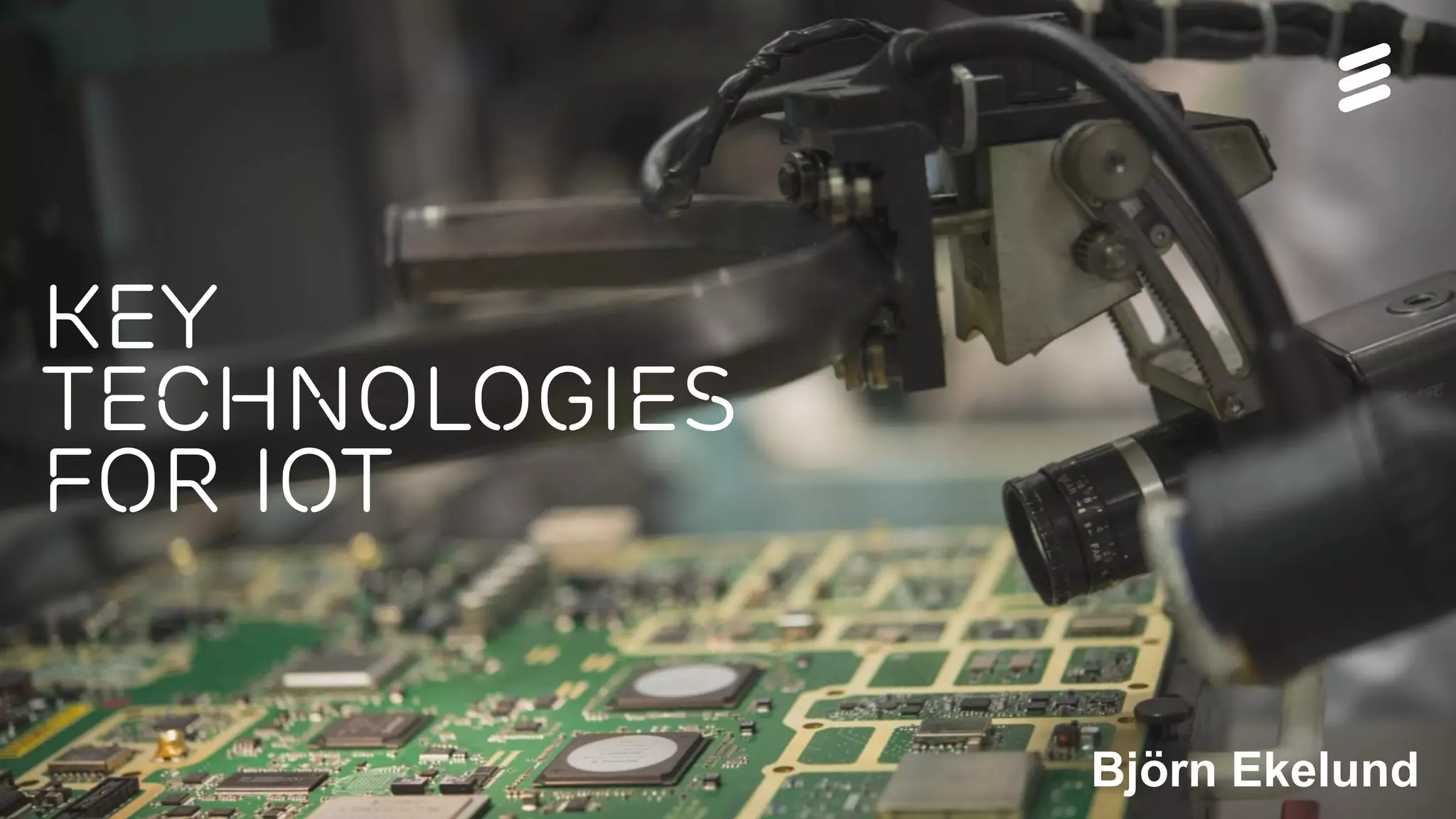
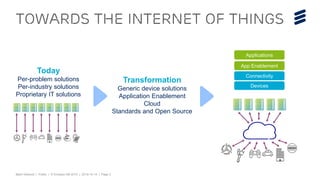
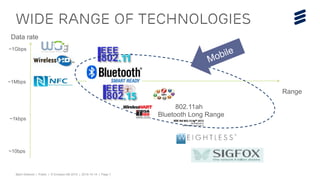
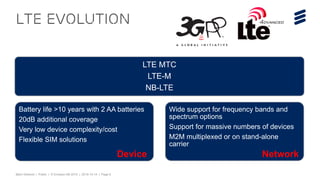
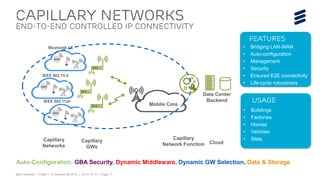
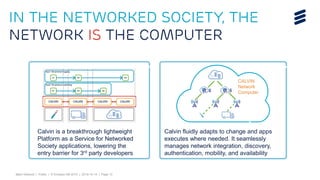
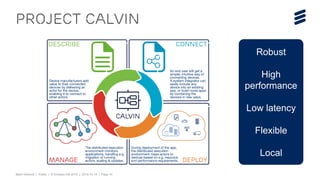
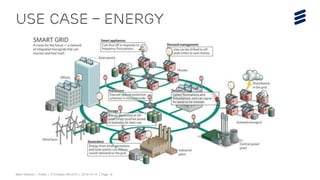
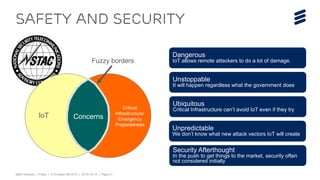
This document discusses key technologies that are enabling the Internet of Things (IoT), including wireless connectivity standards like LTE-M and NB-LTE that allow devices to connect using little power. It also discusses capillary networking which provides end-to-end IP connectivity between devices. Additionally, it covers distributed cloud and edge computing approaches like Project CALVIN which process data closer to where it is generated. Finally, the document outlines security challenges with IoT and the need for approaches that can provide integrity and trustworthiness at scale.