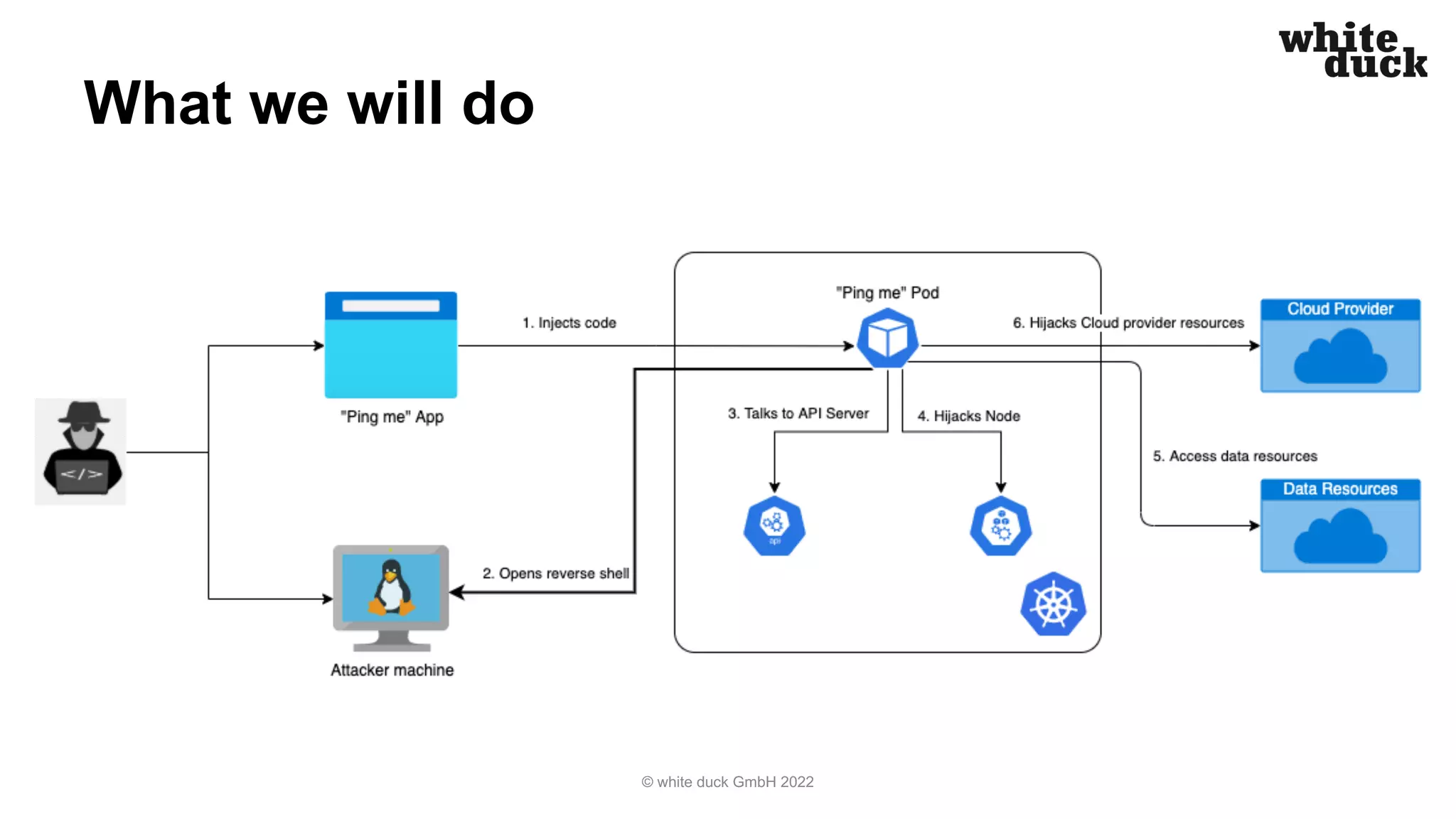
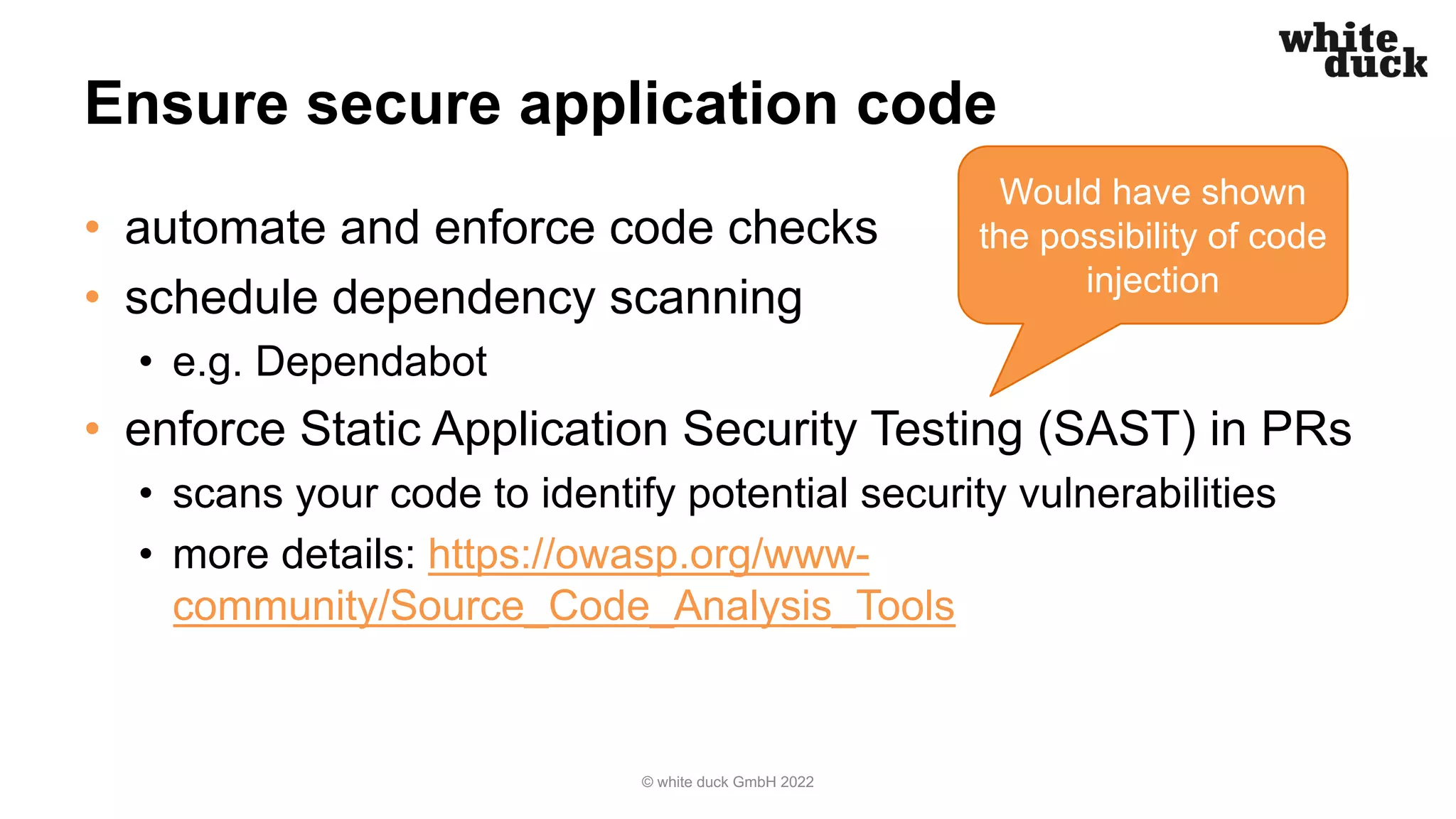
The document presents a walkthrough on how to hijack a Kubernetes cluster while highlighting common attack vectors and preventive measures. It emphasizes secure application code, container image building, secure deployment practices, and the importance of Kubernetes and network policies to enhance security. Additionally, it offers recommendations for best practices to minimize security risks in cloud environments.