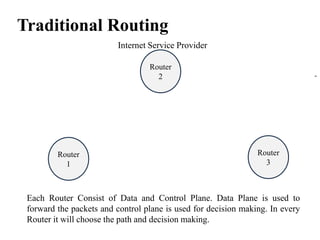
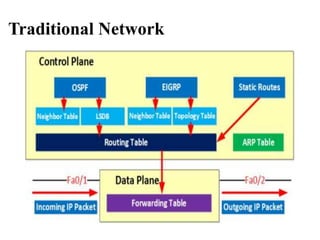
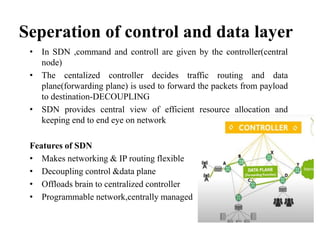
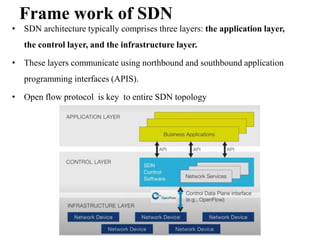
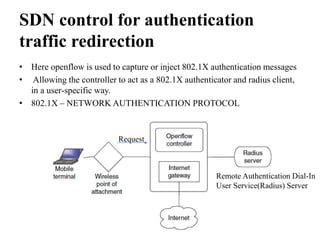
- SDN separates the control plane from the data plane, with a centralized controller making decisions about how traffic is routed through the network (3 sentences)
- This improves network flexibility and programmability. The controller directs traffic flow through OpenFlow switches based on application requirements. SDN also enables network slicing to deliver customized services. (3 sentences)
- In an example, an SDN controller directs test traffic from Generator B to Consumer B instead of Consumer A by tagging the packets and instructing switches to route them accordingly, demonstrating SDN's ability to control traffic flow. (3 sentences)