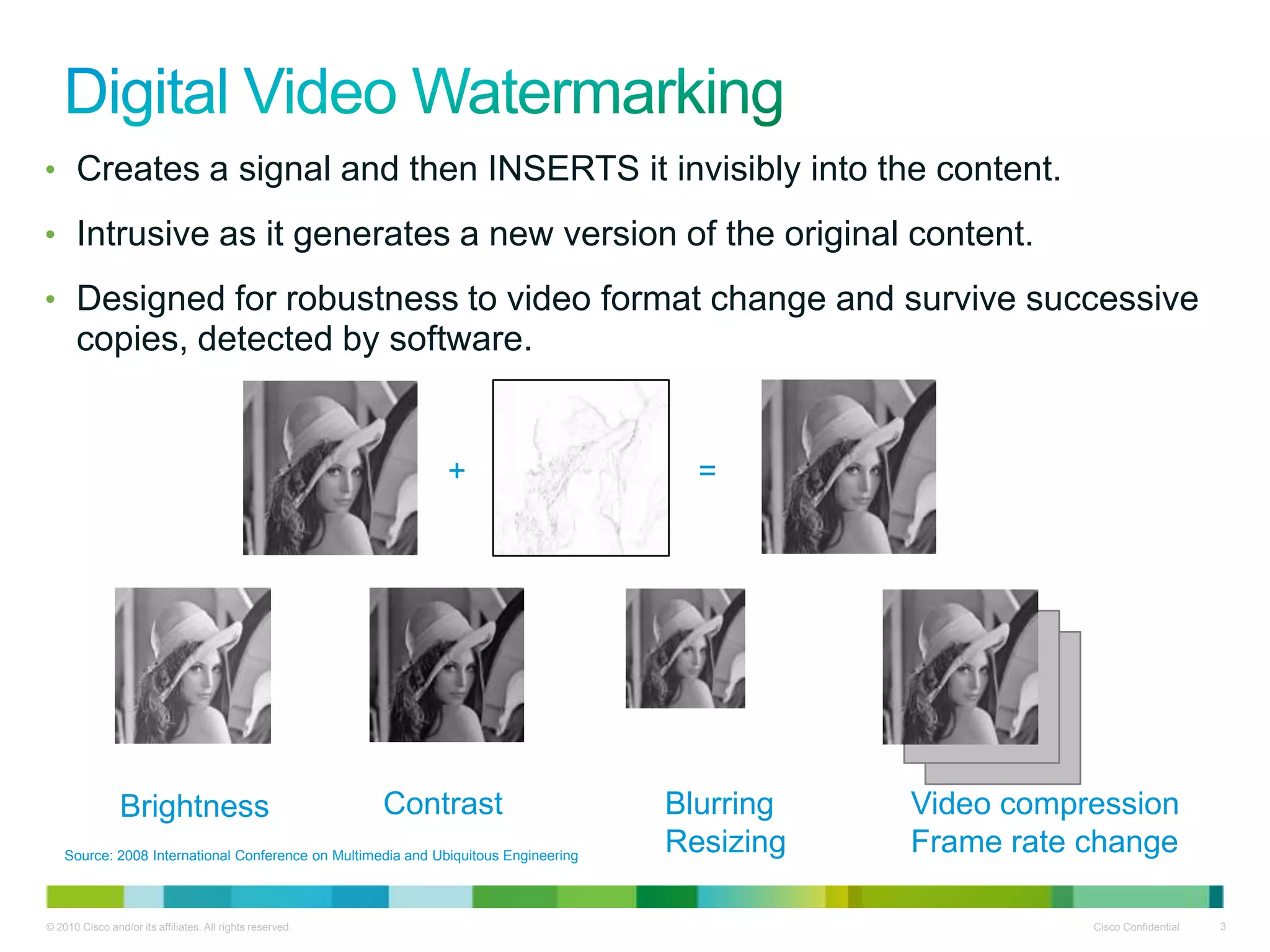
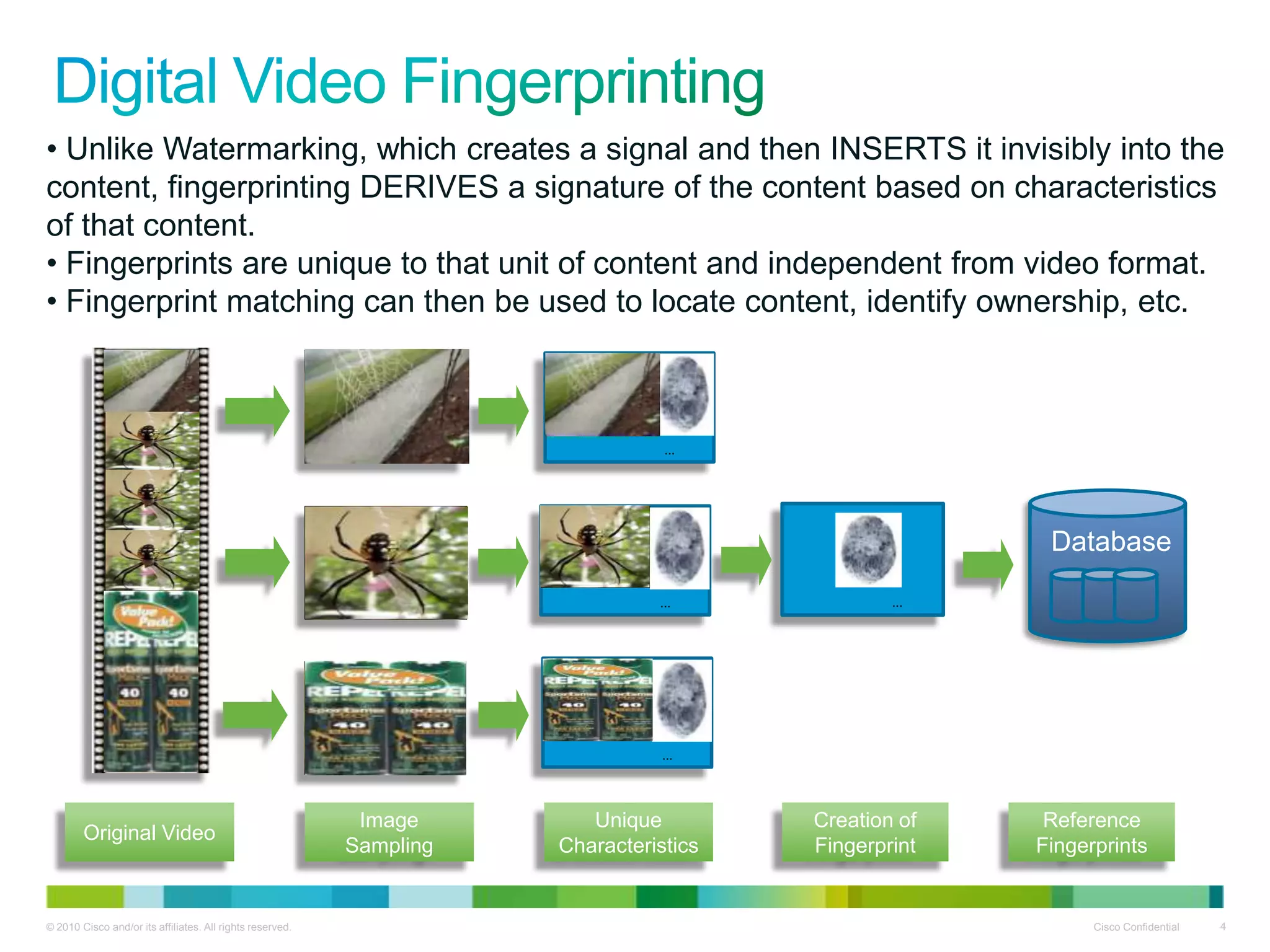
The document discusses solutions for identifying content ownership and managing premium video-on-demand content delivery. It describes fingerprinting and watermarking techniques that can identify content, monitor its distribution, and provide analytics to content owners. These techniques provide complementary ways to persistently track content across different formats and generations.