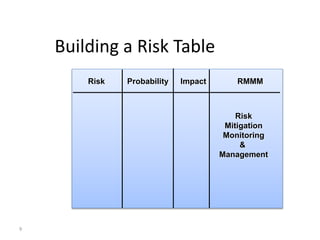
This document discusses risk management in project management. It explains that risk identification, probability assessment, and impact estimation are important activities for risk analysis. Risks can be proactively or reactively managed. Proactive management involves formal risk analysis and addressing root causes, while reactive management involves responding to risks as they occur. Key aspects of risk management include identifying risks, analyzing their probability and impact, developing a risk table to plan mitigation strategies, and continuously monitoring and managing risks throughout the project lifecycle.










![13
Risk Exposure (Impact)
The overall risk exposure, RE, is determined using the
following relationship [Hal98]:
RE = P x C
where
P is the probability of occurrence for a risk, and
C is the cost to the project if the risk occur (i.e loss).](https://image.slidesharecdn.com/risk-management-05012023-025512pm-230109110300-dff7f5b5/85/Risk-Management-05012023-025512pm-ppt-13-320.jpg)


