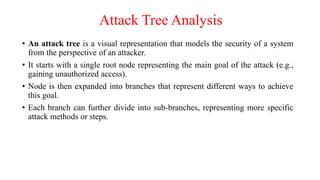
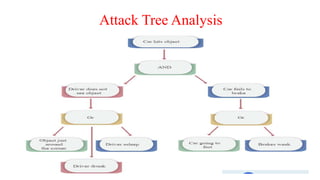
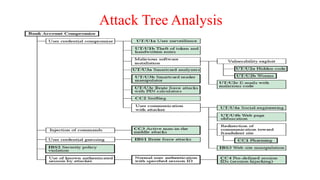
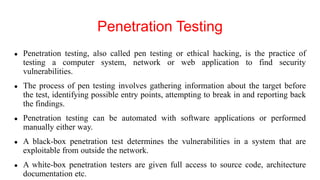
The document outlines the importance of scanning in cybersecurity, including network, vulnerability, web application, database, host-based, and wireless network scanning, highlighting various tools and methodologies used. It discusses attack tree analysis as a structured approach for assessing potential security threats, along with the process of vulnerability assessment and penetration testing to identify weaknesses and mitigate risks. Additionally, it provides insight into common cyber attacks, pentesting tools, roles, responsibilities, and certifications essential for professionals in the field.