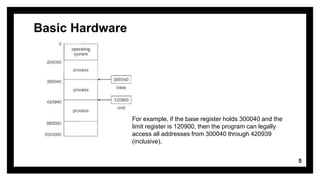
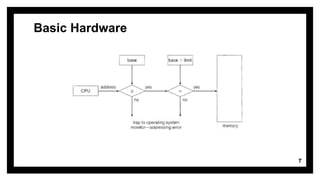
This document discusses memory management and address binding in operating systems. It explains that memory management handles moving processes between main memory and disk during execution. There are three types of address binding: compile time, where addresses are fixed at compile time; load time, where addresses can change at load time; and execution time, where processes can move during runtime and require special hardware. The document also covers basic hardware concepts like registers, caches, and protection using base and limit registers to control memory access for processes.