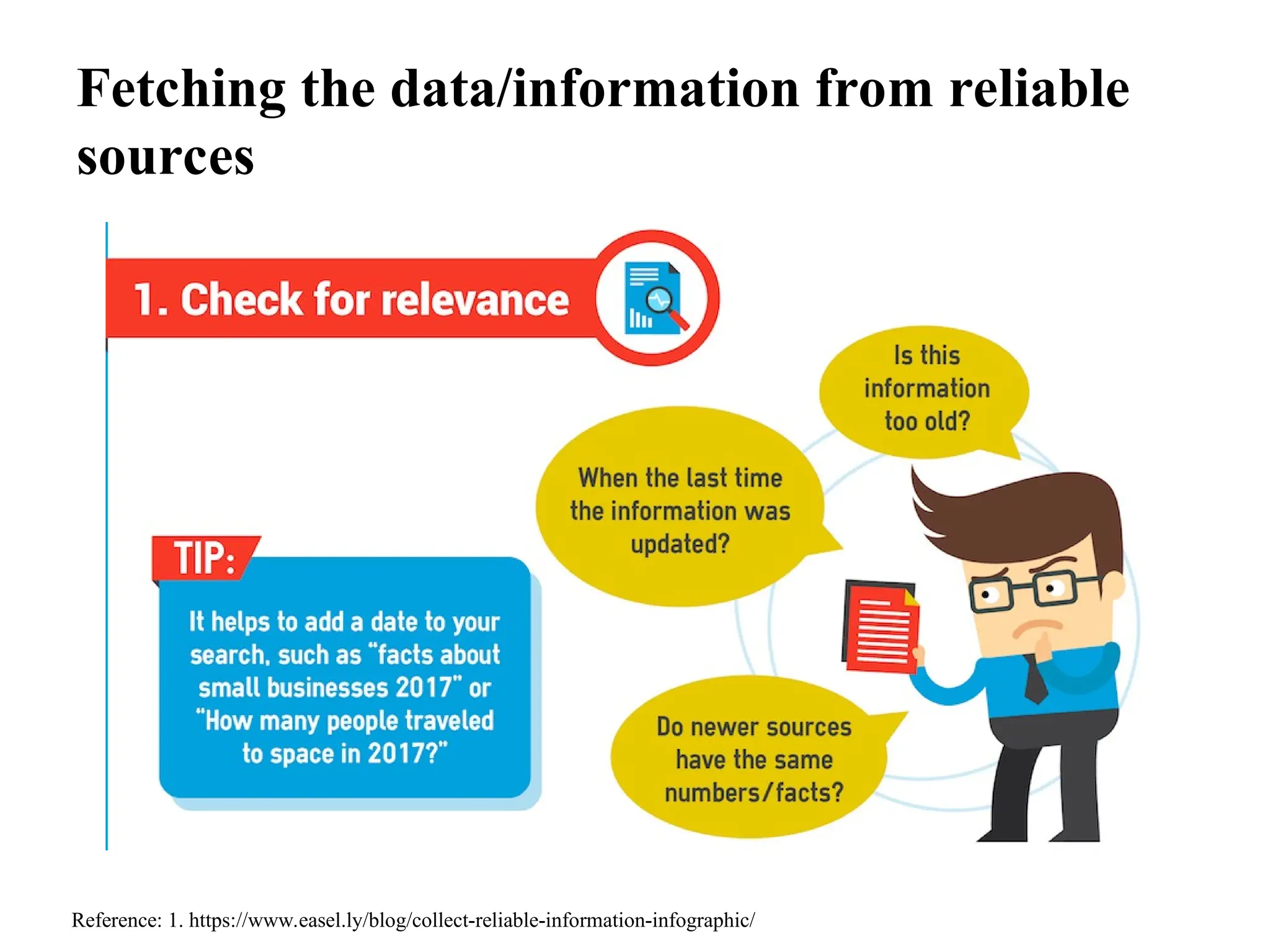
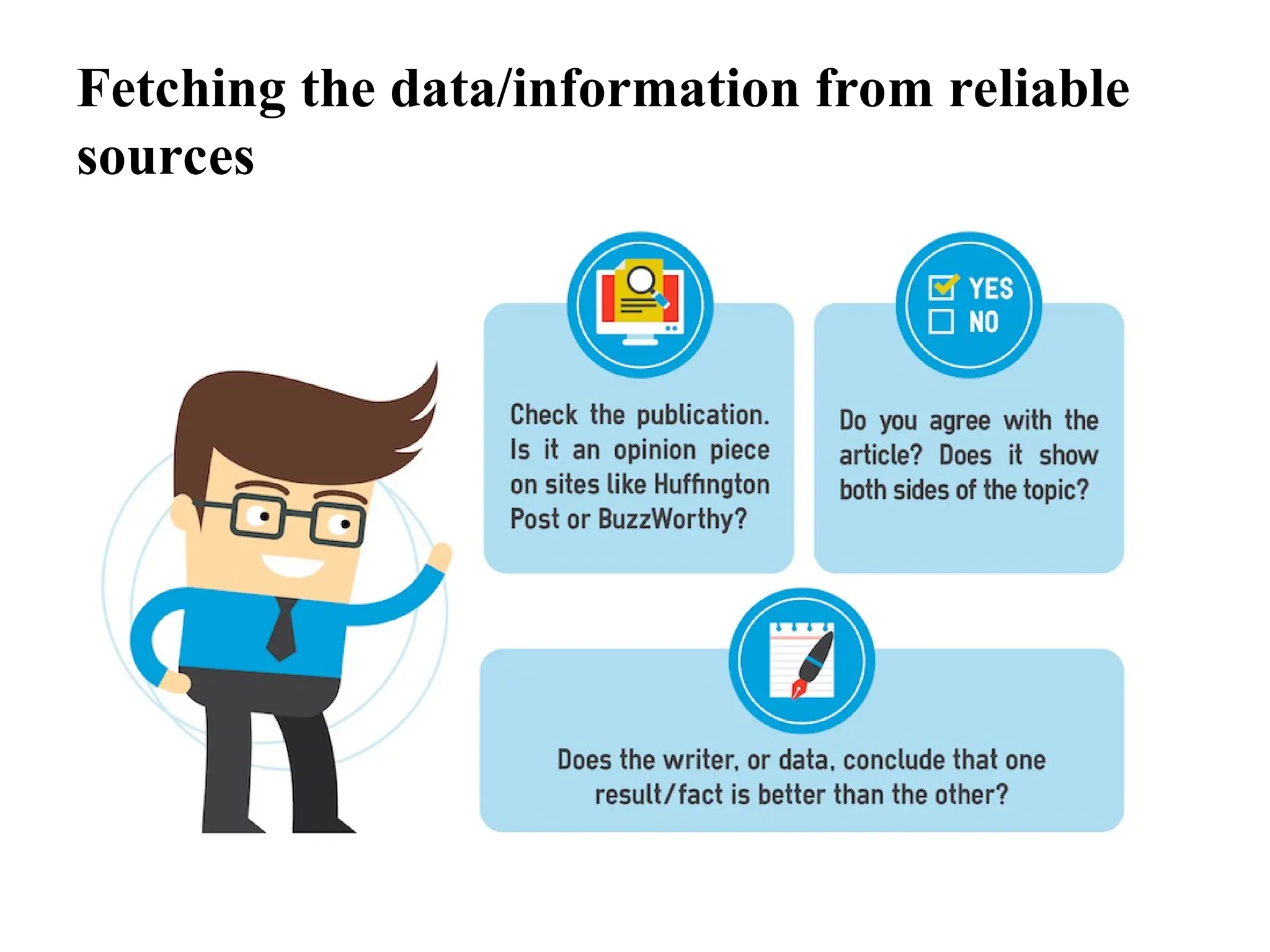
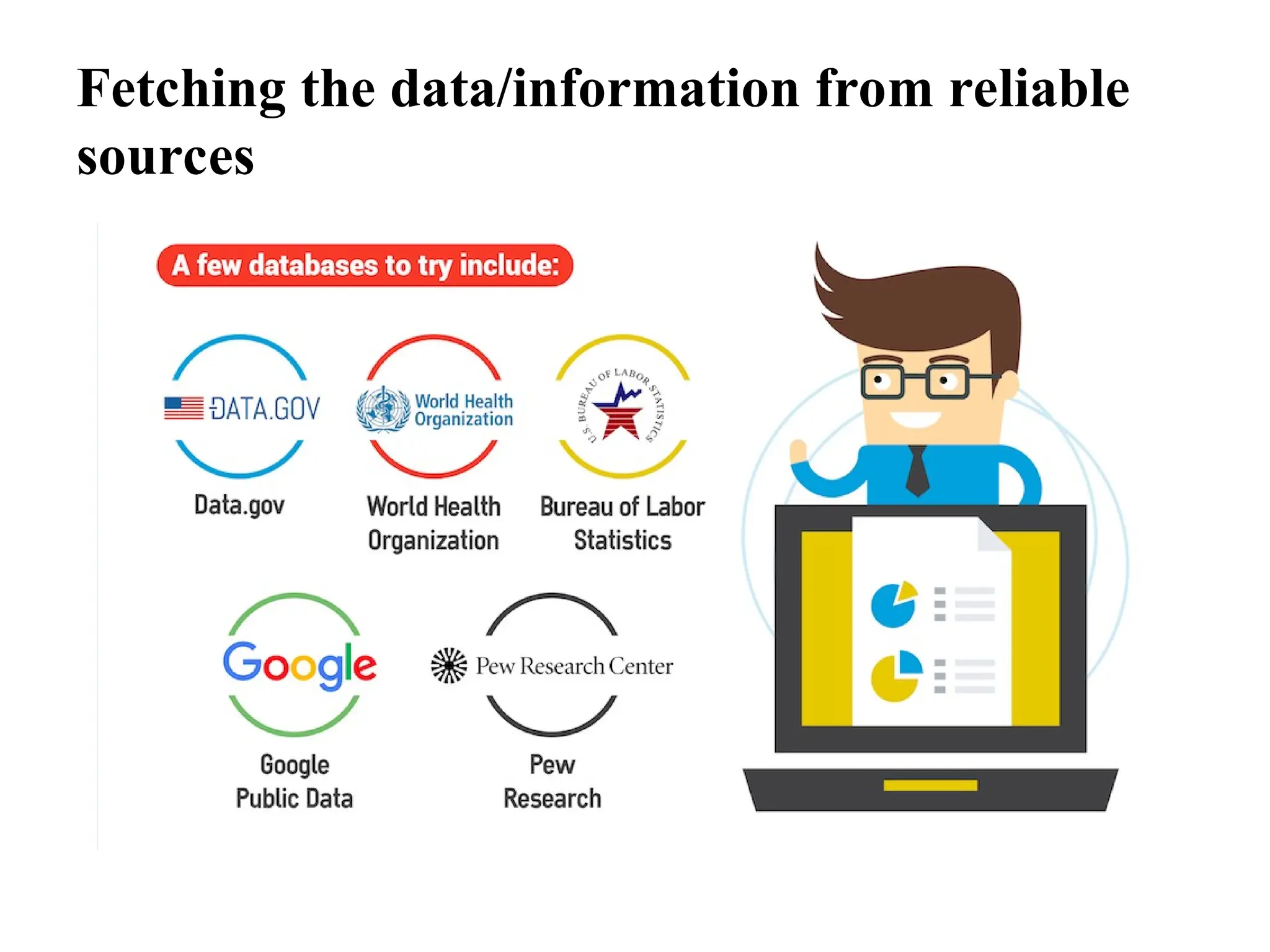
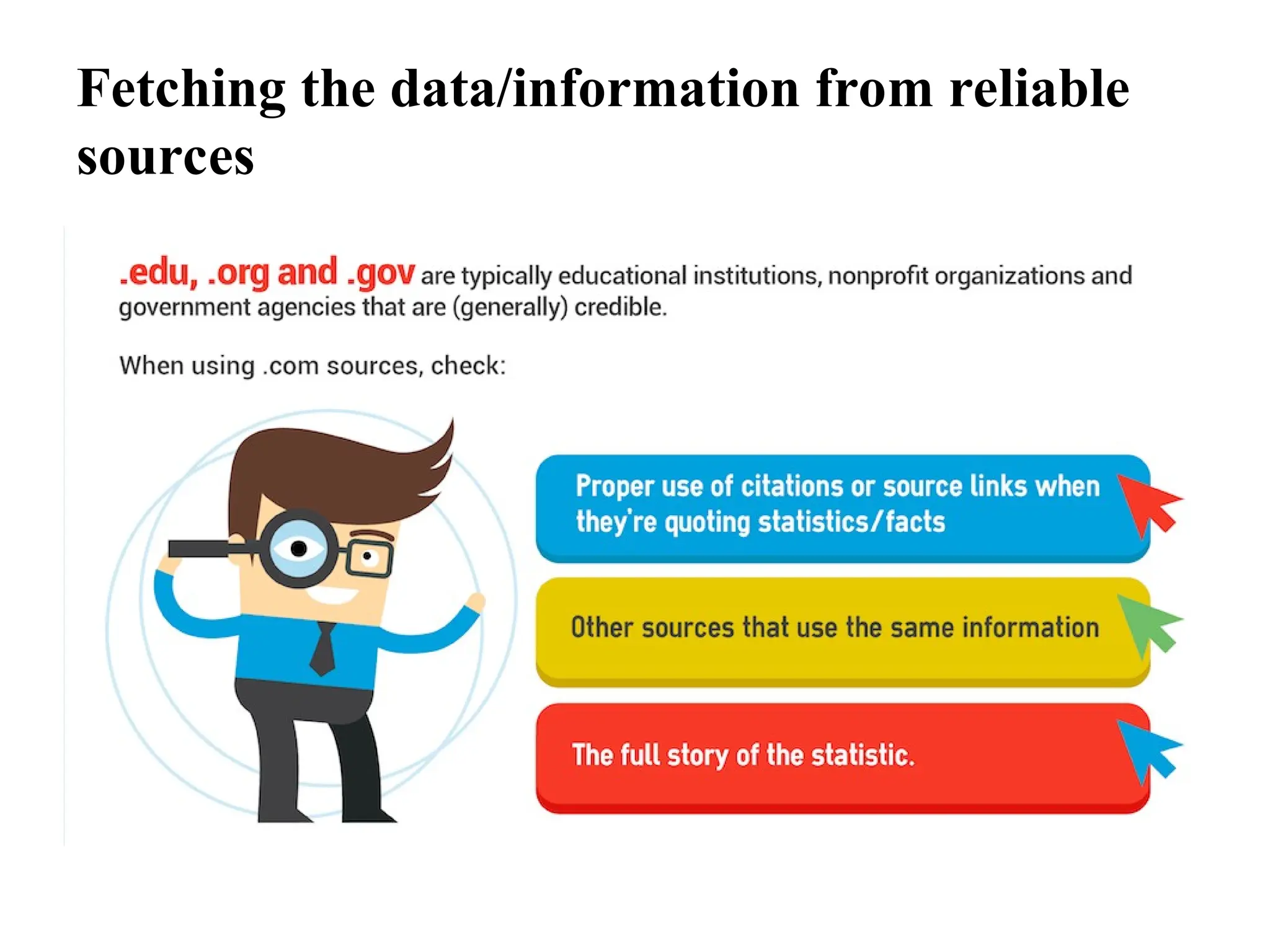
The document provides guidelines on how to fetch, evaluate, verify, and manage data/information effectively in information security. It emphasizes identifying reliable sources, validating data accuracy, and following organizational policies and procedures. Additionally, it outlines the importance of rule-based analysis and documentation to ensure data quality, address anomalies, and facilitate effective decision-making.