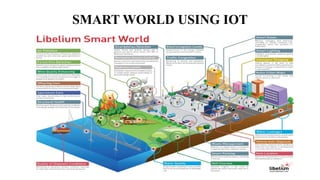
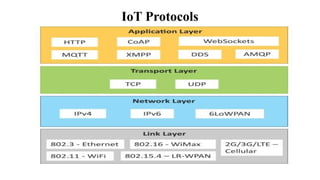
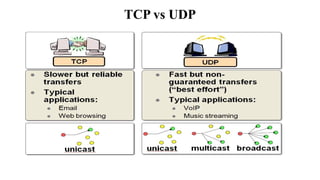
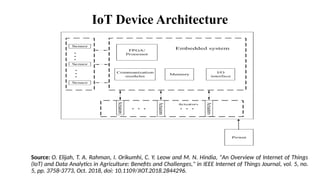
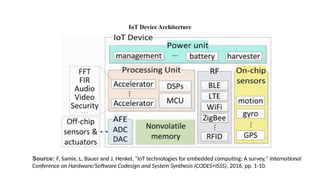
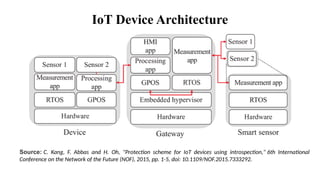
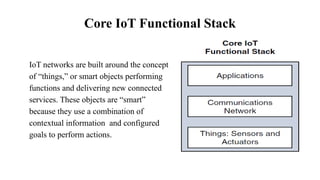
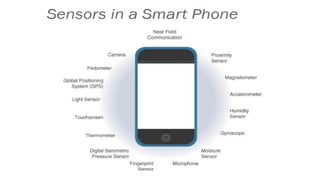
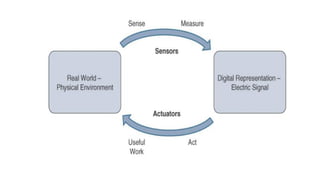
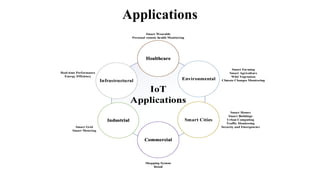
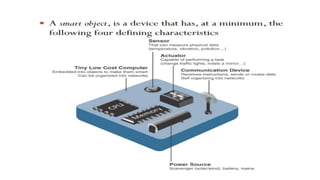
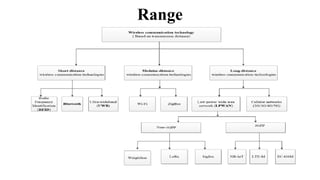
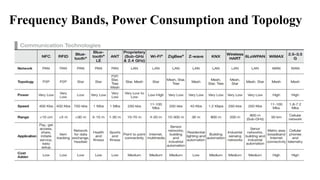
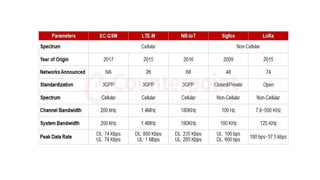
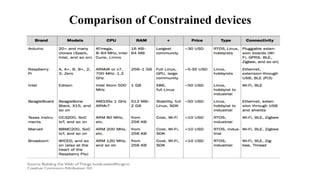
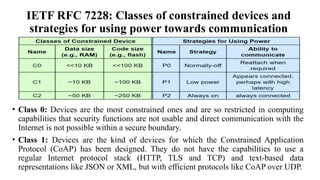
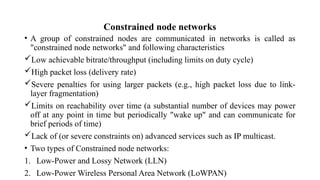
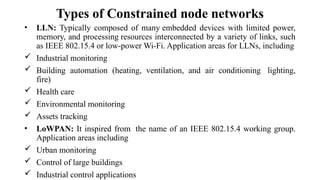
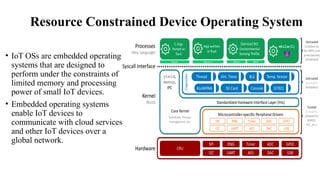
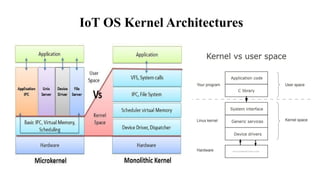
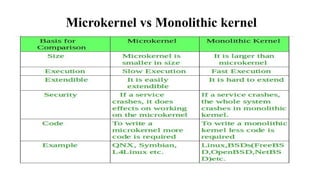
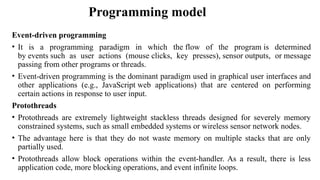
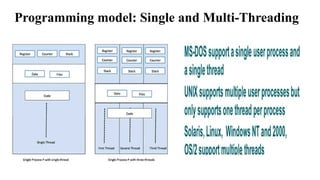
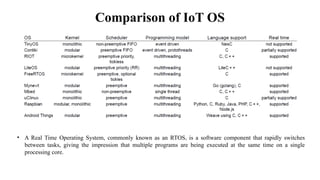
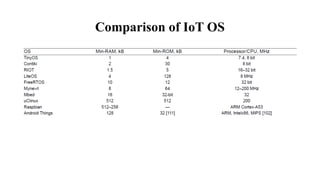
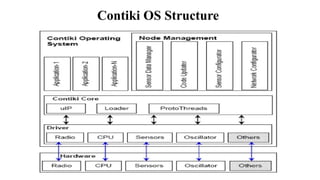
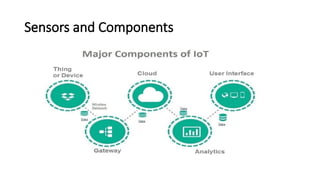
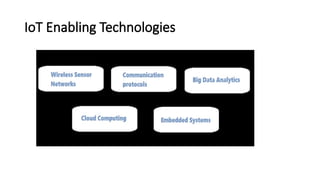
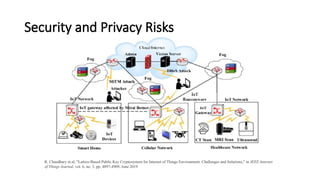
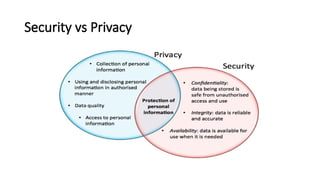
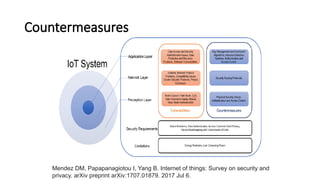
The document provides a comprehensive overview of the Internet of Things (IoT), defining it as a system of interconnected devices capable of data exchange without human interaction. It describes the characteristics, architecture, and protocols of IoT systems, including various types of sensors and actuators and their operational contexts. Additionally, it discusses the challenges and considerations for deploying IoT devices in resource-constrained environments and network management.