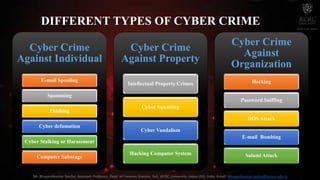
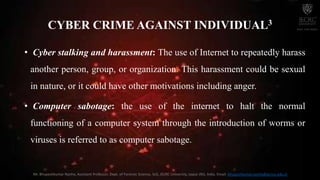
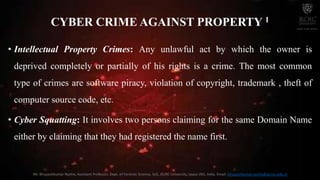
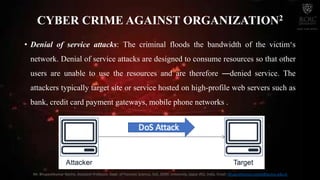
The document discusses cyber crime and its types. It defines cyber crime as any crime committed using computers and the internet. There are three main types of cyber crimes: those against individuals, property, and organizations. Crimes against individuals include email spoofing, phishing, spamming, cyber defamation, cyber stalking, and computer sabotage. Crimes against property involve intellectual property crimes, cyber squatting, cyber vandalism, and hacking. Crimes against organizations include hacking, password sniffing, denial of service attacks, email bombing, and salami attacks. The document also discusses symptoms of cyber attacks and provides recommendations for prevention.