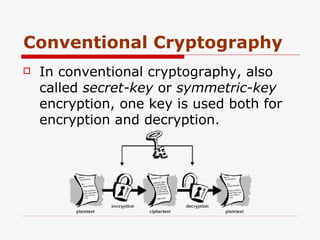
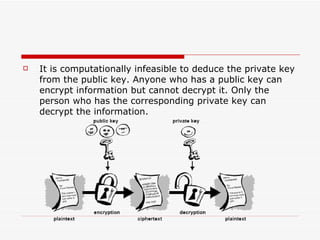
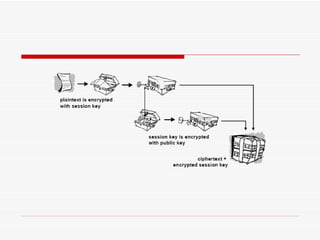
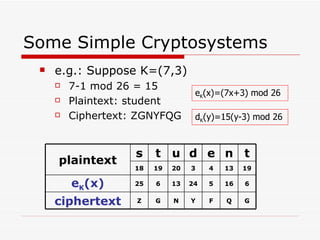
Cryptography involves encrypting plaintext data into ciphertext using encryption algorithms and keys. Conventional cryptography uses a single secret key for both encryption and decryption, while public key cryptography uses separate public and private keys. The combination of these methods in hybrid cryptosystems like PGP provides both the speed of conventional encryption and the key distribution benefits of public key cryptography.