Security operation center.pdf
•
0 likes•176 views
Detecting threats, vulnerabilities and malware at the earliest stage. With SOC network experts, you can ensure complete security of your enterprise.
Report
Share
Report
Share
Download to read offline
Recommended
Bulding Soc In Changing Threat Landscapefinal

my presentation at E-Crime abu dhabi conference about Security operation center Building and measure performance
isms-presentation.ppt

This document provides an overview of information security management systems (ISMS) and the ISO/IEC 27001 standard. It discusses how ISMS establishes a top-down, risk-based approach to securely managing an organization's information assets. Key points covered include the business drivers for ISMS, the components of an effective ISMS based on ISO 27001, and the steps involved in implementing, certifying and maintaining an ISMS over time.
Security Operations Center (SOC) Essentials for the SME

Closing the gaps in security controls, systems, people and processes is not an easy feat, particularly for IT practitioners in smaller organizations with limited budgets and few (if any) dedicated security staff. So, what are the essential security capabilities needed to establish a security operations center and start closing those gaps?
Join Javvad Malik of 451 Research and Patrick Bedwell, VP of Product Marketing at AlienVault for this session covering:
*Developments in the threat landscape driving a shift from preventative to detective controls
*Essential security controls needed to defend against modern threats
*Fundamentals for evaluating a security approach that will work for you, not against you
*How a unified approach to security visibility can help you get from install to insight more quickly
The Next Generation of Security Operations Centre (SOC)

The document discusses the key aspects of building a next generation Security Operations Centre (SOC). It emphasizes that skilled people, well-defined processes, and integrating new technologies are critical. Specifically, it recommends adopting automation and analytics to analyze large datasets, integrating threat intelligence from multiple sources, and establishing red and blue teams to continuously test defenses. The goal of a next generation SOC is to use predictive analysis of vast security data to improve threat detection, response, and the overall security posture of an organization.
Security operation center (SOC)

The document discusses security operation centers (SOCs) and their functions. It describes what a SOC is and its main purpose of monitoring, preventing, detecting, investigating and responding to cyber threats. It outlines the typical roles in a SOC including tier 1, 2 and 3 analysts and security engineers. It also discusses the common tools, skills needed for each role, and types of SOCs such as dedicated, distributed, multifunctional and virtual SOCs.
An introduction to SOC (Security Operation Center)

The document discusses building a security operations center (SOC). It defines a SOC as a centralized unit that deals with security issues on an organizational and technical level. It monitors, assesses, and defends enterprise information systems. The document discusses whether to build an internal SOC or outsource it. It also covers SOC technologies, personnel requirements, and the five generations of SOCs. It provides resources for learning more about designing and maturing a SOC.
Building a Next-Generation Security Operation Center Based on IBM QRadar and ...

Learn about Sogeti’s journey of creating a new Security Operation Center, and how and why we leveraged QRadar solutions. We explore the full program lifecycle, from strategic choices to technical analysis and benchmarking on the product. We explain how QRadar accelerates the go-to-market of the SOC, and how we embed IBM Security Intelligence offerings in our solution. Having a strong collaboration between different IBM stakeholders such as Software Group, Global Technology Services, as well as the Labs, was key to client satisfaction and operational effectiveness. We also show the value of integrating new QRadar features in our SOC roadmap, in order to constantly stay ahead in the cyber security game.
Security operation center

Insight is one of the best security operation center that influences all the necessary things that reduce the advanced threats and security risk all over your company and protects your network infrastructure across the organization. https://insightmsp.co.in/soc-as-service.php
Recommended
Bulding Soc In Changing Threat Landscapefinal

my presentation at E-Crime abu dhabi conference about Security operation center Building and measure performance
isms-presentation.ppt

This document provides an overview of information security management systems (ISMS) and the ISO/IEC 27001 standard. It discusses how ISMS establishes a top-down, risk-based approach to securely managing an organization's information assets. Key points covered include the business drivers for ISMS, the components of an effective ISMS based on ISO 27001, and the steps involved in implementing, certifying and maintaining an ISMS over time.
Security Operations Center (SOC) Essentials for the SME

Closing the gaps in security controls, systems, people and processes is not an easy feat, particularly for IT practitioners in smaller organizations with limited budgets and few (if any) dedicated security staff. So, what are the essential security capabilities needed to establish a security operations center and start closing those gaps?
Join Javvad Malik of 451 Research and Patrick Bedwell, VP of Product Marketing at AlienVault for this session covering:
*Developments in the threat landscape driving a shift from preventative to detective controls
*Essential security controls needed to defend against modern threats
*Fundamentals for evaluating a security approach that will work for you, not against you
*How a unified approach to security visibility can help you get from install to insight more quickly
The Next Generation of Security Operations Centre (SOC)

The document discusses the key aspects of building a next generation Security Operations Centre (SOC). It emphasizes that skilled people, well-defined processes, and integrating new technologies are critical. Specifically, it recommends adopting automation and analytics to analyze large datasets, integrating threat intelligence from multiple sources, and establishing red and blue teams to continuously test defenses. The goal of a next generation SOC is to use predictive analysis of vast security data to improve threat detection, response, and the overall security posture of an organization.
Security operation center (SOC)

The document discusses security operation centers (SOCs) and their functions. It describes what a SOC is and its main purpose of monitoring, preventing, detecting, investigating and responding to cyber threats. It outlines the typical roles in a SOC including tier 1, 2 and 3 analysts and security engineers. It also discusses the common tools, skills needed for each role, and types of SOCs such as dedicated, distributed, multifunctional and virtual SOCs.
An introduction to SOC (Security Operation Center)

The document discusses building a security operations center (SOC). It defines a SOC as a centralized unit that deals with security issues on an organizational and technical level. It monitors, assesses, and defends enterprise information systems. The document discusses whether to build an internal SOC or outsource it. It also covers SOC technologies, personnel requirements, and the five generations of SOCs. It provides resources for learning more about designing and maturing a SOC.
Building a Next-Generation Security Operation Center Based on IBM QRadar and ...

Learn about Sogeti’s journey of creating a new Security Operation Center, and how and why we leveraged QRadar solutions. We explore the full program lifecycle, from strategic choices to technical analysis and benchmarking on the product. We explain how QRadar accelerates the go-to-market of the SOC, and how we embed IBM Security Intelligence offerings in our solution. Having a strong collaboration between different IBM stakeholders such as Software Group, Global Technology Services, as well as the Labs, was key to client satisfaction and operational effectiveness. We also show the value of integrating new QRadar features in our SOC roadmap, in order to constantly stay ahead in the cyber security game.
Security operation center

Insight is one of the best security operation center that influences all the necessary things that reduce the advanced threats and security risk all over your company and protects your network infrastructure across the organization. https://insightmsp.co.in/soc-as-service.php
Security operations center-SOC Presentation-مرکز عملیات امنیت

Cyber Security Trends
Business Concerns
Cyber Threats
The Solutions
Security Operation Center
requirement
SOC Architecture model
SOC Implementation
SOC & NOC
SOC & CSIRT
SIEM & Correlation
-----------------------------------------------------------
Definition
Gartner defines a SOC as both a team, often operating in shifts around the clock, and a facility dedicated to and organized to prevent, detect, assess and respond to cybersecurity threats and incidents, and to fulfill and assess regulatory compliance. The term "cybersecurity operation center "is often used synonymously for SOC.
A network operations center (NOC) is not a SOC, which focuses on network device management rather than detecting and responding to cybersecurity incidents. Coordination between the two is common, however.
A managed security service is not the same as having a SOC — although a service provider may offer services from a SOC. A managed service is a shared resource and not solely dedicated to a single organization or entity. Similarly, there is no such thing as a managed SOC.
Most of the technologies, processes and best practices that are used in a SOC are not specific to a SOC. Incident response or vulnerability management remain the same, whether delivered from a SOC or not. It is a meta-topic, involving many security domains and disciplines, and depending on the services and functions that are delivered by the SOC.
Services that often reside in a SOC are:
• Cyber security incident response
• Malware analysis
• Forensic analysis
• Threat intelligence analysis
• Risk analytics and attack path modeling
• Countermeasure implementation
• Vulnerability assessment
• Vulnerability analysis
• Penetration testing
• Remediation prioritization and coordination
• Security intelligence collection and fusion
• Security architecture design
• Security consulting
• Security awareness training
• Security audit data collection and distribution
Alternative names for SOC :
Security defense center (SDC)
Security intelligence center
Cyber security center
Threat defense center
security intelligence and operations center (SIOC)
Infrastructure Protection Centre (IPC)
مرکز عملیات امنیت
Implementing Vulnerability Management 

Derek Milroy, IS Security Architect at U.S. Cellular Corporation, defined “vulnerability management” and how it affects today’s organizations during his presentation at the 2014 Chief Information Security Officer (CISO) Leadership Forum in Chicago on Nov. 19. In his presentation, “Enterprise Vulnerability Management/Security Incident Response,” Milroy noted vulnerability management has different meanings to different organizations, but an organization that utilizes vulnerability management processes can effectively safeguard its data.
According to Milroy, an organization should develop its own vulnerability management baselines to monitor its security levels. By doing so, Milroy said an organization can launch and control vulnerability management systems successfully. In addition, Milroy pointed out that vulnerability management problems occasionally will arise, but a well-prepared organization will be equipped to handle such issues: “Problems are going to happen … You have to work with your people. This can translate to any tool that you’re putting in place. Make sure your people have plans for what happens when it goes wrong, because it’s going to [happen] every single time.”
Milroy also noted that having actionable vulnerability management data is important for organizations of all sizes. If an organization evaluates its vulnerability management processes regularly, Milroy said, it can collect data and use this information to improve its security: “The simplest rule of thumb for vulnerability management, click the report, hand the report to someone. Don’t ever do that. There is no such thing as a report from a tool that you can just click and hand to someone until you first tune it and pare it down.”
- See more at: http://www.argylejournal.com/chief-information-security-officer/enterprise-vulnerability-managementsecurity-incident-response-derek-milroy-is-security-architect-u-s-cellular-corporation/#sthash.Buh6CzLS.dpuf
Security Operation Center Fundamental

The document provides an introduction and agenda for a 3-day security operations center fundamentals course. Day 1 will cover famous attacks and how to confront them, as well as an introduction to security operations centers. Day 2 will discuss the key features, modules, processes, and people involved in SOCs. Day 3 will focus on the technology used in SOCs, including network monitoring, investigation, and correlation tools. The instructor is introduced and the document provides an overview of common attacks such as eavesdropping, data modification, spoofing, password attacks, denial of service, man-in-the-middle, and application layer attacks.
Balbix-New-CISO-Board-Deck.pptx

The CISO is presenting to the board of directors to introduce cyber risk management at the company. The presentation covers three key areas: introducing cyber risk and the company's framework for managing it, the strategic roadmap and metrics for the information security function, and establishing information security as a board-level topic. The goal is to help the board understand cybersecurity risks, provide oversight of risk management, and introduce the CISO's vision and plans to improve the security posture.
Cyber Security Seminar.pptx

The document provides an overview of cyber security as a career option. It discusses how cyber security protects internet-connected systems from cyber threats. It outlines the growing global market size for cyber security and increasing demand for cyber security specialists. Key skills needed for the field include technical degrees, security testing experience, and problem solving abilities. Popular job titles include cyber security analyst, engineer, and chief information security officer, with salaries ranging from $80,000 to $230,000. Top certifications include CISSP, CISA, and security-related certifications from EC Council.
SOC Cyber Security

Find out the SOC Cyber Security at Steppa. Our SOC contains several capabilities like process and break down any PC translated information, assess and distinguish suspicious and maicious web and system activities, visualize and monitor all threats in real time.
Building Security Operation Center

The document discusses building a security operations center (SOC) and provides information on why an organization would build a SOC, how to establish the necessary skills and processes, and technology solutions like HP ArcSight that can be used. It describes how HP consultants have experience building SOCs for major companies and can help customers establish an effective SOC to monitor for security events, ensure compliance, and protect the organization. It provides details on how to structure a SOC, including defining roles and processes, implementing a security information and event management (SIEM) system, and establishing performance metrics to improve over time.
Cyber Resilience – Strengthening Cybersecurity Posture & Preparedness by Phil...

World Continuity Congress conference on 7th October 2015 at Pullman Putrajaya Lakeside by BCM Institute
Building a Cyber Security Operations Center for SCADA/ICS Environments

Abstract: Modern day cyber threats are ever increasing in sophistication and evasiveness against Process Control Networks. Organizations in the industry are facing a constant challenge to adopt modern techniques to proactively monitor the security posture within the SCADA infrastructure whilst keeping cyber attackers and threat actors at bay.
In this presentation we will cover the fundamental building blocks of building a SCADA cyber security operations center with key responsibilities such as Incident Response Management, Vulnerability and Patch Management, Secure-by-design Architecture, Security Logging and Monitoring and how such security domains drive accountability and act as a line of authority across the PCN.
Cyber Security Operations Center (C-SOC) 

The document discusses the benefits of exercise for mental health. Regular physical activity can help reduce anxiety and depression and improve mood and cognitive functioning. Exercise causes chemical changes in the brain that may help protect against mental illness and improve symptoms.
Guide to Risk Management Framework (RMF)

Navigating the complex Risk Management Framework (RMF) requirements can be daunting. Learn best practices and gain a better understanding of NIST's RMF.
Cybersecurity Roadmap Development for Executives

Secrets to managing your Duty of Care in an ever- changing world.
How well do you know your risks?
Are you keeping up with your responsibilities to provide Duty of Care?
How well are you prioritising Cybersecurity initiatives?
Liability for Cybersecurity attacks sits with Executives and Board members who may not have the right level of technical security knowledge. This session will outline what practical steps executives can take to implement a Cybersecurity Roadmap that is aligned with its strategic objectives.
Led by Krist Davood, who has spent over 28 years implementing secure mission critical systems for executives. Krist is an expert in protecting the interconnectedness of technology, intellectual property and information systems, as evidenced through his roles at The Good Guys, Court Services Victoria and Schiavello.
The seminar will cover:
• Fiduciary responsibility
• How to efficiently deal with personal liability and the threat of court action
• The role of a Cybersecurity Executive Dashboard and its ability to simplify risk and amplify informed decision making
• How to identify and bridge the gap between your Cybersecurity Compliance Rating and the threat of court action
Conceptual security architecture

This document provides an overview of conceptual security architecture using the SABSA framework. It describes key concepts like security architecture, enterprise frameworks, control objectives, multi-layered security strategies, security entity models, security domains, and security lifetimes and deadlines. The goal is to conceptualize security at a high level to address business risks and requirements through control objectives and a multi-layered approach using concepts like entities, domains, and relationships of trust.
Effective Security Operation Center - present by Reza Adineh

The document discusses how to effectively manage a cyber security operations center (SOC). It addresses questions about how to assess the effectiveness and maturity of a SOC, ensure sufficient threat detection capabilities through proper sensors and data collection, and utilize threat intelligence and data enrichment. The document also provides steps to implement threat management, incident response processes, and leverage machine learning and user entity behavior analytics to detect anomalous user behavior and insider threats.
Security Information and Event Management

This document provides an overview of security information and event management (SIEM) tools and related topics. It discusses getting started with Security Onion and Docker, then covers SIEM concepts like collecting events, creating incidents, and example tools like IBM QRadar and Splunk. It also summarizes related areas like user entity behavior analytics, security orchestration automation and response, threat intelligence attribution and distribution, and security analytics hunting techniques.
Vulnerability Management

Presentation I gave to a client on showing the importance of implementing a vulnerability management program life cycle.
Threat Modelling

This document discusses threat modeling for software applications. It covers the key stages of threat modeling including decomposing the application, determining and ranking threats using STRIDE, and determining countermeasures. Specific topics covered include threat modeling approaches, data flow diagrams, trust levels, the STRIDE framework for analyzing spoofing, tampering, repudiation, information disclosure, denial of service, and elevation of privilege threats. It also discusses mobile threat modeling and provides an example threat analysis of a student results portal application.
From SIEM to SOC: Crossing the Cybersecurity Chasm

You own a SIEM, but to be secure, you need a Security Operations Center! How do you cross the chasm? Do you hire staff or outsource? And what skills are needed? Mike Ostrowski, a cybersecurity industry veteran, will review common pitfalls experienced through the journey from SIEM to SOC, the pros and cons of an all in-house SOC vs. outsourcing, and the benefits of a hybrid SOC model.
Learning Objectives:
1: You own a SIEM, but to be secure, you need a SOC. How do you cross the chasm?
2: What are the pros and cons of in-house, fully managed and hybrid security?
3: What considerations go into deciding whether to employ a hybrid strategy?
(Source: RSA Conference USA 2018)
SOC and SIEM.pptx

SOC and SIEM systems can help organizations detect and respond to security incidents and threats in a timely manner. A SOC acts as a security operations center to monitor, analyze, and respond to cybersecurity incidents. SIEM provides real-time analysis of security alerts and events to help identify potential threats. Implementing SOC and SIEM solutions can improve an organization's security posture through early threat detection, compliance with regulations, and reduced breach impact.
ASPEN - NEXT GENERATION SIEM

We combine ASPEN with its SOC (Security Operations Centre) services to a solution that addresses the widest spectrum of internal and external threats organisations face today
ASPEN Brochure

With cyber-attacks on the rise, companies are transforming their approach to security monitoring from reactive towards intelligence-driven security. We can help you empower your security teams, and your business, to perform better in the digital world with a next-generation Security Information and Event Management (SIEM) platform and Security Operations Center (SOC)
More Related Content
What's hot
Security operations center-SOC Presentation-مرکز عملیات امنیت

Cyber Security Trends
Business Concerns
Cyber Threats
The Solutions
Security Operation Center
requirement
SOC Architecture model
SOC Implementation
SOC & NOC
SOC & CSIRT
SIEM & Correlation
-----------------------------------------------------------
Definition
Gartner defines a SOC as both a team, often operating in shifts around the clock, and a facility dedicated to and organized to prevent, detect, assess and respond to cybersecurity threats and incidents, and to fulfill and assess regulatory compliance. The term "cybersecurity operation center "is often used synonymously for SOC.
A network operations center (NOC) is not a SOC, which focuses on network device management rather than detecting and responding to cybersecurity incidents. Coordination between the two is common, however.
A managed security service is not the same as having a SOC — although a service provider may offer services from a SOC. A managed service is a shared resource and not solely dedicated to a single organization or entity. Similarly, there is no such thing as a managed SOC.
Most of the technologies, processes and best practices that are used in a SOC are not specific to a SOC. Incident response or vulnerability management remain the same, whether delivered from a SOC or not. It is a meta-topic, involving many security domains and disciplines, and depending on the services and functions that are delivered by the SOC.
Services that often reside in a SOC are:
• Cyber security incident response
• Malware analysis
• Forensic analysis
• Threat intelligence analysis
• Risk analytics and attack path modeling
• Countermeasure implementation
• Vulnerability assessment
• Vulnerability analysis
• Penetration testing
• Remediation prioritization and coordination
• Security intelligence collection and fusion
• Security architecture design
• Security consulting
• Security awareness training
• Security audit data collection and distribution
Alternative names for SOC :
Security defense center (SDC)
Security intelligence center
Cyber security center
Threat defense center
security intelligence and operations center (SIOC)
Infrastructure Protection Centre (IPC)
مرکز عملیات امنیت
Implementing Vulnerability Management 

Derek Milroy, IS Security Architect at U.S. Cellular Corporation, defined “vulnerability management” and how it affects today’s organizations during his presentation at the 2014 Chief Information Security Officer (CISO) Leadership Forum in Chicago on Nov. 19. In his presentation, “Enterprise Vulnerability Management/Security Incident Response,” Milroy noted vulnerability management has different meanings to different organizations, but an organization that utilizes vulnerability management processes can effectively safeguard its data.
According to Milroy, an organization should develop its own vulnerability management baselines to monitor its security levels. By doing so, Milroy said an organization can launch and control vulnerability management systems successfully. In addition, Milroy pointed out that vulnerability management problems occasionally will arise, but a well-prepared organization will be equipped to handle such issues: “Problems are going to happen … You have to work with your people. This can translate to any tool that you’re putting in place. Make sure your people have plans for what happens when it goes wrong, because it’s going to [happen] every single time.”
Milroy also noted that having actionable vulnerability management data is important for organizations of all sizes. If an organization evaluates its vulnerability management processes regularly, Milroy said, it can collect data and use this information to improve its security: “The simplest rule of thumb for vulnerability management, click the report, hand the report to someone. Don’t ever do that. There is no such thing as a report from a tool that you can just click and hand to someone until you first tune it and pare it down.”
- See more at: http://www.argylejournal.com/chief-information-security-officer/enterprise-vulnerability-managementsecurity-incident-response-derek-milroy-is-security-architect-u-s-cellular-corporation/#sthash.Buh6CzLS.dpuf
Security Operation Center Fundamental

The document provides an introduction and agenda for a 3-day security operations center fundamentals course. Day 1 will cover famous attacks and how to confront them, as well as an introduction to security operations centers. Day 2 will discuss the key features, modules, processes, and people involved in SOCs. Day 3 will focus on the technology used in SOCs, including network monitoring, investigation, and correlation tools. The instructor is introduced and the document provides an overview of common attacks such as eavesdropping, data modification, spoofing, password attacks, denial of service, man-in-the-middle, and application layer attacks.
Balbix-New-CISO-Board-Deck.pptx

The CISO is presenting to the board of directors to introduce cyber risk management at the company. The presentation covers three key areas: introducing cyber risk and the company's framework for managing it, the strategic roadmap and metrics for the information security function, and establishing information security as a board-level topic. The goal is to help the board understand cybersecurity risks, provide oversight of risk management, and introduce the CISO's vision and plans to improve the security posture.
Cyber Security Seminar.pptx

The document provides an overview of cyber security as a career option. It discusses how cyber security protects internet-connected systems from cyber threats. It outlines the growing global market size for cyber security and increasing demand for cyber security specialists. Key skills needed for the field include technical degrees, security testing experience, and problem solving abilities. Popular job titles include cyber security analyst, engineer, and chief information security officer, with salaries ranging from $80,000 to $230,000. Top certifications include CISSP, CISA, and security-related certifications from EC Council.
SOC Cyber Security

Find out the SOC Cyber Security at Steppa. Our SOC contains several capabilities like process and break down any PC translated information, assess and distinguish suspicious and maicious web and system activities, visualize and monitor all threats in real time.
Building Security Operation Center

The document discusses building a security operations center (SOC) and provides information on why an organization would build a SOC, how to establish the necessary skills and processes, and technology solutions like HP ArcSight that can be used. It describes how HP consultants have experience building SOCs for major companies and can help customers establish an effective SOC to monitor for security events, ensure compliance, and protect the organization. It provides details on how to structure a SOC, including defining roles and processes, implementing a security information and event management (SIEM) system, and establishing performance metrics to improve over time.
Cyber Resilience – Strengthening Cybersecurity Posture & Preparedness by Phil...

World Continuity Congress conference on 7th October 2015 at Pullman Putrajaya Lakeside by BCM Institute
Building a Cyber Security Operations Center for SCADA/ICS Environments

Abstract: Modern day cyber threats are ever increasing in sophistication and evasiveness against Process Control Networks. Organizations in the industry are facing a constant challenge to adopt modern techniques to proactively monitor the security posture within the SCADA infrastructure whilst keeping cyber attackers and threat actors at bay.
In this presentation we will cover the fundamental building blocks of building a SCADA cyber security operations center with key responsibilities such as Incident Response Management, Vulnerability and Patch Management, Secure-by-design Architecture, Security Logging and Monitoring and how such security domains drive accountability and act as a line of authority across the PCN.
Cyber Security Operations Center (C-SOC) 

The document discusses the benefits of exercise for mental health. Regular physical activity can help reduce anxiety and depression and improve mood and cognitive functioning. Exercise causes chemical changes in the brain that may help protect against mental illness and improve symptoms.
Guide to Risk Management Framework (RMF)

Navigating the complex Risk Management Framework (RMF) requirements can be daunting. Learn best practices and gain a better understanding of NIST's RMF.
Cybersecurity Roadmap Development for Executives

Secrets to managing your Duty of Care in an ever- changing world.
How well do you know your risks?
Are you keeping up with your responsibilities to provide Duty of Care?
How well are you prioritising Cybersecurity initiatives?
Liability for Cybersecurity attacks sits with Executives and Board members who may not have the right level of technical security knowledge. This session will outline what practical steps executives can take to implement a Cybersecurity Roadmap that is aligned with its strategic objectives.
Led by Krist Davood, who has spent over 28 years implementing secure mission critical systems for executives. Krist is an expert in protecting the interconnectedness of technology, intellectual property and information systems, as evidenced through his roles at The Good Guys, Court Services Victoria and Schiavello.
The seminar will cover:
• Fiduciary responsibility
• How to efficiently deal with personal liability and the threat of court action
• The role of a Cybersecurity Executive Dashboard and its ability to simplify risk and amplify informed decision making
• How to identify and bridge the gap between your Cybersecurity Compliance Rating and the threat of court action
Conceptual security architecture

This document provides an overview of conceptual security architecture using the SABSA framework. It describes key concepts like security architecture, enterprise frameworks, control objectives, multi-layered security strategies, security entity models, security domains, and security lifetimes and deadlines. The goal is to conceptualize security at a high level to address business risks and requirements through control objectives and a multi-layered approach using concepts like entities, domains, and relationships of trust.
Effective Security Operation Center - present by Reza Adineh

The document discusses how to effectively manage a cyber security operations center (SOC). It addresses questions about how to assess the effectiveness and maturity of a SOC, ensure sufficient threat detection capabilities through proper sensors and data collection, and utilize threat intelligence and data enrichment. The document also provides steps to implement threat management, incident response processes, and leverage machine learning and user entity behavior analytics to detect anomalous user behavior and insider threats.
Security Information and Event Management

This document provides an overview of security information and event management (SIEM) tools and related topics. It discusses getting started with Security Onion and Docker, then covers SIEM concepts like collecting events, creating incidents, and example tools like IBM QRadar and Splunk. It also summarizes related areas like user entity behavior analytics, security orchestration automation and response, threat intelligence attribution and distribution, and security analytics hunting techniques.
Vulnerability Management

Presentation I gave to a client on showing the importance of implementing a vulnerability management program life cycle.
Threat Modelling

This document discusses threat modeling for software applications. It covers the key stages of threat modeling including decomposing the application, determining and ranking threats using STRIDE, and determining countermeasures. Specific topics covered include threat modeling approaches, data flow diagrams, trust levels, the STRIDE framework for analyzing spoofing, tampering, repudiation, information disclosure, denial of service, and elevation of privilege threats. It also discusses mobile threat modeling and provides an example threat analysis of a student results portal application.
From SIEM to SOC: Crossing the Cybersecurity Chasm

You own a SIEM, but to be secure, you need a Security Operations Center! How do you cross the chasm? Do you hire staff or outsource? And what skills are needed? Mike Ostrowski, a cybersecurity industry veteran, will review common pitfalls experienced through the journey from SIEM to SOC, the pros and cons of an all in-house SOC vs. outsourcing, and the benefits of a hybrid SOC model.
Learning Objectives:
1: You own a SIEM, but to be secure, you need a SOC. How do you cross the chasm?
2: What are the pros and cons of in-house, fully managed and hybrid security?
3: What considerations go into deciding whether to employ a hybrid strategy?
(Source: RSA Conference USA 2018)
SOC and SIEM.pptx

SOC and SIEM systems can help organizations detect and respond to security incidents and threats in a timely manner. A SOC acts as a security operations center to monitor, analyze, and respond to cybersecurity incidents. SIEM provides real-time analysis of security alerts and events to help identify potential threats. Implementing SOC and SIEM solutions can improve an organization's security posture through early threat detection, compliance with regulations, and reduced breach impact.
What's hot (20)
Security operations center-SOC Presentation-مرکز عملیات امنیت

Security operations center-SOC Presentation-مرکز عملیات امنیت
Cyber Resilience – Strengthening Cybersecurity Posture & Preparedness by Phil...

Cyber Resilience – Strengthening Cybersecurity Posture & Preparedness by Phil...
Building a Cyber Security Operations Center for SCADA/ICS Environments

Building a Cyber Security Operations Center for SCADA/ICS Environments
Effective Security Operation Center - present by Reza Adineh

Effective Security Operation Center - present by Reza Adineh
From SIEM to SOC: Crossing the Cybersecurity Chasm

From SIEM to SOC: Crossing the Cybersecurity Chasm
Similar to Security operation center.pdf
ASPEN - NEXT GENERATION SIEM

We combine ASPEN with its SOC (Security Operations Centre) services to a solution that addresses the widest spectrum of internal and external threats organisations face today
ASPEN Brochure

With cyber-attacks on the rise, companies are transforming their approach to security monitoring from reactive towards intelligence-driven security. We can help you empower your security teams, and your business, to perform better in the digital world with a next-generation Security Information and Event Management (SIEM) platform and Security Operations Center (SOC)
Infosec cert service

SK Infosec is a South Korean security services provider with over 860 employees. It offers security consulting, system integration, monitoring and management services. In recent years, its annual revenue and growth have increased substantially, with total revenue reaching nearly $101 million in 2012 and growth of 14.7% that year. SK Infosec provides a full range of managed security services including prevention, management, monitoring and incident handling for its customers in Korea.
Security Operation Centre Console.docx

Security Operation Centre Consoles" are specialized workstations designed for monitoring and managing security operations. These consoles typically feature multiple screens, integrated communication systems, and ergonomic design to facilitate real-time surveillance, threat detection, and rapid response. They serve as the central hub for security personnel to coordinate efforts, analyze data, and ensure the safety and security of an organization's assets and personnel
SanerNow platform-datasheet

Many Products, No Security
So many products: Organizations invest in multiple products, many with overlapping
capabilities. And investments are huge when considering the cost of products,maintenance, professional services, training and vendor management.
Security is our duty and we shall deliver it - White Paper

Quality Management, Information Security, Threat Hunting and Mitigation Plans for a Software Company or a Technology Start-up engaged in building, deploying or consulting in Software and Internet Applications.
braincavesoft-com-cyber-security.pdf

At BrainCave Software, we understand the critical importance of safeguarding your digital assets against cyber threats.
braincavesoft-com-cyber-security (1).pdf

The document summarizes the cyber security services offered by BrainCave Software. It discusses how their team of experts utilizes advanced tools and technologies to provide comprehensive cyber security solutions tailored to clients' needs, including vulnerability assessments, network security, encryption, employee training, and incident response. It also provides testimonials from satisfied clients who have strengthened their data security and reduced security breaches through BrainCave's proactive cyber security approach.
Leo TechnoSoft’s Intelligence Driven SOC is integrated Context-aware Security...

Leo TechnoSoft provides an intelligence driven security operation center (SOC) that uses adaptive security frameworks to predict, prevent, detect, and respond to threats across an organization's IT stack. The SOC integrates security incident and event management, identity and access management, privilege identity management, and cloud access security broker solutions built on security big data. It can correlate device events, identity, access, and context to predict advanced risks. The SOC delivers continuous network monitoring with visibility into user behavior, threats, risks, and compliance.
Splunk EMEA Webinar: Scoping infections and disrupting breaches

This document discusses best practices for scoping infections and disrupting breaches. It outlines the necessary data sources like network endpoint, access/identity, and threat intelligence data. It describes capabilities for monitoring, alerting, investigating incidents, and detecting threats. The document demonstrates investigating a breach example using the attack kill chain. It recommends establishing a security intelligence platform to connect and analyze security-related data from multiple sources. Lastly, it promotes the upcoming Splunk conference and training opportunities.
5 BEST PRACTICES FOR A SECURITY OPERATION CENTER (SOC)

Security Management is very complex and does not limit itself to products and technologies. It is important to consider alternatives when setting up a Security Operation Center (SOC), from insight into the business plan requirements, ability and the skill set of people who will handle the SOC, the responsibilities for the team, budget and more.
Dhishant -Latest Resume

This document is a resume for Dhishant Abrol summarizing his professional experience and qualifications. He has over 6 years of experience in information and network security, currently working as a Security Researcher. Previous roles include managing security operations centers and security architectures for clients. He has various technical certifications and skills in areas like vulnerability assessment, malware analysis, compliance, and security tools.
Threat Intelligence Making your Bespoke Security Operations Centre Work for Y...

We have a wide range of IT desktop solutions and print services for any business across the UK.
Not only do we offer high-quality services across IT Services we offer business broadband solutions, telecommunications and much, much more.
inSOC Sales Deck Dec 2020.pdf

In response to this challenge, inSOC has
developed a layered security solution
comprised of enterprise grade tool sets,
framework-driven onboarding and escalation
processes and a team of highly qualified
security professionals that have eyes on glass
24/7/365.
All inclusive pricing structures
Mix and match offerings
Flexible contract lengths
Sales enablement
Minimal operational overhead
MSSP Accelerator self paced training
Advanced cybersecurity certification leading
to SSAE 19 certification
MSSP Accelerator
program is designed to
fast track the MSP's
security practice and
unlock the potential
revenue streams available
by delivering enterprisegrade security services, via
a self-paced online course
and sales enablement.
The Accelerator program
can then lead to SSAE-19
certification underlining
your value and enabling you
to establish yourself as a
leader in the field. SSAE 19
is a consultancy led
certification program, taking
a minimum 12 months to
complete.
We provide an
advanced onboarding
to harden
environments to a set
standard
Our wraparound SOC
team is lead by highly
qualified security
professionals including
CISSPs and CCIEs, to
ensure best-in-class
delivery 24/7/365
And we base
everything on the NIST
Cybersecurity
Framework
inSOC’s tools and processes are centred
around the NIST 800 Cybersecurity
framework and the Centre for Internet
Security’s Top 20 Critical Security Controls.
The implementation of this known and
trusted security framework significantly
reduces the risk of breach in the first place,
minimising alert noise and pinpointing true
threats proactively and reactivel
Benchmarks
• Base on established security frameworks
• We recommend the Center for Internet Security
• Windows OS benchmark is 1200+ pages
• Subscription to CIS for preconfigured GPO scripts
Playbooks
• Create benchmark playbooks to manage hardening tasks consistently
• Base playbooks on established security frameworks and benchmarks
• Capture audit ready evidence and attach to playbook
• Manage tasks and dependent projects
Change Control
• Manage any hardening initiative with a standard change control methodology
• Beta testing, user acceptance testing, release
LIFT OFF 2017: Transforming Security

This document discusses how Splunk is transforming security through their security platform and solutions. It provides an overview of Splunk's security analytics, awareness and response capabilities including machine learning, risk scoring, threat intelligence and more. It also outlines Splunk's security framework and how their solutions integrate with various security data sources and tools to provide end-to-end security visibility across on-premise, cloud, and hybrid environments.
Top Cyber Threat Intelligence Tools in 2021.pdf

Cyber threat intelligence is used for collecting necessary information about new and old threat actors from various sources. The collected data is analyzed, processed, and converted into useful threat intelligence.
https://www.infosectrain.com/courses/certified-threat-intelligence-analyst-ctia-certification-training/
Splunk for Security Breakout Session

The document discusses security session presented by Philipp Drieger. It begins with a safe harbor statement noting any forward-looking statements are based on current expectations and could differ from actual results. The agenda includes discussing Splunk for security, enterprise security, and Splunk user behavior analytics. It provides examples of how Splunk can be used to detect threats like fraud and advanced persistent threats by analyzing machine data from various sources. It also discusses how threat intelligence can be incorporated using STIX/TAXII standards and open IOCs. Customer examples show how Nasdaq and Cisco have replaced their SIEMs with Splunk to gain better scalability and flexibility.
BISS - 11nov2011

The document discusses the 10 year anniversary of BISS, an IT security company in Romania. It provides an overview of BISS's services and expertise in areas like firewalls, encryption, vulnerability management and compliance. It also discusses the growing need for security due to factors like increasing network complexity, rapidly changing technologies, and a large number of unpatched vulnerabilities. Common security threats include attacks on websites, employee devices, and databases. The document promotes BISS's integrated security solutions and intelligence-driven approach to help customers address security challenges.
SOC 3.0: strategic threat intelligence May 2016

The document discusses moving security operations from a traditional reactive model to a proactive model called SOC 3.0. SOC 3.0 leverages vast amounts of data from both internal and external sources, including social media, dark web monitoring, business intelligence, and technical data. By analyzing patterns in this diverse data, SOC 3.0 aims to provide strategic threat intelligence rather than just responding to incidents. The key is gaining a fundamental understanding of the business to interpret technical data within the proper context. Outsourcing SOC services can help organizations gain the benefits of this approach without the cost and challenges of building extensive in-house security operations capabilities.
Seceon's aiXDR_ Automating Cybersecurity Threat Detection in 2023 - Seceon.pptx

Seceon aiXDR solution is built upon its Open Threat Management (OTM) Platform enabling organizations to detect both signature-based malware with precedence and zero-day threats without precedence, quickly and effectively, thereby thwarting the kill chain and minimizing the extent of damage across business and enterprise environments.
Similar to Security operation center.pdf (20)
Security is our duty and we shall deliver it - White Paper

Security is our duty and we shall deliver it - White Paper
Leo TechnoSoft’s Intelligence Driven SOC is integrated Context-aware Security...

Leo TechnoSoft’s Intelligence Driven SOC is integrated Context-aware Security...
Splunk EMEA Webinar: Scoping infections and disrupting breaches

Splunk EMEA Webinar: Scoping infections and disrupting breaches
5 BEST PRACTICES FOR A SECURITY OPERATION CENTER (SOC)

5 BEST PRACTICES FOR A SECURITY OPERATION CENTER (SOC)
Threat Intelligence Making your Bespoke Security Operations Centre Work for Y...

Threat Intelligence Making your Bespoke Security Operations Centre Work for Y...
Seceon's aiXDR_ Automating Cybersecurity Threat Detection in 2023 - Seceon.pptx

Seceon's aiXDR_ Automating Cybersecurity Threat Detection in 2023 - Seceon.pptx
More from Skillmine Technology Consulting
SAP Managed Services Best Practices and Implementation Strategies

SAP, an acronym for Systems, Applications, and Products in
Data Processing, holds a prominent position as a worldwide
frontrunner in enterprise software solutions.
Microservices and Enterprise App Development

A Gartner survey says that by the end of 2023, over 80% of all enterprise software will be built using a microsevices architecture. The State of Microservices Maturity Report found that 61% of respondents experienced improved application resilience after transitioning tomicroservices
Microservices and Enterprise App Development.pdf

A Gartner survey says that by the end of 2023, over 80% of all enterprise software will be built using a microsevices architecture. The State of Microservices Maturity Report found that 61% of respondents experienced improved application resilience after transitioning tomicroservices
Cybersecurity in the Age of IoT - Skillmine

Cybersecurity stands as the bedrock of our digital world, safeguarding systems, networks, and data from a rising tide of cyber threats. In the era of the Internet of Things (IoT), wherean ever-expanding array of devices and objects are seamlessly interconnected, the importance of cybersecurity has escalated to unprecedented levels.
Unlocking Opportunities on the Cloud Through Container Technology.pdf

Unlocking Opportunities on the Cloud Through Container Technology.pdfSkillmine Technology Consulting
An age of outstanding application development has begun due to
the cloud, which has altered the IT industry's format and market
structure. Businesses can concentrate more on creating more commercially viable solutions that fulfil their mission using cloud and
container technologies are the greatest option for enhancing cloud
service capabilities.5 Reasons Why Datafication is The Future of Businesss

Data has enormous power in the present day. As a primary asset of organizations, it is revolutionizing various sectors. Simply put, data is the information stored in or utilised by a computer, smartphone, or other electronic devices. The process of "Datafication," which includes the identification of data, is seen by businesses and analysts worldwide as the way of the future of commerce
Measure To Avoid Cyber Attacks

The document discusses various measures that companies can take to avoid cyber attacks. It recommends that companies train employees on cybersecurity awareness, keep systems fully updated to patch vulnerabilities, implement zero trust and SSL inspection for security, examine permissions of frequently used apps, create mobile device management plans, use passwordless authentication and behavior monitoring, regularly audit networks to detect threats, develop strong data governance, automate security practices, and have an incident response plan in place. Taking a proactive approach to cybersecurity through multiple defensive strategies is crucial for businesses of all sizes to protect against increasing cyber attacks.
Skillmine - Corporate Profile v2 2023.pdf

We are a new-generation IT Software Company, helping our customers to optimize their IT investments, while preparing them for the best-in-class operating model, for delivering that “competitive edge” in their marketplace. Agility is our strength and customer focus is our guiding principle. We engage with customers to unearth bottlenecks in the current IT operating ecosystem - our consulting practice enables the optimum use of current IT assets, tools, people and practices.
Information Security Statutory Compliance

Skillmine began its journey 10 years ago with a purpose! What began as an effort to close the delivery gap has made us a name to reckon with in IT Consulting and Managed Services. As a team of highly competent individuals, we have the agility to cater to unique needs and the power to provide scalability to enterprises.
Network Operation Center

Consistency is what keeps us ahead. Efficient management of your Network Operations Center Services (NOC) is maintained through consistent processes to monitor all events and incidents. Speedy recording, reporting and resolution of each such event or incident are also ensured. Regular service monitoring and surveillance procedures are conducted to ensure efficiency.
Skillmine-InfoSecurity-VAPT-V.2.

It will provide strategies and guidance for the recovery of
the underlying infrastructure, including the data centres,
servers, data storage and network links and Infrastructure
applications. The IT DRP will serve as a ‘master plan run book’
encompassing the key services and components of the IT
environment at the Organization.
BUSINESS CONTINUITY MANAGEMENT

It will provide strategies and guidance for the recovery of
the underlying infrastructure, including the data centres,
servers, data storage and network links and Infrastructure
applications. The IT DRP will serve as a ‘master plan run book’
encompassing the key services and components of the IT
environment at the Organization.
IT Infrastrucure Technology Transformation

Skillmine has deep expertise & experience in IT Infrastructure, Data Center, and Cloud transformation with proven track record enabled by industry best practices & innovations across technologies.
MANAGED IT SERVICES

Managed Services are part of an end-to-end approach at Skillmine. We are business technologists and our business divisions all work openly and collaboratively together in the pursuit of a single goal - ”To power progress for our Customers”. This collaboration is the foundation of our ability to design, build and operate business solutions and IT infrastructure.
A Guide To IT Compliance Assessment And Management

Another survey conducted in 2021 by the International Association of Privacy Professionals (IAPP) found that compliance with data protection laws such as GDPR and CCPA is the top privacy-related concern for organizations.
Skillmine CISO as service

This document describes Skillmine's CISO as-a-Service offering which provides information security services to help organizations comply with regulations and improve their security posture. The services include assessing an organization's security maturity and risks, implementing mitigation strategies and tools, monitoring the security program, and conducting audits. Skillmine's team of experienced security consultants help clients develop security strategies, integrate solutions, protect assets, and refine security programs on an ongoing basis.
Skillmine IT Service Management

Skillmine began its journey 10 years ago with a purpose! What began as an effort to close the delivery gap has made us a name to reckon with in IT Consulting and Managed Services. As a team of highly competent individuals, we have the agility to cater to unique needs and the power to provide scalability to enterprises.
IT CLOUD SECURITY

Cloud security protects data stored in cloud computing environments from theft, deletion, and leakage. It involves methods like access control, firewalls, penetration testing, virtual private networks, and not using public internet connections. Cloud security responsibilities are shared between cloud providers and customers depending on the type of cloud service - infrastructure as a service involves the highest level of customer responsibility for security.
IT INFRASTRUCTURE SERVICES

Skillmine Infrastructure Services o
ering comprises a comprehensive portfolio of services that maps across
all aspects of IT infrastructure advisory, design, implementation and ongoing management, to serve as true
end–to–end capability partner entirely focused on business outcomes. The result is an infrastruc– ture
solution that is e
cient, scalable and secure, that strikes a balance between flexibility and cost, while
facilitating innovation and future business planning.
Enterprise Application Development

Modern technologies are paving the way for companies and agencies to develop at a very fast pace. For companies, enterprise app development is bringing in comprehensive capabilities such as automation, machine learning, and artificial intelligence. A tailored application software allows a company to manage several aspects of the business, including enterprise administration and sta
cooperation.
More from Skillmine Technology Consulting (20)
SAP Managed Services Best Practices and Implementation Strategies

SAP Managed Services Best Practices and Implementation Strategies
Unlocking Opportunities on the Cloud Through Container Technology.pdf

Unlocking Opportunities on the Cloud Through Container Technology.pdf
5 Reasons Why Datafication is The Future of Businesss

5 Reasons Why Datafication is The Future of Businesss
A Guide To IT Compliance Assessment And Management

A Guide To IT Compliance Assessment And Management
Recently uploaded
Ellen Burstyn: From Detroit Dreamer to Hollywood Legend | CIO Women Magazine

In this article, we will dive into the extraordinary life of Ellen Burstyn, where the curtains rise on a story that's far more attractive than any script.
欧洲杯赌球-欧洲杯赌球买球官方官网-欧洲杯赌球比赛投注官网|【网址🎉ac55.net🎉】

【网址🎉ac55.net🎉】欧洲杯赌球是世界上历史最悠久的博彩公司之一。其历史可以追溯到十九世纪末,确切时间是1886年。这家英国公司拥有超过15000名员工,是博彩行业规模最大的公司。欧洲杯赌球是英国最受欢迎的实体博彩公司之一,其排名仅次于欧洲杯赌球,旗下2800家投注站遍布全英国。
Satta Matka Dpboss Kalyan Matka Results Kalyan Chart

SATTA MATKA DPBOSS KALYAN MATKA RESULTS KALYAN MATKA MATKA RESULT KALYAN MATKA TIPS SATTA MATKA MATKA COM MATKA PANA JODI TODAY BATTA SATKA MATKA PATTI JODI NUMBER MATKA RESULTS MATKA CHART MATKA JODI SATTA COM INDIA SATTA MATKA MATKA TIPS MATKA WAPKA ALL MATKA RESULT LIVE ONLINE MATKA RESULT KALYAN MATKA RESULT DPBOSS MATKA 143 MAIN MATKA KALYAN MATKA RESULTS KALYAN CHART KALYAN CHART
Satta Matka Dpboss Kalyan Matka Results Kalyan Chart

SATTA MATKA DPBOSS KALYAN MATKA RESULTS KALYAN CHART KALYAN MATKA MATKA RESULT KALYAN MATKA TIPS SATTA MATKA MATKA COM MATKA PANA JODI TODAY BATTA SATKA MATKA PATTI JODI NUMBER MATKA RESULTS MATKA CHART MATKA JODI SATTA COM INDIA SATTA MATKA MATKA TIPS MATKA WAPKA ALL MATKA RESULT LIVE ONLINE MATKA RESULT KALYAN MATKA RESULT DPBOSS MATKA 143 MAIN MATKA KALYAN MATKA RESULTS KALYAN CHART
Satta Matka Dpboss Kalyan Matka Results Kalyan Chart

SATTA MATKA DPBOSS KALYAN MATKA RESULTS KALYAN CHART KALYAN MATKA MATKA RESULT KALYAN MATKA TIPS SATTA MATKA MATKA COM MATKA PANA JODI TODAY BATTA SATKA MATKA PATTI JODI NUMBER MATKA RESULTS MATKA CHART MATKA JODI SATTA COM INDIA SATTA MATKA MATKA TIPS MATKA WAPKA ALL MATKA RESULT LIVE ONLINE MATKA RESULT KALYAN MATKA RESULT DPBOSS MATKA 143 MAIN MATKA KALYAN MATKA RESULTS KALYAN CHART
1Q24_HYUNDAI CAPITAL SERVICES INC. AND SUBSIDIARIES

1Q24_HYUNDAI CAPITAL SERVICES INC. AND SUBSIDIARIES
The Steadfast and Reliable Bull: Taurus Zodiac Sign

Explore the steadfast and reliable nature of the Taurus Zodiac Sign. Discover the personality traits, key dates, and horoscope insights that define the determined and practical Taurus, and learn how their grounded nature makes them the anchor of the zodiac.
AI Transformation Playbook: Thinking AI-First for Your Business

I dive into how businesses can stay competitive by integrating AI into their core processes. From identifying the right approach to building collaborative teams and recognizing common pitfalls, this guide has got you covered. AI transformation is a journey, and this playbook is here to help you navigate it successfully.
Satta Matka Dpboss Kalyan Matka Results Kalyan Chart

SATTA MATKA DPBOSS KALYAN MATKA RESULTS KALYAN CHART KALYAN MATKA MATKA RESULT KALYAN MATKA TIPS SATTA MATKA MATKA COM MATKA PANA JODI TODAY BATTA SATKA MATKA PATTI JODI NUMBER MATKA RESULTS MATKA CHART MATKA JODI SATTA COM INDIA SATTA MATKA MATKA TIPS MATKA WAPKA ALL MATKA RESULT LIVE ONLINE MATKA RESULT KALYAN MATKA RESULT DPBOSS MATKA 143 MAIN MATKA KALYAN MATKA RESULTS KALYAN CHART
PM Surya Ghar Muft Bijli Yojana: Online Application, Eligibility, Subsidies &...

PM Surya Ghar Muft Bijli Yojana: Online Application, Eligibility, Subsidies &...Ksquare Energy Pvt. Ltd.
During the budget session of 2024-25, the finance minister, Nirmala Sitharaman, introduced the “solar Rooftop scheme,” also known as “PM Surya Ghar Muft Bijli Yojana.” It is a subsidy offered to those who wish to put up solar panels in their homes using domestic power systems. Additionally, adopting photovoltaic technology at home allows you to lower your monthly electricity expenses. Today in this blog we will talk all about what is the PM Surya Ghar Muft Bijli Yojana. How does it work? Who is eligible for this yojana and all the other things related to this scheme?1 Circular 003_2023 ISO 27001_2022 Transition Arrangments v3.pdf

1 Circular 003_2023 ISO 27001_2022 Transition Arrangments v3.pdf
DearbornMusic-KatherineJasperFullSailUni

My powerpoint presentation for my Music Retail and Distribution class at Full Sail University
Discover the Beauty and Functionality of The Expert Remodeling Service

Unlock your kitchen's true potential with expert remodeling services from O'Brien Group Inc. Transform your space into a functional, modern, and luxurious haven with their experienced professionals. From layout reconfiguration to high-end upgrades, they deliver stunning results tailored to your style and needs. Visit obriengroupinc.com to elevate your kitchen's beauty and functionality today.
Satta Matka Dpboss Kalyan Matka Results Kalyan Chart

SATTA MATKA DPBOSS KALYAN MATKA RESULTS KALYAN CHART KALYAN MATKA MATKA RESULT KALYAN MATKA TIPS SATTA MATKA MATKA COM MATKA PANA JODI TODAY BATTA SATKA MATKA PATTI JODI NUMBER MATKA RESULTS MATKA CHART MATKA JODI SATTA COM INDIA SATTA MATKA MATKA TIPS MATKA WAPKA ALL MATKA RESULT LIVE ONLINE MATKA RESULT KALYAN MATKA RESULT DPBOSS MATKA 143 MAIN MATKA KALYAN MATKA RESULTS KALYAN CHART
Satta Matka Dpboss Kalyan Matka Results Kalyan Chart

SATTA MATKA DPBOSS KALYAN MATKA RESULTS KALYAN CHART KALYAN MATKA MATKA RESULT KALYAN MATKA TIPS SATTA MATKA MATKA COM MATKA PANA JODI TODAY BATTA SATKA MATKA PATTI JODI NUMBER MATKA RESULTS MATKA CHART MATKA JODI SATTA COM INDIA SATTA MATKA MATKA TIPS MATKA WAPKA ALL MATKA RESULT LIVE ONLINE MATKA RESULT KALYAN MATKA RESULT DPBOSS MATKA 143 MAIN MATKA KALYAN MATKA RESULTS KALYAN CHART
Kirill Klip GEM Royalty TNR Gold Lithium Presentation

Lithium Will Power Us For The Next 50 Years And Then Robots: Kirill Klip GEM Royalty TNR Gold Lithium Presentation
Kalyan Chart Satta Matka Dpboss Kalyan Matka Results

KALYAN CHART SATTA MATKA DPBOSS KALYAN MATKA RESULTS KALYAN MATKA MATKA RESULT KALYAN MATKA TIPS SATTA MATKA MATKA COM MATKA PANA JODI TODAY BATTA SATKA MATKA PATTI JODI NUMBER MATKA RESULTS MATKA CHART MATKA JODI SATTA COM INDIA SATTA MATKA MATKA TIPS MATKA WAPKA ALL MATKA RESULT LIVE ONLINE MATKA RESULT KALYAN MATKA RESULT DPBOSS MATKA 143 MAIN MATKA KALYAN MATKA RESULTS KALYAN CHART
Recently uploaded (20)
Ellen Burstyn: From Detroit Dreamer to Hollywood Legend | CIO Women Magazine

Ellen Burstyn: From Detroit Dreamer to Hollywood Legend | CIO Women Magazine
Satta Matka Dpboss Kalyan Matka Results Kalyan Chart

Satta Matka Dpboss Kalyan Matka Results Kalyan Chart
Satta Matka Dpboss Kalyan Matka Results Kalyan Chart

Satta Matka Dpboss Kalyan Matka Results Kalyan Chart
Satta Matka Dpboss Kalyan Matka Results Kalyan Chart

Satta Matka Dpboss Kalyan Matka Results Kalyan Chart
1Q24_HYUNDAI CAPITAL SERVICES INC. AND SUBSIDIARIES

1Q24_HYUNDAI CAPITAL SERVICES INC. AND SUBSIDIARIES
The Steadfast and Reliable Bull: Taurus Zodiac Sign

The Steadfast and Reliable Bull: Taurus Zodiac Sign
Registered-Establishment-List-in-Uttarakhand-pdf.pdf

Registered-Establishment-List-in-Uttarakhand-pdf.pdf
AI Transformation Playbook: Thinking AI-First for Your Business

AI Transformation Playbook: Thinking AI-First for Your Business
Satta Matka Dpboss Kalyan Matka Results Kalyan Chart

Satta Matka Dpboss Kalyan Matka Results Kalyan Chart
PM Surya Ghar Muft Bijli Yojana: Online Application, Eligibility, Subsidies &...

PM Surya Ghar Muft Bijli Yojana: Online Application, Eligibility, Subsidies &...
1 Circular 003_2023 ISO 27001_2022 Transition Arrangments v3.pdf

1 Circular 003_2023 ISO 27001_2022 Transition Arrangments v3.pdf
Discover the Beauty and Functionality of The Expert Remodeling Service

Discover the Beauty and Functionality of The Expert Remodeling Service
Satta Matka Dpboss Kalyan Matka Results Kalyan Chart

Satta Matka Dpboss Kalyan Matka Results Kalyan Chart
Satta Matka Dpboss Kalyan Matka Results Kalyan Chart

Satta Matka Dpboss Kalyan Matka Results Kalyan Chart
Kirill Klip GEM Royalty TNR Gold Lithium Presentation

Kirill Klip GEM Royalty TNR Gold Lithium Presentation
Kalyan Chart Satta Matka Dpboss Kalyan Matka Results

Kalyan Chart Satta Matka Dpboss Kalyan Matka Results
Security operation center.pdf
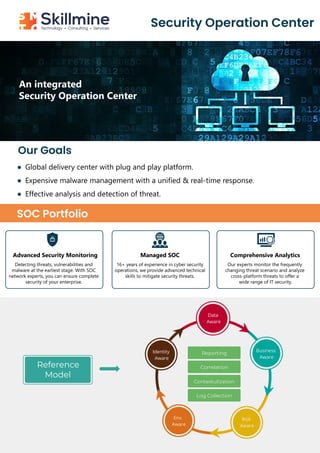
- 1. Security Operation Center An integrated Security Operation Center Our Goals SOC Portfolio Global delivery center with plug and play platform. Expensive malware management with a unified & real-time response. Effective analysis and detection of threat. Advanced Security Monitoring Managed SOC Comprehensive Analytics Detecting threats, vulnerabilities and malware at the earliest stage. With SOC network experts, you can ensure complete security of your enterprise. 16+ years of experience in cyber security operations, we provide advanced technical skills to mitigate security threats. Our experts monitor the frequently changing threat scenario and analyze cross-platform threats to offer a wide range of IT security. Data Aware Business Aware Risk Aware Env. Aware Identity Aware Reporting Correlation Contextulization Log Collection Reference Model
- 2. For more information: For more information: info@skill-mine.com For commercial information: orders@skill-mine.com www.skill-mine.com Technology Consulting Services Skillmine (Design & Implement) (Run the SOC for a defined Period) (Transition Processes & People) Build Operate Transfer 01 02 03 Detect Prevent Control Product Event Monitoring Event Analysis Event Processing Event Reporting Overall Site Analysis Process 3 Layer Structure Underpinning Knowledge Base Shift Rotation Lean and Efficient People Skillmine’s Approach Guidance & Planning Define objectives and requirements that will govern the design and use of SIEM. Infrastructure Define, Design and implement servers, software, log collectors etc comprising the SIEM system architecture. Implementation Design. Integrate and implement components needed to generate alerts and visibility. Operations & Support Define and manage processes needed to ensure ongoing support, management and tuning of SIEM. Incident Response Build, test, and respond to contain and eradicate the threat. Metrics & Reporting Establish measurement, reporting and communication capabilities to demonstrate changing state on Security. Enhance Continuously Improve & Enhance the solution capabilities based on new requirements and gain operational effciencies. 01 02 03 04 05 06 07
