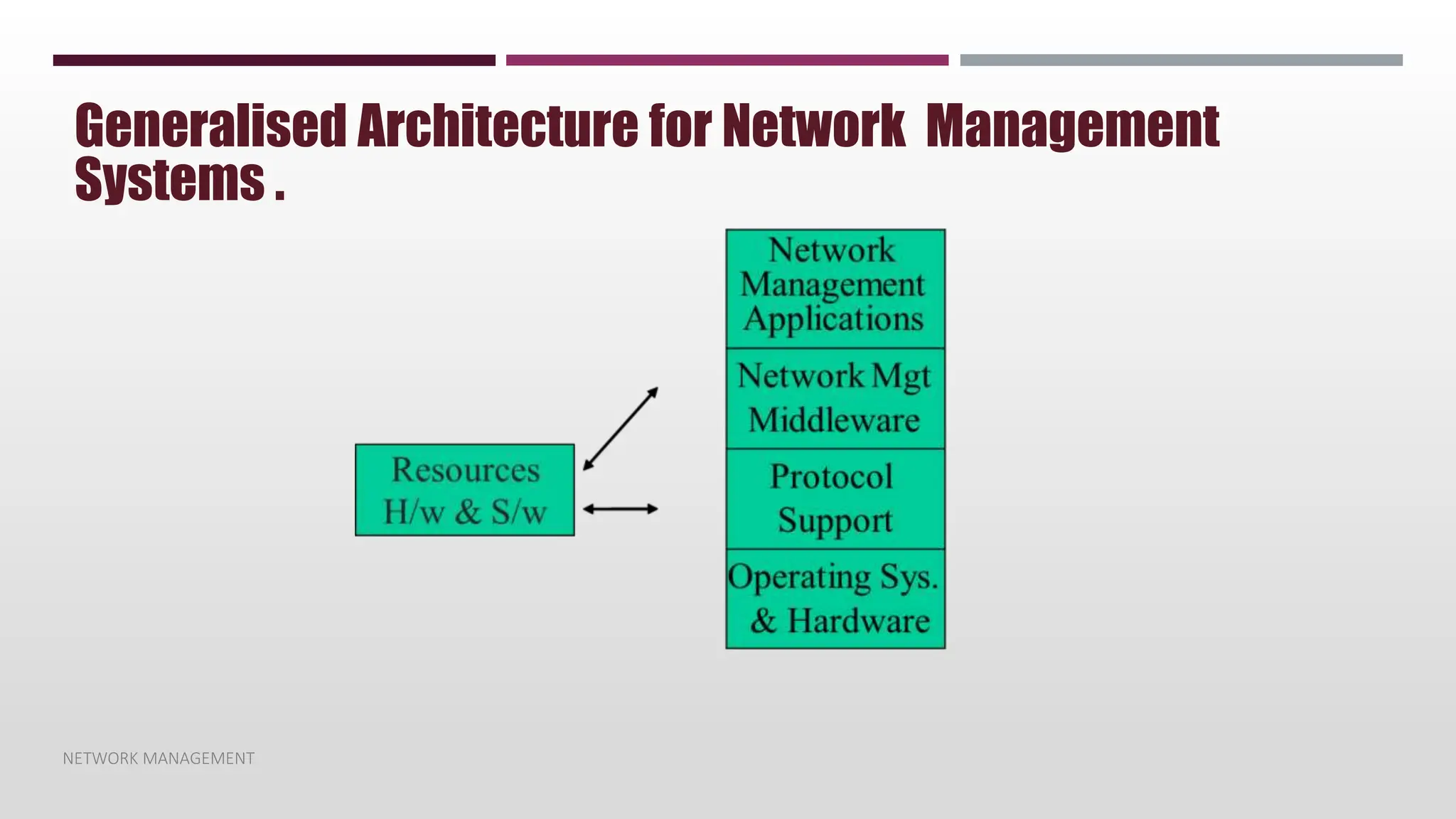
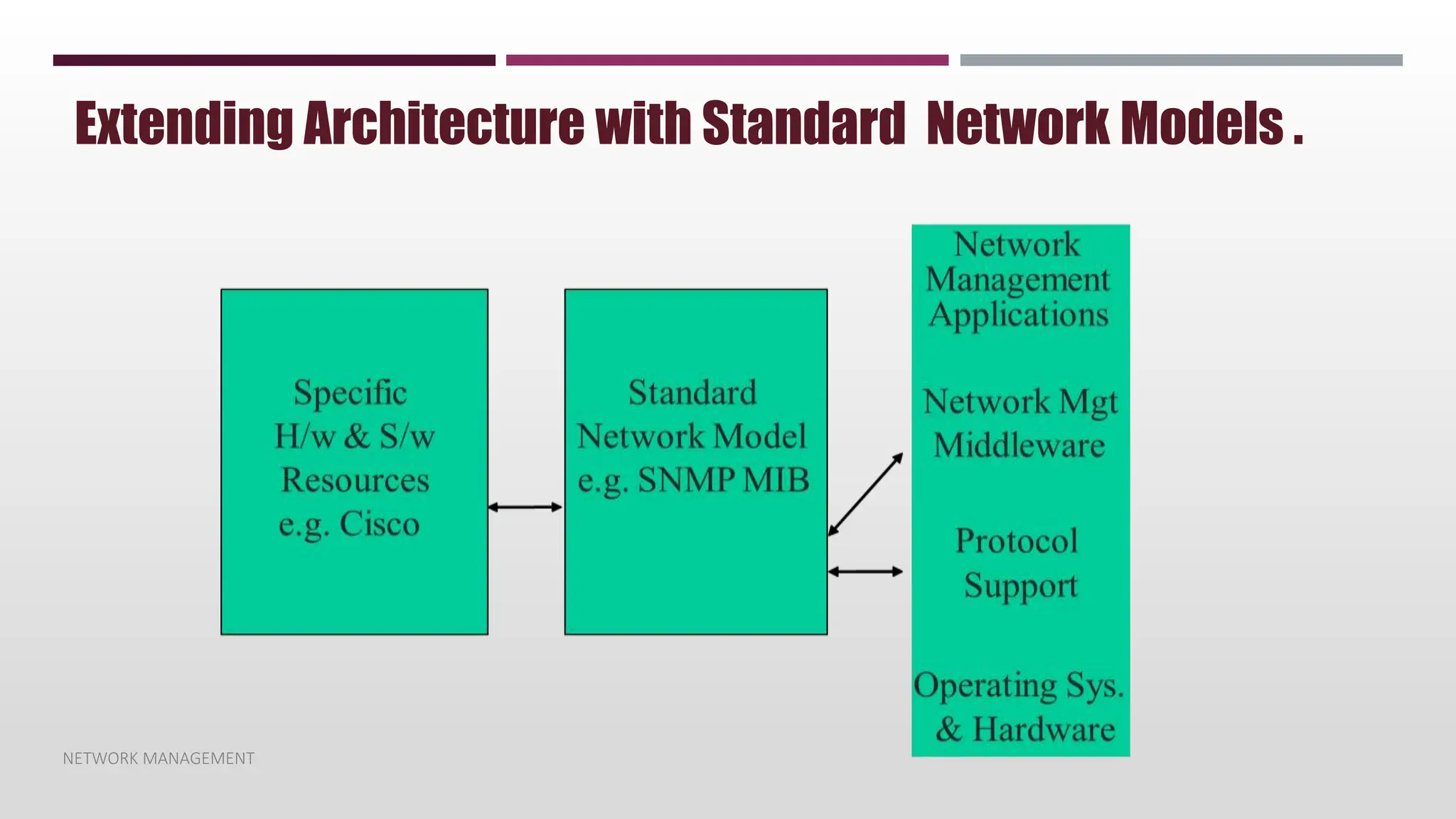
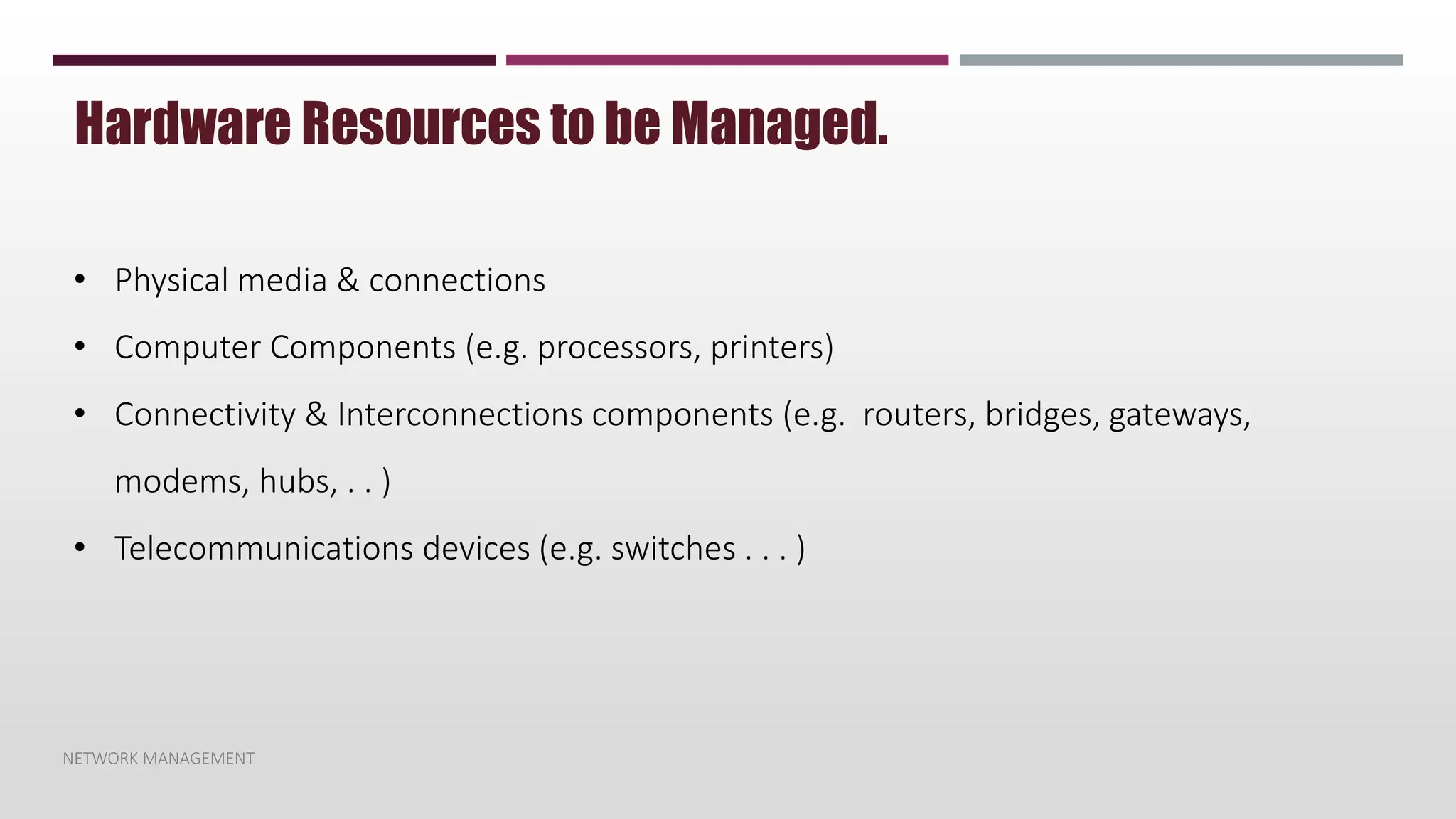
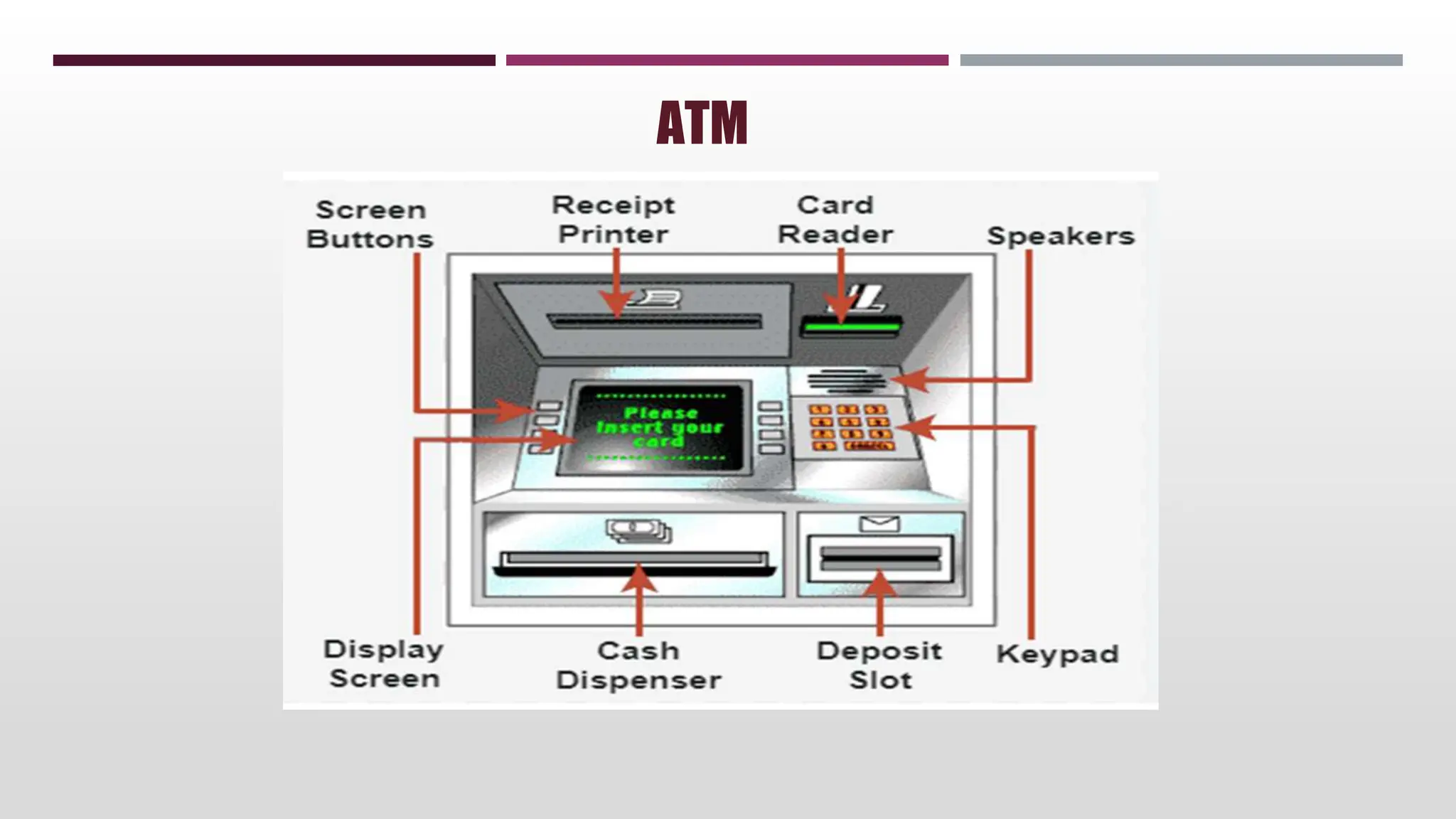
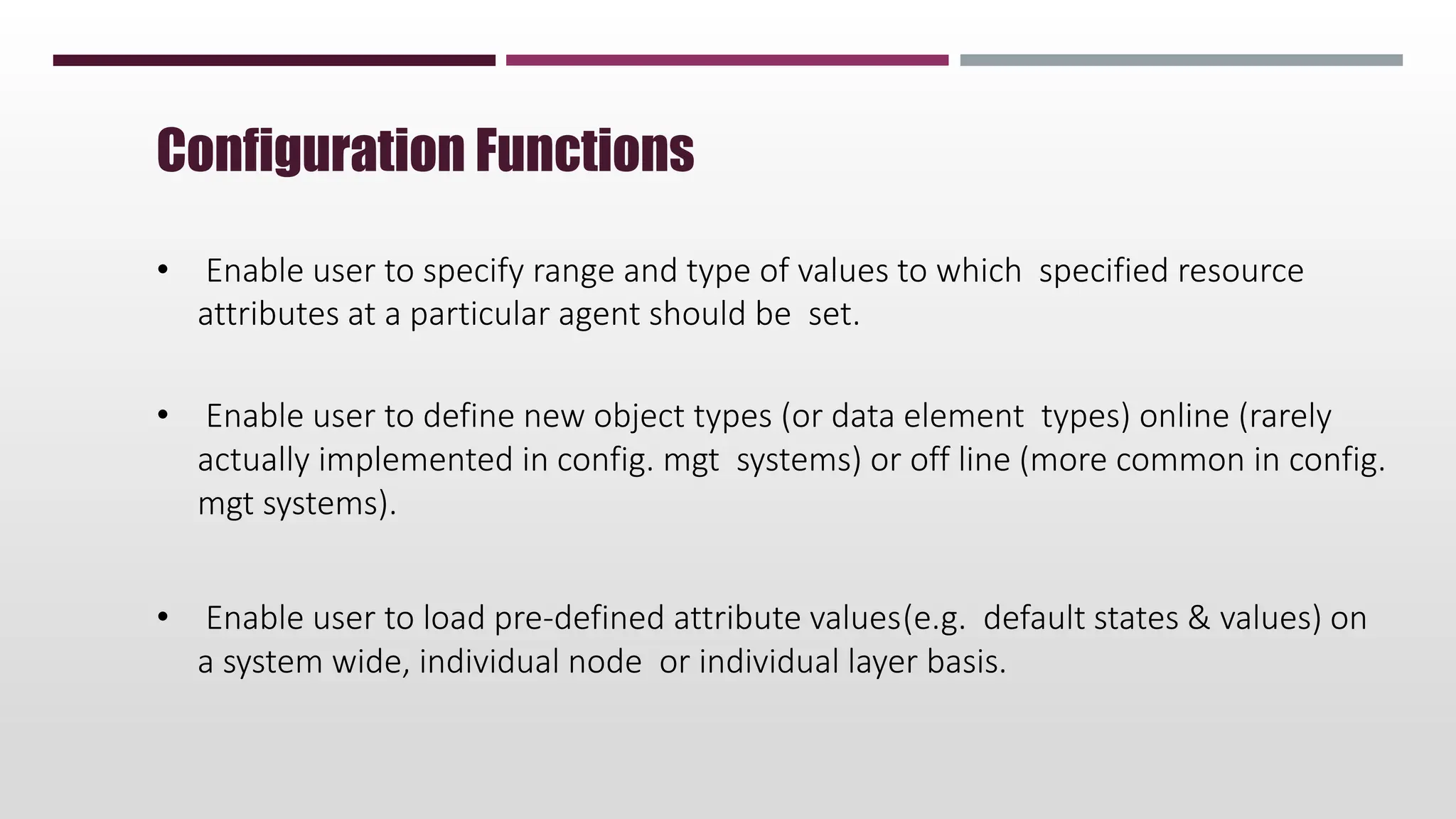
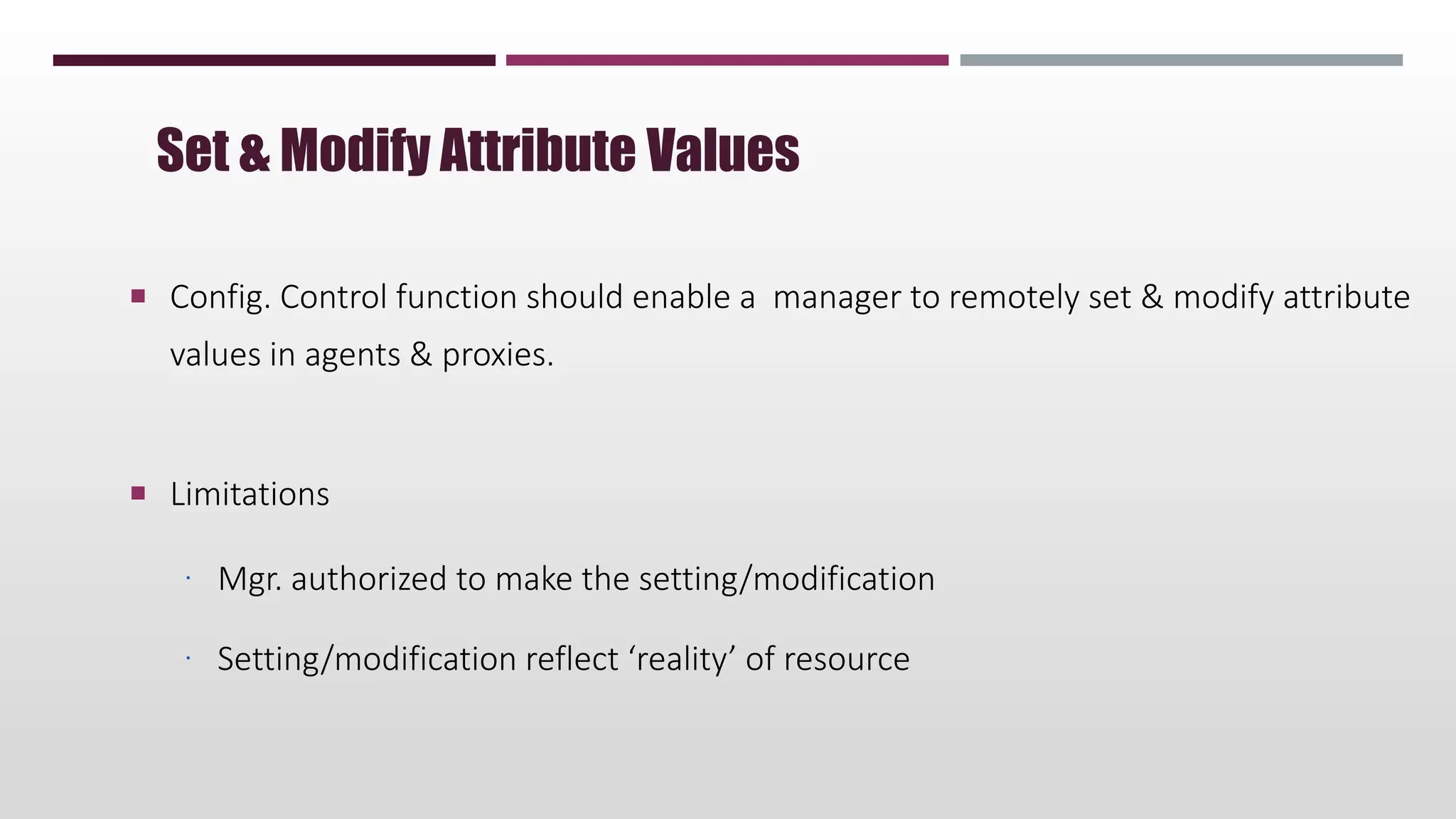
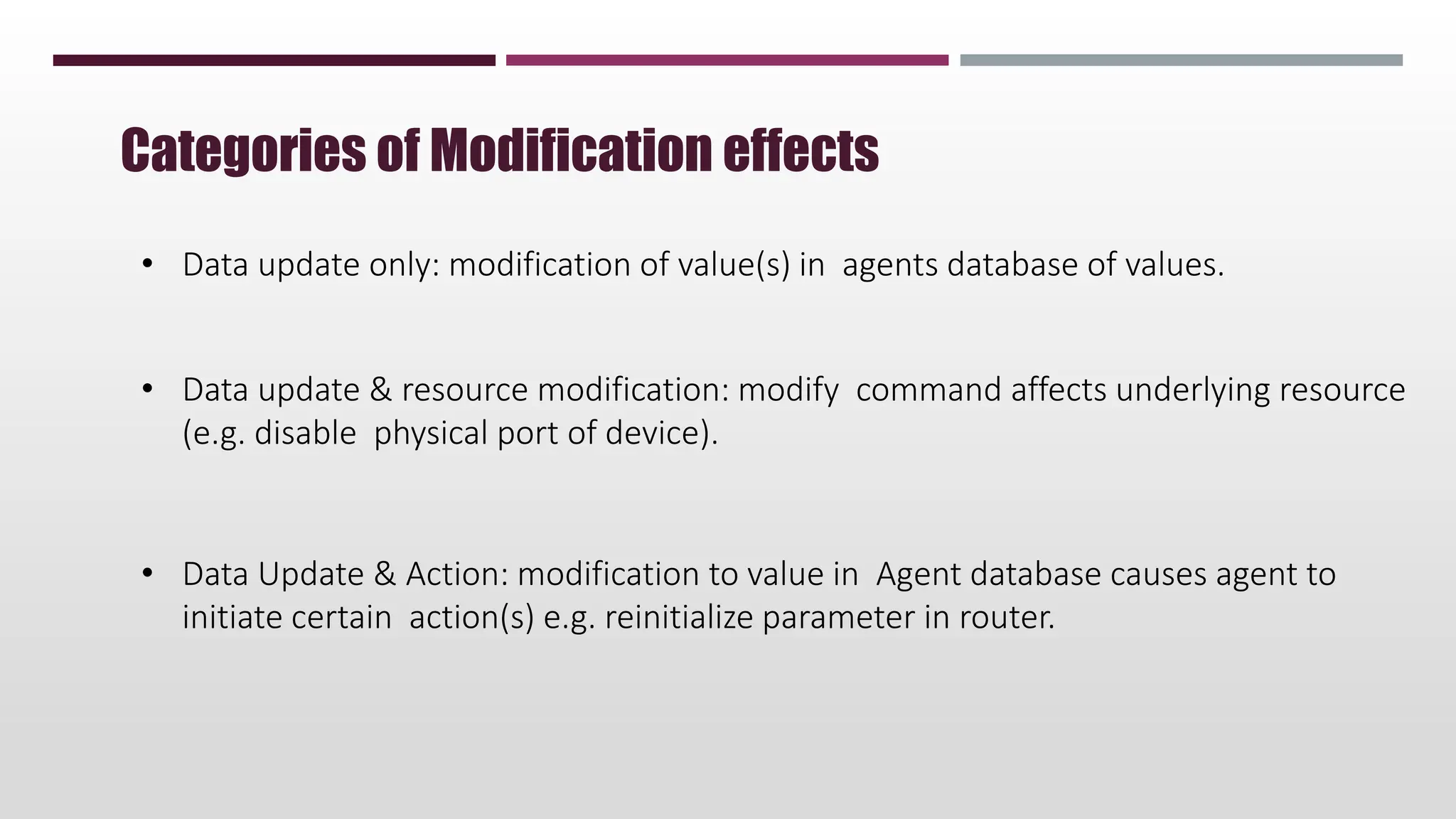
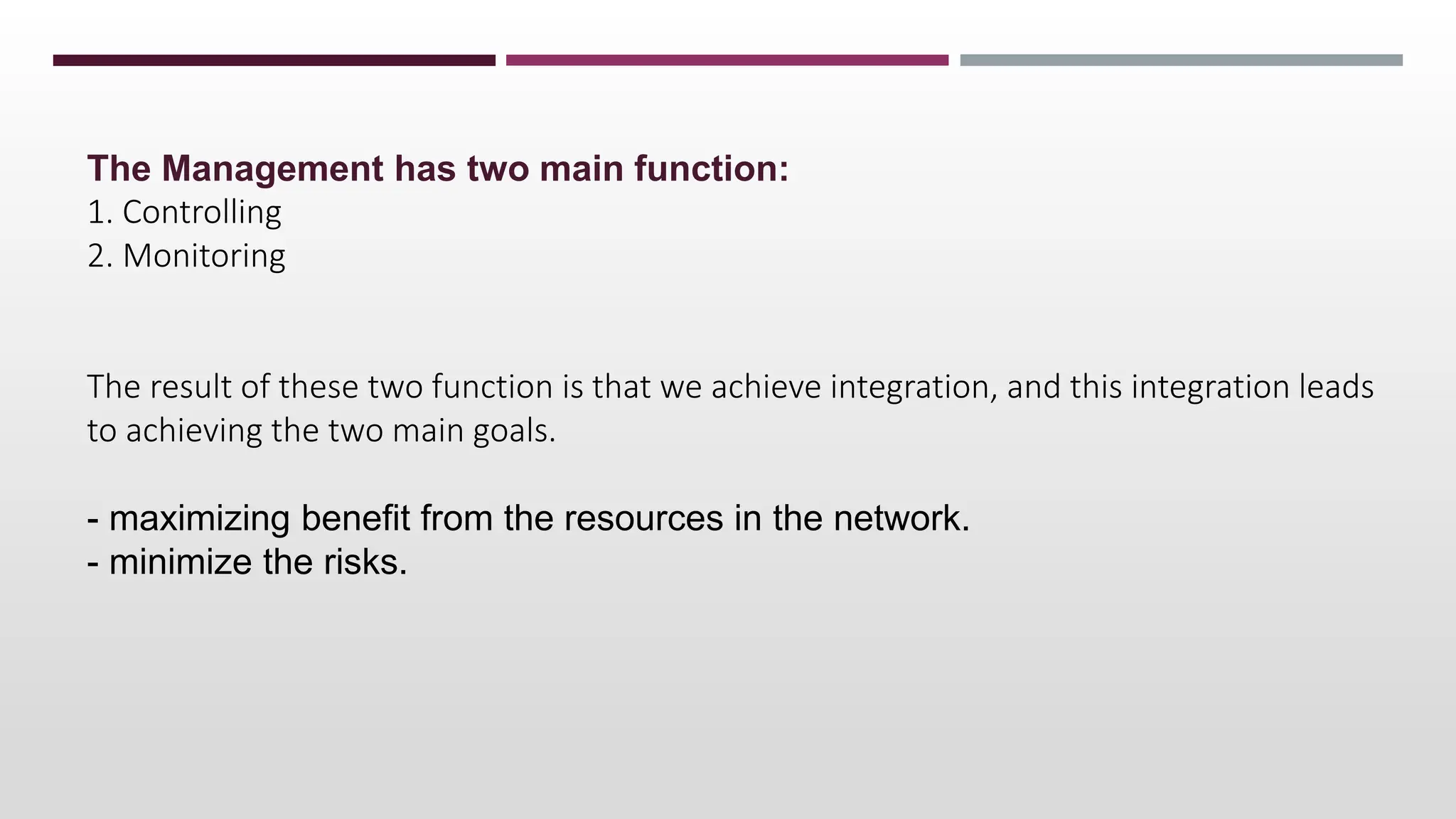
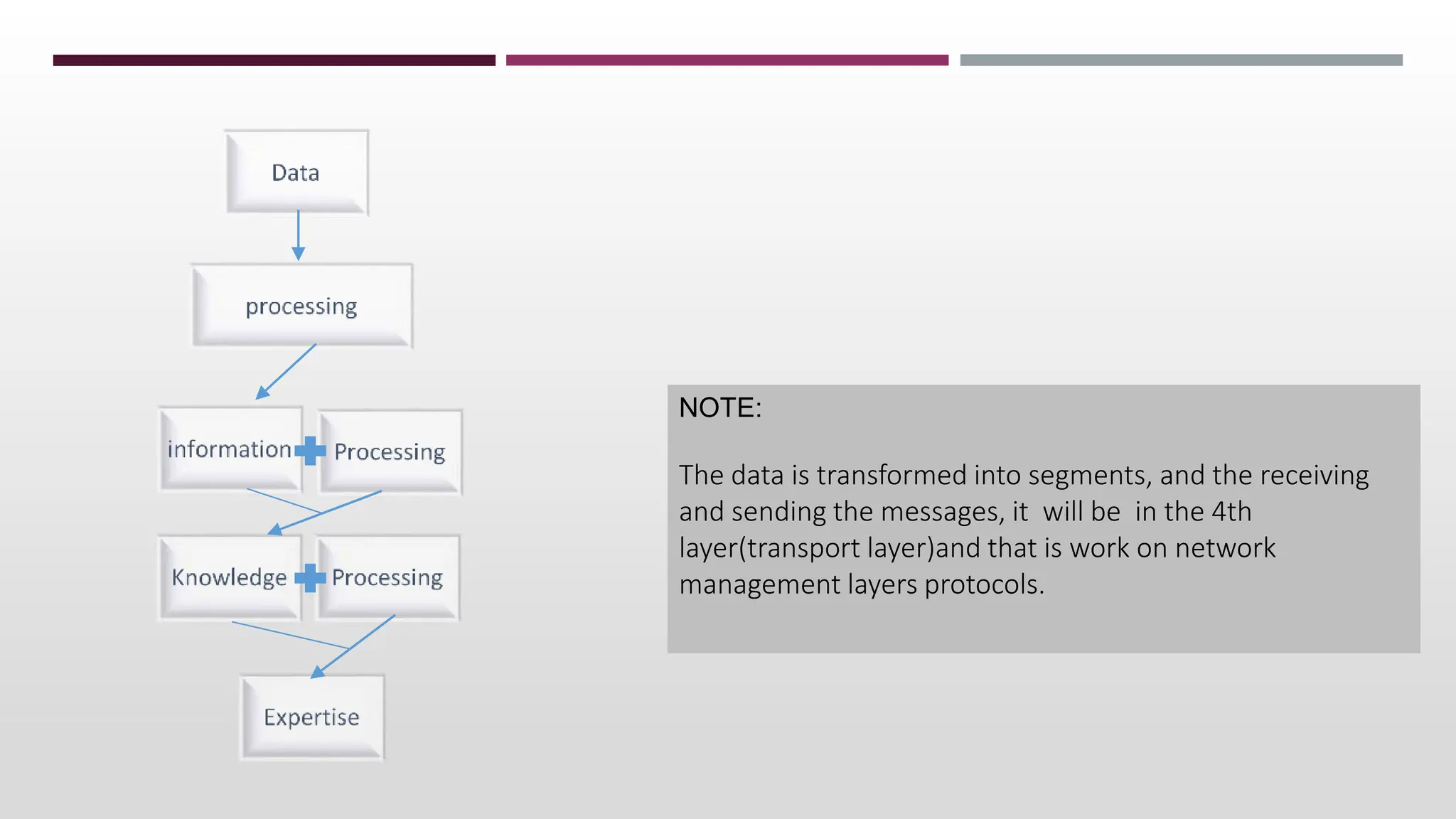
This document discusses network management. It begins by defining management and describing the two main functions of controlling and monitoring. It then discusses why network management is needed, the basic models of peer-to-peer and hierarchical management, and the general architecture. It also covers the hardware and software resources that need to be managed, as well as common management protocols and applications.
![NETWORK MANAGEMENT
What is Network Management& Systems Management ???
Several Definitions available!
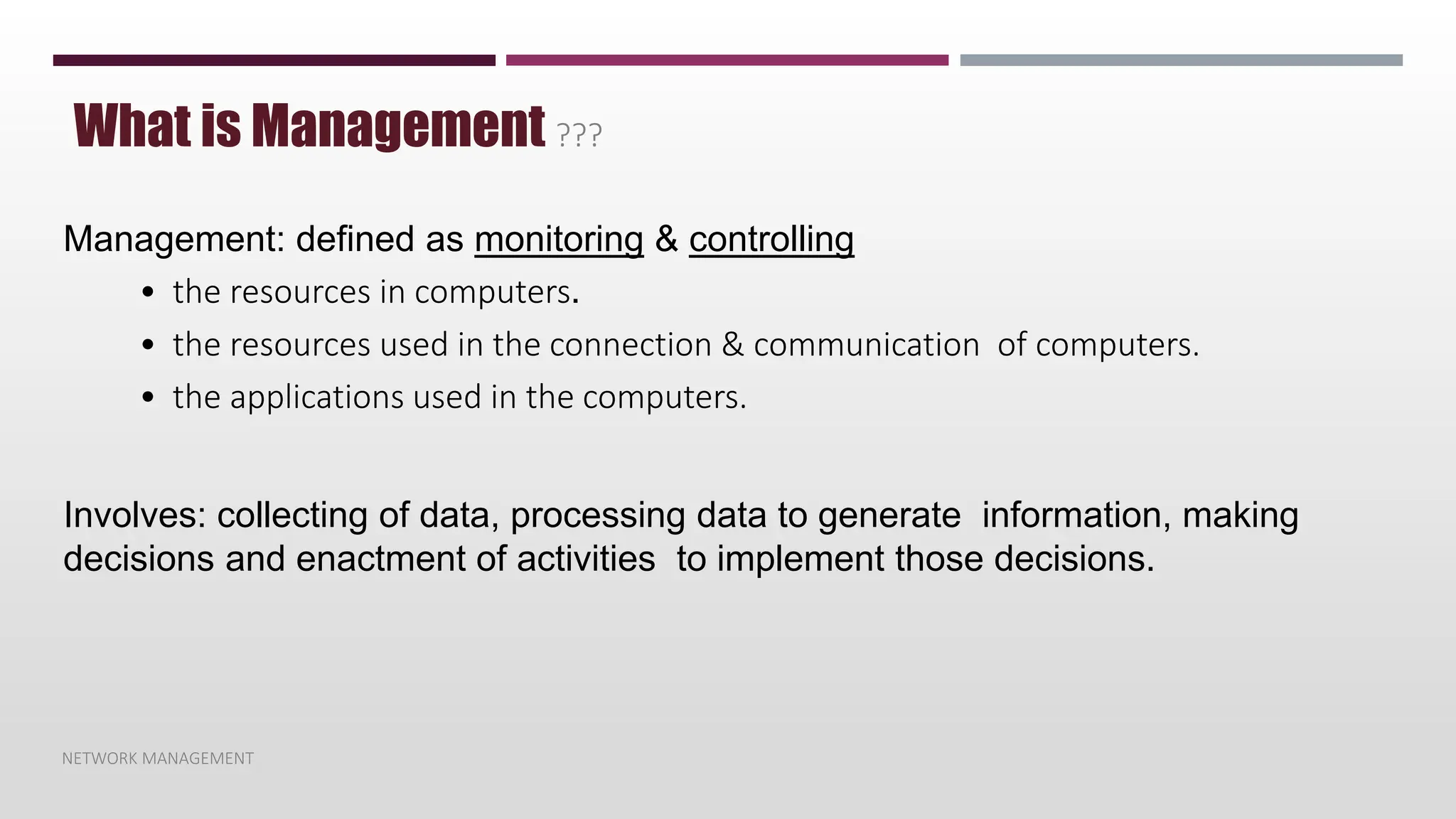
Network Management (NM) provides mechanisms for the monitoring, control and
coordination of all managed objects within the physical and data link layer of a network
node > [IEEE] (Institute of Electrical and Electronics Engineers)
Systems Management provides mechanisms for the monitoring, control and
coordination of all managed objects within open systems. This is effected through
application layer protocol > [IEEE] (Institute of Electrical and Electronics Engineers)
Network Management is subset of Systems Management](https://image.slidesharecdn.com/netmng1-231103143652-f70de9cd/75/Net-Mng1-pptx-5-2048.jpg)