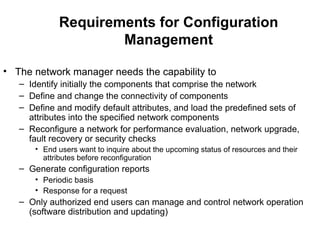
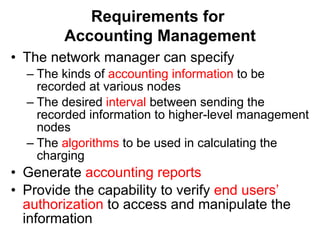
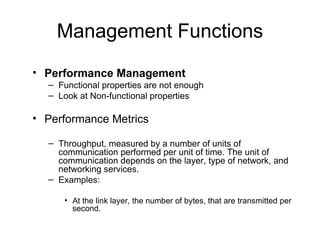
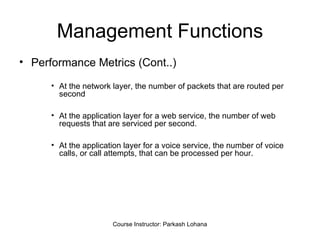
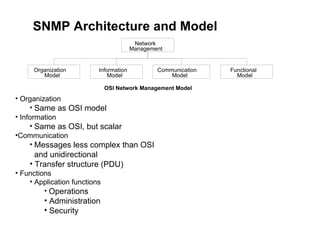
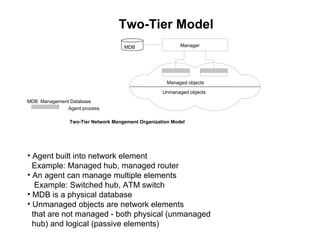
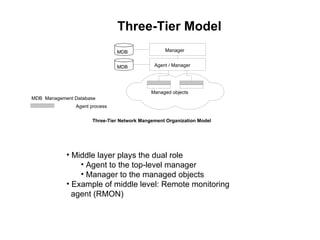
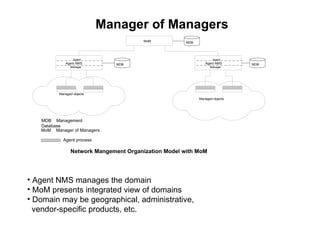
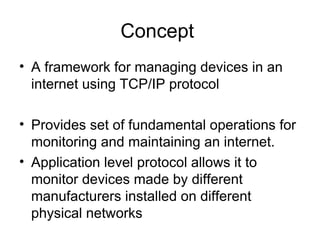
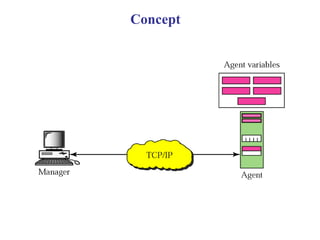
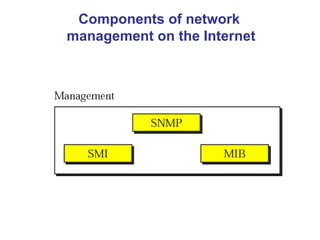
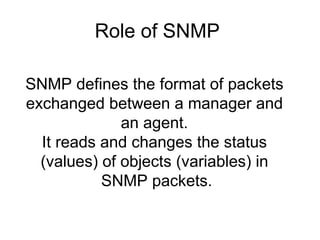
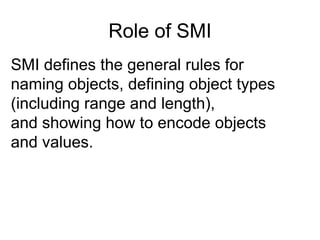
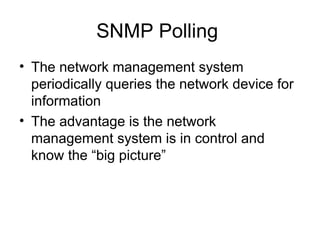
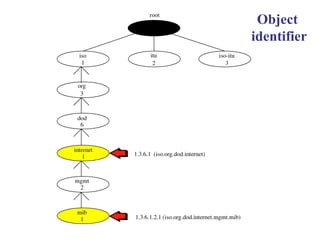
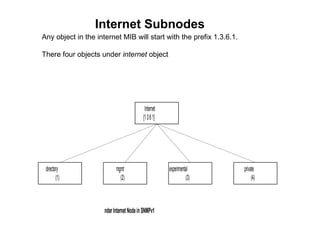
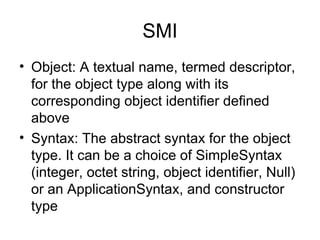
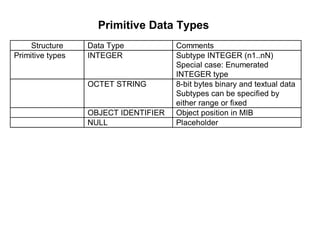
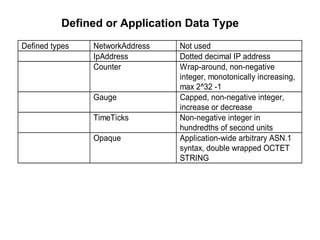
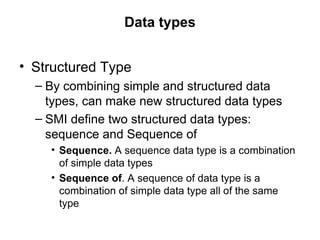
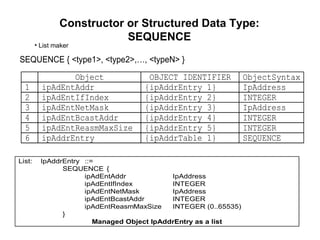
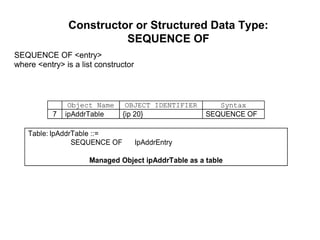
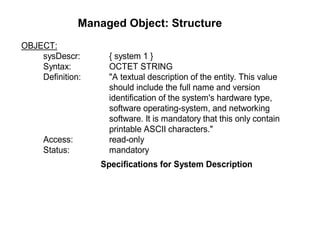
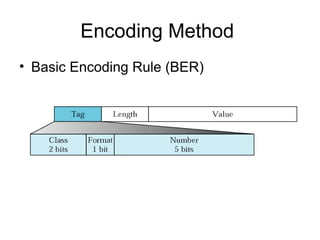
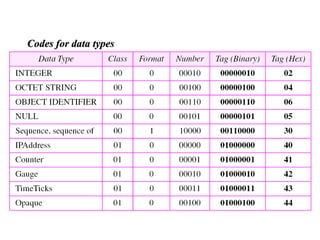
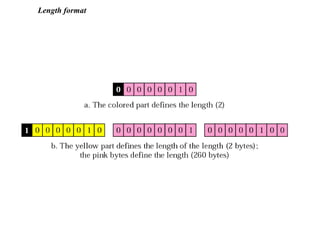
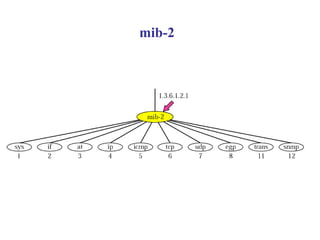
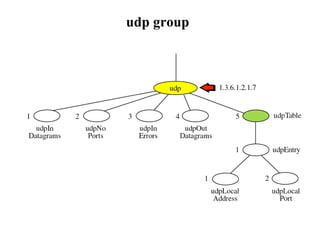
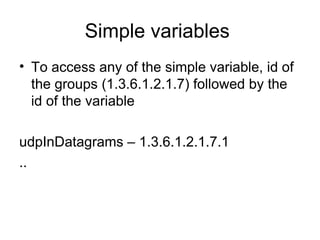
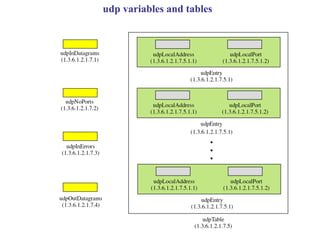
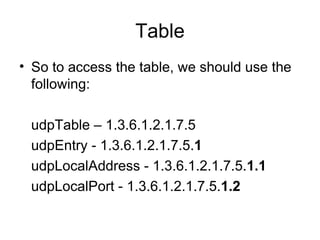
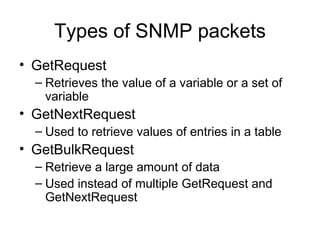
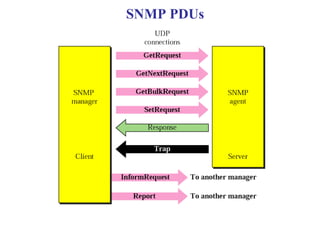
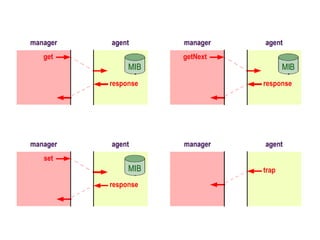
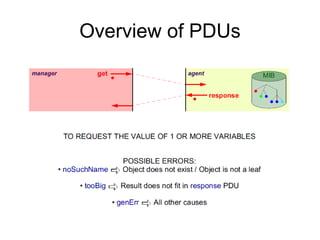
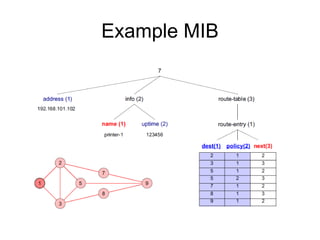
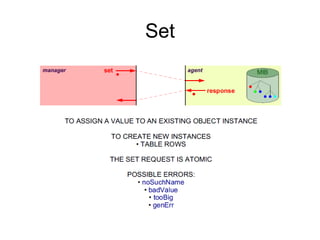
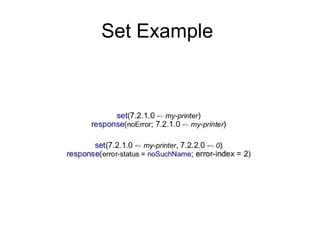
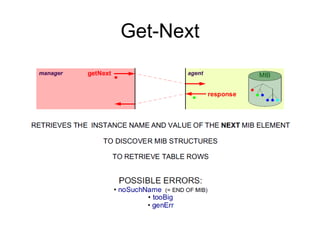
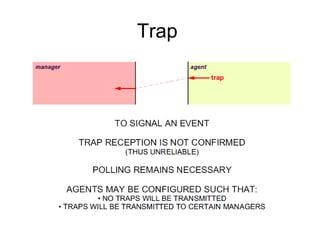
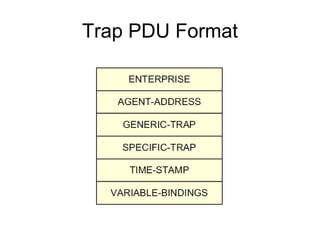
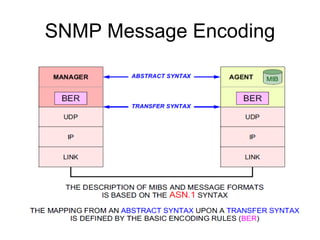
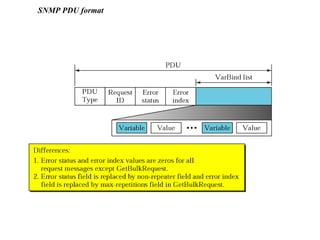
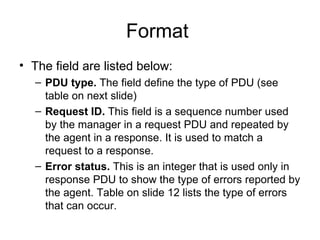
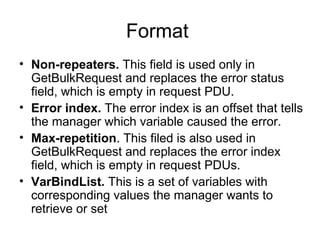
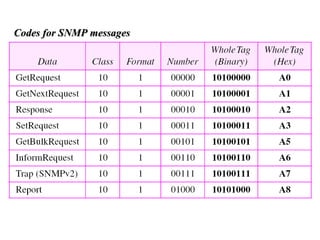
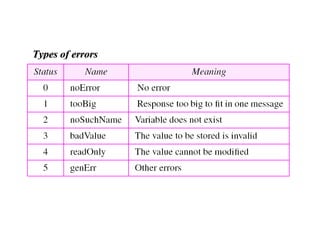
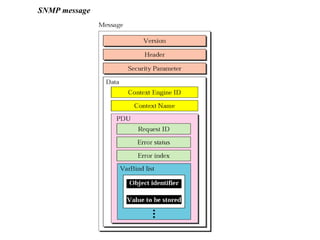
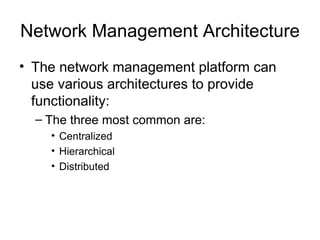
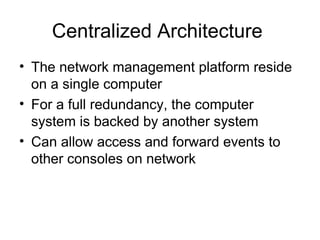
The document provides information about network management functions including fault management, configuration management, accounting management, performance management, and security management. It discusses the key concepts of SNMP including the manager, agent, MIB, SMI roles and the use of traps and polling for network monitoring.