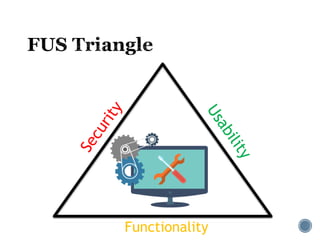
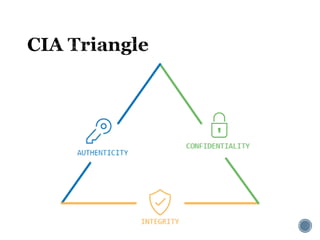
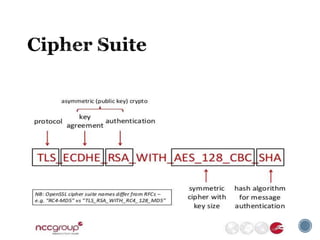
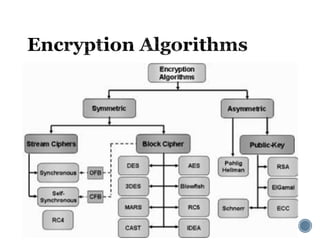
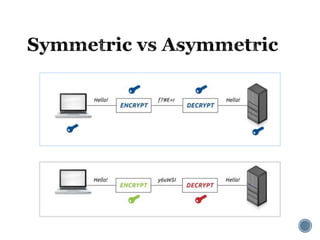
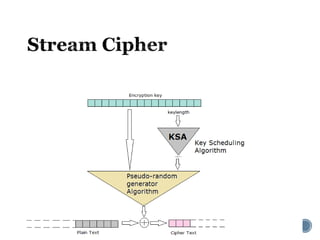
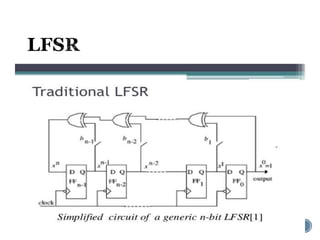
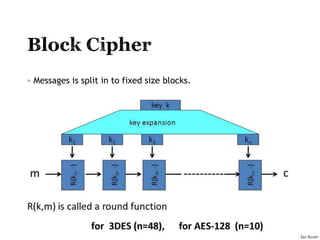
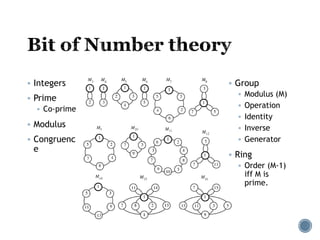
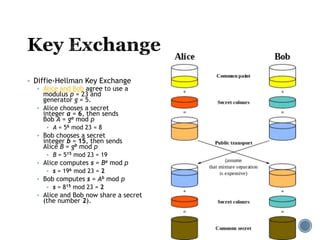
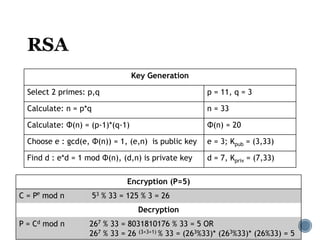
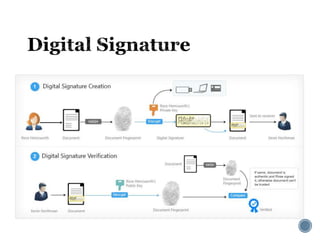
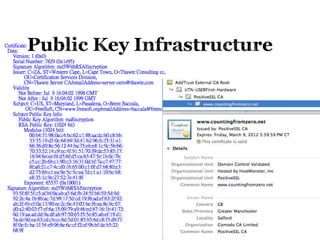
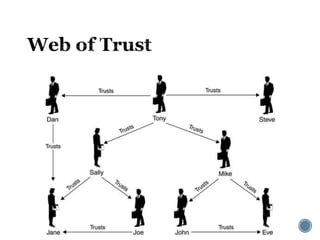
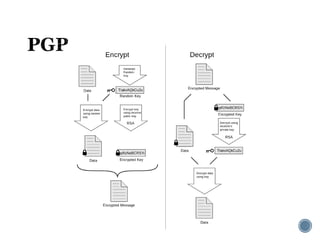
The document provides an overview of cryptography concepts for beginners. It discusses encryption techniques like encoding, encryption, obfuscation and cryptography. It also covers cryptanalysis, steganography, transposition ciphers, substitution ciphers, block ciphers and padding standards. Key concepts in public key cryptography like prime numbers, modular arithmetic, Diffie-Hellman key exchange and RSA encryption/decryption are summarized with examples. The document is intended as a basic introduction to cryptography topics for those just starting out.