The document discusses Linux hardening techniques and mitigations against memory corruption vulnerabilities, highlighting specific CVEs related to memory safety bugs that could be exploited. It covers various mitigation strategies such as Non-Executable Stack, Address Space Layout Randomization (ASLR), and Stack Canaries, and introduces advanced concepts like Return-Oriented Programming (ROP) and Side Channels (Spectre). The presentation concludes with discussions on modern mitigation techniques and the importance of kernel self-protection projects.


![Memory Corruption
Why I’m talking about this old vulnerability class
CVE-2018-5188 Memory safety bugs present in Firefox 60 [...]
Some of these bugs showed evidence of memory
corruption and we presume that with enough effort
that some of these could be exploited to run arbitrary
code. [...]
CVE-2018-6069 Stack buffer overflow in Skia in Google Chrome
prior to 65.0.3325.146 allowed a remote attacker to
perform an out of bounds memory read via a crafted
HTML page.
CVE-2018-16842 Curl versions 7.14.1 through 7.61.1 are vulnerable
to a heap-based buffer over-read in the
tool_msgs.c:voutf() function that may result in
information exposure and denial of service.](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-3-320.jpg)

![Buffer Overflow
Introduction
C Code
uint32_t a;
unsigned char b[4];
ASM
sub esp,0x8
a
b](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-5-320.jpg)
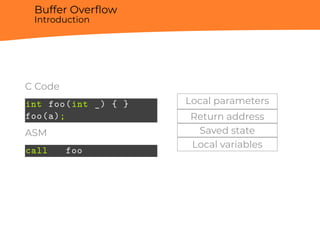
![Buffer Overflow
Introduction
C Code
int foo(int _) {
uint32_t a;
char b[4];
return 0;
}
Local parameters
Return address
Saved State
a
b](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-7-320.jpg)
![Buffer Overflow
Introduction
C Code
int foo(int _) {
uint32_t a;
char b[4];
==> gets(b);
return 0;
}
Local parameters
Return address
Saved State
a
b](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-8-320.jpg)
![Buffer Overflow
Introduction
C Code
int foo(int _) {
uint32_t a;
char b[4];
==> gets(b);
return 0;
}
Local parameters
Return address
Saved State
a
A A A A](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-9-320.jpg)
![Buffer Overflow
Introduction
C Code
int foo(int _) {
uint32_t a;
char b[4];
==> gets(b);
return 0;
}
Local parameters
Return address
Saved State
aA A A A
A A A A](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-10-320.jpg)
![Buffer Overflow
Introduction
C Code
int foo(int _) {
uint32_t a;
char b[4];
==> gets(b);
return 0;
}
Local parameters
Return address
A A A A
A A A A
A A A A](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-11-320.jpg)
![Buffer Overflow
Introduction
C Code
int foo(int _) {
uint32_t a;
char b[4];
==> gets(b);
return 0;
}
Local parameters
A A A A
A A A A
A A A A
A A A A](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-12-320.jpg)
![Buffer Overflow
Introduction
C Code
int foo(int _) {
uint32_t a;
char b[4];
gets(b);
==> return 0;
}
Local parameters
A A A A
A A A A
A A A A
A A A A](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-13-320.jpg)
![Buffer Overflow
Shellcode
C Code
int foo(int _) {
uint32_t a;
char b[4];
gets(b);
==> return 0;
}
Local parameters
0x......
Shellcode](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-16-320.jpg)

![Buffer Overflow
Return 2 libc
C Code
int foo(int _) {
uint32_t a;
char b[4];
gets(b);
==> return 0;
}
Local parameters
Address of system
Padding](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-20-320.jpg)
![Buffer Overflow
Return 2 libc
C Code
int foo(int _) {
uint32_t a;
char b[4];
gets(b);
==> return 0;
}
Previous AR
Fake return
Address of system
Padding](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-21-320.jpg)
![Buffer Overflow
Return 2 libc
C Code
int foo(int _) {
uint32_t a;
char b[4];
gets(b);
==> return 0;
}
Address of ”/bin/sh”
Fake return
Address of system
Padding](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-22-320.jpg)
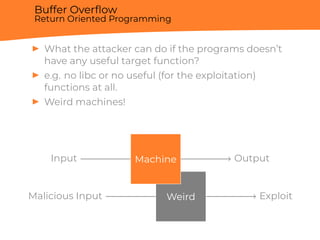


![Information Leak
printf format parameter leak
C Code:
#include <stdio.h>
#include <stdint.h>
int main(int argc, char **argv) {
uintptr_t token = 0x1234;
return printf(argv[1]);
}
Exploit:
$ ./foo hello
hello
$ ./foo %p
0x7ffedf09fb10
$ ./foo %9$p
0x1234](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-26-320.jpg)
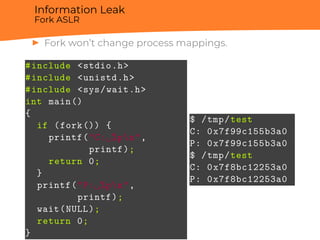
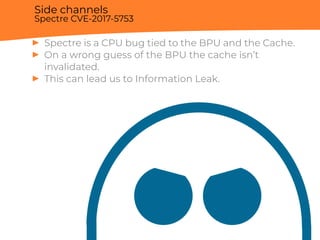
![Side channels
Spectre CVE-2017-5753
Cache
...
if (a < b)
array2[array1[a]] ”warning”
return](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-29-320.jpg)
![Side channels
Spectre CVE-2017-5753
Cache
array2[array1[a]]
if (a < b)
array2[array1[a]] ”warning”
return](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-30-320.jpg)
![Side channels
Spectre CVE-2017-5753
Cache
array2[array1[a]]
if (a < b)
array2[array1[a]] ”warning”
return](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-31-320.jpg)
![Side channels
Spectre CVE-2017-5753
Cache
...
if (a < b)
array2[array1[a]] ”warning”
return](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-32-320.jpg)
![Side channels
Spectre CVE-2017-5753
Cache
...
if (a < b)
array2[array1[a]] ”warning”
return](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-33-320.jpg)
![Side channels
Spectre CVE-2017-5753
Cache
array2[array1[a]]
if (a < b)
array2[array1[a]] ”warning”
return](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-34-320.jpg)
![Side channels
Spectre CVE-2017-5753
Cache
array2[array1[a]]
▶ Now we can leak the memory!
▶ array1[a] == 2
array2[0]
∆time ∼= x
array2[1]
∆time ∼= x
array2[2]
∆time ≪ x](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-35-320.jpg)

![Memory Corruptions
-fsanitize
Vulnerable program:
#include <stdio.h>
#include <stdlib.h>
int main(int argc, char **argv)
{
void *s[64] = {};
printf("%pn",
s[63 - atoi(argv[1]));
return 0;
}
$ clang test.c
$ ./a.out 1
(nil)
$ ./a.out 2
(nil)
$ ./a.out -1
0x7ffe3187bf10](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-38-320.jpg)

![Other problems
Alloca and VLA
▶ alloca will allocate memory on the stack, this
facilitates stack smashing and stack overflow!
▶ There are alloca checkers, so you can trace and
hunt bugs based on this feature.
int *x = alloca(3 * sizeof(int));
▶ VLA (variable length arrays), allocated using alloca.
▶ Security Nightmare (and bad practice)!
int foo(int a)
{
int x[a];
}](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-46-320.jpg)

![Buffer Overflow
Heap Overflow
▶ We can hijack malloc control fields
(malloc-maleficarium, House of Einherjar).
#include <cstdio >
#include <cstring >
class O {
private:
char buf[256];
public:
void getusr(char *b) {
strcpy(buf, b);
}
virtual void print() {
printf("%sn", buf);
}
};
int main(int argc,
char **argv)
{
O *o[2]={new O(),
new O()};
o[0]->getusr(argv[1]);
o[1]->getusr(argv[2]);
o[0]->print();
o[1]->print();
}](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-50-320.jpg)
![Buffer Overflow
Heap overflow
o[0]->buf
o[0]->vtable
o[1]->vtable
o[1]->buf
o[0]->vtable
AAAA
AAAA
BBBB](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-51-320.jpg)
![Control Flow Integrity
clang −fsanitize= c f i −f v i s i b i l i t y =hidden −f l t o
▶ You can view your program as a graph.
▶ Forward-edge-control-flow-integrity
▶ Backward-edge-contol-flow-integrity
typedef void *(*foo_t)(void *);
void *foo(void *_) { ... }
void *bar(void *_) { ... }
foo_t foos[2];
int main(int argc, char **argv) {
return foo[atoi(argv[1][0])](NULL);
}](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-53-320.jpg)
![Side channels
MeltDown
▶ For performance memory mapping is not changed
upon a context switch (but is protected using a
guard value).
raise_exception();
// the line below is never reached
access(probe_array[data * 4096]);
▶ With KAISER the kernel get swapped out from the
user space.](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-54-320.jpg)
![Side channels
SpectreV2
▶ Indirect branch predictions.
C:
class Base {
public:
virtual void Foo() = 0;
};
class Derived : public Base {
public:
void Foo() override { … }
};
Base* obj = new Derived;
obj->Foo();
ASM:
...
jmp [r15]
...](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-55-320.jpg)
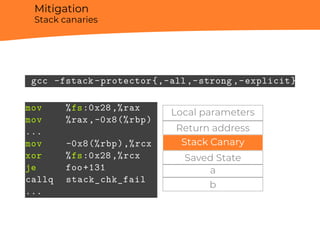
![Side channels
Spectre Mitigations
▶ LFENCE - serialization instruction;
▶ Retpoline - hack to avoid processor speculation on
indirect branch prediction.
jmp [r15]
Retpoline will rewrite this
indirect call to:
call set_up_target
loop:
pause
jmp loop
set_up_target:
mov r15, [rsp]
ret
lfence
; All instructions
; are serialized.](https://image.slidesharecdn.com/berardi-linuxhardeningandsecuritymeasuresagainstmemorycorruption-181212162855/85/Davide-Berardi-Linux-hardening-and-security-measures-against-Memory-corruption-56-320.jpg)