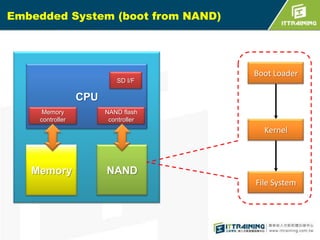
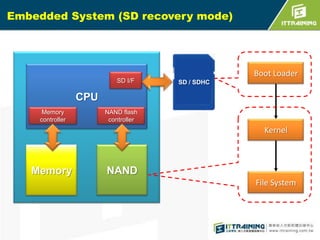
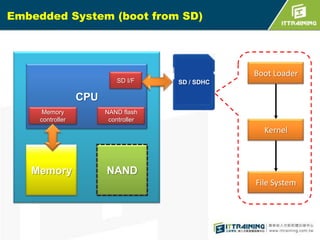
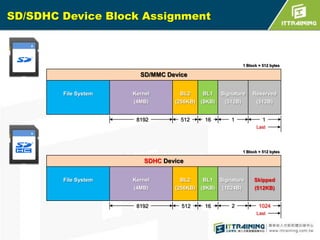
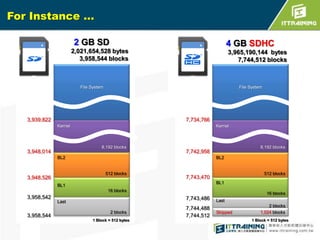
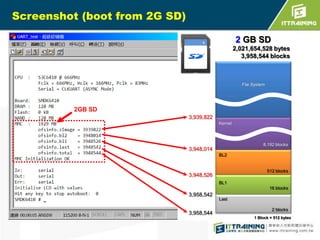
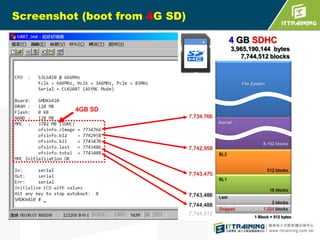
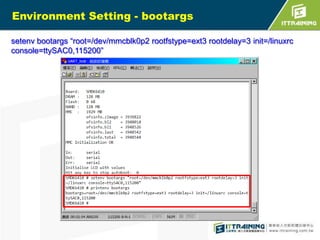
The document discusses the challenges of loading embedded systems from NAND flash memory and proposes a method to build the system on an SD card instead. It highlights the benefits of using an SD card, such as cost savings, ease of recovery, and the ability to update systems easily. Additionally, the document outlines the architecture, processes, and a shell script utility for fusing the boot loader, kernel, and file system onto the SD card.






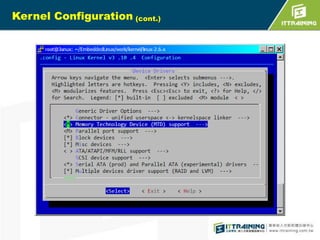
![S3C6410 iROM booting
S3C6410
ARM1176JZF-S
SDRAM
Controller
SDRAM
Booting Device
(SD/MMC Card,
OneNAND, Nand)
Stepping
Stone (8KB)
iROM(BL0)
(32KB)
OM=iROM Boot
HS-MMC
Controller
BL2
Kernel
OneNAND
Controller
D-TCM (16KB)
BL1
(8KB)
File
System
NAND
Controller
GPN[15:13]:Booting
device pin selection
1.iROM supports initial boot up
Initialize system clock, D-TCM,
device specific controller and
booting device.](https://image.slidesharecdn.com/embeddedlinuxsdfinal20130718-131111014415-phpapp02/85/Linux-SD-Card-11-320.jpg)
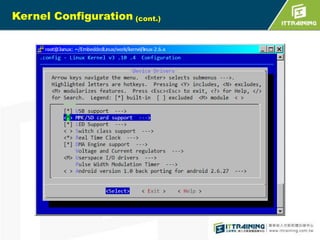
![S3C6410 iROM booting
(cont.)
S3C6410
ARM1176JZF-S
SDRAM
Controller
SDRAM
Booting Device
(SD/MMC Card,
OneNAND, Nand)
Stepping
Stone (8KB)
iROM(BL0)
(32KB)
OM=iROM Boot
HS-MMC
Controller
BL2
Kernel
OneNAND
Controller
D-TCM (16KB)
BL1
(8KB)
File
System
NAND
Controller
GPN[15:13]:Booting
device pin selection
2.iROM boot codes can load 8KB of
boot loader to stepping stone.
The 8 KB boot loader is called
BL1.](https://image.slidesharecdn.com/embeddedlinuxsdfinal20130718-131111014415-phpapp02/85/Linux-SD-Card-12-320.jpg)
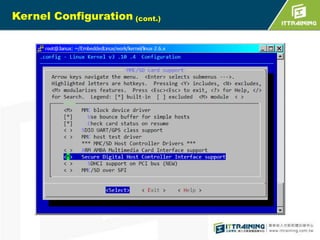
![S3C6410 iROM booting
(cont.)
S3C6410
ARM1176JZF-S
SDRAM
Controller
SDRAM
Booting Device
(SD/MMC Card,
OneNAND, Nand)
Stepping
Stone (8KB)
iROM(BL0)
(32KB)
OM=iROM Boot
HS-MMC
Controller
BL2
Kernel
OneNAND
Controller
D-TCM (16KB)
BL1
(8KB)
File
System
NAND
Controller
GPN[15:13]:Booting
device pin selection
3.BL1 can initialize system clock,
UART, and SDRAM for user.
After initializing, BL1 will load the
remaining boot loader called BL2
to SDRAM.](https://image.slidesharecdn.com/embeddedlinuxsdfinal20130718-131111014415-phpapp02/85/Linux-SD-Card-13-320.jpg)
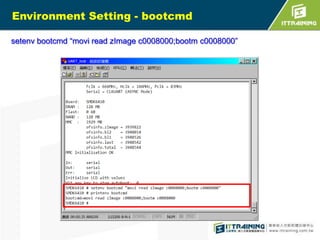
![S3C6410 iROM booting
(cont.)
S3C6410
ARM1176JZF-S
SDRAM
Controller
SDRAM
Booting Device
(SD/MMC Card,
OneNAND, Nand)
Stepping
Stone (8KB)
iROM(BL0)
(32KB)
OM=iROM Boot
HS-MMC
Controller
BL2
Kernel
OneNAND
Controller
D-TCM (16KB)
BL1
(8KB)
File
System
NAND
Controller
GPN[15:13]:Booting
device pin selection
4.Finally, jump to start address of
BL2. That will make good
environment to use system.](https://image.slidesharecdn.com/embeddedlinuxsdfinal20130718-131111014415-phpapp02/85/Linux-SD-Card-14-320.jpg)






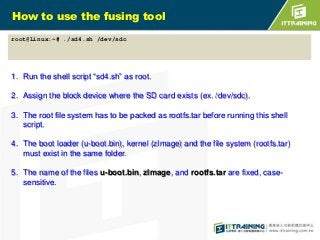
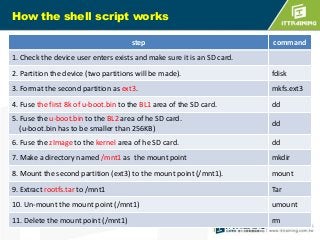
![Fusing Tool
To fuse the boot loader (u-boot.bin), kernel (zImage), and file system (rootfs.tar) to
SD card automatically.
sdcard=$1
if [ "$sdcard" = "" ];then
echo " # Usage - ./sd.sh /dev/SDcardDevicename (ex. sd.sh /dev/sdc)"
echo " # prepare the necessary files(zImage,rootfs.tar,uboot.bin
rootfs.tar is a tar.bz2 file)"
echo " # and verify that the device is correct"
exit 0
.
mkdir /mnt1
mount ${sdcard}2 /mnt1
tar -jxvf rootfs.tar -C /mnt1
cp -rap /mnt/rootfs/* /mnt1
umount /mnt1
rm -rf /mnt1](https://image.slidesharecdn.com/embeddedlinuxsdfinal20130718-131111014415-phpapp02/85/Linux-SD-Card-34-320.jpg)