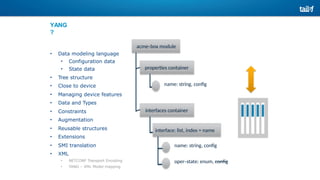
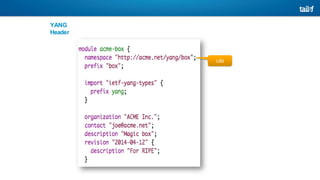
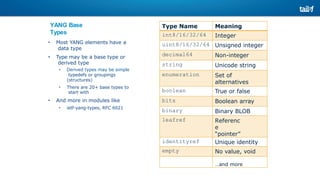
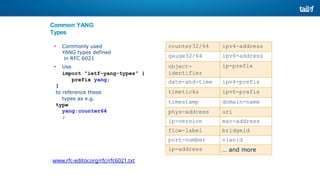
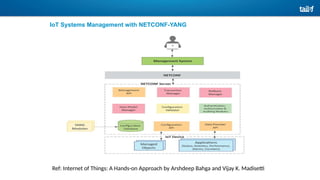
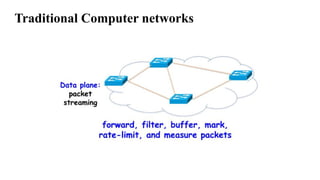
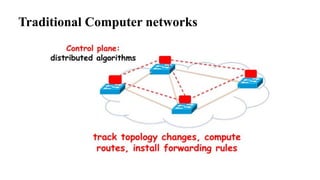
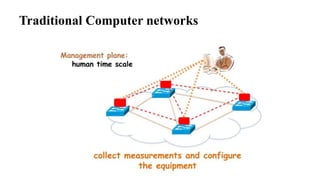
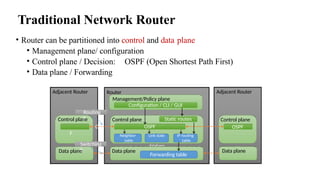
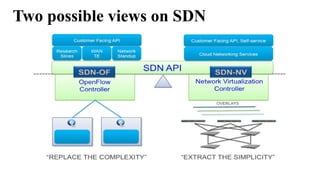
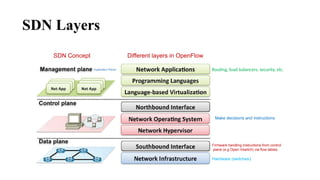
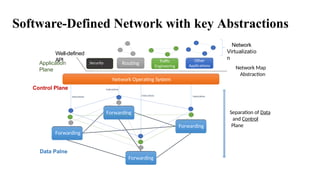
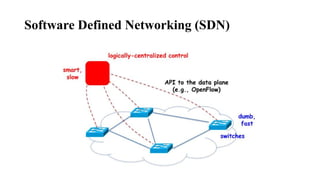
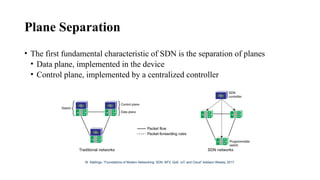
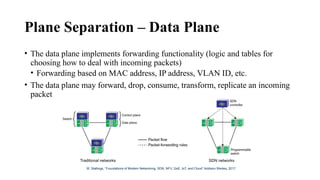
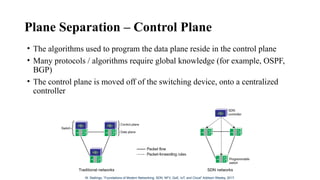
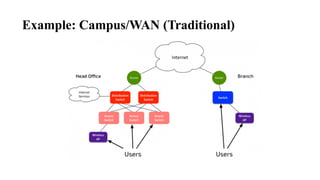
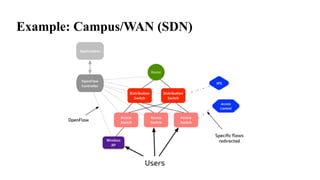
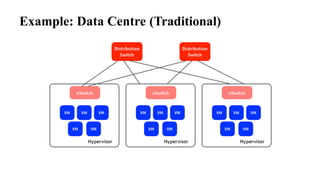
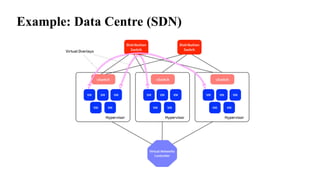
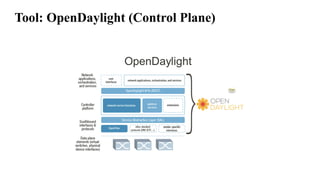
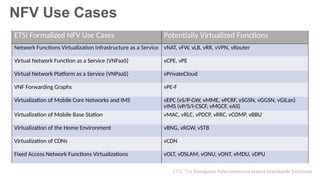
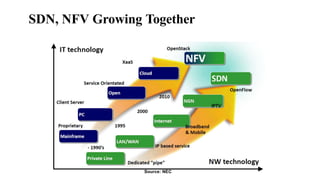
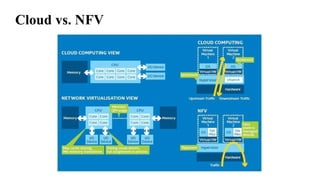
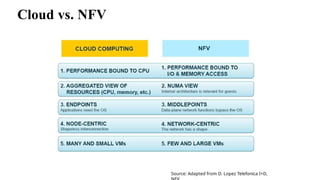
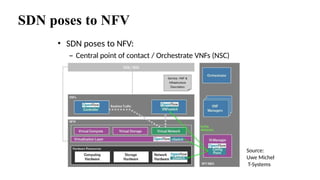
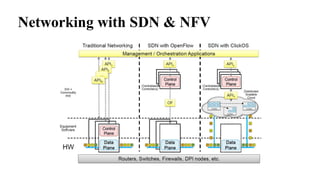
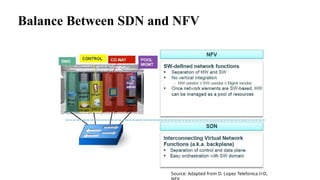
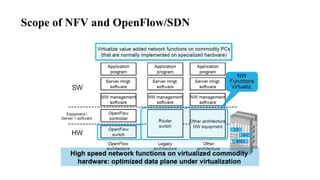
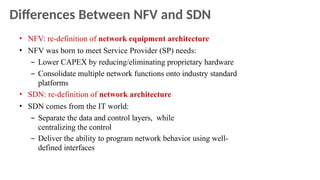
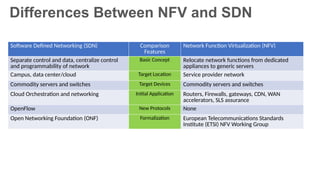
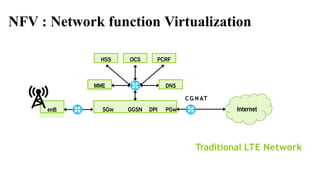
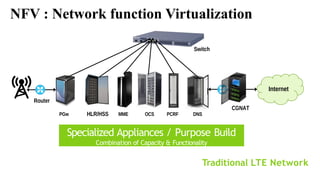
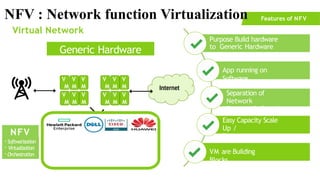
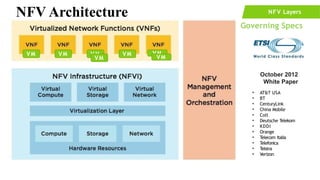
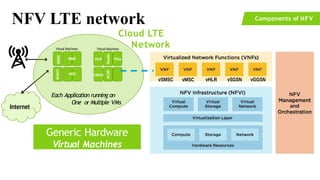
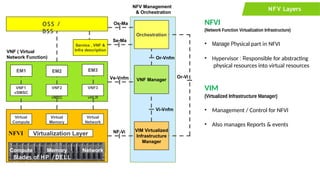
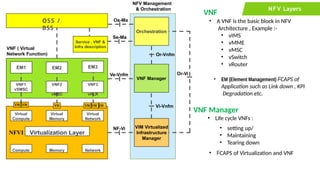
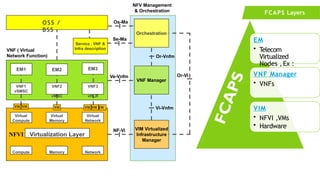
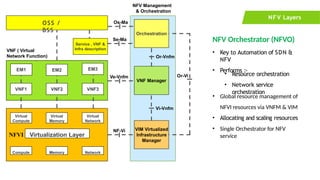
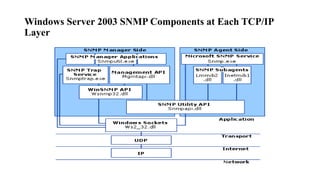
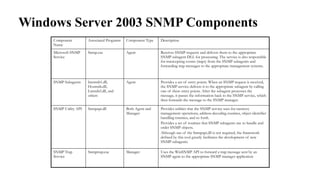
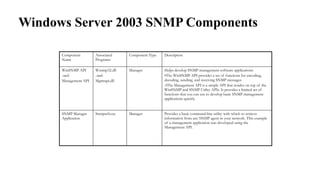
The document provides an overview of Software Defined Networking (SDN) and Network Function Virtualization (NFV), highlighting their fundamental characteristics, operational components, and benefits. It explains the separation of control and data planes in SDNs, centralized management of network operations, and the virtualization of network functions in NFV, which allows for better resource utilization and operational efficiency. Additionally, it discusses tools like OpenDaylight and various use cases for both SDN and NFV technologies in modern networking environments.























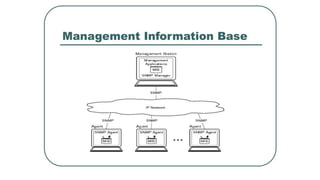
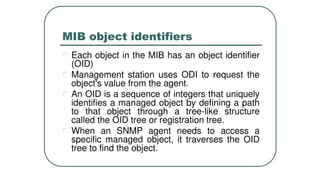
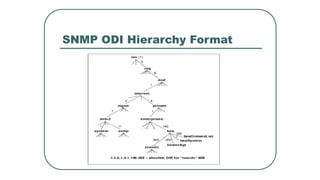
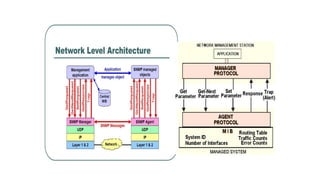





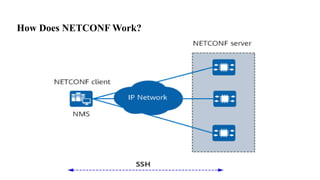

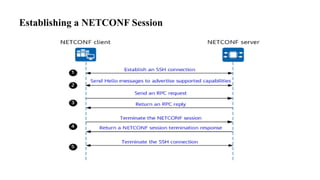





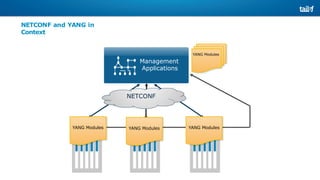
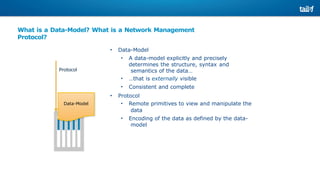



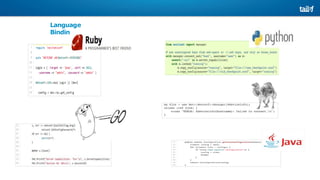



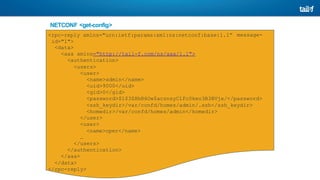
![NETCONF <hello>
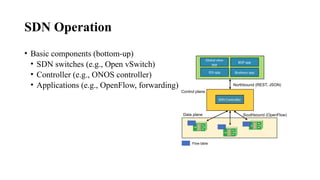
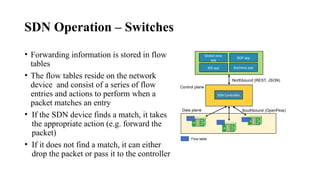
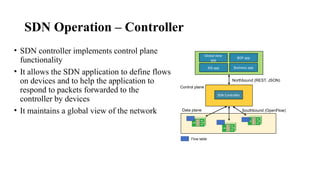
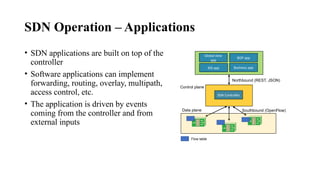
Operation
• Capabilities exchange
• Data model ID exchange
• Encoding
• Framing
• NETCONF 1.0 EOM, ]]>]]>
• NETCONF 1.1 Chunk Framing
<?xml version="1.0" encoding="UTF-8"?>
<hello xmlns="urn:ietf:params:xml:ns:netconf:base:1.1">
<capabilities>
<capability>urn:ietf:params:netconf:base:1.1</capability>
</capabilities>
</hello>](https://image.slidesharecdn.com/m-240929155637-71463193/85/M-Tech-Internet-of-Things-Unit-IV-pptx-111-320.jpg)