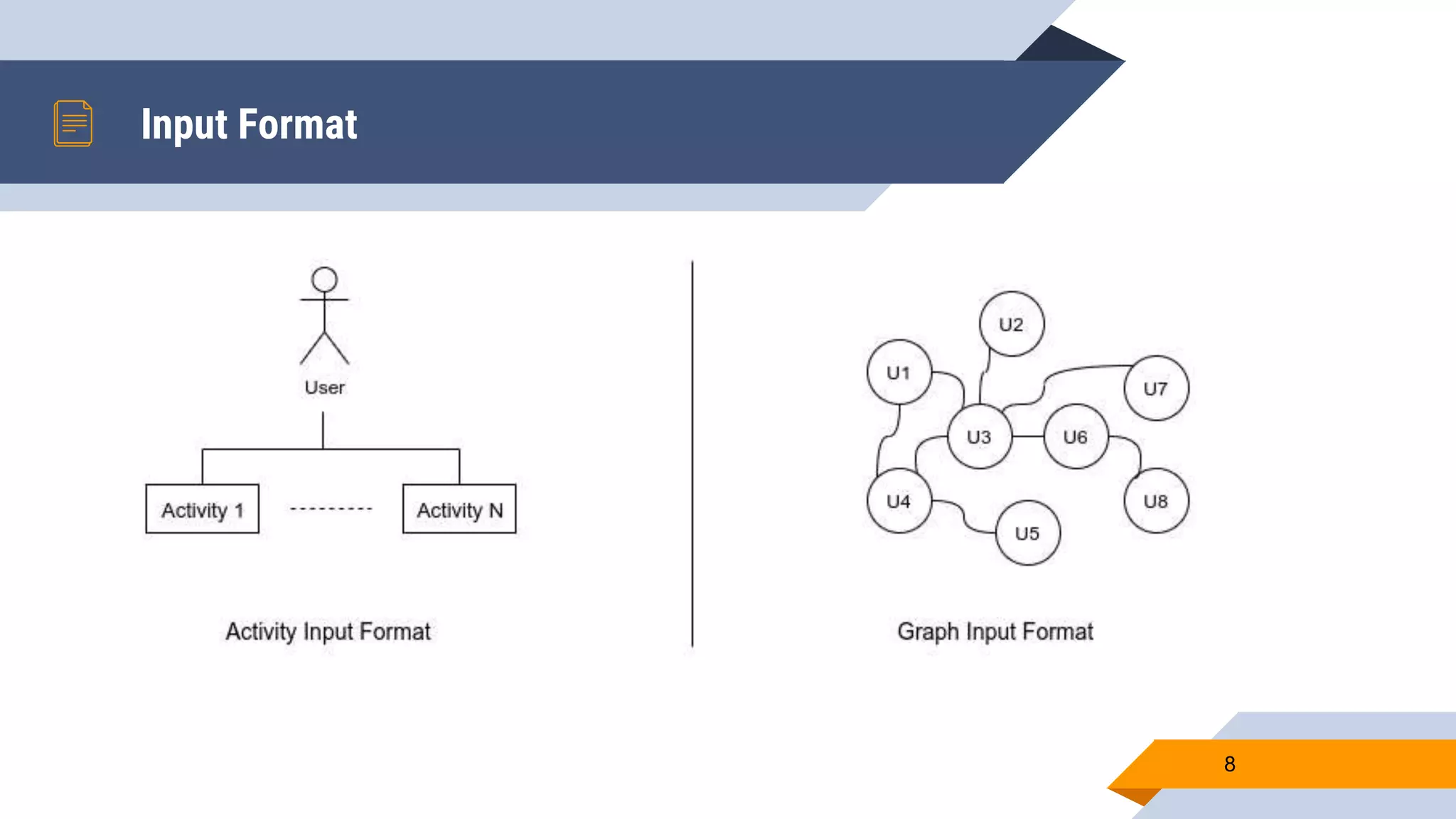
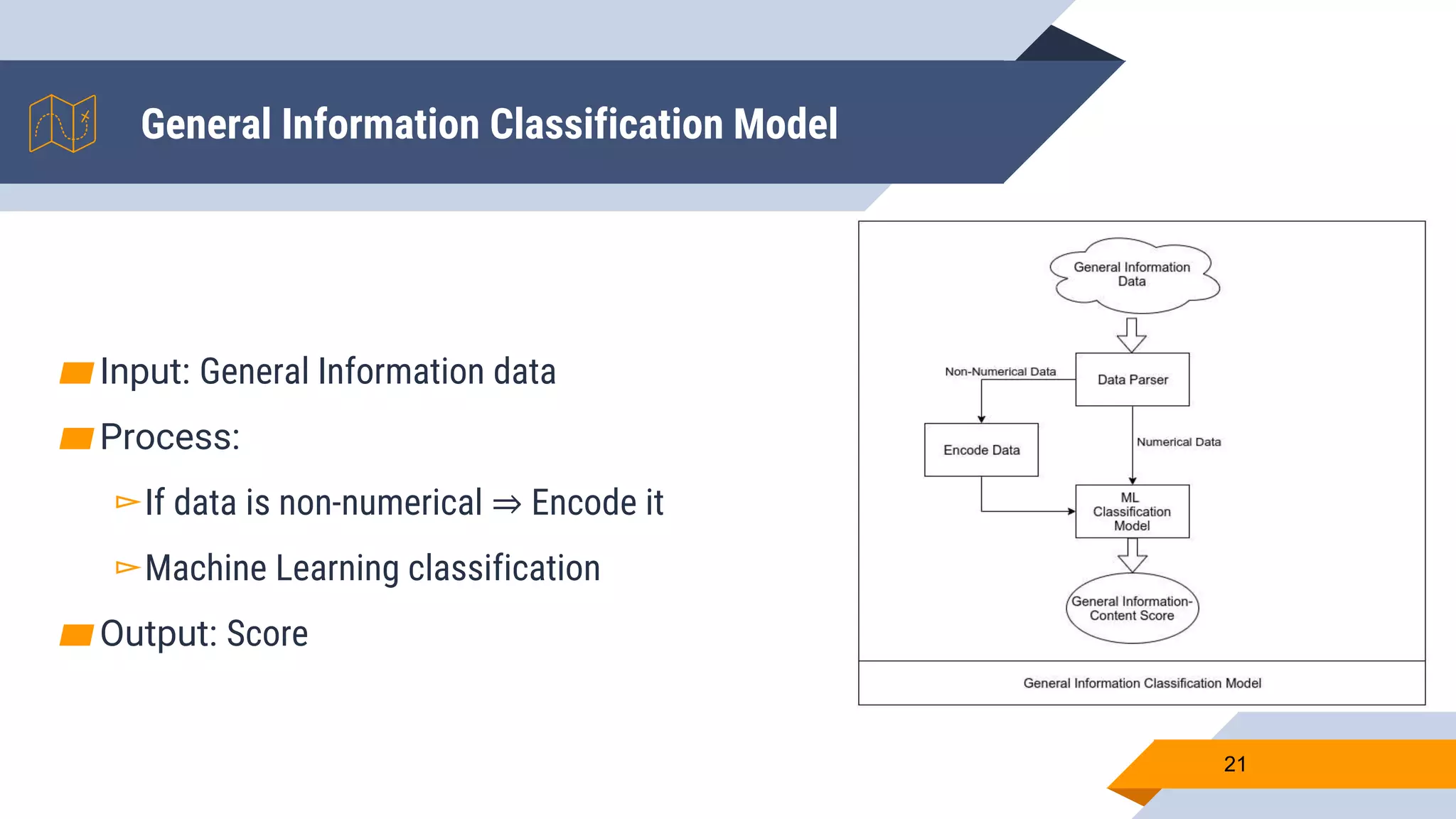
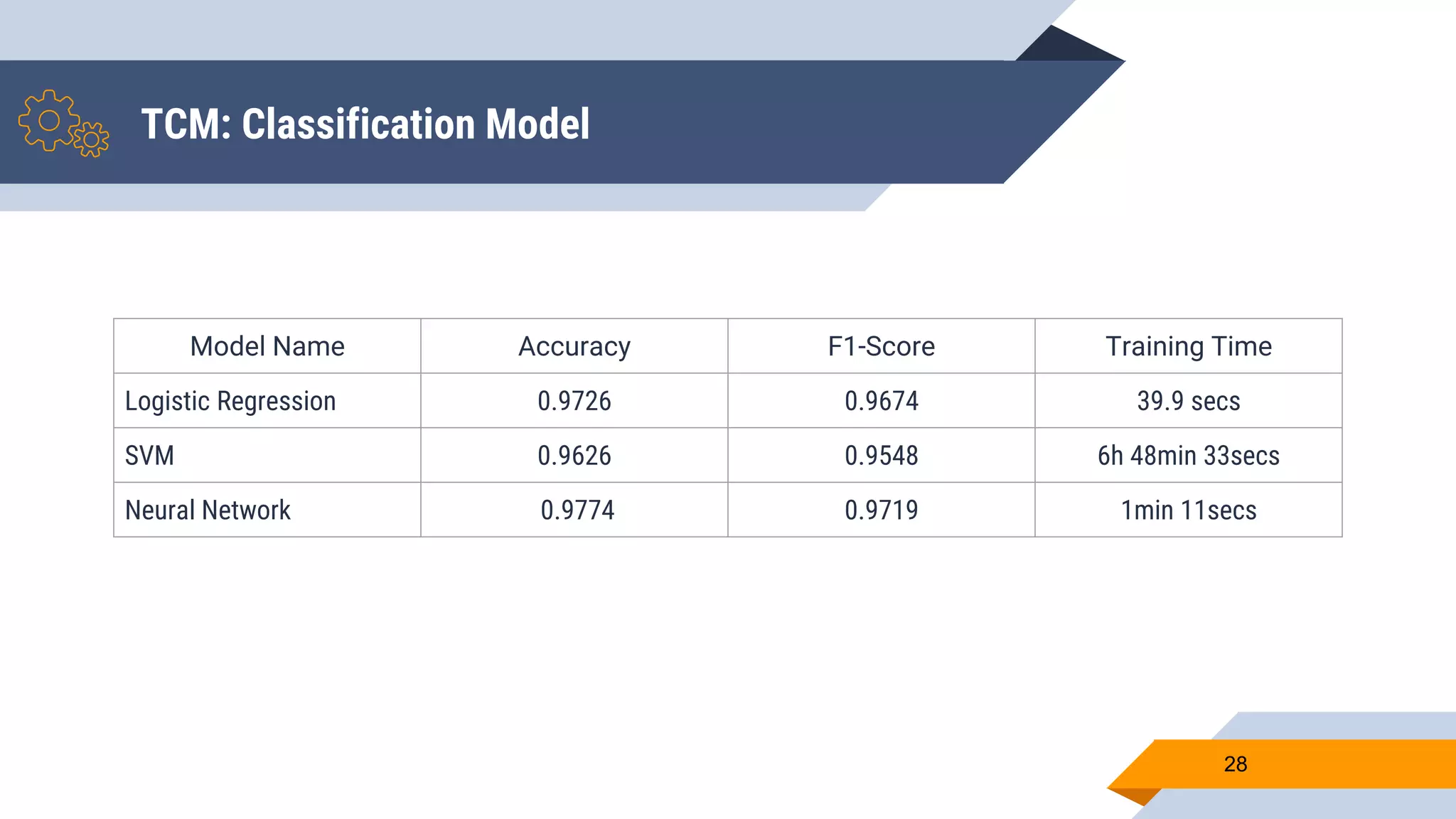
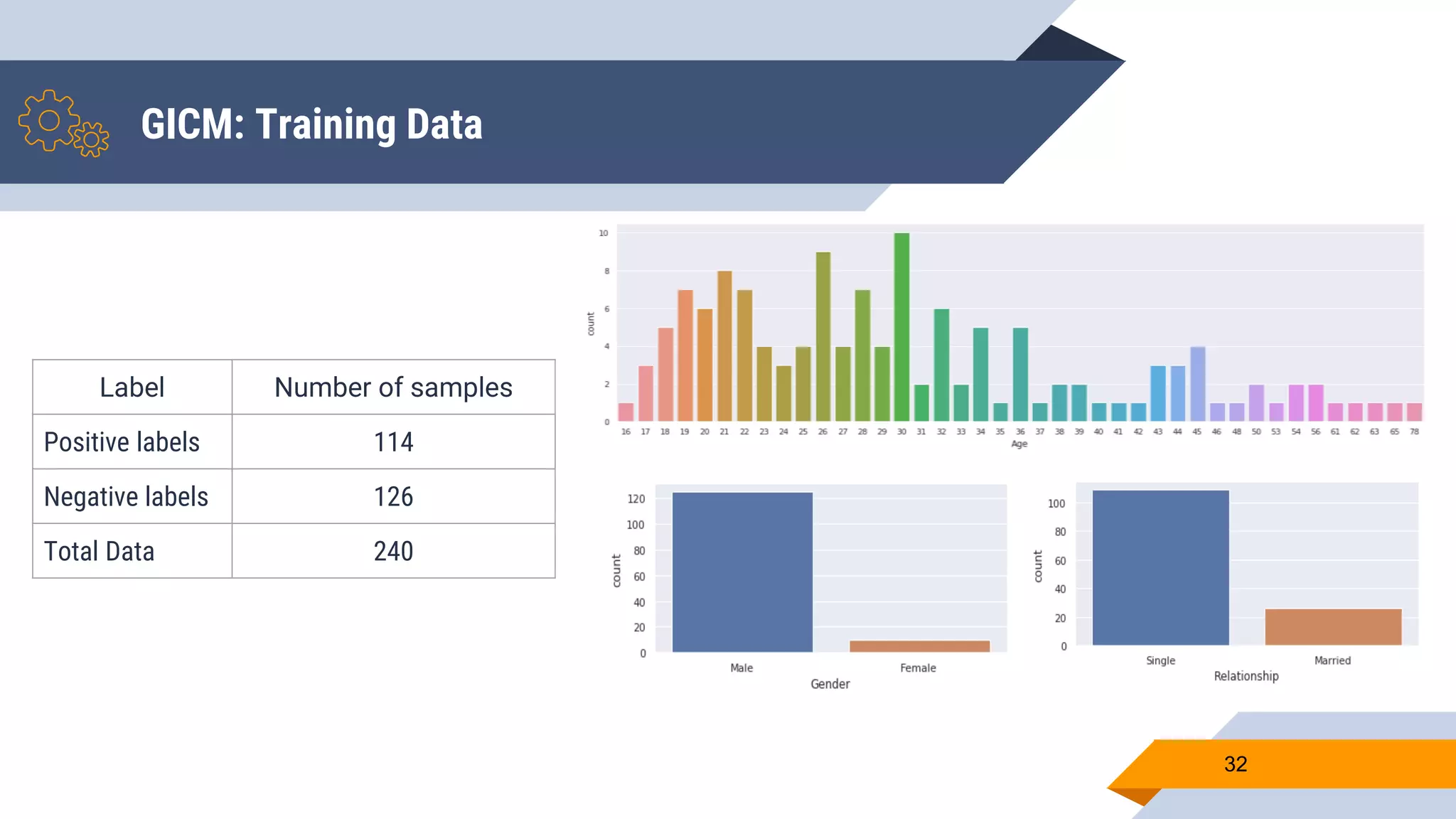
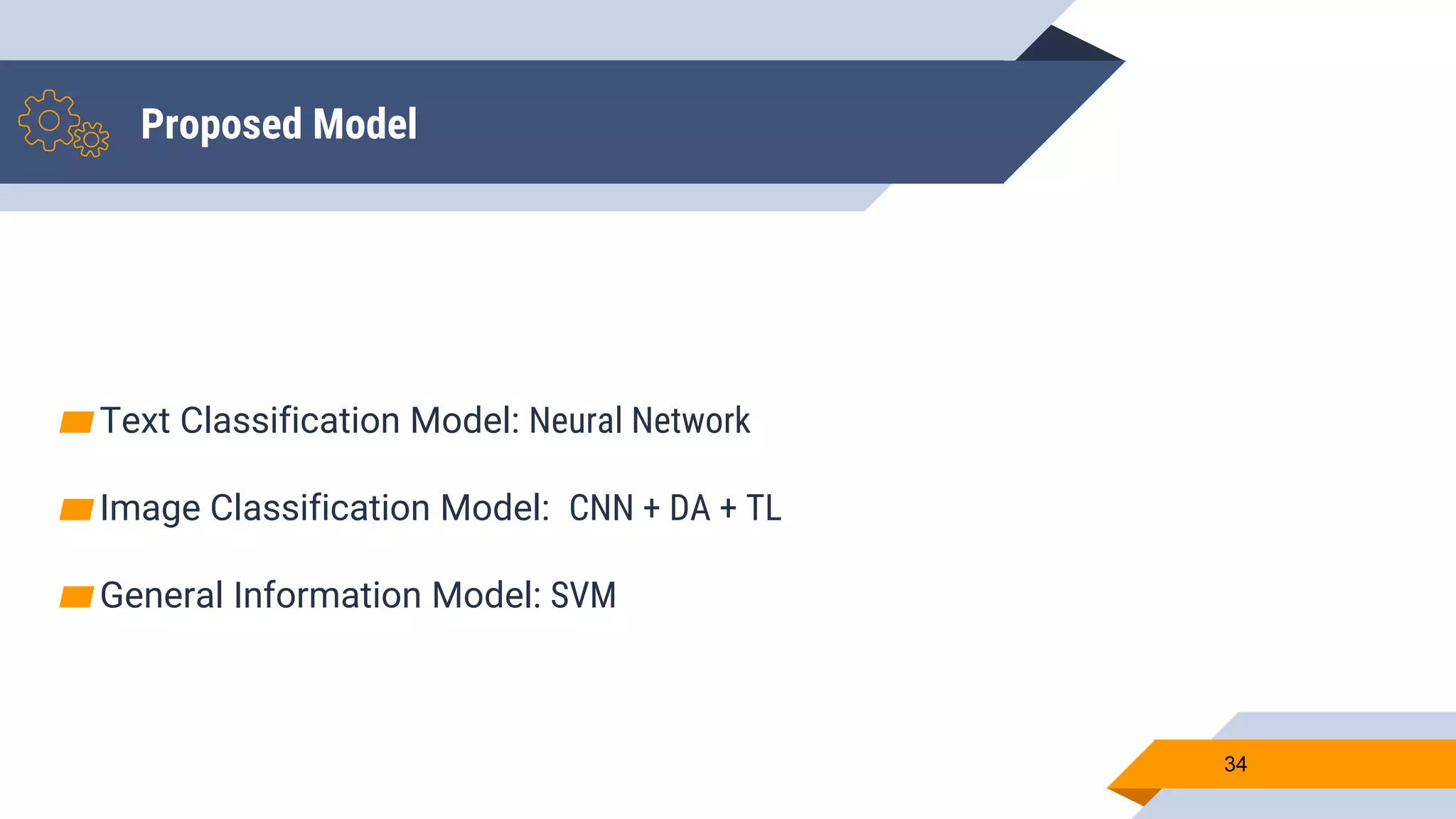
Wajdi Khattel presented a proposal for a terrorist detection model in social networks. The model uses a multi-dimensional network as input and consists of three sub-models: a text classification model, image classification model, and general information classification model. The sub-models each output a score that is then used by a decision making module to classify a user as a terrorist or not based on a threshold. The implementation involved collecting offline training data from banned Twitter accounts, Google images, and a public dataset. Online data was also collected from Facebook, Instagram, and Twitter using their APIs. Several machine learning models were tested for each sub-model and the proposed full model uses a neural network for text, CNN with data augmentation and