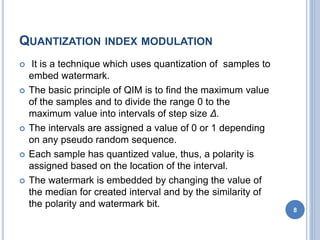
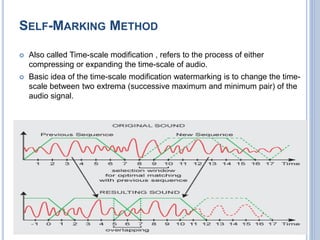
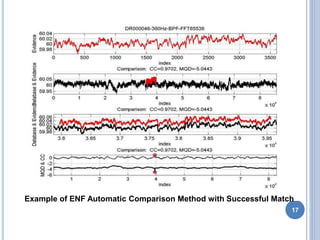
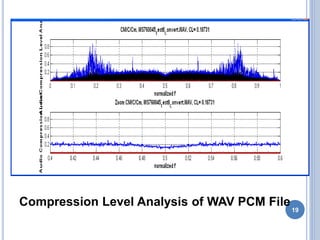
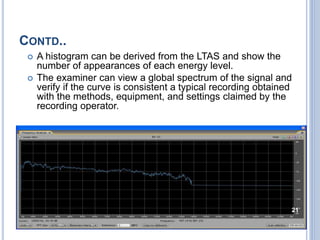
Audio authentication techniques can establish whether an audio recording is original, continuous, and unaltered. Some key techniques include audio watermarking, file structure analysis, waveform analysis, phase consistency testing, and compression analysis. Audio watermarking embeds identifying information through techniques like spread spectrum watermarking, LSB substitution, and quantization index modulation. File structure analysis examines the file format, header, and hexadecimal data. Waveform analysis and phase consistency testing look for discontinuities. Compression analysis evaluates lossy compression effects. These techniques help determine if an audio recording has been illegally copied or modified.