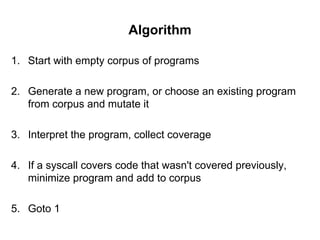
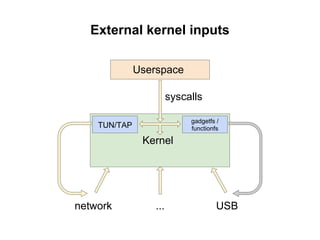
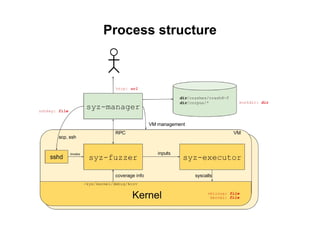
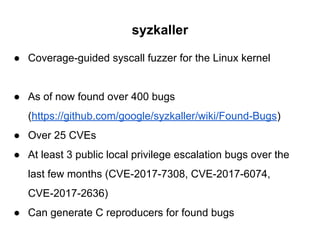
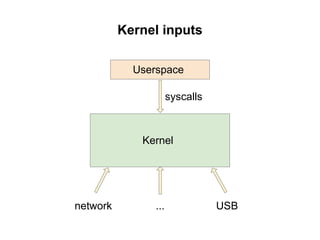
The document discusses methods for finding 0days in the Linux kernel using various tools like AddressSanitizer, libFuzzer, and syzkaller, which help detect a range of bug types through dynamic bug finding techniques. Syzkaller is highlighted as a coverage-guided fuzzer that has found over 400 bugs, including serious vulnerabilities, and the document outlines a step-by-step approach to using it for bug discovery. It also mentions additional fuzzing tools and techniques for enhancing kernel security and bug detection methods.





![KASAN report
BUG: KASAN: use-after-free in sctp_id2assoc+0x3a3/0x3b0
net/sctp/socket.c:224
Read of size 8 at addr ffff8800385b6838 by task syz-executor2/5889
Call Trace:
sctp_id2assoc+0x3a3/0x3b0 net/sctp/socket.c:224
sctp_setsockopt_rtoinfo net/sctp/socket.c:2931 [inline]
sctp_setsockopt+0x4b7/0x60f0 net/sctp/socket.c:4018
sock_common_setsockopt+0x95/0xd0 net/core/sock.c:2850
SYSC_setsockopt net/socket.c:1798 [inline]
SyS_setsockopt+0x270/0x3a0 net/socket.c:1777
entry_SYSCALL_64_fastpath+0x1f/0xbe](https://image.slidesharecdn.com/phdays2017-howtofind0daysinthelinuxkernel-170531082317/85/Linux-6-320.jpg)
![KASAN report
Allocated by task 5841:
kzalloc include/linux/slab.h:663 [inline]
sctp_association_new+0x114/0x2180 net/sctp/associola.c:309
...
SyS_connect+0x24/0x30 net/socket.c:1569
entry_SYSCALL_64_fastpath+0x1f/0xbe
Freed by task 5882:
kfree+0xe8/0x2b0 mm/slub.c:3882
sctp_association_destroy net/sctp/associola.c:435 [inline]
...
syscall_return_slowpath+0x3ba/0x410 arch/x86/entry/common.c:263
entry_SYSCALL_64_fastpath+0xbc/0xbe](https://image.slidesharecdn.com/phdays2017-howtofind0daysinthelinuxkernel-170531082317/85/Linux-7-320.jpg)


![Syscall descriptions
open(file filename, flags flags[open_flags],
mode flags[open_mode]) fd
read(fd fd, buf buffer[out], count len[buf])
close(fd fd)
open_flags = O_RDONLY, O_WRONLY, O_RDWR, O_APPEND ...](https://image.slidesharecdn.com/phdays2017-howtofind0daysinthelinuxkernel-170531082317/85/Linux-12-320.jpg)
![Syscall descriptions:
discriminated syscalls
socket$inet_tcp(
domain const[AF_INET],
type const[SOCK_STREAM],
proto const[0]) sock_tcp
socket$packet(
domain const[AF_PACKET],
type flags[packet_socket_type],
proto const[ETH_P_ALL_BE]) sock_packet](https://image.slidesharecdn.com/phdays2017-howtofind0daysinthelinuxkernel-170531082317/85/Linux-13-320.jpg)
![Syscall descriptions:
structs layout
sockaddr_ll {
sll_family const[AF_PACKET, int16]
sll_protocol flags[packet_protocols, int16be]
sll_ifindex ifindex
sll_hatype const[ARPHRD_ETHER, int16]
sll_pkttype int8
sll_halen const[6, int8]
sll_addr mac_addr
pad array[const[0, int8], 2]
}
bind$packet(fd sock_packet, addr ptr[in, sockaddr_ll], addrlen len[addr])](https://image.slidesharecdn.com/phdays2017-howtofind0daysinthelinuxkernel-170531082317/85/Linux-14-320.jpg)
![Syscall descriptions:
resources
resource sock[fd]
socket(domain flags[socket_domain], type flags[socket_type],
proto int8) sock
bind(fd sock, addr ptr[in, sockaddr_storage], addrlen len[addr])
resource sock_packet[sock]
socket$packet(domain const[AF_PACKET], type flags[packet_socket_type],
proto const[ETH_P_ALL_BE]) sock_packet
bind$packet(fd sock_packet, addr ptr[in, sockaddr_ll], addrlen len[addr])](https://image.slidesharecdn.com/phdays2017-howtofind0daysinthelinuxkernel-170531082317/85/Linux-15-320.jpg)