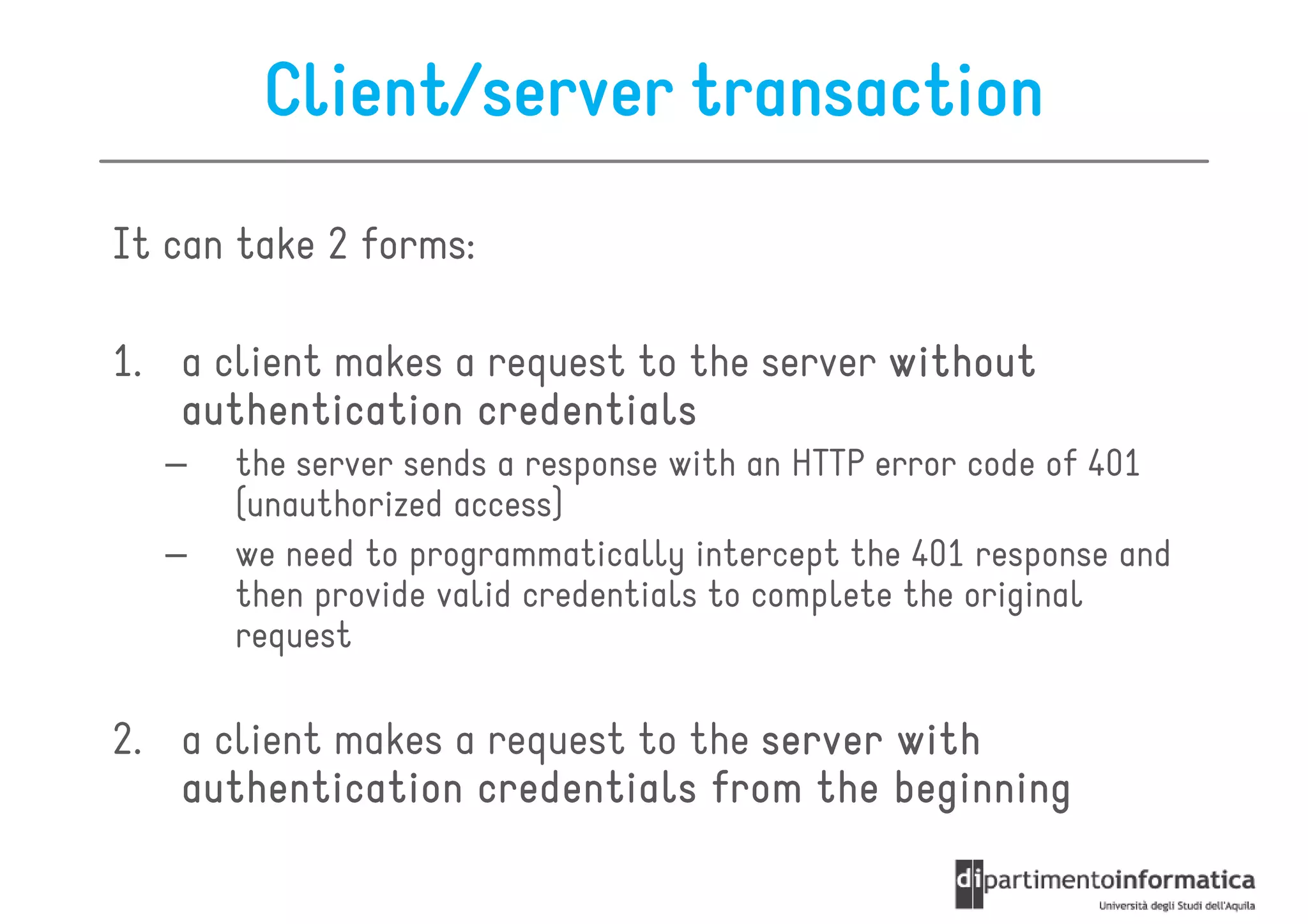
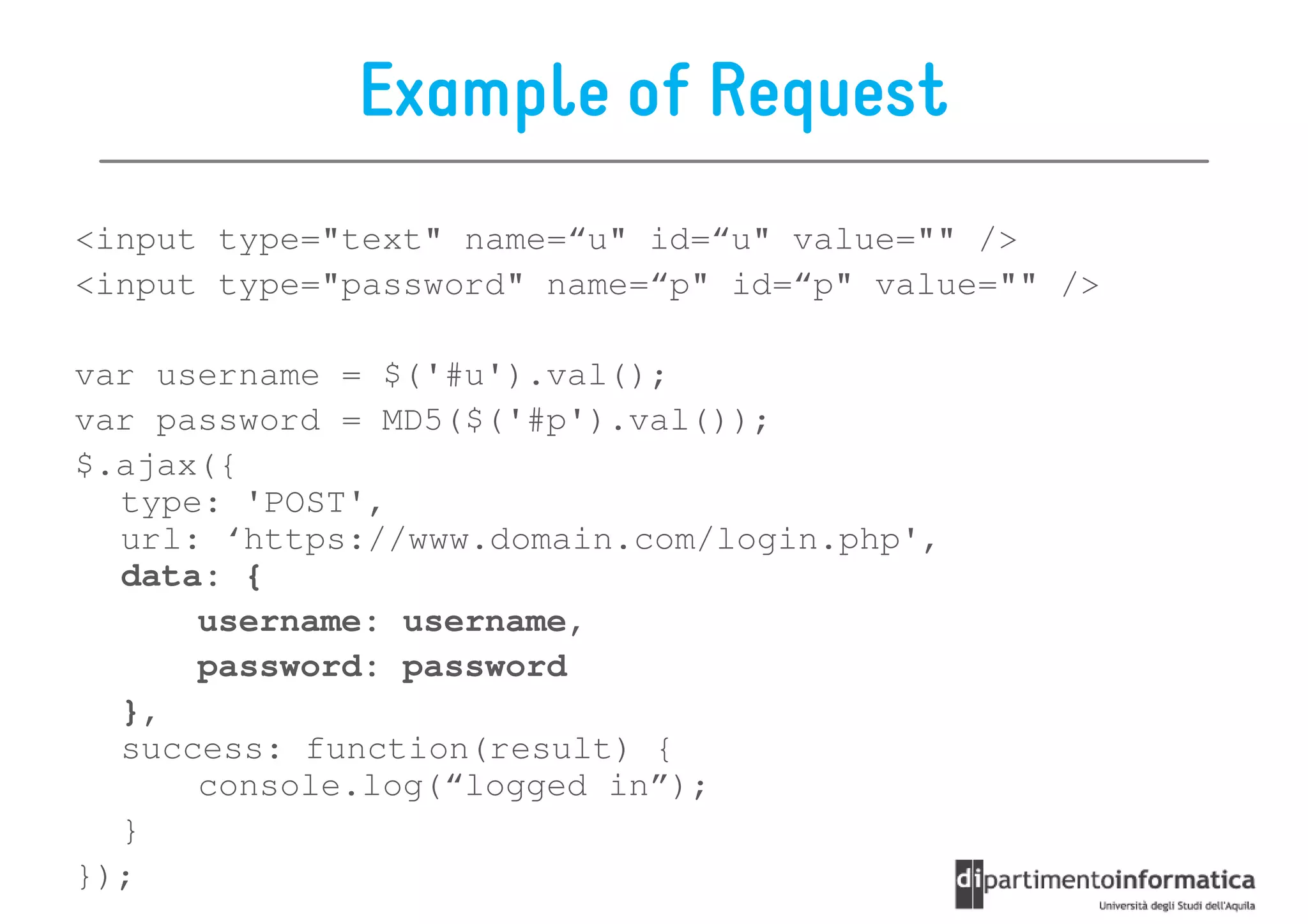
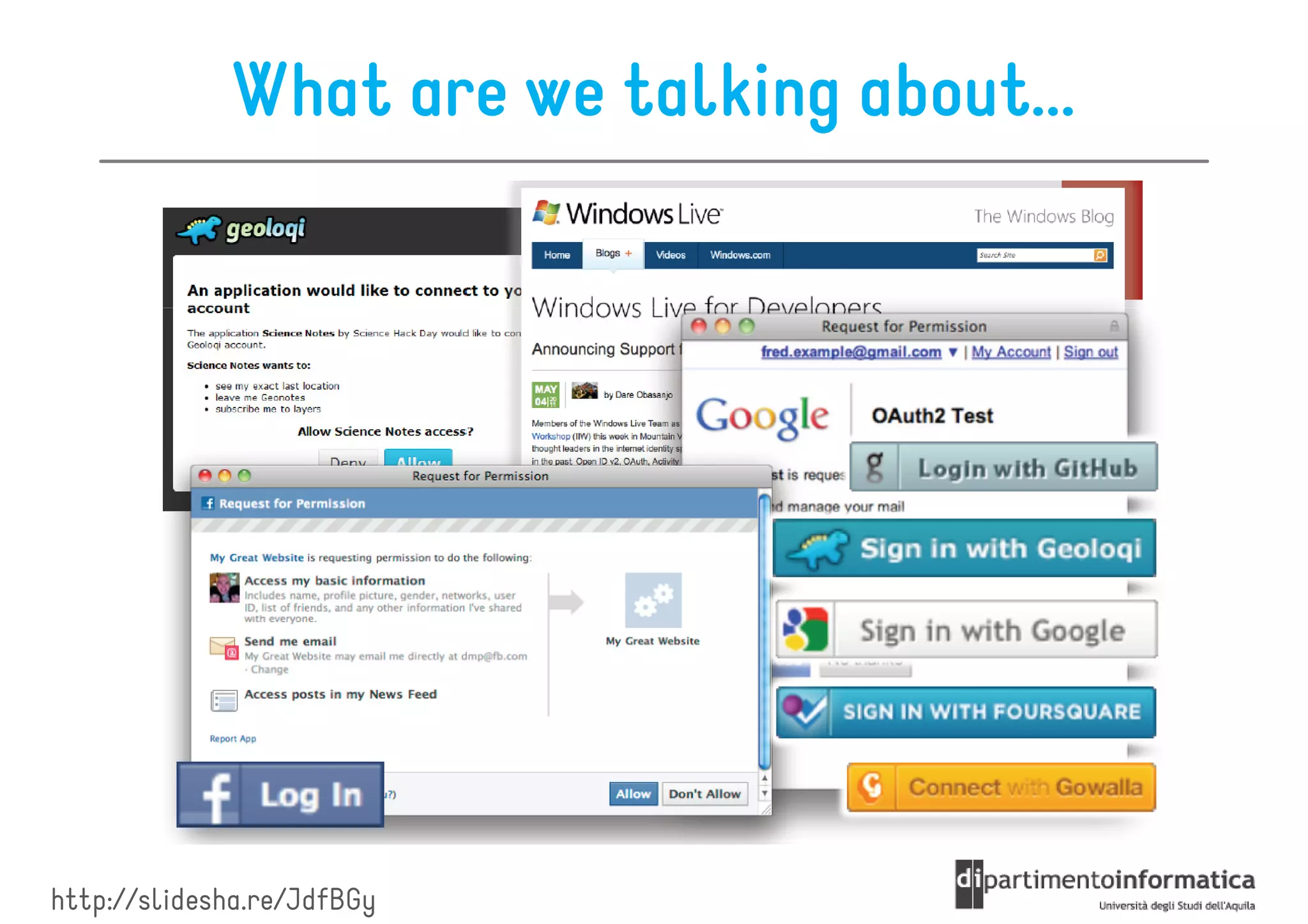
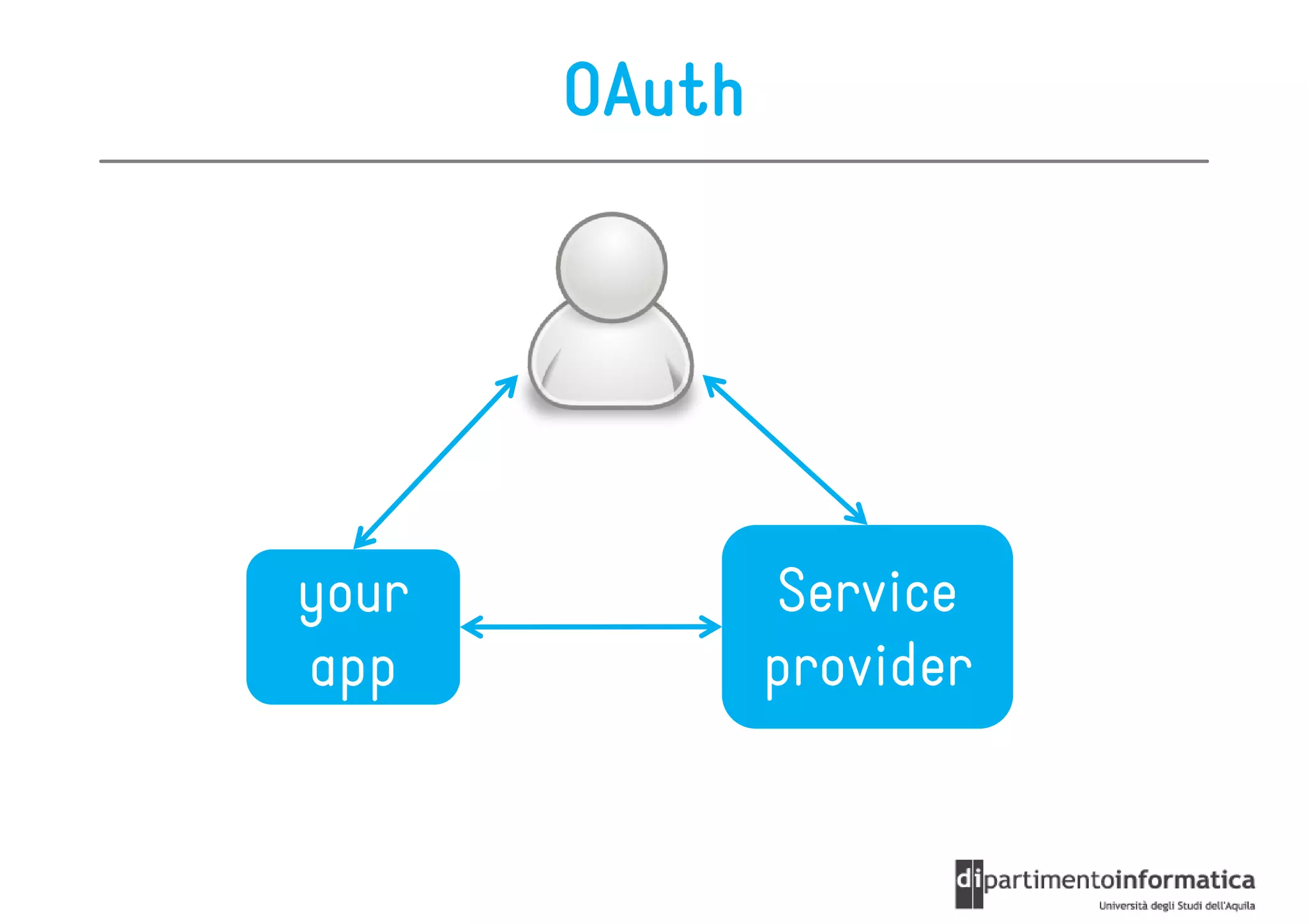
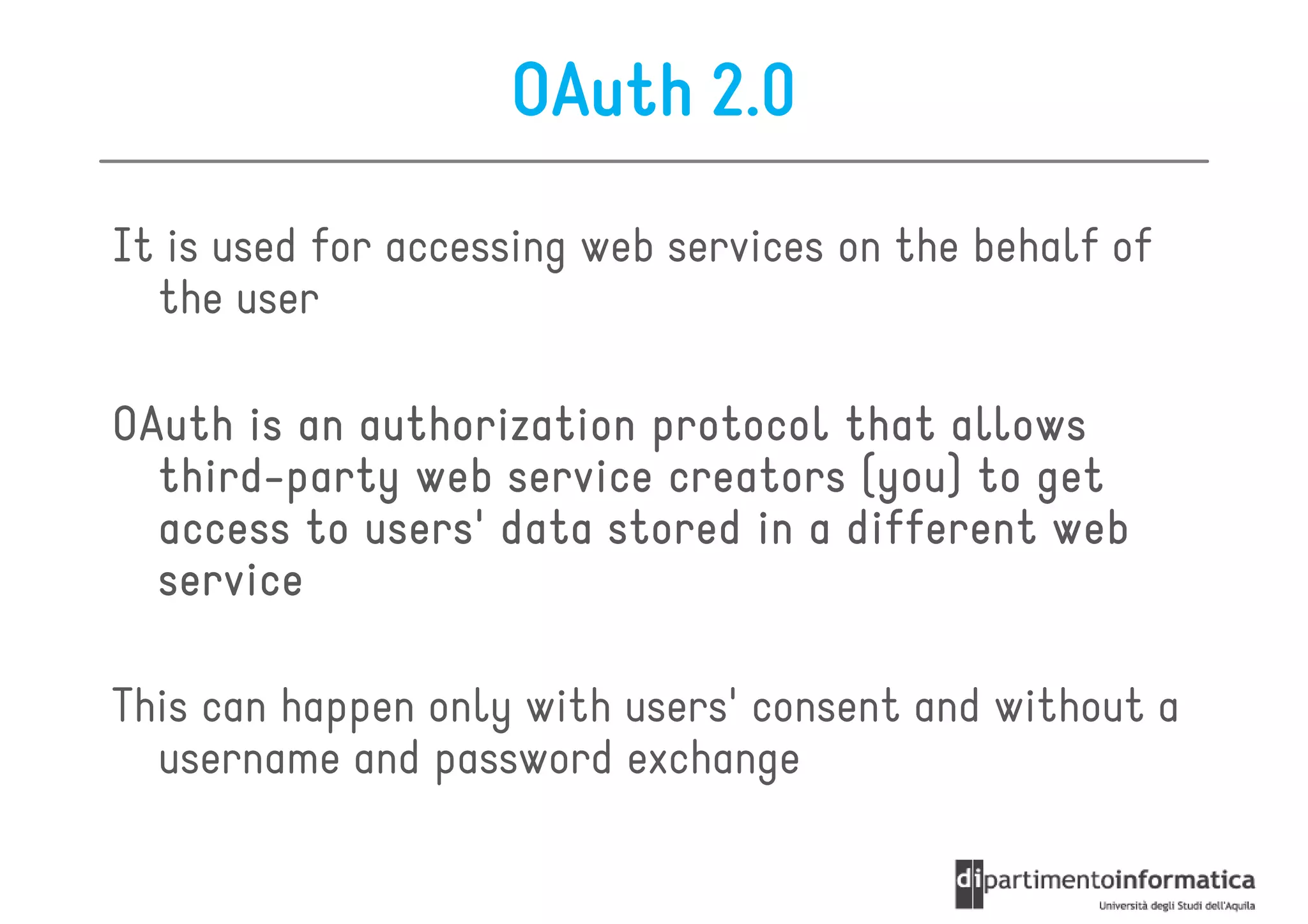
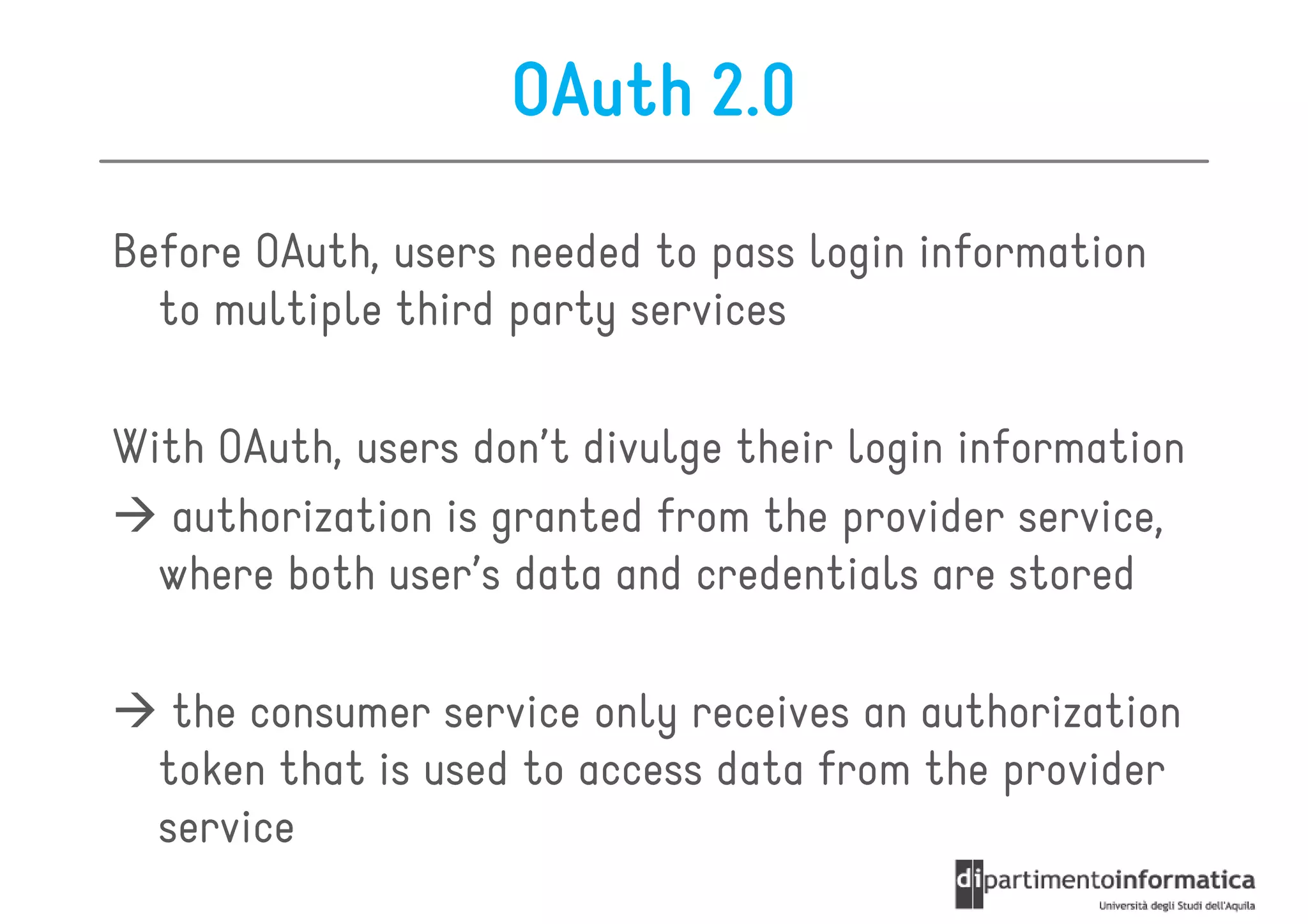
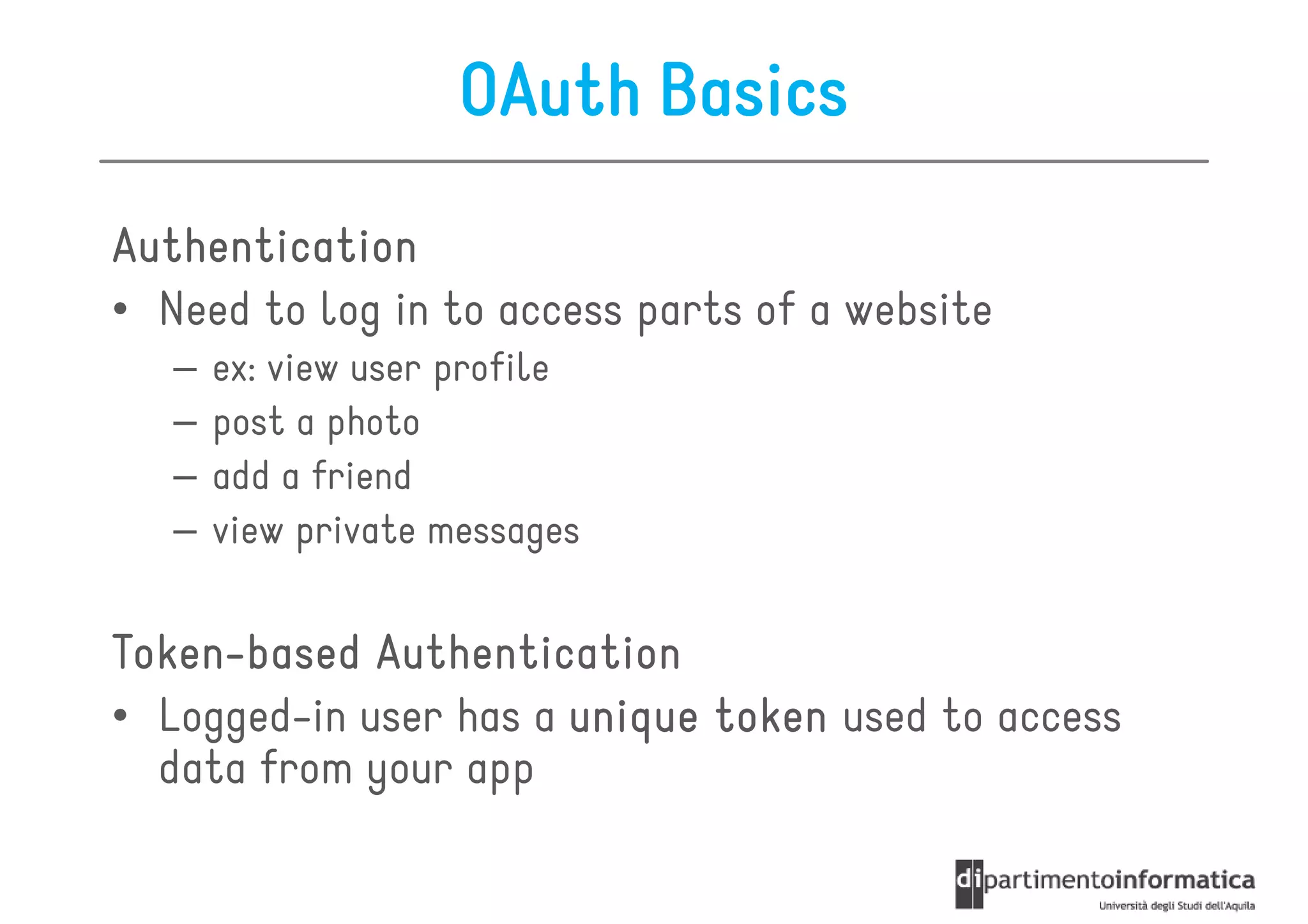
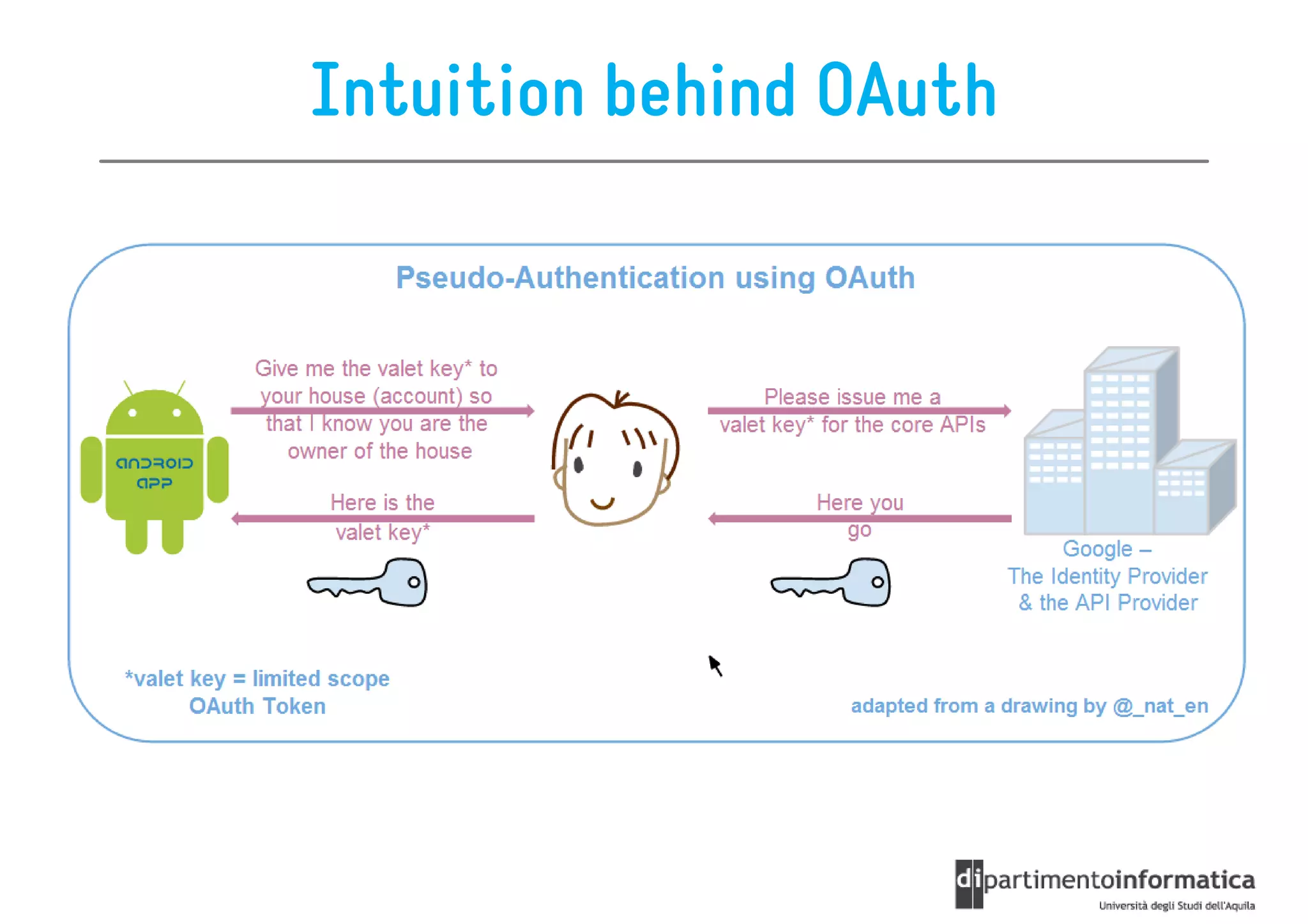
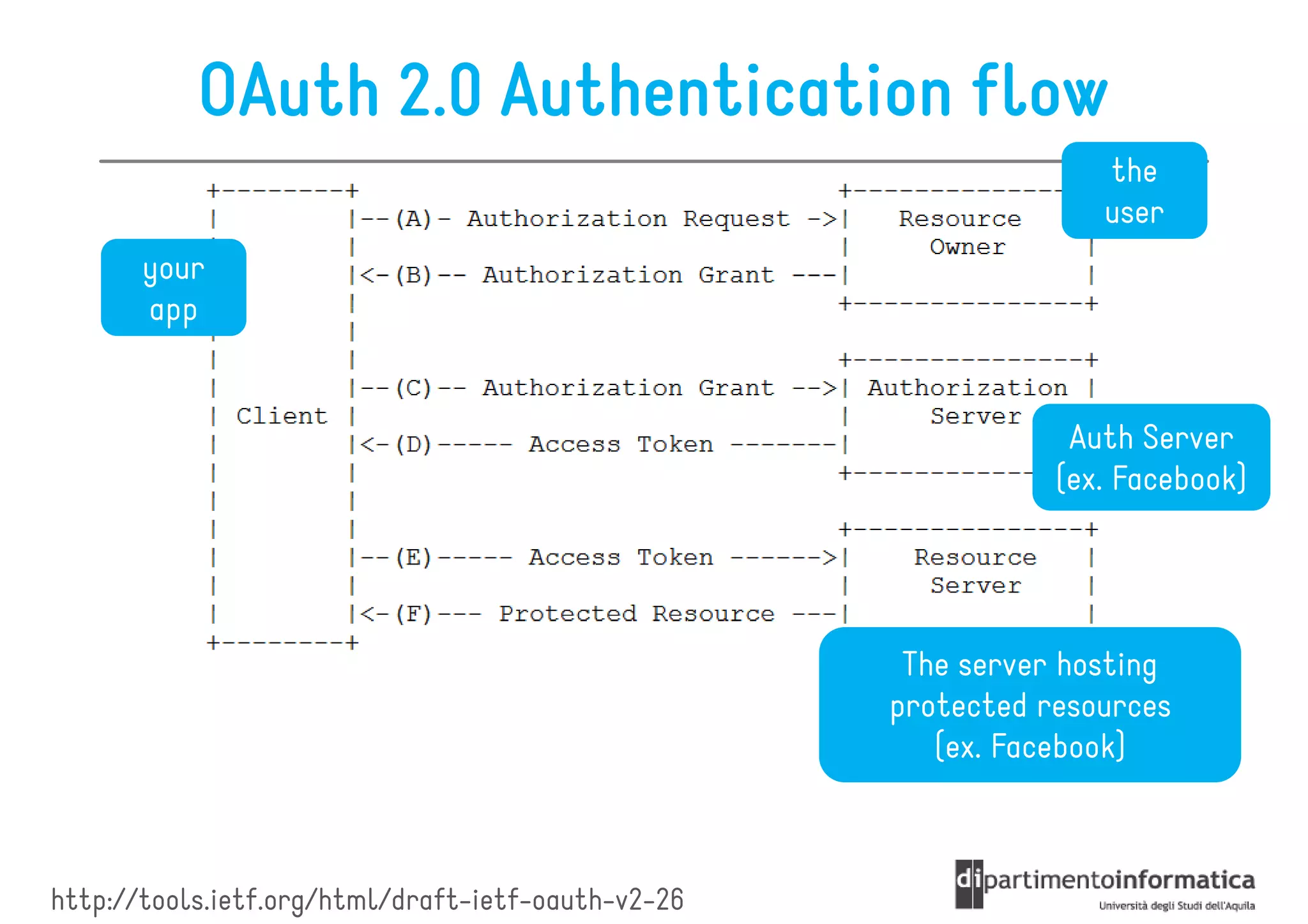
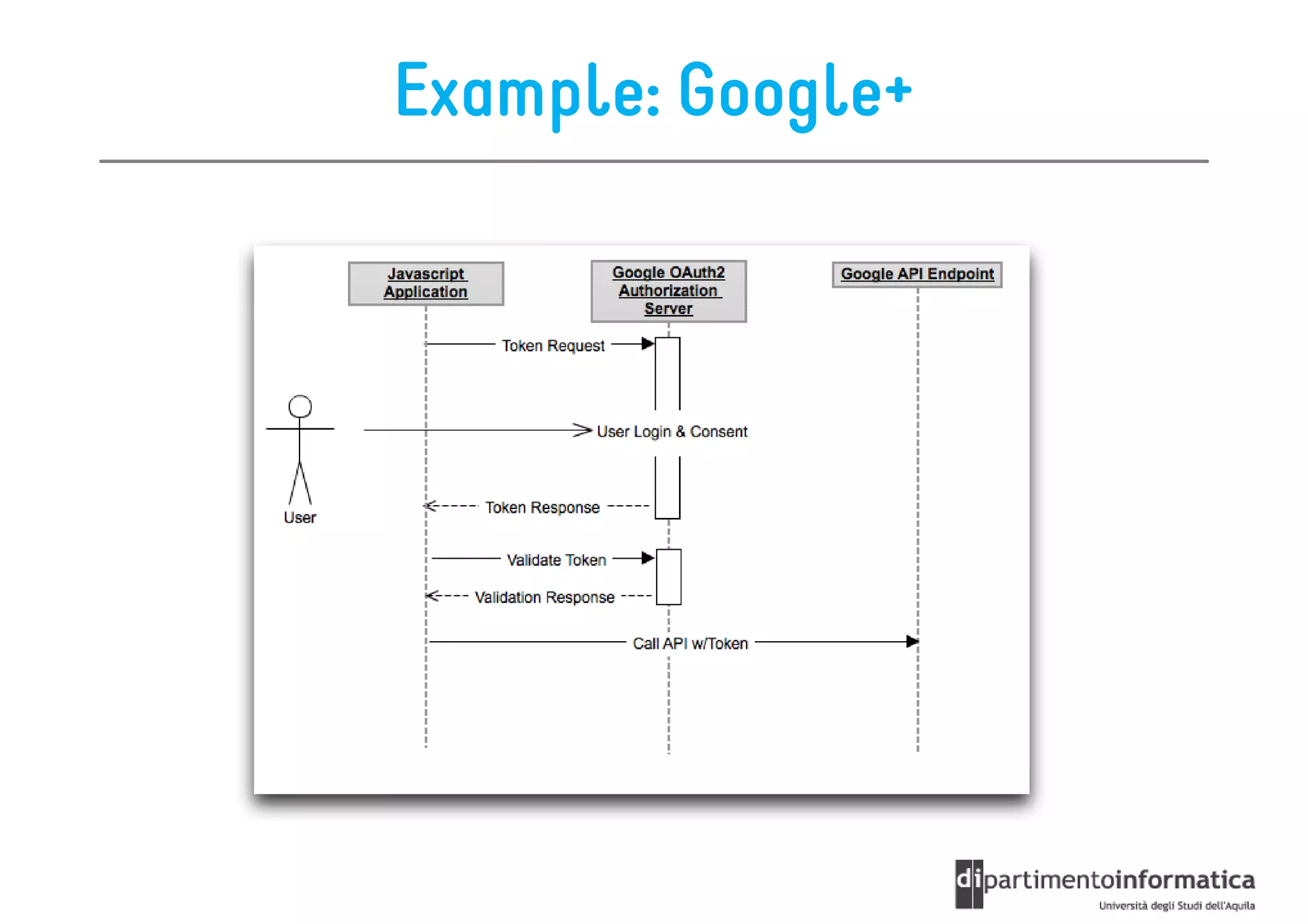
This document provides an overview of the REST architectural style, outlining its principles, constraints, and main components including resources, representations, and actions. It covers key operations such as GET, POST, PUT, and DELETE, as well as methods for securing RESTful services using token authentication, HTTP basic authentication, and OAuth 2.0. Additionally, it explains how URIs and representations are utilized in client-server communication, emphasizing the importance of HTTP status codes and content types in interactions.